Session Layer Working Based on Cloud Environments
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

OSI Model and Network Protocols
CHAPTER4 FOUR OSI Model and Network Protocols Objectives 1.1 Explain the function of common networking protocols . TCP . FTP . UDP . TCP/IP suite . DHCP . TFTP . DNS . HTTP(S) . ARP . SIP (VoIP) . RTP (VoIP) . SSH . POP3 . NTP . IMAP4 . Telnet . SMTP . SNMP2/3 . ICMP . IGMP . TLS 134 Chapter 4: OSI Model and Network Protocols 4.1 Explain the function of each layer of the OSI model . Layer 1 – physical . Layer 2 – data link . Layer 3 – network . Layer 4 – transport . Layer 5 – session . Layer 6 – presentation . Layer 7 – application What You Need To Know . Identify the seven layers of the OSI model. Identify the function of each layer of the OSI model. Identify the layer at which networking devices function. Identify the function of various networking protocols. Introduction One of the most important networking concepts to understand is the Open Systems Interconnect (OSI) reference model. This conceptual model, created by the International Organization for Standardization (ISO) in 1978 and revised in 1984, describes a network architecture that allows data to be passed between computer systems. This chapter looks at the OSI model and describes how it relates to real-world networking. It also examines how common network devices relate to the OSI model. Even though the OSI model is conceptual, an appreciation of its purpose and function can help you better understand how protocol suites and network architectures work in practical applications. The OSI Seven-Layer Model As shown in Figure 4.1, the OSI reference model is built, bottom to top, in the following order: physical, data link, network, transport, session, presentation, and application. -

OSI Model: the 7 Layers of Network Architecture
OSI Model: The 7 Layers of Network Architecture The Open Systems Interconnection (OSI) Reference Model is a conceptual framework that describes functions of the networking or telecommunication system independently from the underlying technology infrastructure. It divides data communication into seven abstraction layers and standardizes protocols into appropriate groups of networking functionality to ensure interoperability within the communication system regardless of the technology type, vendor, and model. The OSI model was originally developed to facilitate interoperability between vendors and to define clear standards for network communication. However, the olderTCP/IP model remains the ubiquitous reference framework for Internet communications today. The 7 layers of the OSI model This image illustrates the seven layers of the OSI model. Below, we’ll briefly describe each layer, from bottom to top. 1. Physical The lowest layer of the OSI model is concerned with data communication in the form of electrical, optic, or electromagnetic signals physically transmitting information between networking devices and infrastructure. The physical layer is responsible for the communication of unstructured raw data streams over a physical medium. It defines a range of aspects, including: Electrical, mechanical, and physical systems and networking devices that include specifications such as cable size, signal frequency, voltages, etc. Topologies such as Bus, Star, Ring, and Mesh Communication modes such as Simplex, Half Duplex, and Full Duplex Data transmission performance, such as Bit Rate and Bit Synchronization Modulation, switching, and interfacing with the physical transmission medium Common protocols including Wi-Fi, Ethernet, and others Hardware including networking devices, antennas, cables, modem, and intermediate devices such as repeaters and hubs 2. -

The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
The Application Usage and Risk Report An Analysis of End User Application Trends in the Enterprise 8th Edition, December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 94089 www.paloaltonetworks.com Table of Contents Executive Summary ........................................................................................................ 3 Demographics ............................................................................................................................................. 4 Social Networking Use Becomes More Active ................................................................ 5 Facebook Applications Bandwidth Consumption Triples .......................................................................... 5 Twitter Bandwidth Consumption Increases 7-Fold ................................................................................... 6 Some Perspective On Bandwidth Consumption .................................................................................... 7 Managing the Risks .................................................................................................................................... 7 Browser-based Filesharing: Work vs. Entertainment .................................................... 8 Infrastructure- or Productivity-Oriented Browser-based Filesharing ..................................................... 9 Entertainment Oriented Browser-based Filesharing .............................................................................. 10 Comparing Frequency and Volume of Use -

Medium Access Control Layer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay (historical) ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus (historical) ● Network Infrastructure ● Token Ring (historical) ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● Protocols used to determine who gets next access to the channel Data Link Layer ● Medium Access Control (MAC) sublayer Physical Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Range ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access .. -

Cloud Computing
International Journal on Applications in Electrical and Electronics Engineering Volume 1: Issue 8: August 2015, pp 1-5. www.aetsjournal.com ISSN (Online) : 2395-3527 ----------------------------------------------------------------------------------------------------------------------------- ------------------------------ Cloud Computing R.Ramya, K.Ramya These cloud applications use large data centers and Abstract— Cloud computing is location independent computing, powerful services that host Web applications and Web whereby shared servers provide resources, software, and data to services. computers and other devices on demand, as with the electricity grid. Anyone with a suitable Internet connection and a Or more simply, remote computing. Cloud computing is a natural standard browser can access a cloud application. evolution of the widespread adoption of virtualization, service- oriented architecture and utility computing. Details are abstracted from consumers, who no longer have need for expertise in, or control over, the technology infrastructure "in the cloud" that supports them.. A cloud service has three distinct characteristics that differentiate it from traditional hosting. It is sold on demand, typically by the minute or the hour; it is elastic -- a user can have as much or as little of a service as they want at any given time; and the service is fully managed by the provider (the consumer needs nothing but a personal computer and Internet access). Significant innovations in virtualization and distributed computing, as well as improved access User of the cloud only care about the service or information to high-speed Internet and a weak economy, have accelerated interest they are accessing – be it from their PCs, mobile devices, or in cloud computing. anything else connected to the Internet – not about the In this paper we are also going to discuss the advantages, underlying details of how the cloud works. -

A Review on Cloud Computing: Design Challenges in Architecture and Security
Journal of Computing and Information Technology - CIT 19, 2011, 1, 25–55 25 doi:10.2498/cit.1001864 A Review on Cloud Computing: Design Challenges in Architecture and Security Fei Hu1, Meikang Qiu2,JiayinLi2, Travis Grant1, Draw Tylor1, Seth McCaleb1, Lee Butler1 and Richard Hamner 1 1 Department of Electrical and Computer Engineering, University of Alabama, Tuscaloosa, AL, USA 2 Department of Electrical and Computer Engineering, University of Kentucky, Lexington, KY, USA Cloud computing is becoming a powerful network archi- Rather than hard-wire data circuits between the tecture to perform large-scale and complex computing. provider and customers, telephone companies In this paper, we will comprehensively survey the concepts and architecture of cloud computing, as well began using VPN-based services to transmit as its security and privacy issues. We will compare data. This allowed providers to offer the same different cloud models, trust/reputation models and amount of bandwidth at a lower cost by rerout- privacy-preservation schemes. Their pros and cons ing network traffic in real-time to accommo- are discussed for each cloud computing security and architecture strategy. date ever-changing network utilization. Thus, it was not possible to accurately predict which Keywords: cloud computing, security, privacy, computer path data would take between the provider and networks, models customer. As a result, the service provider’s network responsibilities were represented by a cloud symbol to symbolize the black box of sorts from the end-users’ perspective. It is in 1. Introduction this sense that the term “cloud” in the phrase cloud computing metaphorically refers to the Cloud computing is quickly becoming one of Internet and its underlying infrastructure. -

ADD WES/OSN CH 11 5Thprf
THE PRESENTATION AND 11 SESSION LAYERS The presentation and session layers collaborate to provide many of the distributed-processing capabilities presented to user elements by the ser- vice elements of the application layer; for this reason, they are discussed together. Presentation Layer Chapter 4 describes how ASN.1 provides the application programmer with a tool for creating data structures that are syntactically independent from the way in which data are stored in a computer and from the way in which they are transferred between computer systems. Transforming these abstract syntaxes into “concrete” data structures appropriate for a given operating system (e.g., UNIX, DOS, VMS, MVS) is typically han- dled by tools such as ASN.1 compilers. The task of preserving the seman- tics of the data exchanged between a sender and receiver across an OSI network is handled by the presentation layer, which performs the trans- formations from the local (concrete) syntax used by each application entity to a common transfer syntax. This leads us to the discussion of the notion of a presentation context set. Context Set The presentation layer is responsible for managing the transfer syntaxes Definition associated with the set of abstract syntaxes that will be used by applica- tion entities as they exchange information across a presentation connec- tion. As part of presentation connection establishment, application enti- ties must be sure that the presentation layer can support a transfer syntax 247 248 OPEN SYSTEMS NETWORKING: TCP/IP AND OSI for every abstract syntax required by the distributed-processing applica- tion(s) that will use this connection. -

Media Cloud Application for Android
PERSONAL MEDIA CLOUD APPLICATION FOR ANDROID Prajakta Sarurkar B.E., Nagpur University, 2000 PROJECT Submitted in partial satisfaction of the requirements for the degree of MASTER OF SCIENCE in COMPUTER SCIENCE at CALIFORNIA STATE UNIVERSITY, SACRAMENTO SPRING 2012 © 2012 Prajakta Sarurkar ALL RIGHTS RESERVED ii PERSONAL MEDIA CLOUD APPLICATION FOR ANDROID A Project by Prajakta Sarurkar Approved by: __________________________________, Committee Chair Du Zhang, Ph.D. __________________________________, Second Reader Mary Jane Lee, Ph.D. ____________________________ Date iii Student: Prajakta Sarurkar I certify that this student has met the requirements for format contained in the University format manual, and that this project is suitable for shelving in the Library and credit is to be awarded for the project. __________________________, Graduate Coordinator ___________________ Nikrouz Faroughi, Ph.D. Date Department of Computer Science iv Abstract of PERSONAL MEDIA CLOUD APPLICATION FOR ANDROID by Prajakta Sarurkar Recent advances in communication technologies have enabled an exponential growth in connected devices like Android smart phones and tablets. These devices are mainly used for content consumption. However, limited resources available on these devices, as well as always connected internet accessibility makes these devices ideal platforms for cloud computing. This project is an attempt at creating personal media cloud player app for Android smart phone devices. The project uses off the shelf hardware components for private cloud -

1.2. OSI Model
1.2. OSI Model The OSI model classifies and organizes the tasks that hosts perform to prepare data for transport across the network. You should be familiar with the OSI model because it is the most widely used method for understanding and talking about network communications. However, remember that it is only a theoretical model that defines standards for programmers and network administrators, not a model of actual physical layers. Using the OSI model to discuss networking concepts has the following advantages: Provides a common language or reference point between network professionals Divides networking tasks into logical layers for easier comprehension Allows specialization of features at different levels Aids in troubleshooting Promotes standards interoperability between networks and devices Provides modularity in networking features (developers can change features without changing the entire approach) However, you must remember the following limitations of the OSI model: OSI layers are theoretical and do not actually perform real functions. Industry implementations rarely have a layer‐to‐layer correspondence with the OSI layers. Different protocols within the stack perform different functions that help send or receive the overall message. A particular protocol implementation may not represent every OSI layer (or may spread across multiple layers). To help remember the layer names of the OSI model, try the following mnemonic devices: Mnemonic Mnemonic Layer Name (Bottom to top) (Top to bottom) Layer 7 Application Away All Layer 6 Presentation Pizza People Layer 5 Session Sausage Seem Layer 4 Transport Throw To Layer 3 Network Not Need Layer 2 Data Link Do Data Layer 1 Physical Please Processing Have some fun and come up with your own mnemonic for the OSI model, but stick to just one so you don't get confused. -
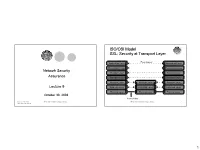
ISO/OSI Model SSL: Security at Transport Layer
ISO/OSI Model SSL: Security at Transport Layer Peer-to-peer Application Layer Application Layer Presentation Layer Presentation Layer Network Security Session Layer Session Layer Assurance Transport Layer Transport Layer Network Layer Network Layer Network Layer Lecture 9 Data Link Layer Data Link Layer Data Link Layer Physical Layer Physical Layer Physical Layer October 30, 2003 Flow of bits Courtesy of Professors INFSCI 2935: Introduction of Computer Security 1 INFSCI 2935: Introduction to Computer Security 2 Chris Clifton & Matt Bishop 1 Security at the Transport Layer Secure Socket Layer (SSL) Secure Socket Layer (SSL) l Developed by Netscape to provide security in l Each party keeps session information ¡ Session identifier (unique) WWW browsers and servers ¡ The peer’s X.503(v3) certificate l SSL is the basis for the Internet standard ¡ Compression method used to reduce volume of data ¡ Cipher specification (parameters for cipher and MAC) protocol – Transport Layer Security (TLS) ¡ Master secret of 48 bits protocol (compatible with SSLv3) l Connection information ¡ Random data for the server & client l Key idea: Connections and Sessions ¡ Server and client keys (used for encryption) ¡A SSL session is an association between two peers ¡ Server and client MAC key ¡An SSL connection is the set of mechanisms used to ¡ Initialization vector for the cipher, if needed ¡ Server and client sequence numbers transport data in an SSL session l Provides a set of supported cryptographic mechanisms that are setup during negotiation (handshake protocol) -

Wireless Evolution •..••••.•.•...•....•.•..•.•••••••...••••••.•••.••••••.••.•.••.••••••• 4
Department of Justice ,"'''''''''<11 Bureau of Investigation ,Operational Technology Division WIRELESS EVDLUTIDN IN THIS Iselil-it:: .. WIRELESS EVOLUTIDN I!I TECH BYTES • LONG TERM EVOLUTIQN ill CLDUD SERVICES • 4G TECHNOLOGY ill GESTURE-RECOGNITION • FCC ON BROADBAND • ACTIVITY-BASED NAVIGATION 'aw PUIi! I' -. q f. 8tH'-.1 Waa 8RI,. (!.EIi/RiW81 R.d-nl)) - 11 - I! .el " Ij MESSAGE FROM MANAGEMENT b7E he bou~~aries of technology are constantly expanding. develop technical tools to combat threats along the Southwest Recognizing the pathway of emerging technology is Border. a key element to maintaining relevance in a rapidly changing technological environment. While this The customer-centric approach calls for a high degree of T collaboration among engineers, subject matter experts (SMEs), proficiency is fundamentally important in developing strategies that preserve long-term capabilities in the face of emerging and the investigator to determine needs and requirements. technologies, equally important is delivering technical solutions To encourage innovation, the technologists gain a better to meet the operational needs of the law enforcement understanding of the operational and investigative needs customer in a dynamic 'threat' environment. How can technical and tailor the technology to fit the end user's challenges. law enforcement organizations maintain the steady-state Rather than developing solutions from scratch, the customer production of tools and expertise for technical collection, while centric approach leverages and modifies the technoloe:v to infusing ideas and agility into our organizations to improve our fit the customer's nFlFlrt~.1 ability to deliver timely, relevant, and cutting edge tools to law enforcement customers? Balancing these two fundamentals through an effective business strategy is both a challenge and an opportunity for the Federal Bureau of Investigation (FBI) and other Federal, state, and local law enforcement agencies.