SYSTEMS ARCHITECTURE and EVALUATION Edited by Michael
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Vodafone Paredes De Coura 2017
DOSSIER DE IMPRENSA VODAFONE PAREDES DE COURA 2017 Vodafone Paredes de Coura Ritmos Edição 2017 Biblioteca Digital Vodafone Vozes da Escrita Vodafone Music Sessions Acções Vodafone Vodafone FM Fest Cool Down Palco Jazz Relva Sobe à Vila Cartaz 2017 Programação por Dias Biografias Contactos 2017 © RITMOS, LDA VODAFONE PAREDES DE COURA 2017 VODAFONE O Vodafone Paredes de Coura está de regresso às margens do Taboão para celebrar a 25.ª edição. paredes DE São 25 anos de história repletos de momentos inesquecíveis. Das atuações COURA memoráveis, ao reencontro entre amigos e ao convívio com a natureza, o festival cresceu e deu fama internacional à vila minhota, que é agora destino de férias de eleição para tantos que a visitam. O Vodafone Paredes de Coura, habitat natural da música, mudou a forma de a ouvir, e viver. Soube despertar tendências, arriscar sonoridades, descobrir novos talentos, consagrar grandes nomes. Uma caminhada de esforços e superações, de provas e de conquistas, de lutas e de vitórias. 25 anos depois, a música continua no centro das atenções de um festival de experiências únicas. A história da música em Portugal não seria a mesma sem o Festival Paredes de Coura. EDIÇÃO 2016 A 24.ª edição materializou o sonho sob a forma de quatro dias de música em comunhão com a natureza, numa celebração conjunta que levou perto de 100 mil pessoas à Praia Fluvial do Taboão. Depois do sucesso da edição de 2015, completamente esgotada, o Vodafone Paredes de Coura continuou a apostar nas melhorias na área do campismo e do anfiteatro natural, que viu o seu espaço ampliado, mas manteve a lotação, o que permitiu receber o público com um cuidado reforçado e proporcionar ainda mais conforto, condições de higiene e segurança. -

"Blessing for the Nations" in the Patriarchal Narratives
THE THFIIE OF "BLESSING FOR THE NATIONS" IN THE PATRIARCHAL NARRATIVES OF GENESIS A thesis submitted in fulfilment of the requirements for the degree of Doctor of Philosophy Department of Biblical Studies University of Sheffield Riang Chea CHEW October, 1982 x ACKNOWLEDGE1ETS To be able to complete the present study is in itself a reflection of the assistance I received. It is therefore with great pleasure I express my appreciation to Mr. David Clines, my supervisor and Reader of the Biblical Studies Department, for his perceptive guidance throughout the period of my research. His kind friendship, understanding, and sacrifice of time, all contributed greatly to the completion of this thesis. In additions I would also like to express my thanks to Drs. Philip Davies and David Gunn, both also of the Biblical Studies Department.. Dr. Davies supervised me and Dr. &unn kindly gave of his time to discuss part of my work, during Mr. CIines' sabbatical leave in 1980/81. A special word of thanks also goes to Mr. Ken Rawlins of Sheffield whom I burdened with the unenviable task of correcting my English. I, of course, remain responsible for all the unidiomatic use of English still present in the study. Without the financial support of the Langham Trust, the present course of studies waulci not have been started and completed. In this, the personal encouragement of the Rev. Dr. John Stott is especially acknowledged. In addition, a number of organisations and friends have also contributed to the cost of maintenance for my family over the past three years. Of these, special thanks go to the consistent support given by the Lee Foundation, Singapore, and the church of which I am a member, both in Singapore and in Sheffield. -

Prospec Or Four Key Things to Look out for This Competition ENT
University of Texas at El Paso DigitalCommons@UTEP The rP ospector Special Collections Department 1-17-2012 The rP ospector, January 17, 2012 UTEP Student Publications Follow this and additional works at: http://digitalcommons.utep.edu/prospector Part of the Journalism Studies Commons, and the Mass Communication Commons Comments: This file is rather large, with many images, so it may take a few minutes to download. Please be patient. Recommended Citation UTEP Student Publications, "The rP ospector, January 17, 2012" (2012). The Prospector. Paper 67. http://digitalcommons.utep.edu/prospector/67 This Article is brought to you for free and open access by the Special Collections Department at DigitalCommons@UTEP. It has been accepted for inclusion in The rP ospector by an authorized administrator of DigitalCommons@UTEP. For more information, please contact [email protected]. The University of Texas at El Paso · January 17, 2012 theassayer of student opinion www.utepprospector.com Student design wins Orbit Gum prospec or Four key things to look out for this competition ENT. 9 semester SPORTS 13 CHEWING ON $5000 Welcome back Miners! WHAT TO WATCH FOR Students struggle with financial burden As debt mounts, grad school seems to be a distant option BY JASMINE AGUILERA consideration credit card, mortgage “It’s quite upsetting when I meet The Prospector or car payments or any other debt someone who gets everything paid when awarding financial aid. for but slacks off and doesn’t appre- According to the Project on Stu- “Last semester, we paid for my ciate it,” De Leon said. “There are dent Debt, two-thirds of college classes with my mom’s credit card,” plenty of other people that actually graduates take out student loans and De Leon said. -

First Headliner Announced for Reading & Leeds Festival 2017 – a Uk Festival Exclusive
EMBARGOED UNTIL 7:45AM THURSDAY 1 DECEMBER 2016 PRESENTS 25TH – 27TH AUGUST 2017, BANK HOLIDAY WEEKEND FIRST HEADLINER ANNOUNCED FOR READING & LEEDS FESTIVAL 2017 – A UK FESTIVAL EXCLUSIVE MUSE MAJOR LAZER, BASTILLE, ARCHITECTS, TORY LANEZ, AT THE DRIVE-IN, GLASS ANIMALS, AGAINST THE CURRENT, ANDY C, DANNY BROWN AND WHILE SHE SLEEPS ALSO CONFIRMED HUNDREDS MORE TO BE ANNOUNCED FOR 2017 http://www.readingandleedsfestival.com Reading & Leeds Festivals announce Muse, in a UK festival exclusive, as the first headliners for next year’s festival, taking place 25-27 August 2017. Stadium rock royalty, Muse are one of the most influential and revered live bands of modern times. Led by the commanding presence of frontman Matt Bellamy, the trio have taken to the biggest stages around the world with their interstellar anthems for over 22 years, and their return to Reading & Leeds promises to be yet another landmark moment in their storied career. Muse commented: "We’re very excited to be playing Reading and Leeds again. More news about our plans for 2017 coming in the new year." Melvin Benn commented: “I’m thrilled to be able to announce Muse as the first headliner for Reading and Leeds 2017. Their incredible live show promises to be an unforgettable performance - we have so much more to announce and I can’t wait to reveal the rest of the line up.” Also confirmed for Reading & Leeds 2017 in a UK festival exclusive, are dancehall-rejuvenators Major Lazer. Diplo, Jillionaire and Walshy Fire have become the soundtrack of modern dance, claiming No.1 records, chart-dominating tracks such as ‘Lean On’ and ‘Cold Water’ as well as live shows packed with genre-mashing moments promising an unrivalled party atmosphere. -

Berkeley C.Pdf
Cardinal Classic XI Packet by Berkeley C Round 4 Tossups 1. He trudges Southern Street searching for a place where he may eat or rest, looking vainly for a job other than menial labor, feeling the "hate stare." (*) His effigy was hung from the center light on Main Street. Hate-filled people whispered that he had been a Negro all along. He is a white man who darkened the color of his skin. FTP, name this man, who retold these events and more in "Black Like Me." Answer: John Howard --Griffin 2. As a teenager he followed the political economy work of Smith and Ricardo, and in 1848 he published his Principles (*) of Political Economy. A disciple of Jeremy Bentham, he became a prominent proponent of utilitarianism. He also penned the treatise The Subjection of Women, manifesting his belief in women's rights. For ten points, name this English author of "On Liberty." Answer: John Stuart Mill 3. It is the complement to Norton's theorem, and states that a linear, (*) active, resistive network which contains independent voltage or current sources can be replaced by a single voltage source and a series resistance. FTP, what is this circuit analysis theorem, which greatly simplifies network analysis under various load conditions? Answer: Thevenin's theorem 4. On Dec 30th, 1853, Santa Anna made one of the biggest blunders of his political career. Because the Treaty of Guadalupe Hidalgo (*) left the western part of the U.S.-Mexico border disputed, and the United States wanted a southern railroad route to the Pacific, 29,640 square miles of land between the Gila River on the north and the current border were sold to the United States for 10 Million Dollars. -
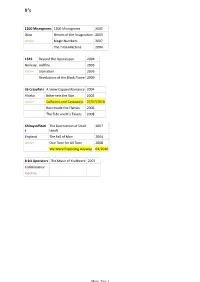
1200 Micrograms 1200 Micrograms 2002 Ibiza Heroes of the Imagination 2003 Active Magic Numbers 2007 the Time Machine 2004
#'s 1200 Micrograms 1200 Micrograms 2002 Ibiza Heroes of the Imagination 2003 Active Magic Numbers 2007 The Time Machine 2004 1349 Beyond the Apocalypse 2004 Norway Hellfire 2005 Active Liberation 2003 Revelations of the Black Flame 2009 36 Crazyfists A Snow Capped Romance 2004 Alaska Bitterness the Star 2002 Active Collisions and Castaways 27/07/2010 Rest Inside the Flames 2006 The Tide and It's Takers 2008 65DaysofStati The Destruction of Small 2007 c Ideals England The Fall of Man 2004 Active One Time for All Time 2008 We Were Exploding Anyway 04/2010 8-bit Operators The Music of Kraftwerk 2007 Collaborative Inactive Music Page 1 A A Forest of Stars The Corpse of Rebirth 2008 United Kingdom Opportunistic Thieves of Spring 2010 Active A Life Once Lost A Great Artist 2003 U.S.A Hunter 2005 Active Iron Gag 2007 Open Your Mouth For the Speechless...In Case of Those 2000 Appointed to Die A Perfect Circle eMOTIVe 2004 U.S.A Mer De Noms 2000 Active Thirteenth Step 2003 Abigail Williams In the Absence of Light 28/09/2010 U.S.A In the Shadow of A Thousand Suns 2008 Active Abigor Channeling the Quintessence of Satan 1999 Austria Fractal Possession 2007 Active Nachthymnen (From the Twilight Kingdom) 1995 Opus IV 1996 Satanized 2001 Supreme Immortal Art 1998 Time Is the Sulphur in the Veins of the Saint... Jan 2010 Verwüstung/Invoke the Dark Age 1994 Aborted The Archaic Abattoir 2005 Belgium Engineering the Dead 2001 Active Goremageddon 2003 The Purity of Perversion 1999 Slaughter & Apparatus: A Methodical Overture 2007 Strychnine.213 2008 Aborym -

Bye, Bye, Miss American Pie? the Supply of New Recorded Music Since Napster
NBER WORKING PAPER SERIES BYE, BYE, MISS AMERICAN PIE? THE SUPPLY OF NEW RECORDED MUSIC SINCE NAPSTER Joel Waldfogel Working Paper 16882 http://www.nber.org/papers/w16882 NATIONAL BUREAU OF ECONOMIC RESEARCH 1050 Massachusetts Avenue Cambridge, MA 02138 March 2011 The title refers to Don McLean’s song, American Pie, which chronicled a catastrophic music supply shock, the 1959 crash of the plane carrying Buddly Holly, Richie Valens, and Jiles Perry “The Big Bopper” Richardson, Jr. The song’s lyrics include, “I saw Satan laughing with delight/The day the music died.” I am grateful to seminar participants at the Carlson School of Management and the WISE conference in St. Louis for questions and comments on a presentation related to an earlier version of this paper. The views expressed in this paper are my own and do not reflect the positions of the National Academy of Sciences’ Committee on the Impact of Copyright Policy on Innovation in the Digital Era or those of the National Bureau of Economic Research. NBER working papers are circulated for discussion and comment purposes. They have not been peer- reviewed or been subject to the review by the NBER Board of Directors that accompanies official NBER publications. © 2011 by Joel Waldfogel. All rights reserved. Short sections of text, not to exceed two paragraphs, may be quoted without explicit permission provided that full credit, including © notice, is given to the source. Bye, Bye, Miss American Pie? The Supply of New Recorded Music Since Napster Joel Waldfogel NBER Working Paper No. 16882 March 2011 JEL No. -

Dancing on the Corpse's Ashes
University of Texas at El Paso DigitalCommons@UTEP Open Access Theses & Dissertations 2011-01-01 "Dancing On The orC pse's Ashes": Analyzing The Emotional Use Of Music And Genre By At The Drive In And How It Communicates Border Identity Crystal A. Robert-Segura University of Texas at El Paso, [email protected] Follow this and additional works at: https://digitalcommons.utep.edu/open_etd Part of the Communication Commons Recommended Citation Robert-Segura, Crystal A., ""Dancing On The orC pse's Ashes": Analyzing The motE ional Use Of Music And Genre By At The Drive In And How It Communicates Border Identity" (2011). Open Access Theses & Dissertations. 2572. https://digitalcommons.utep.edu/open_etd/2572 This is brought to you for free and open access by DigitalCommons@UTEP. It has been accepted for inclusion in Open Access Theses & Dissertations by an authorized administrator of DigitalCommons@UTEP. For more information, please contact [email protected]. “DANCING ON THE CORPSE’S ASHES”: ANALYZING THE EMOTIONAL USE OF MUSIC AND GENRE BY AT THE DRIVE IN AND HOW IT COMMUNICATES BORDER IDENTITY CRYSTAL A. ROBERT-SEGURA DEPARTMENT OF COMMUNICATION APPROVED: __________________________________________ Richard D. Pineda, Ph.D., Chair __________________________________________ Stacey Sowards, Ph.D __________________________________________ Dennis Bixler-!"#$%&', Ph.D. __________________________________________ Patricia D. Witherspoon, Ph.D. Dean of the Graduate School( Copyright © by Crystal Robert-Segura 2011 “DANCING ON THE CORPSE’S ASHES”: ANALYZING THE EMOTIONAL USE OF MUSIC AND GENRE BY AT THE DRIVE IN AND HOW IT COMMUNICATES BORDER IDENTITY. By CRYSTAL A. ROBERT-SEGURA THESIS Presented to the Faculty of the Graduate School of The University of Texas at El Paso in Partial Fulfillment of the Requirements for the Degree of MASTER OF ARTS Department of Communication THE UNIVERSITY OF TEXAS AT EL PASO May 2011 ACKNOWLEDGEMENTS First and foremost I would like to thank my thesis advisor, Dr. -
UCLA UCLA Pacific Basin Law Journal
UCLA UCLA Pacific Basin Law Journal Title What's Law Got to Do with It? Legal Institutions and Economic Reform in China Permalink https://escholarship.org/uc/item/7vc208st Journal UCLA Pacific Basin Law Journal, 10(1) Author Clarke, Donald C. Publication Date 1991 DOI 10.5070/P8101021983 Peer reviewed eScholarship.org Powered by the California Digital Library University of California ARTICLES WHAT'S LAW GOT TO DO WITH IT? LEGAL INSTITUTIONS AND ECONOMIC REFORM IN CHINA Donald C. Clarke* TABLE OF CONTENTS I. INTRODUCTION ................................. 2 II. BACKGROUND TO REFORM .................... 4 A. Economic Reform in China ...................... 4 B. Center Versus Region in the Chinese Polity ....... 13 III. THE ROLE OF LAW IN ECONOMIC REFORM.. 15 A. What's So Special About Legal Rules? ........... 15 B. Institutionsfor Making and Enforcing Rules ..... 17 IV. CHARACTERISTICS OF LEGAL RULES ......... 23 A. Who Is Supposed to "Obey" the Rule? ........... 23 B. Who Promulgated the Rule and How Authoritative Is It? ........................................... 26 C. Who Is to Enforce the Rule and How? ........... 30 D. Can the Rule Really Be Enforced?............... 33 Assistant Professor of Law, University of Washington School of Law. Princeton University, A.B., 1977; School of Oriental and African Studies, University of London, M.Sc., 1983; Harvard Law School, J.D., 1987. This Article began as a paper written as part of an American-European-Chinese joint project researching reforms in the ownership system of Chinese state-owned enter- prises. The project is supported by the Ford Foundation and the Institute of Economics of the Chinese Academy of Social Sciences. Citations in the footnotes make apparent but understate my debt to Barry Naughton of the University of California at San Diego for my understanding of the Chinese economy. -

THE Norton and Becker Win Primary
Going to the Drive-In Molly's Club With its latest release, At The Drive-In Members of the mysterious Molly's Club Tuesday establishes itself as one of the most intense respond to yesterday's article and further punk-rock bands in America today. explain the club's unique organization. FEBRUARY 13, Scene + page 13 Viewpoint+ page 10 2001 THE The Independent Newspaper Serving Notre Dame and Saint Mary's VOL XXXIV NO. 86 HTTP://OHSERVER.N D.EDU Norton and Becker win primary • Smith/Andre dent of elections John Bauters this year and we're happy informed the six tickets that simply to make it to the run 2001 Primary Elections ticket comes in a Brooke Norton and Brian off." close third Mascona would face Ryan Last year's student body Results Becker and Nikki McCord in elections included several By LAURA ROMPF Thursday's run-off election. campaign violations. a dis Assistant News Editor "I was really excited to hear qualification and an appeal. the results," said presidential but Bauters said this year's candidate Brooke Norton, election has run smoothly so Except for the 30 seconds it whose ticket received 42 per far. took to fill out a ballot, cent of the vote. "I am looking "The reason this year's Monday was normal for most forward to a hard week." election has been so good is students. But for the 12 can R y a n because we have quality can didates Becker, didates across the board," running for whose tick Bauters said. "The Notre student et received Dame student body had the body presi 23 percent most difficult decision it's had dent and of the vote, in years." vice presi said he is Bauters said election sta d e n t , satisfied tions in each dorm closed by Monday with the 7 p.m. -

Západočeská Univerzita V Plzni Fakulta Pedagogická Bakalářská
Západočeská univerzita v Plzni Fakulta pedagogická Bakalářská práce 2014 Filip Fendrych ZÁPADOČESKÁ UNIVERZITA V PLZNI FAKULTA PEDAGOGICKÁ KATEDRA HUDEBNÍ KULTURY Hudební styl post-hardcore BAKALÁŘSKÁ PRÁCE Filip Fendrych Specializace v pedagogice, obor Popularizace hudební kultury Vedoucí práce: doc. Mgr. Tomáš Kun, Ph.D. Plzeň, 2014 Prohlašuji, že jsem bakalářskou práci vypracoval(a) samostatně s použitím uvedené literatury a zdrojů informací. Plzeň, 30. 6. 2014 ................................................................ vlastnoruční podpis Poděkování Rád bych poděkoval vedoucímu své bakalářské práce panu doc. Mgr. Tomáši Kuhnovi, Ph.D. za příkladné vedení práce, vstřícnost a cenné rady při vypracovávání mé bakalářské práce. OBSAH ÚVOD ................................................................................................................................................. 1 1 VZNIK HUDEBNÍHO STYLU POST-HARDCORE......................................................... 2 1.1 STRUČNÁ HISTORIE HARDCOROVÉ SCÉNY ........................................................................... 3 1.1.1 Životní styl ................................................................................................................ 5 1.1.2 Hardcore a politika .................................................................................................. 7 1.1.3 Móda ........................................................................................................................ 8 1.1.4 Taneční styl ............................................................................................................. -

When I Was Sixteen I Wanted to Be Graham Coxon When I Was Sixteen I Wanted to Be Graham Coxon
When I was Sixteen I wanted to be Graham Coxon When I was Sixteen I wanted to be Graham Coxon Adam Crosland Copyright (c) Adam Crosland 2014 The right of Adam Crosland to be identified as the author of the work has been asserted by him in accordance with the Copyright, Designs and Patents Act 1988 All rights reserved. No part of this publication may may be reproduced without prior written consent of the author. Some names and identities have been changed to protect the privacy of the individuals involved. Pond Life Press 2014 www.adamcrosland.com For Dan, Nath and Al 1 When I was sixteen I wanted to be Graham Coxon. All of my friends wanted to be Noel Gallagher, but I just didn't like Noel, or Oasis. Graham was different. He wore geek glasses, odd t-shirts and made a racket on the guitar. Graham was ace. Blur were clever and cool. The first time I took notice of Graham was when their eponymously titled fifth album 'Blur' came out. To be honest, I hated Blur up until them, cos I thought they were too laddy and poppy and everyone liked 'em. They were for the masses. I was a Prince fan, and a proud elitist as he was unpopular with all my teenage mates because he looked a bit gay. And so what if he was. But he wasn't gay. He talked about (vaginal) sex all the time and played mean guitar. But they didn't know that. Anyway, back to Graham. So there Blur were – and they'd changed.