SIGNATURE EXAMPLES, 37 CFR 1.4(D)(2) Effective September 21, 2004
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Domain-Specific Pseudonymous Signatures Revisited
Domain-Specific Pseudonymous Signatures Revisited Kamil Kluczniak Wroclaw University of Technology, Department of Computer Science [email protected] Abstract. Domain-Specific Pseudonymous Signature schemes were re- cently proposed for privacy preserving authentication of digital identity documents by the BSI, German Federal Office for Information Secu- rity. The crucial property of domain-specific pseudonymous signatures is that a signer may derive unique pseudonyms within a so called domain. Now, the signer's true identity is hidden behind his domain pseudonyms and these pseudonyms are unlinkable, i.e. it is infeasible to correlate two pseudonyms from distinct domains with the identity of a single signer. In this paper we take a critical look at the security definitions and construc- tions of domain-specific pseudonymous signatures proposed by far. We review two articles which propose \sound and clean" security definitions and point out some issues present in these models. Some of the issues we present may have a strong practical impact on constructions \provably secure" in this models. Additionally, we point out some worrisome facts about the proposed schemes and their security analysis. Key words: eID Documents, Privacy, Domain Signatures, Pseudonymity, Security Definition, Provable Security 1 Introduction Domain signature schemes are signature schemes where we have a set of users, an issuer and a set of domains. Each user obtains his secret keys in collaboration with the issuer and then may sign data with regards to his pseudonym. The crucial property of domain signatures is that each user may derive a pseudonym within a domain. Domain pseudonyms of a user are constant within a domain and a user should be unable to change his pseudonym within a domain, however, he may derive unique pseudonyms in each domain of the system. -

How to Leak a Secret: Theory and Applications of Ring Signatures
How to Leak a Secret: Theory and Applications of Ring Signatures Ronald L. Rivest1, Adi Shamir2, and Yael Tauman1 1 Laboratory for Computer Science, Massachusetts Institute of Technology, Cambridge, MA 02139, 2 Computer Science department, The Weizmann Institute, Rehovot 76100, Israel. Abstract. In this work we formalize the notion of a ring signature, which makes it possible to specify a set of possible signers without re- vealing which member actually produced the signature. Unlike group sig- natures, ring signatures have no group managers, no setup procedures, no revocation procedures, and no coordination: any user can choose any set of possible signers that includes himself, and sign any message by using his secret key and the others' public keys, without getting their approval or assistance. Ring signatures provide an elegant way to leak authoritative secrets in an anonymous way, to sign casual email in a way that can only be veri¯ed by its intended recipient, and to solve other problems in multiparty computations. Our main contribution lies in the presentation of e±cient constructions of ring signatures; the general concept itself (under di®erent terminology) was ¯rst introduced by Cramer et al. [CDS94]. Our constructions of such signatures are unconditionally signer-ambiguous, secure in the random oracle model, and exceptionally e±cient: adding each ring member in- creases the cost of signing or verifying by a single modular multiplication and a single symmetric encryption. We also describe a large number of extensions, modi¯cations and applications of ring signatures which were published after the original version of this work (in Asiacrypt 2001). -

Electronic Signatures in German, French and Polish Law Perspective
Article Electronic signatures in German, French and Polish law perspective DR CHRISTIANE BIEREKOVEN, PHILIP BAZIN AND TOMASZ KOZLOWSKI This article presents some significant apply to the German legislation on electronic issues on the recognition of signatures. electronic signatures with regard to It may be stressed that Germany was the first foreign certificates from the country in the European Union that issued a law perspective of German, French and on electronic, respectively digital, signatures prior to the Electronic Signature Directive. The Act on Polish law. The European Union Digital Signatures came into force on 1 August legislation applies to Germany and 1997 and was restricted to the use of digital France, and has served as a guide signatures only. It had to be amended after the for Polish legislation in the course of Electronic Signature Directive was published, preparations of the accession of because the Directive provides for electronic Poland to the European Union. signatures in general and is not restricted to the There are therefore strong use of digital signatures only. similarities between the legislation I of these countries, but as the French The German legislation example shows, the results may also The Electronic Signature Directive was differ with regard to the material implemented into German law by the “Act on law applicable to a contract. The outlining Conditions for Electronic Signatures and difference between simple and for the Amendment of further Regulations” advanced electronic signature is (Gesetz über Rahmenbedingungen für discussed within the context of elektronische Signaturen und zur Änderung weiterer Vorschriften), hereinafter referred to as French law. “SigG” - of 21 May 2001. -

Basis Technology Unicode対応ライブラリ スペックシート 文字コード その他の名称 Adobe-Standard-Encoding A
Basis Technology Unicode対応ライブラリ スペックシート 文字コード その他の名称 Adobe-Standard-Encoding Adobe-Symbol-Encoding csHPPSMath Adobe-Zapf-Dingbats-Encoding csZapfDingbats Arabic ISO-8859-6, csISOLatinArabic, iso-ir-127, ECMA-114, ASMO-708 ASCII US-ASCII, ANSI_X3.4-1968, iso-ir-6, ANSI_X3.4-1986, ISO646-US, us, IBM367, csASCI big-endian ISO-10646-UCS-2, BigEndian, 68k, PowerPC, Mac, Macintosh Big5 csBig5, cn-big5, x-x-big5 Big5Plus Big5+, csBig5Plus BMP ISO-10646-UCS-2, BMPstring CCSID-1027 csCCSID1027, IBM1027 CCSID-1047 csCCSID1047, IBM1047 CCSID-290 csCCSID290, CCSID290, IBM290 CCSID-300 csCCSID300, CCSID300, IBM300 CCSID-930 csCCSID930, CCSID930, IBM930 CCSID-935 csCCSID935, CCSID935, IBM935 CCSID-937 csCCSID937, CCSID937, IBM937 CCSID-939 csCCSID939, CCSID939, IBM939 CCSID-942 csCCSID942, CCSID942, IBM942 ChineseAutoDetect csChineseAutoDetect: Candidate encodings: GB2312, Big5, GB18030, UTF32:UTF8, UCS2, UTF32 EUC-H, csCNS11643EUC, EUC-TW, TW-EUC, H-EUC, CNS-11643-1992, EUC-H-1992, csCNS11643-1992-EUC, EUC-TW-1992, CNS-11643 TW-EUC-1992, H-EUC-1992 CNS-11643-1986 EUC-H-1986, csCNS11643_1986_EUC, EUC-TW-1986, TW-EUC-1986, H-EUC-1986 CP10000 csCP10000, windows-10000 CP10001 csCP10001, windows-10001 CP10002 csCP10002, windows-10002 CP10003 csCP10003, windows-10003 CP10004 csCP10004, windows-10004 CP10005 csCP10005, windows-10005 CP10006 csCP10006, windows-10006 CP10007 csCP10007, windows-10007 CP10008 csCP10008, windows-10008 CP10010 csCP10010, windows-10010 CP10017 csCP10017, windows-10017 CP10029 csCP10029, windows-10029 CP10079 csCP10079, windows-10079 -

Lesson 3 8,UNBELIEVABLE60 HE SAYS4
L 3 Qotatio M, A, Pnt, S B, O, L L (U), Ssh Now learn the following additional punctuation signs: apostrophe ’ [or] ' ' (dot 3) opening one-cell (non-specific) quotation mark 8 (dots 236) closing one-cell (non-specific) quotation mark 0 (dots 356) opening single quotation mark ‘ [or] ' ,8 (dots 6, 236) closing single quotation mark ’ [or] ' ,0 (dots 6, 356) opening parenthesis ( "< (dots 5, 126) closing parenthesis ) "> (dots 5, 345) opening square bracket [ .< (dots 46, 126) (dots 46, 345) closing square bracket ] .> 3.1 S D Qotatio M [UEB §7.6] In braille, there are several different symbols to represent the various types of print quotation marks (additional information about quotation marks will be studied in Lesson 16). In most cases, the opening and clo one- (-ecific) tatio marks should be used to represent the primary or outer quotation marks in the text, and the two- cell opening and closing single quotation marks should represent the inner quotation marks. Examples: "Unbelievable!" he says. 8,BEIEABE60 HE A4 "I only wrote 'come home soon'," he claims. 3 - 1 8,I E ,8CE HE ,010 HE CAI4 3.2 Arop Follow print for the use of apostrophes. Example: "Tell 'em Sam's favorite music is new—1990's too old." 8,E 'E ,A' FAIE IC I E,-#AIIJ' D40 3.2 A api lette. A capital indicator is always placed immediately before the letter to which it applies. Therefore, if an apostrophe comes before a capital letter in print, the apostrophe is brailled before the capital indicator. Example: "'Twas a brilliant plan," says Dan O'Reilly. -
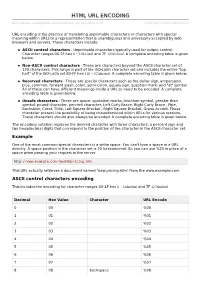
HTML URL Encoding
HHTTMMLL UURRLL EENNCCOODDIINNGG http://www.tutorialspoint.com/html/html_url_encoding.htm Copyright © tutorialspoint.com URL encoding is the practice of translating unprintable characters or characters with special meaning within URLs to a representation that is unambiguous and universally accepted by web browsers and servers. These characters include: ASCII control characters - Unprintable characters typically used for output control. Character ranges 00-1F hex 0 − 31decimal and 7F 127decimal. A complete encoding table is given below. Non-ASCII control characters - These are characters beyond the ASCII character set of 128 characters. This range is part of the ISO-Latin character set and includes the entire "top half" of the ISO-Latin set 80-FF hex 128 − 255decimal. A complete encoding table is given below. Reserved characters - These are special characters such as the dollar sign, ampersand, plus, common, forward slash, colon, semi-colon, equals sign, question mark, and "at" symbol. All of these can have different meanings inside a URL so need to be encoded. A complete encoding table is given below. Unsafe characters - These are space, quotation marks, less than symbol, greater than symbol, pound character, percent character, Left Curly Brace, Right Curly Brace , Pipe, Backslash, Caret, Tilde, Left Square Bracket , Right Square Bracket, Grave Accent. These character present the possibility of being misunderstood within URLs for various reasons. These characters should also always be encoded. A complete encoding table is given below. The encoding notation replaces the desired character with three characters: a percent sign and two hexadecimal digits that correspond to the position of the character in the ASCII character set. -

AIX Globalization
AIX Version 7.1 AIX globalization IBM Note Before using this information and the product it supports, read the information in “Notices” on page 233 . This edition applies to AIX Version 7.1 and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright International Business Machines Corporation 2010, 2018. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents About this document............................................................................................vii Highlighting.................................................................................................................................................vii Case-sensitivity in AIX................................................................................................................................vii ISO 9000.....................................................................................................................................................vii AIX globalization...................................................................................................1 What's new...................................................................................................................................................1 Separation of messages from programs..................................................................................................... 1 Conversion between code sets............................................................................................................. -

List of Approved Special Characters
List of Approved Special Characters The following list represents the Graduate Division's approved character list for display of dissertation titles in the Hooding Booklet. Please note these characters will not display when your dissertation is published on ProQuest's site. To insert a special character, simply hold the ALT key on your keyboard and enter in the corresponding code. This is only for entering in a special character for your title or your name. The abstract section has different requirements. See abstract for more details. Special Character Alt+ Description 0032 Space ! 0033 Exclamation mark '" 0034 Double quotes (or speech marks) # 0035 Number $ 0036 Dollar % 0037 Procenttecken & 0038 Ampersand '' 0039 Single quote ( 0040 Open parenthesis (or open bracket) ) 0041 Close parenthesis (or close bracket) * 0042 Asterisk + 0043 Plus , 0044 Comma ‐ 0045 Hyphen . 0046 Period, dot or full stop / 0047 Slash or divide 0 0048 Zero 1 0049 One 2 0050 Two 3 0051 Three 4 0052 Four 5 0053 Five 6 0054 Six 7 0055 Seven 8 0056 Eight 9 0057 Nine : 0058 Colon ; 0059 Semicolon < 0060 Less than (or open angled bracket) = 0061 Equals > 0062 Greater than (or close angled bracket) ? 0063 Question mark @ 0064 At symbol A 0065 Uppercase A B 0066 Uppercase B C 0067 Uppercase C D 0068 Uppercase D E 0069 Uppercase E List of Approved Special Characters F 0070 Uppercase F G 0071 Uppercase G H 0072 Uppercase H I 0073 Uppercase I J 0074 Uppercase J K 0075 Uppercase K L 0076 Uppercase L M 0077 Uppercase M N 0078 Uppercase N O 0079 Uppercase O P 0080 Uppercase -
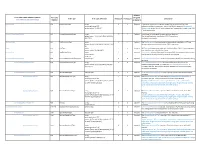
Form 1094-C Schema to Form Crosswalk
Element Form 1094-C XML Schema Elements Form Line Required eFile Type eFile Type Definition minOccurs maxOccurs Description Form1094CUpstreamDetailType Number or Optional SubmissionId N/A SubmissionIdType string 1 1 Required A sequential number (non-negative integer) that uniquely identifies each maxLength value="10" submission within a transmission - every Form 1094-C requires a SubmissionId. pattern value="[1-9][0-9]*" SubmissionId should start at 1 and increment by 1 sequentially for each Form 1094- C in the transmission. OriginalUniqueSubmissionId N/A UniqueSubmissionIdType string 0 1 Optional Global type for the Original Unique Submission Identifier. pattern value="[^\s].[^\s]{1,80}\|[1-9]{1}[0- The UniqueSubmission Identifier for 1094-C is as follows: 9]{0,15}"/> ReceiptId|SubmissionId TestScenarioId N/A TestScenarioIdType string 0 1 Optional The TestScenarioId is only applicable to transmissions submitted to AATS and pattern ([1-9]|[1-9][0-9])C{0,1}-([0-9]|[1-9][0- identifies which test scenario the Form 1094-C represents. 9]) TaxYr N/A YearType string 1 1 Required IRS TaxYr is the tax year for which the data on the Form 1094-C is being submitted. pattern value="[1-9][0-9]{3}"/ Base type for a year in the format of YYYY. CorrectedInd N/A DigitBooleanType string 1 1 Required CorrectedInd indicates if the record is an original (0) or a correction (1) to a record enumerations: that the IRS has already received, processed, and accepted. "0" or" 1" CorrectedSubmissionInfoGrp N/A CorrectedSubmissionInfoGrpType complexType 0 1 Optional CorrectedSubmissionInfoGrp contains Information to identify the submission being corrected. CorrectedUniqueSubmissionId N/A UniqueSubmissionIdType string 1 1 Required CorrectedUniqueSubmissionId is the unique submission identifier of the pattern value="[^\s].[^\s]{1,80}\|[1-9]{1}[0- submission being corrected. -

Instructions for Filling up the Passport Application Form (Diplomatic/ Official)
INSTRUCTIONS FOR FILLING UP THE PASSPORT APPLICATION FORM (DIPLOMATIC/ OFFICIAL) A. GENERAL INSTRUCTIONS This Diplomatic/ Official Passport Application Form, issued by the Government of India, is machine-readable. It will be scanned by the Intelligent Character Recognition (ICR) enabled scanners. Incomplete or inappropriately-filled application form will not be accepted. Please follow the instructions given below while filling the form. Use CAPITAL LETTERS only, throughout the application form, as shown in the image below – Applicant's Given Name Applicant's Given Name s h a s h i S H A S H I Incorrect Correct Use standard fonts and avoid stylized writing. Use black or blue ball point pen only. Do NOT fill the application form with ink-pen or pencil. Write as clearly as possible. Use a pen with a thinnest possible tip. Put a cross ( ) in the boxes where you have to choose one or more options as your answer and leave the other option(s) blank. For example, if your gender is male, put a cross in the box against male as shown in the image below – Do NOT put dots ( ), tick marks ( ), etc, in the boxes, to choose the appropriate option as your answer. Write clearly within the boxes without touching the boundaries. Try and write in the centre of the box, as shown in the image below – Incorrect Correct Leave one box blank after each complete word, while filling up the boxes. Father's Given Name Father's Given Name D E V A N G J I G N E S H D E V A N G J I G N E S H Incorrect Correct Do NOT write anything outside the given boxes. -

COMMON PROBLEMS with CITATION Q: Does the Punctuation Mark Appear Before Or After the Quotation Mark?
Common Problems 1 COMMON PROBLEMS WITH CITATION Always introduce quotations before they appear in your paper. No quotation should stand by itself as a separate sentence. Instead, your introductory phrasing should tie the quotation into the flow of your argument, and you should follow each quotation by explaining why it is important or what point it illustrates. • Bad Example #1: There are many examples of self-analysis in Plato's philosophy. "The unexamined life is not worth living" (Plato 45). • Bad Example #2: Plato thinks people should analyze their own lives. "The unexamined life is not worth living" (Plato 45). • Acceptable Example: Plato thinks people should analyze their own lives: "The unexamined life is not worth living" (Plato 45). [In this example, the author uses a colon to show that a quote follows the first sentence] • Better Example: Plato thinks people should analyze their own lives. As he writes in one dialogue, "The unexamined life is not worth living" (Plato 45). His attitude is a common one among Greek philosophers. Note that in the good examples, the writer doesn't suddenly start off a quotation at the beginning of the sentence, and the writer doesn't leave it hanging, unattached from the surrounding sentences. Instead, the writer attaches it to the previous introductory material with appropriate punctuation, or she adds a short introductory phrase to set the reader up for the quote. She also follows the quote with an explanation of why that quote is important. Q: Does the Punctuation Mark Appear Before or After the Quotation Mark? A: It varies. -
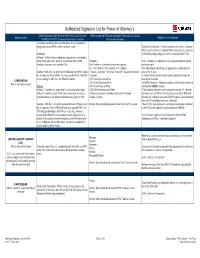
Authorized Signature List for Poas.Xlsx
Authorized Signature List for Power of Attorney’s List the following on the first line of the POA, as well as in the Who may sign the POA and Acceptable Titles to list on Capacity Business Entity Additional Forms Required WITNESS WHEREOF line near the bottom of the form line (last line on form) The legal corporation name and DBA name if the corporation is doing business as (DBA) another company name Corporate Certification – Should someone other than a Corporate Officer sign the POA, a Corporate Officer must sign the Corporate Subsidiary Certification giving said power to the person signing the POA Defined - A wholly owned subsidiary corporation is considered a stand-alone legal entity. As such, a corporate officer of the President 5106 - Additions or updates may be required and should not be subsidiary company must sign the POA. Vice President - authorized to bind the company performed until: I.E. - V.P. Finance, V.P. Customs, V.P. Logistics, • An initial importer bond query is generated to review importer Example - ABC Inc. is a wholly owned subsidiary of Whole Foods Treasurer, Secretary - Secretary Treasurer - Assistant Secretary data on file in ACE Inc. A corporate officer of ABC Inc. must sign the POA. The POA Treasurer • Letter of authorization from the client to update their importer is only binding for ABC Inc., not Whole Foods Inc. CEO Chief Executive Officer record with Customs CORPORATION COO Chief Operation Officer • EIN/IRS Numbers – Obtain acceptable proof from the importer to POA is valid until revoked Division CFO Chief Financial Officer validate their EIN/IRS number.