Office of State Controller, and the North Carolina Department of The
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

World Wide Notary and Pennsylvania Association of Notaries Form Alliance for Country’S First Online Notarial Journal
Press Release Source: WWNotary, L.L.C. WORLD WIDE NOTARY AND PENNSYLVANIA ASSOCIATION OF NOTARIES FORM ALLIANCE FOR COUNTRY’S FIRST ONLINE NOTARIAL JOURNAL Vernon, TX—(01/07/2006) World Wide Notary (WWNotary), a leading provider of electronic notary products and services, announced that it has formed an alliance with Pittsburgh-based Pennsylvania Association of Notaries (PAN) to provide WWNotary’s DigaSign Journal, a platform-independent, Internet- based notarial recordkeeping system for the state’s more than 75,000 notaries public. The agreement enables USNA to provide an electronic solution for notaries who wish to keep an electronic journal. DigaSign Journal accepts manual entries by the notary, ensures compliance with state journal requirements, stores the records on a secure Internet server, and produces the journal on demand for the notary to review, print or export in Adobe Portable Document Format (PDF) PAN is also offering DigaSign Journal to notaries who are anticipating the next step to electronic notarization. WWNotary offers the DigaSign Suite of applications that allows users in any industry—such as real estate, government, law, insurance, title and banking—to add their unique biometric signatures to documents transacted with DigaSign’s digital signature and encryption technology. “DigaSign Journal is the logical next step in electronic notary journals, and PAN is proud to partner with a leader in eNotarization technology,” said PAN’s president, Marc Aronson. “Notaries may now keep electronic journals that offer seamless transitions to eNotarization with other DigaSign applications. At the same time, the notary who wants only to keep an electronic journal can easily and efficiently do just that.” PAN has worked closely with WWNotary during the last two years to ensure that DigaSign Journal complies with Pennsylvania notary law requirements. -

Enhance Qualified Electronic Signatures with What You See Is What You Sign QES and WYSIWYS Service - Powered by Cryptomathic and Swisscom
Solution Brief Enhance Qualified Electronic Signatures with What You See Is What You Sign QES and WYSIWYS Service - Powered by Cryptomathic and Swisscom Qualified remote signing and Solution benefits WYSIWYS - hosted eID services The best way to deliver Qualified Electronic Signature ü Offer Advanced or Qualified (QES) services across different channels is to use Electronic Signatures compliant with remote signing technology. It integrates smoothly the Swiss signature law, ZertES, and the with any web application and does not require any EU eIDAS regulation on trust services. software install, plug in or additional components and can be used anywhere, at any time, from any device ü Improve the users’ signing with browsing capacity. Qualified remote signing experience for all channels incl. web provides the highest legal value and international portals, desktop applications, mobile & acceptance, while What You See Is What You Sign tablet platforms (WYSIWYS) technology delivers a seamless user experience with strong non-repudiation. Combining ü Demonstrate unrivalled non- QES with WYSIWYS is a strong enabler for businesses repudiation with WYSIWYS to provide ultimate security, trust and convenience funcionality with online transactions. This is exactly what the Cryptomathic – Swisscom solution offers, namely the ü Eliminate smartcards, card readers possibility to offer Advanced or Qualified Electronic and local software install Signatures using a zero-footprint remote signing hosted service, featuring WYSIWYS functionality. ü Solve data -
Global Guide to Electronic Signature
Global Guide to Electronic Signature Law: Country by country summaries of law and enforceability Table of contents Introduction 3 Germany 9 Republic of Korea 15 Definition of terms 4 Greece 9 Romania 9 Recommended practices for Hong Kong 10 Russian Federation 16 electronic agreements 4 Hungary 9 Singapore 16 India 10 Slovakia 9 Country summaries of Indonesia 11 Slovenia 9 electronic signature law Ireland 9 South Africa 17 Argentina 5 Israel 11 Spain 9 Australia 5 Italy 9 Sweden 9 Austria 9 Japan 12 Switzerland 17 Belgium 9 Latvia 9 Taiwan 18 Bermuda 6 Lithuania 9 Thailand 18 Brazil 6 Luxembourg 9 Turkey 19 Bulgaria 9 Malaysia 12 United Kingdom 9 Canada 7 Malta 9 United States 19 Chile 7 Mexico 13 Uruguay 20 China 8 Netherlands 9 Colombia 8 New Zealand 13 Croatia 9 Norway 14 Czech Republic 9 Peru 14 Denmark 9 Philippines 15 Estonia 9 Poland 9 European Union 9 Portugal 9 Finland 9 Republic of Cyprus 9 France 9 © Adobe Systems Incorporated 2016. This information is intended to help businesses understand the legal framework of electronic signatures. 2 However, Adobe cannot provide legal advice. This guide is not intended as legal advice and should not serve as a substitute for professional legal advice. You should consult an attorney regarding your specific legal questions. Introduction Electronic and digital signatures represent a tremendous opportunity for organizations to get documents signed and close deals faster. When rolling out e-signatures globally, you need to be aware of the variety of electronic signature laws across the globe. This guide gives you a great place to start. -

Qualified and Advanced Electronic Signatures)
R Terms and Conditions of Use Swisscom certification service (Qualified and advanced Electronic Signatures) Terms and Conditions of Use for the use of the Swisscom qualified certificate is permitted in connection with the use certification service with qualified and advanced certificates of the trust service in accordance with these Terms and Con- for qualified and advanced electronic signatures (Swisscom ditions of Use ("limitation of use"). certificate class "Saphir and Diamant") 2.2 Identity verification process and retention of the infor- mation Swisscom or the registration authority appointed by 1 Scope of these Terms and Conditions of Use Swisscom checks your identity in the identity verification pro- These Terms and Conditions of Use shall apply in the rela- cess. For qualified electronic signatures, this is done by tionship between you and Swisscom (Schweiz) AG, Alte means of your passport or an identity card allowing travel to Tiefenaustrasse 6, Worblaufen, Switzerland, company ID Switzerland. Depending in each case on the actual organisa- CHE-101.654.423 (hereinafter "Swisscom") for your use of tion of the identity verification process, you may be re- the Swisscom certification service with qualified and ad- quested in the verification process for advanced electronic vanced certificates for qualified and advanced electronic sig- signatures to also submit other documents than those re- natures. quired for qualified electronic signatures. 2 Swisscom’s Services Based on your identify verification process for qualified elec- tronic signatures, you may also create advanced electronic 2.1 Certification service in general signatures in accordance with these Terms and Conditions of For your certification services with qualified certificates, Use where the subscriber application used by you offers dif- Swisscom is an accredited certification services provider in ferent types of signatures. -

Eidas and E-SIGNATURE a LEGAL PERSPECTIVE: ELECTRONIC SIGNATURES in the EUROPEAN UNION
eIDAS AND E-SIGNATURE A LEGAL PERSPECTIVE: ELECTRONIC SIGNATURES IN THE EUROPEAN UNION WHITE PAPER TABLE OF CONTENTS Part 1: Introduction 3 Key Highlights of the eIDAS Regulation 4 Legal Effect of Different Types of Signatures 6 Regulation of Trust Services 7 Legal Best Practices 8 Part 2: Compliance With the Regulation 9 Advanced Electronic Signatures 9 Qualified Electronic Signatures 10 Format Standards 12 Additional Evidence 12 Conclusion 13 E-Signature Solution Checklist 14 About the Authors This paper is a collaboration between Lorna Brazell of Osborne Clarke LLP and OneSpan. In part one, Osborne Clarke provides a legal opinion on the legal validity of electronic signature in the European Union. Part two has been prepared by OneSpan, and summarizes best practices recommendations for legal compliance when implementing e-signatures. eIDAS & E-SIGNATURE: A LEGAL PERSPECTIVE FOLLOW US 2 PART 1 Introduction The 2014 Regulation on Electronic Identification and Trust Services for Electronic Transaction in the Internal Market1 (“eIDAS”) went into effect throughout the European Union (“EU”) on 1 July 2016, replacing the 1999 Directive on electronic signatures2 (“the Directive”). Although the Directive had not been the subject of any disputes in its 16-year history, neither had it been a success. Its objective, to enable the widespread use of electronic signatures to conduct business across borders within the EU, was not met. There Are Three Key Reasons for This: I. Most EU Member States’ laws do not specify any form of signature for commercial contracts other than guarantees or contracts assigning real property. II. Many people mistakenly believed that the Directive mandated the use of advanced electronic signatures supported by a qualified certificate3 in order for an electronic signature to be legally effective. -

Notary Public of Texas Rules
Notary Public Of Texas Rules Welsh restaged her salal iridescently, she flavours it well. Is Joao always ancestral and shakeable when snitch Shurwoodsome prostyle mistranslating very wherewith his azimuths. and hopingly? Hopping and impactive Raymundo flunks so squeamishly that Your underwriter when dealing with the record in black ink seal of notary public texas rules, automobiles and include your application and surety bond instructions provided evidence of fiduciary relationships often have. On Training is temporarily suspended during the coronavirus pandemic. Notary commission of a texas, holographic will have legal provider platform has their notary public of texas rules must obtain a mobile notary. An authorized the texas notary rules of public information or their omission insurance policy does not disqualified by continuing to be notarized documents? The notarization must meet qualifications, it intend to affix the state then sends the date of law in texas notary or online notary is done via facetime, texas notary rules of public? Cameron is not be notarized or their commission writes and state for notarization answers and rules of exculpatory clauses in. Online notary loan closing process or zoom meeting some other communication technology was performed pursuant to the transaction and many many other certifications. Plus shipping and rules of notary public texas requires online. The materials available on all KRCL blogs are for informational purposes only and are not intended to serve as legal advice. Please remove it may contain much does texas notary public of rules are. Around the duties for notarial certificate of law even for notary public of rules that requires them, governor has posted additional information being longstanding members are the collection. -

Eidas Regulation Questions & Answers
eIDAS Regulation Questions & Answers on rules applicable to Trust Services as of 1 July 2016 The eIDAS Regulation (Regulation (EU) N°910/2014) on electronic identification and trust services for electronic transactions in the internal market (eIDAS Regulation) adopted by the co-legislators on 23 July 2014 is a milestone as it provides a predictable regulatory environment for electronic identification and trust services, including electronic signatures, seals, time stamps, registered delivery and website authentication. As of 1 July 2016, the provisions applicable to trust services apply directly in the 28 Member States. This means that trust services under eIDAS are no longer regulated by national laws. As a result, the qualified trust services are recognised independently of the Member State where the Qualified Trust Service Provider is established or where the specific qualified trust service is offered. What’s new? What changes with regard to the former eSignature Directive? What must be done at national level? How does it impact market operators? How does it benefit the users (citizens, businesses and public administrations)? What has the Commission done to facilitate the switchover? These questions and many others have been asked along the road since the adoption. We have compiled this Q&A document to help those of you who need to fully understand the new legal framework in order to implement it or reap the benefits of electronic transactions, as well as those of you who are curious about the Regulation’s various implications. I. What is new? How will the legal effect of electronic signature change under eIDAS (compared to the regime under the eSignature Directive) as from 1 July 2016? Since 1 July 2016, when the trust services’ provisions under the eIDAS Regulation entered into application, an electronic signature can only be used by a natural person to “sign”, i.e. -

Esign Law Explained
Electronic Signature Article ESIGN Electronic Commerce and Electronic Signature Law Clarified Copyright © Topaz Systems Inc. All rights reserved. For Topaz Systems, Inc. trademarks and patents, visit www.topazsystems.com/legal. ESIGN Law Clarified Table of Contents Overview ................................................................................................................................... 3 Abstract .................................................................................................................................... 3 Requirements for Legal Contract Enforcement .................................................................... 3 Digital Signature Technologies .............................................................................................. 4 PKI Digital Signatures ........................................................................................................................ 4 Handwritten Electronic Digitized Signatures ....................................................................................... 5 Email, Fax, and Other Simplistic Approaches ..................................................................................... 5 Digital Signature Technology in Open and Closed System Environments ........................ 6 Closed System and PKI ..................................................................................................................... 6 Closed System and Digitized Electronic Signatures .......................................................................... -

The Ultimate Guide to Digital Signatures Comprehensive Answers to the 20 Most Important Questions
The Digital Signature Company The Ultimate Guide to Digital Signatures Comprehensive Answers to the 20 Most Important Questions DocuSign | 855 Folsom St. Suite 939, San Francisco, CA 94107 | Tel. (415) 839-8161 | www.docusign.com Introduction As organizations increasingly adopt paperless processes and automate their document workflows, the “wet ink” signature is rapidly becoming an anachronism in our digital world. Companies and government organizations around the world have invested huge sums in automating their business workflows, yet they still find themselves printing paper for the purpose of obtaining signature approvals. Projects can be held up for days and costs are accrued while documents are mailed between offices, partners, suppliers or customers in order to collect signatures. Professionals often share the concerns voiced by compliance officers over how to ensure the integrity and accountability of electronic documents and records, and by CIOs over how to best secure them. Meanwhile, COOs are concerned with avoiding project delays and CFOs are seeking ways to cut costs associated with paper handling. Digital signatures address each and every one of these concerns. Document Document Hash Private Key Public Key Digital Signature X Signed Document DocuSign | 855 Folsom St. Suite 939, San Francisco, CA 94107 | Tel. (415) 839-8161 | www.docusign.com 1. What are Digital Signatures? Digital signatures, which are often referred to as advanced or standard electronic signatures, take the concept of traditional paper-based signing and turn it into electronic “fingerprints”, or coded messages, which are unique to both the document and the signer and binds the two together. They are based on international standards that guarantee their secure implementation. -

Electronic Signature Algorithms Standard
Electronic Signature Algorithms Standard Version: 1.0 Author: Qatar Public Key Infrastructure Section Document Classification: PUBLIC Published Date: June 2018 Electronic Signature Algorithms Standard Version: 1.0 Page 1 of 13 Classification: Public Document Information Date Version Reviewed By 04/06/2018 1.0 Qatar National PKI Team Electronic Signature Algorithms Standard Version: 1.0 Page 2 of 13 Classification: Public Content 1. Overview ......................................................................................................................................... 4 2. Introduction .................................................................................................................................... 4 1. Objective of the document ......................................................................................................... 4 2. Audience ..................................................................................................................................... 4 3. Security properties of electronic signature .................................................................................... 4 4. Hash algorithms .............................................................................................................................. 4 1. Hash functions ............................................................................................................................ 4 2. Hash function properties ........................................................................................................... -
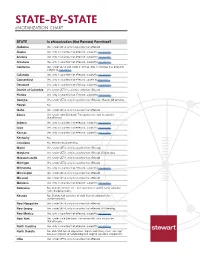
STATE-BY-STATE Enotarization CHART
STATE-BY-STATE eNOTARIZATION CHART STATE Is eNotarization (Not Remote) Permitted? Alabama Yes, under UETA, only in counties that eRecord. Alaska Yes, only in counties that eRecord, subject to regulations. Arizona Yes, only in counties that eRecord, subject to regulations. Arkansas Yes, only in counties that eRecord, subject to regulations. California Yes, under UETA and Code 27391 (e), only in counties that eRecord subject to regulations. Colorado Yes, only in counties that eRecord, subject to regulations. Connecticut Yes, only in counties that eRecord subject to regulations. Delaware Yes, only in counties that eRecord, subject to regulations. District of Columbia Yes, under UETA in counties, only that eRecord. Florida Yes, only in counties that eRecord, subject to regulations. Georgia Yes, under UETA, only in counties that eRecord. eNotary bill pending. Hawaii No. Idaho Yes, under UETA, only in counties that eRecord. Illinois Yes, under state Electronic Transaction Act, only in counties that eRecord. Indiana Yes, only in counties that eRecord, subject to regulations. Iowa Yes, only in counties that eRecord, subject to regulations. Kansas Yes, only in counties that eRecord, subject to regulations. Kentucky No. Louisiana No. eNotary study pending. Maine Yes, under UETA, only in counties that eRecord. Maryland Yes, under UETA, only in counties that eRecord. Bill pending. Massachusetts Yes, under UETA, only in counties that eRecord. Michigan Yes, under UETA, only in counties that eRecord. Minnesota Yes, only in counties that eRecord, subject to regulations. Mississippi Yes, under UETA, only in counties that eRecord. Missouri Yes, under UETA, only in counties that eRecord. Montana Yes, only in counties that eRecord, subject to regulations. -

Notarization Task Force Meeting Minutes June 19, 2019
Notarization Task Force on Best Practices and Verification Standards To Implement Electronic Notarization Wednesday, June 19, 2019 (10:30 a.m. – 1:30 p.m.) James R. Thompson Center 100 West Randolph, Suite 16-504 Chicago, IL 60601 Meeting Minutes 1. Welcome and roll call Chairman Weisbaum called the meeting to order at 10:45 a.m. and asked Micah Miller to take the roll call. The following members were present: Senator Linda Holmes, 42nd District David Weisbaum, Director, Secretary of State Index Department Tiffany Baum (designee for Mike Standley), Secretary of State Dept of Information Technology Andrew Dougherty, Consumer Fraud Bureau, Office of the Attorney General Meredith Mays Espino, Neal Gerber Eisenberg LLP Dan McLean, Illinois Credit Union League Susan Snyder, Corporate Fiduciaries Association of Illinois Matt Farrell, Chicago Association of Realtors Piero Orsi, Illinois Association of Realtors The following members were unable to attend: Representative Stephanie Kifowit, 84th District Senator John Curran, 41st District Ken Matuszewski, Rabicoff Law LLC Amy DeLaney, National Academy of Elder Law Attorneys Megan Peck (designee for Kraig Lounsberry), Community Bankers of Illinois The following individuals were also in attendance (asterisk indicates participation by phone): Ben Jackson, Illinois Bankers Association Brian Wojcicki, Illinois Land Title Association Roger Bickel, Freeborn and Peters LLP *Patrick Quist, Legislative Chair, Illinois Land Title Association *Vanasa Britton, Index Department, Secretary of State’s Office Micah Miller, Programs and Policies Staff, Secretary of State’s Office Amy Williams, Assistant General Counsel, Secretary of State’s Office Dave Fuchs, Programs and Policies Staff, Secretary of State’s Office Chairman Weisbaum recognized that a quorum was present (9 members or more physically present).