A Session Layer Design to Secure the Internet
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

OSI Model and Network Protocols
CHAPTER4 FOUR OSI Model and Network Protocols Objectives 1.1 Explain the function of common networking protocols . TCP . FTP . UDP . TCP/IP suite . DHCP . TFTP . DNS . HTTP(S) . ARP . SIP (VoIP) . RTP (VoIP) . SSH . POP3 . NTP . IMAP4 . Telnet . SMTP . SNMP2/3 . ICMP . IGMP . TLS 134 Chapter 4: OSI Model and Network Protocols 4.1 Explain the function of each layer of the OSI model . Layer 1 – physical . Layer 2 – data link . Layer 3 – network . Layer 4 – transport . Layer 5 – session . Layer 6 – presentation . Layer 7 – application What You Need To Know . Identify the seven layers of the OSI model. Identify the function of each layer of the OSI model. Identify the layer at which networking devices function. Identify the function of various networking protocols. Introduction One of the most important networking concepts to understand is the Open Systems Interconnect (OSI) reference model. This conceptual model, created by the International Organization for Standardization (ISO) in 1978 and revised in 1984, describes a network architecture that allows data to be passed between computer systems. This chapter looks at the OSI model and describes how it relates to real-world networking. It also examines how common network devices relate to the OSI model. Even though the OSI model is conceptual, an appreciation of its purpose and function can help you better understand how protocol suites and network architectures work in practical applications. The OSI Seven-Layer Model As shown in Figure 4.1, the OSI reference model is built, bottom to top, in the following order: physical, data link, network, transport, session, presentation, and application. -

OSI Model: the 7 Layers of Network Architecture
OSI Model: The 7 Layers of Network Architecture The Open Systems Interconnection (OSI) Reference Model is a conceptual framework that describes functions of the networking or telecommunication system independently from the underlying technology infrastructure. It divides data communication into seven abstraction layers and standardizes protocols into appropriate groups of networking functionality to ensure interoperability within the communication system regardless of the technology type, vendor, and model. The OSI model was originally developed to facilitate interoperability between vendors and to define clear standards for network communication. However, the olderTCP/IP model remains the ubiquitous reference framework for Internet communications today. The 7 layers of the OSI model This image illustrates the seven layers of the OSI model. Below, we’ll briefly describe each layer, from bottom to top. 1. Physical The lowest layer of the OSI model is concerned with data communication in the form of electrical, optic, or electromagnetic signals physically transmitting information between networking devices and infrastructure. The physical layer is responsible for the communication of unstructured raw data streams over a physical medium. It defines a range of aspects, including: Electrical, mechanical, and physical systems and networking devices that include specifications such as cable size, signal frequency, voltages, etc. Topologies such as Bus, Star, Ring, and Mesh Communication modes such as Simplex, Half Duplex, and Full Duplex Data transmission performance, such as Bit Rate and Bit Synchronization Modulation, switching, and interfacing with the physical transmission medium Common protocols including Wi-Fi, Ethernet, and others Hardware including networking devices, antennas, cables, modem, and intermediate devices such as repeaters and hubs 2. -

Medium Access Control Layer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay (historical) ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus (historical) ● Network Infrastructure ● Token Ring (historical) ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● Protocols used to determine who gets next access to the channel Data Link Layer ● Medium Access Control (MAC) sublayer Physical Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Range ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access .. -

ADD WES/OSN CH 11 5Thprf
THE PRESENTATION AND 11 SESSION LAYERS The presentation and session layers collaborate to provide many of the distributed-processing capabilities presented to user elements by the ser- vice elements of the application layer; for this reason, they are discussed together. Presentation Layer Chapter 4 describes how ASN.1 provides the application programmer with a tool for creating data structures that are syntactically independent from the way in which data are stored in a computer and from the way in which they are transferred between computer systems. Transforming these abstract syntaxes into “concrete” data structures appropriate for a given operating system (e.g., UNIX, DOS, VMS, MVS) is typically han- dled by tools such as ASN.1 compilers. The task of preserving the seman- tics of the data exchanged between a sender and receiver across an OSI network is handled by the presentation layer, which performs the trans- formations from the local (concrete) syntax used by each application entity to a common transfer syntax. This leads us to the discussion of the notion of a presentation context set. Context Set The presentation layer is responsible for managing the transfer syntaxes Definition associated with the set of abstract syntaxes that will be used by applica- tion entities as they exchange information across a presentation connec- tion. As part of presentation connection establishment, application enti- ties must be sure that the presentation layer can support a transfer syntax 247 248 OPEN SYSTEMS NETWORKING: TCP/IP AND OSI for every abstract syntax required by the distributed-processing applica- tion(s) that will use this connection. -

1.2. OSI Model
1.2. OSI Model The OSI model classifies and organizes the tasks that hosts perform to prepare data for transport across the network. You should be familiar with the OSI model because it is the most widely used method for understanding and talking about network communications. However, remember that it is only a theoretical model that defines standards for programmers and network administrators, not a model of actual physical layers. Using the OSI model to discuss networking concepts has the following advantages: Provides a common language or reference point between network professionals Divides networking tasks into logical layers for easier comprehension Allows specialization of features at different levels Aids in troubleshooting Promotes standards interoperability between networks and devices Provides modularity in networking features (developers can change features without changing the entire approach) However, you must remember the following limitations of the OSI model: OSI layers are theoretical and do not actually perform real functions. Industry implementations rarely have a layer‐to‐layer correspondence with the OSI layers. Different protocols within the stack perform different functions that help send or receive the overall message. A particular protocol implementation may not represent every OSI layer (or may spread across multiple layers). To help remember the layer names of the OSI model, try the following mnemonic devices: Mnemonic Mnemonic Layer Name (Bottom to top) (Top to bottom) Layer 7 Application Away All Layer 6 Presentation Pizza People Layer 5 Session Sausage Seem Layer 4 Transport Throw To Layer 3 Network Not Need Layer 2 Data Link Do Data Layer 1 Physical Please Processing Have some fun and come up with your own mnemonic for the OSI model, but stick to just one so you don't get confused. -
ISO/OSI Model SSL: Security at Transport Layer
ISO/OSI Model SSL: Security at Transport Layer Peer-to-peer Application Layer Application Layer Presentation Layer Presentation Layer Network Security Session Layer Session Layer Assurance Transport Layer Transport Layer Network Layer Network Layer Network Layer Lecture 9 Data Link Layer Data Link Layer Data Link Layer Physical Layer Physical Layer Physical Layer October 30, 2003 Flow of bits Courtesy of Professors INFSCI 2935: Introduction of Computer Security 1 INFSCI 2935: Introduction to Computer Security 2 Chris Clifton & Matt Bishop 1 Security at the Transport Layer Secure Socket Layer (SSL) Secure Socket Layer (SSL) l Developed by Netscape to provide security in l Each party keeps session information ¡ Session identifier (unique) WWW browsers and servers ¡ The peer’s X.503(v3) certificate l SSL is the basis for the Internet standard ¡ Compression method used to reduce volume of data ¡ Cipher specification (parameters for cipher and MAC) protocol – Transport Layer Security (TLS) ¡ Master secret of 48 bits protocol (compatible with SSLv3) l Connection information ¡ Random data for the server & client l Key idea: Connections and Sessions ¡ Server and client keys (used for encryption) ¡A SSL session is an association between two peers ¡ Server and client MAC key ¡An SSL connection is the set of mechanisms used to ¡ Initialization vector for the cipher, if needed ¡ Server and client sequence numbers transport data in an SSL session l Provides a set of supported cryptographic mechanisms that are setup during negotiation (handshake protocol) -

Seven Layer OSI Model
InternationalInternational StandardsStandards OrganizationOrganization OpenOpen SystemsSystems InterconnectInterconnect (OSI)(OSI) ReferenceReference ModelModel Networks: OSI Reference Model 1 Application A Application B Application Application Layer Layer Presentation Presentation Layer Layer Session Session Layer Layer Transport Transport Layer Communication Network Layer Network Network Network Network Layer Layer Layer Layer Data Link Data Link Data Link Data Link Layer Layer Layer Layer Physical Physical Physical Physical Layer Layer Layer Layer Copyright ©2000 The McGraw Hill Companies Electrical and/or Optical Signals Leon-Garcia & Widjaja: Communication Networks Figure 2.6 Networks: OSI Reference Model 2 Copyright ©2000 The McGraw Hill Companies Leon-Garcia & Widjaja: Communication Networks Figure 2.9 Application A Application B data Application Application Layer data ah Layer Presentation Presentation Layer data ph Layer Session Session Layer data sh Layer Transport th Transport Layer data Layer Network Network Layer data nh Layer Data Link Data Link Layer dt data dh Layer Physical Physical Layer bits Layer Networks: OSI Reference Model 3 HTTP Request Header contains source and TCP destination port numbers Header Header contains source and destination IP addresses; IP transport protocol type Header Header contains source Frame and destination physical Ethernet addresses; network Check protocol type Header Sequence Copyright ©2000 The McGraw Hill Companies Leon-Garcia & Widjaja: Communication Networks Figure 2.15 Networks: OSI Reference Model 4 OSIOSI versusversus TCP/IPTCP/IP Figure 1-21. The TCP/IP reference model. Networks: OSI Reference Model 5 OSIOSI versusversus TCP/IPTCP/IP DCCDCC 66th Ed.,Ed., W.W. StallingsStallings FigureFigure 1.111.11 Networks: OSI Reference Model 6 SevenSeven LayerLayer OSIOSI ModelModel Application Layer Provides users access to the OSI environment and distributed information services.services. -
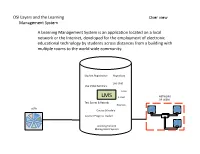
OSI & LMS Final Project.Pptx
OSI Layers and the Learning Over view Management System A Learning Management System is an applicaon located on a local network or the Internet, developed for the employment of electronic educaonal technology by students across distances from a building with mul7ple rooms to the world wide community. Student Registraon Repository Live Chat Live Video Seminars Tests LMS E-mail NETWORK OF USERS Test Scores & Records Courses USER Course Schedule Learner Progress Tracker Learning Content Management System OSI Layers and the Learning Physical Layer Management System DEVICE DEVICE CABLE MODEM FREQUENCY CABLE The physical layer supports the actual movement of bits and volts between devices (smart phone, computer, tablet, modem, repeater) through copper wire, fiber op7c cable, radio frequencies, or any other medium used to transmit data by a MODEM physical means. The physical layer is not concerned with the structure or organizaon of data, it is simply transming and receiving the data. Some devices func7on on other layers of the OSI model, so they do not fit neatly into physical layer because they conduct a CABLE func7on beyond simply moving bits and volts. However, all devices par7ally operate CABLE in the physical layer, but it is their primary func7on that solidly places them in one of CABLE REPEATER the other layers. REPEATER MODEM DEVICE OSI Layers and the Learning Data Link Layer Management System WIDE AREA NETWORK or LOCAL AREA NETWORK NODE NODE NIC NIC FRAMES—FRAMES—FRAMES—FRAMES FRAMES—FRAMES—FRAMES SWITCH / BRIDGE The data link layer is divided into two sub-layers; Logical Link Control (LLC) and Media Access Control (MAC). -

Session Layer OSI Reference Model Fatih SÜRER 2010514060
13.4.2015 OSI LAYER 5 - Session Layer OSI Reference Model Fatih SÜRER 2010514060 2 Review of the First Four Layer 3 4 Session Layer In the seven-layer OSI model of computer networking , the session layer is layer 5. This layer is primarily concerned with coordinating applications as they interact on different hosts. Support the dialog between cooperating application programs The session layer offers provisions for efficient data transfer. The session layer decides when to turn communication on and off between two computer Provides duplex, half-duplex, or simplex communications between devices. 5 6 1 13.4.2015 Session Layer Cont. The Session Layer provides services that allow to establish/manage/terminate a session-connection, to support orderly data exchange, to organize and to synchronize the dialogue and to release the connection in an orderly manner. The session’s layer objective is to hide the possible failures of transport-level connections to the upper layer higher. 7 8 Session Layer Cont. Session Layer Cont. Session layer provides a name space that is used to tie together the Sessions offer various services, including dialog potentially different transport streams that are part of a single control (keeping track of whose turn it is to application. For example, it might manage an audio stream and a video stream that are being combined in a teleconferencing transmit), token management (preventing two application. long story short, principal task of the session layer is parties from attempting the same critical operation to connect two processes together into a session. simultaneously), and synchronization (checkpointing The session layer whose overall function is to ensure the end to end integrity of the applications that are being supported. -

The Seven Layers of OSI the OSI Model Was Created to Impose A
The Seven Layers of OSI 1 The OSI model was created to impose a standardised from of networking, because up till the point it was introduced every computer company would have different network protocol. This meant that you couldn't buy computers from more than one company and expect them to work, because the computers wouldn't understand how each other coded and decoded the binary code that travels through the given network media. Layer 1 - Physical Layer: The physical layer encompasses all physical components and media used during data transfer in a network. This includes, but is not limited to, cables, switches, network cards and routers. Data transferred on the level of the Physical layer is in binary. Layer 2 - Data Link Layer This layer codes and decodes the bits being transferred by the physical layer. The data link layer frames the packets of data that are sent and checks for errors in the data. Layer 3 - Network Layer This layer determines the fastest route for data to travel to its destination and routes it as such. The network layer also handles a certain amount of error checking. Layer 4 - Transport Layer This layer determines the end to end transfer and it checks the data transfer was completed error free. End to end refers to the computers at each end of the cable/WI-FI. Layer 5 - Session Layer This layer establishes, manages and terminates connections between applications. The session layer also reports upper layer errors. Layer 6 - Presentation Layer This layer formats, encrypts and decrypts data to being sent and received by computers in a network. -
Medium Access Control Sublayer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Prof. Dr. Mesut Güneş Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Distributed, embedded Systems Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (()MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus ● Network Infrastructure ● Token Ring ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Prof. Dr. Mesut Güneş ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Prof. Dr. Mesut Güneş ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● PtProtoco ls use dtdtd to determ ine w ho gets next access to the channel Data Link Layer ● Medium Access Control (()MAC) sublay er Phy sical Laye r Prof. Dr. Mesut Güneş ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Rang e ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access - LLC IEEE 802.2 Logical Link Control .. -

Media Access Control Protocols in Local Area Networks / Paresh Shah Lehigh University
Lehigh University Lehigh Preserve Theses and Dissertations 1986 Media access control protocols in local area networks / Paresh Shah Lehigh University Follow this and additional works at: https://preserve.lehigh.edu/etd Part of the Electrical and Computer Engineering Commons Recommended Citation Shah, Paresh, "Media access control protocols in local area networks /" (1986). Theses and Dissertations. 4652. https://preserve.lehigh.edu/etd/4652 This Thesis is brought to you for free and open access by Lehigh Preserve. It has been accepted for inclusion in Theses and Dissertations by an authorized administrator of Lehigh Preserve. For more information, please contact [email protected]. Media Access Control Protocols • Ill Local Area Networks \ by Paresh Shah A Thesis Presented to the Graduate Committee of Lehigh University in Candidacy for the Degree of Master of Science . )Il Comp·uter Science Lehigh University 1986 This thesis is accepted and approved in partial fulfillment of t·he· re·qJXite~ ments for the Degree of Master of Science . .. Chai..rma·:n· CSEE Department ... 11 Acknowledgments I would like to take this time to acknowledge all those who have helped to bring about this thesis and the various concepts that are expressed. Initially, .I would like to thank rny parents for their years of support, guidance, love and understanding without which 1 could not have produced this thesis. I would like to thank Prof. Kenneth Tzeng for being a caring teacher and advisor during the research of this thesis. I would also like to thank Prof. Richard Denton for providing the necessary background material. Finally, I would like to thank all my friends and fellow graduate students who supported me during the research.