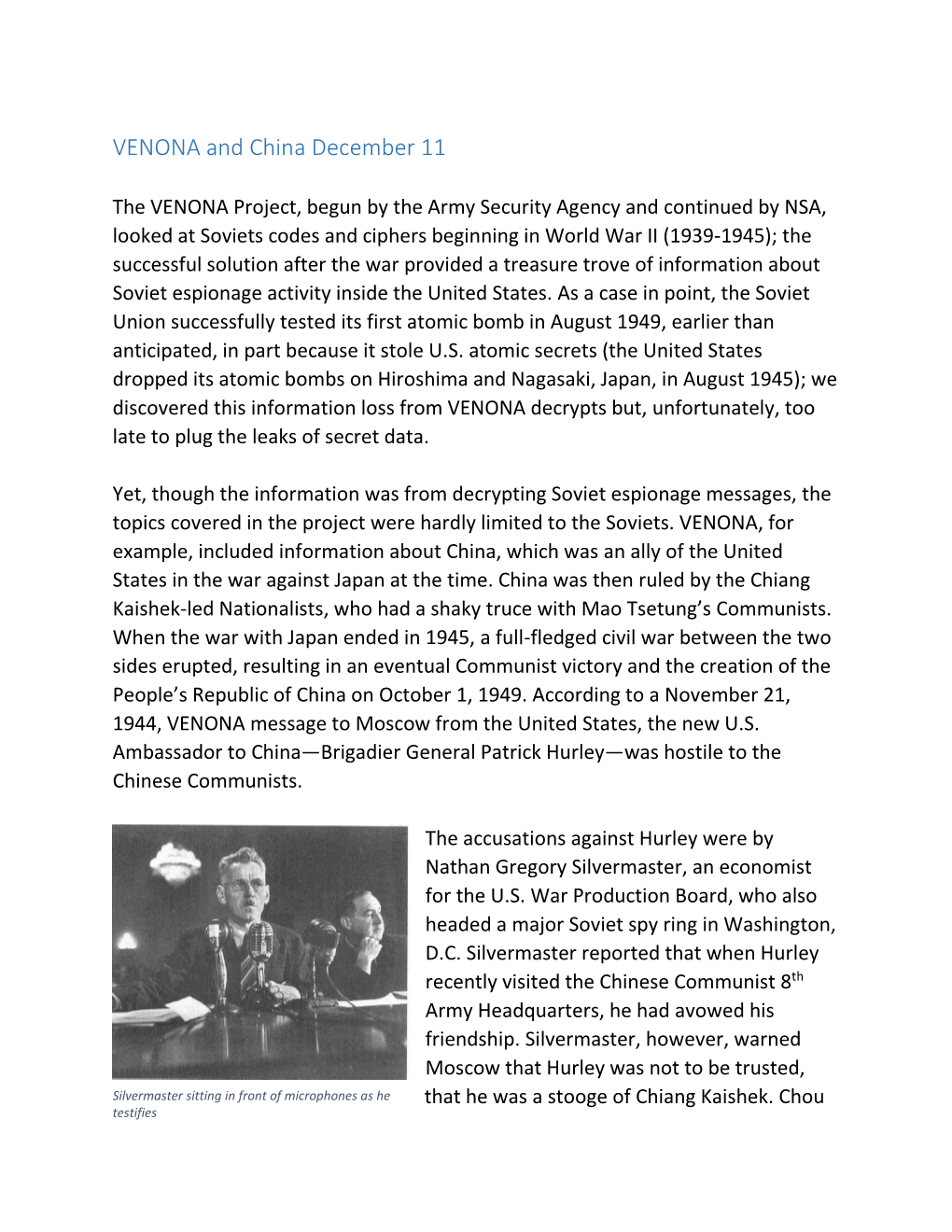
VENONA and China December 11
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

National Security Agency
Coordinates: 39°6′32″N 76°46′17″W National Security Agency The National Security Agency (NSA) is a national-level intelligence agency of the United National Security Agency States Department of Defense, under the authority of the Director of National Intelligence. The NSA is responsible for global monitoring, collection, and processing of information and data for foreign and domestic intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems.[8][9] The NSA relies on a variety of measures to accomplish its Seal of the National Security Agency mission, the majority of which are clandestine.[10] Originating as a unit to decipher coded communications in World War II, it was officially formed as the NSA by President Harry S. Truman in 1952. Since then, it has become the largest of the U.S. intelligence organizations in terms of Flag of the National Security Agency personnel and budget.[6][11] The NSA currently conducts worldwide mass data collection and has been known to physically bug electronic systems as one method to this end.[12] The NSA is also alleged to have been behind such attack software as Stuxnet, which severely damaged Iran's nuclear program.[13][14] The NSA, alongside the Central Intelligence Agency (CIA), maintains a physical presence in many countries across the globe; the CIA/NSA joint Special Collection Service (a NSA Headquarters, Fort Meade, Maryland highly classified intelligence team) inserts eavesdropping devices in high value targets (such Agency overview as presidential palaces or embassies). -

ABSTRACT Title of Document: from the BELLY of the HUAC: the RED PROBES of HOLLYWOOD, 1947-1952 Jack D. Meeks, Doctor of Philos
ABSTRACT Title of Document: FROM THE BELLY OF THE HUAC: THE RED PROBES OF HOLLYWOOD, 1947-1952 Jack D. Meeks, Doctor of Philosophy, 2009 Directed By: Dr. Maurine Beasley, Journalism The House Un-American Activities Committee, popularly known as the HUAC, conducted two investigations of the movie industry, in 1947 and again in 1951-1952. The goal was to determine the extent of communist infiltration in Hollywood and whether communist propaganda had made it into American movies. The spotlight that the HUAC shone on Tinsel Town led to the blacklisting of approximately 300 Hollywood professionals. This, along with the HUAC’s insistence that witnesses testifying under oath identify others that they knew to be communists, contributed to the Committee’s notoriety. Until now, historians have concentrated on offering accounts of the HUAC’s practice of naming names, its scrutiny of movies for propaganda, and its intervention in Hollywood union disputes. The HUAC’s sealed files were first opened to scholars in 2001. This study is the first to draw extensively on these newly available documents in an effort to reevaluate the HUAC’s Hollywood probes. This study assesses four areas in which the new evidence indicates significant, fresh findings. First, a detailed analysis of the Committee’s investigatory methods reveals that most of the HUAC’s information came from a careful, on-going analysis of the communist press, rather than techniques such as surveillance, wiretaps and other cloak and dagger activities. Second, the evidence shows the crucial role played by two brothers, both German communists living as refugees in America during World War II, in motivating the Committee to launch its first Hollywood probe. -

Communicator
DOCID: 3682074 SECRET Vol III, No. 40 10October1995 A Note From the Director (U} fPO~ Presidential Decision Directive (PDD) 35, signed earlier this year, represents the President's highest national intelligence priorities and is intended to chart the course of Intelligence Community (IC) actions in programming, collection, analysis, reporting, resource allocation, and other related areas. During his Town Meeting here in August, the DC!, Dr. Deutch. echoed these objectives as he discussed his perception of the post-Cold War priorities of the IC. tFOUOf It is critical that every member of the NSA workforce be familiar with the provisions of PDD-35, and understand its impact on the Agency's mission. Furthermore, every effort should be made to ensure that all overview briefings, background papers, mission statements, etc., are updated to reflect a focus consistent with the Directive. 1'POU01 The following article highlights key provisions of PDD-35. I urge you to review it carefully and contact N5P, 963-3247s, with any related questions. Very Respecifully, VADM J.M. McConnell ~As INTELLIGENCE national security takes on a broader definition in the post-Cold War era, intelligence must address a wider range of threats and policy needs. PRIORITIES - In addition to maintaining its global perspective, the Intelligence Community EXCERPTS must refine and focus its collection on information unavailable to the policymaker by other means or from other sources. The Community's tactical FROM PDD-35 and strategic analytic efforts should provide a coherent framework that (u) systematically incorporates intelligence to help senior U.S. officials identify and overcome potential challenges to the nation's military. -

Historical Dictionary of International Intelligence Second Edition
The historical dictionaries present essential information on a broad range of subjects, including American and world history, art, business, cities, countries, cultures, customs, film, global conflicts, international relations, literature, music, philosophy, religion, sports, and theater. Written by experts, all contain highly informative introductory essays on the topic and detailed chronologies that, in some cases, cover vast historical time periods but still manage to heavily feature more recent events. Brief A–Z entries describe the main people, events, politics, social issues, institutions, and policies that make the topic unique, and entries are cross- referenced for ease of browsing. Extensive bibliographies are divided into several general subject areas, providing excellent access points for students, researchers, and anyone wanting to know more. Additionally, maps, pho- tographs, and appendixes of supplemental information aid high school and college students doing term papers or introductory research projects. In short, the historical dictionaries are the perfect starting point for anyone looking to research in these fields. HISTORICAL DICTIONARIES OF INTELLIGENCE AND COUNTERINTELLIGENCE Jon Woronoff, Series Editor Israeli Intelligence, by Ephraim Kahana, 2006. Russian and Soviet Intelligence, by Robert W. Pringle, 2006. Cold War Counterintelligence, by Nigel West, 2007. World War II Intelligence, by Nigel West, 2008. Sexspionage, by Nigel West, 2009. Air Intelligence, by Glenmore S. Trenear-Harvey, 2009. Middle Eastern Intelligence, by Ephraim Kahana and Muhammad Suwaed, 2009. German Intelligence, by Jefferson Adams, 2009. Ian Fleming’s World of Intelligence: Fact and Fiction, by Nigel West, 2009. Naval Intelligence, by Nigel West, 2010. Atomic Espionage, by Glenmore S. Trenear-Harvey, 2011. Chinese Intelligence, by I. C. -

Project VENONA: Breaking the Unbreakable Code
Georgia Southern University Digital Commons@Georgia Southern University Honors Program Theses 2020 Project VENONA: Breaking the Unbreakable Code Cassandra Hankin Georgia Southern University Follow this and additional works at: https://digitalcommons.georgiasouthern.edu/honors-theses Part of the History Commons Recommended Citation Hankin, Cassandra, "Project VENONA: Breaking the Unbreakable Code" (2020). University Honors Program Theses. 471. https://digitalcommons.georgiasouthern.edu/honors-theses/471 This thesis (open access) is brought to you for free and open access by Digital Commons@Georgia Southern. It has been accepted for inclusion in University Honors Program Theses by an authorized administrator of Digital Commons@Georgia Southern. For more information, please contact [email protected]. Project VENONA: Breaking the Unbreakable Code An Honors Thesis submitted in partial fulfillment of the requirements for Honors in History. By Cassandra Hankin Under the mentorship of Dr. Bill Allison ABSTRACT Project VENONA was a top-secret counterintelligence program initiated by the United States Army Signals Intelligence Service during World War II. VENONA was established to decipher intercepted Soviet communications and break the “unbreakable” Soviet code system. Examining Project VENONA and its discoveries is vital to understanding the history of the early Cold War. Thesis Mentor:________________________ Dr. Bill Allison Honors Director:_______________________ Dr. Steven Engel April 2020 Department of History University Honors Program Georgia Southern University 2 Acknowledgements There are many people I’d like to thank for helping me during the year and a half I worked on this project. For helping me through the research and writing process, I would like to thank Dr. Bill Allison, who never gave up on me or my project. -

NSA-FOIACASELOG-2016.Pdf
This document is made available through the declassification efforts and research of John Greenewald, Jr., creator of: The Black Vault The Black Vault is the largest online Freedom of Information Act (FOIA) document clearinghouse in the world. The research efforts here are responsible for the declassification of hundreds of thousands of pages released by the U.S. Government & Military. Discover the Truth at: http://www.theblackvault.com NATIONAL SECURITY AGENCY CENTRAL SECURITY SERVICE FORT GEORGE G. MEADE, MARYLAND 20755-6000 FOIA Case: 100503A 4 April 2017 JOHN GREENEWALD Dear Mr. Greenewald: This responds to your Freedom of Information Act (FOIA) request dated 1 January 2017 which was received by this office on 2 January 2017, for "a copy of the FOIA case log for calendar year 2016." For purposes of this request and based on the information you provided in your letter, you are considered an "all other" requester. As such, you are allowed 2 hours of search and the duplication of 100 pages at no cost. Since processing fees were minimal, no fees were assessed. Your request has been processed under the FOIA, and the logs for calendar year 2016 are enclosed, along with a FOIA Case Dispositions reference sheet that explains the final case dispositions. Please be advised that the logs do not contain the number of pages released. They contain a final disposition if the case was closed at the time the logs were created. If there is no final disposition, the case was still pending at the time the logs were created. Certain information has been deleted from the enclosures. -
Assessing Hard-Target Espionage in the Cyber Era Kyle S. Cunliffe Thesis Submitt
An existential crisis and a golden opportunity? Assessing hard-target espionage in the cyber era Kyle S. Cunliffe Thesis submitted in fulfilment of the requirements for the degree of PhD Department of International Politics Aberystwyth University January 18th 2021 Summary Cyberspace is transforming global society. Its effects on states, intelligence, and national security are the subject of much comment, but its relationship with espionage, or human intelligence, remains under-researched to an alarming degree. At a time when the British-US intelligence community is making headway in cyberspace, necessitated by emerging threats and rising nation-state agendas, this is a glaring omission. The strategic imperatives of Russia and China have provoked a reorientation by the British SIS and the US CIA, turning resources back towards nation-state ‘hard targets’. Yet these hard target states are investing resources in innovative surveillance practices, tools that fundamentally threaten intelligence officers’ ability to travel freely or acquire the increasingly important human sources (agents) of espionage. As the operations of British-US intelligence personnel become more threatened in physical terms, espionage agencies now focus their attention towards cyberspace, where innovation opens up new opportunities in tradecraft. By turning to cyberspace to conduct tradecraft, particularly in the recruitment and handling of spies, espionage’s success and failure is now entwined with the value of innovation, and as consequence, cyber-enabled tradecraft is entwined with the present and future of Western security. However, the value of cyberspace to espionage’s sources and methods remains ambiguous, receiving only limited study. Views put forward by a small cadre of mostly seasoned practitioners, express both powerful enthusiasm and debilitating cynicism, reflecting a dichotomy of opinions that have not yet been addressed. -
Read the Introduction (Pdf)
Introduction N WEDNESDAY, June 29, 1955, the Senate Internal Security Sub- committee met in the Caucus Room where the fl amboyant Wis- O consin senator Joseph McCarthy had held his most sensational hearings in 1953 and 1954. Led by Mississippi Democrat James Eastland and undeterred by McCarthy’s political downfall, the subcommittee began an unprecedented investigation of American journalism by delving into alleged Communist infi ltration of some of the nation’s most prominent newspapers. Committee members saw the daily press as a prime Soviet target for propaganda and infi ltration because journalists could often access sensitive information and because they infl uenced public opinion.1 The Eastland committee, as the subcommittee was popularly known, intended to ask selected reporters and editors about any involvement they may have had with the Communist Party, but the actual questioning went much further. The committee asked about their political interests and their personal thoughts and beliefs. Members questioned newspaper editorial policies and hiring practices, areas that were thought to be sacrosanct under the First Amendment. That McCarthy-era inquest reverberated in the summer of 2005 when a federal prosecutor ordered several journalists to identify the sources whose disclosures had led to the publication of a CIA agent’s name. New York Times reporter Judith Miller refused but others complied. She spent eighty-fi ve days in jail and briefl y became a symbol of courageous com- mitment to protecting First Amendment rights, as the media defi ned them. 0001-039_Intro-Ch02_P2R1.indd01-039_Intro-Ch02_P2R1.indd 1 44/18/07/18/07 112:30:232:30:23 PPMM 2 INTRODUCTION The core issue was the same as it had been fi fty years earlier: government power, exercised in the name of national security, to compel journalists to testify and reveal confi dences. -

The Changing Face of the NCMF
The Link BULLETIN OF THE NATIONAL CRYPTOLOGIC MUSEUM FOUNDATION, INC. VOLUMES 9, NO. 3 - , NO. 2, COMPOSITE Summer 2008 THe CHANGING FAce of THe NCMF Events of the past year have moved too quickly for the slow pace of publication of The Link. Issues intended for publication covering Fall 2006 and Winter 2006-2007 have, accordingly, been “pulled back” from the printer and – to adopt the term recently applied to military action in Iraq – we are “surging” by consolidating about a year and a half of content into a single composite issue. That requires a great deal of compression and omission, even to “hit the highlights.” We apologize in advance for the omitted coverage. In return, we plan next to introduce a new look, with color photographs, as the beginning of some further experiments to improve our communication with you, our members and readers. We thank our ambidextrous colleague, John Garcia, and his associates and corporate sponsors for the interim issuance of the occasional “NCMF Newsletter,” mailed to you. Our webmaster, Bob Bowie, Bill Saadi, our website coordinator, and others are pondering changes in the NCMF web site. Thanks also go to occasional Link contributors Ray Schmidt, David Hamer, “cub reporter” Mary Faletto, Kirsten Eland, Jim Boone, Prof. Mark Sommer, and others whose by-lines have appeared. They represent the vanguard of what we hope will be a plethora of “new” (and familiar) names as we invite others of you to remember (as we reminded you in Volume 1, Number 1 ten years ago) that, by our old definition, a “link” should go both ways. -

National Security Agency 60 Years of Defending Our Nation
National Security Agency 60 Years of Defending Our Nation National Security Agency Defending Our Nation. Securing The Future 60 Years of Defending Our Nation 60 Years of Defending Our Nation National Security Agency, circa 1950s. n November 4, 2012, the National Security Agency (NSA) celebrates its 60th anniversary of providing critical information to U.S. decisionmakers and Armed Forces personnel in Odefense of our Nation. NSA has evolved from a staff of approximately 7,600 military and civilian employees housed in 1952 in a vacated school in Arlington, VA, into a workforce of more than 30,000 demographically diverse men and women located at NSA headquarters in Ft. Meade, MD, in four national Cryptologic Centers, and at sites throughout the world. While the mission to defend the Nation against all adversaries has not changed, the adversaries have changed considerably. During the Cold War, NSA’s primary focus was on the Soviet challenge, punctuated by tense crises, such as the one in Cuba in 1962. After the breakup of the Soviet Union, the adversary was less likely to be wearing the uniform of a specific country. In fact, today our greatest threat may be a lone person using a computer. Throughout its six decades, NSA has pursued its mission by employing smart, committed, and courageous people, developing innovative technology, partnering with allied nations, and collaborating with our DoD and IC colleagues. Our commitment to upholding the law of the Nation and protecting the civil liberties of its people has never wavered. On behalf of the dedicated employees of the National Security Agency, we are pleased to present this publication that tells the fascinating story of NSA – 60 years of “Defending Our Nation and Securing The Future.” We have only just begun. -

Introduction Background How It Works the VENONA Breakthrough
By Cindy Flores, Hyeok Jung Kim, Dalia Moradi, Abanob Saleh, Xi Ye You Seminar 3: Science & Technology of NYC, Professor Kent D. Boklan Introduction Significance How It Works On February 1, 1943, a small group of code breakers of the U.S. Army’s Importance of the Venona Project The Code (Vernam Cipher) and How it Works Signal Intelligence Service (SIS) launched the VENONA Project, a secret • Exposed the Soviet spy ring and information about the atomic bomb • Proven to be mathematically secure under ideal implementation by counterintelligence program to decrypt and exploit communication by the • Lasted from 1943 to 1980, declassified in 1995- from World War 2 Claude Shannon Soviet Union. throughout the Cold War (1947-1991) 1) Represent plain text into numbers (alphabet positioning.. ie: A=1) • Exposed Julius and Ethel Rosenberg for espionage and conspiracy to 2) Create a randomly generated key that is the same length as the plain Background provide atomic secrets to the USSR. As a result, they were executed text by electric chair in 1953. 3) Combine the plaintext and random key using XOR or modular addition History • They were implicated by their in-laws Ruth and David Greenglass, 4) Convert the numbers back into cipher text • The code breakers were named “Arlington Hall” after their communists who were also Soviet spies 5) To get back to the plain text, XOR the key again or subtract using headquarters in Virginia • Alger Hiss was a former U.S. State Department official who was modular arithmetic to get the ciphertext. • “Venona” was the code word for the project convicted of perjury in 1950 for involvement in a communist • The SIS led to creation of the National Security Agency (NSA) espionage ring. -

National Security Agency 1 National Security Agency
National Security Agency 1 National Security Agency National Security Agency Seal of the National Security Agency Flag of the National Security Agency Agency overview Formed November 4, 1952 Preceding Agency Armed Forces Security Agency Jurisdiction United States of America Headquarters Fort Meade, Maryland, U.S. Employees Classified Annual budget Classified Agency executives General Keith B. Alexander, U.S. Army, Director of the National Security Agency John C. Inglis, Deputy Director of the National Security Agency Parent Agency United States Department of Defense Website [1] www.nsa.gov The National Security Agency (NSA) is a cryptologic intelligence agency of the United States Department of Defense responsible for the collection and analysis of foreign communications and foreign signals intelligence, as well as protecting U.S. government communications and information systems,[] which involves information security and cryptanalysis/cryptography. The NSA is directed by at least a lieutenant general or vice admiral. NSA is a key component of the U.S. Intelligence Community, which is headed by the Director of National Intelligence. The Central Security Service is a co-located agency created to coordinate intelligence activities and co-operation between NSA and other U.S. military cryptanalysis agencies. The Director of the National Security Agency serves as the Commander of the United States Cyber Command and Chief of the Central Security Service.[2] By law, NSA's intelligence gathering is limited to foreign communications, although domestic incidents such as the NSA warrantless surveillance controversy have occurred. National Security Agency 2 History The National Security Agency's predecessor was the Armed Forces Security Agency (AFSA), created on May 20, 1949.[3] This organization was originally established within the U.S.