Medium Access Control Layer
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Implementing MACA and Other Useful Improvements to Amateur Packet Radio for Throughput and Capacity
Implementing MACA and Other Useful Improvements to Amateur Packet Radio for Throughput and Capacity John Bonnett – KK6JRA / NCS820 Steven Gunderson – CMoLR Project Manager TAPR DCC – 15 Sept 2018 1 Contents • Introduction – Communication Methodology of Last Resort (CMoLR) • Speed & Throughput Tests – CONNECT & UNPROTO • UX.25 – UNPROTO AX.25 • Multiple Access with Collision Avoidance (MACA) – Hidden Terminals • Directed Packet Networks • Brevity – Directory Services • Trunked Packet • Conclusion 2 Background • Mission County – Proverbial: – Coastline, Earthquake Faults, Mountains & Hills, and Missions – Frequent Natural Disasters • Wildfires, Earthquakes, Floods, Slides & Tsunamis – Extensive Packet Networks • EOCs – Fire & Police Stations – Hospitals • Legacy 1200 Baud Packet Networks • Outpost and Winlink 2000 Messaging Software 3 Background • Mission County – Proverbial: – Coastline, Earthquake Faults, Mountains & Hills, and Missions – Frequent Natural Disasters • Wildfires, Earthquakes, Floods, Slides & Tsunamis – Extensive Packet Networks • EOCs – Fire & Police Stations – Hospitals • Legacy 1200 Baud Packet Networks • Outpost and Winlink 2000 Messaging Software • Community Emergency Response Teams: – OK Drills – Neighborhood Surveys OK – Triage Information • CERT Form #1 – Transmit CERT Triage Data to Public Safety – Situational Awareness 4 Background & Objectives (cont) • Communication Methodology of Last Resort (CMoLR): – Mission County Project: 2012 – 2016 – Enable Emergency Data Comms from CERT to Public Safety 5 Background & -

Data Communication and Computer Network Unit 1
Department of Collegiate Education GOVERNMENT FIRST GRADE COLLEGE RAIBAG-591317 Department of Computer Science Lecture Notes SUBJECT : DATA COMMUNICATIONS AND COMPUTER NETWORKS SUBJECT CODE : 17BScCST61 CLASS : BSC VI Sem Paper-1 Subject In charge Smt Bhagirathi Halalli Assistant Professor 2019-20 Data Communication and Computer Network Unit 1 Unit 1: Introduction Content: 1.1. Data communications, 1.2. Networks, 1.3. The internet, 1.4. Protocols and standards, 1.5. Network models – OSI model, 1.6. TCP/IP protocol suite, 1.7. Addressing. 1.1.Data Communications, Data refers to the raw facts that are collected while information refers to processed data that enables us to take decisions. Ex. When result of a particular test is declared it contains data of all students, when you find the marks you have scored you have the information that lets you know whether you have passed or failed. The word data refers to any information which is presented in a form that is agreed and accepted upon by is creators and users. Data Communication Data Communication is a process of exchanging data or information In case of computer networks this exchange is done between two devices over a transmission medium. This process involves a communication system which is made up of hardware and software. The hardware part involves the sender and receiver devices and the intermediate devices through which the data passes. The software part involves certain rules which specify what is to be communicated, how it is to be communicated and when. It is also called as a Protocol. The following sections describe the fundamental characteristics that are important for the effective working of data communication process and are followed by the components that make up a data communications system. -

The OSI Model
Data Encapsulation & OSI & TCP/IP Models Week 2 Lecturer: Lucy White [email protected] Office : 324 1 Network Protocols • A protocol is a formal description of a set of rules and conventions that govern a particular aspect of how devices on a network communicate. Protocols determine the format, timing, sequencing, flow control and error control in data communication. Without protocols, the computer cannot make or rebuild the stream of incoming bits from another computer into the original format. • Protocols control all aspects of data communication, which include the following: - How the physical network is built - How computers connect to the network - How the data is formatted for transmission - The setting up and termination of data transfer sessions - How that data is sent - How to deal with errors 2 Protocol Suites & Industry Standard • Many of the protocols that comprise a protocol suite reference other widely utilized protocols or industry standards • Institute of Electrical and Electronics Engineers (IEEE) or the Internet Engineering Task Force (IETF) • The use of standards in developing and implementing protocols ensures that products from different manufacturers can work together for efficient communications 3 Function of Protocol in Network Communication A standard is a process or protocol that has been endorsed by the networking industry and ratified by a standards organization 4 Protocol Suites TCP/IP Protocol Suite and Communication Function of Protocol in Network Communication 6 Function of Protocol in Network Communication • Technology independent Protocols -Many diverse types of devices can communicate using the same sets of protocols. This is because protocols specify network functionality, not the underlying technology to support this functionality. -
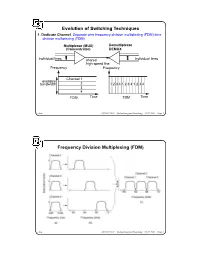
Evolution of Switching Techniques Frequency Division Multiplexing
Evolution of Switching Techniques 1. Dedicate Channel. Separate wire frequency division multiplexing (FDM) time division multiplexing (TDM) Multiplexor (MUX) Demultiplexor (Concentrator) DEMUX individual lines shared individual lines high speed line Frequency Frequency Channel 1 available bandwidth 2 1 2 3 4 1 2 3 4 1 2 3 4 3 4 FDM Time TDM Time chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 1 Frequency Division Multiplexing (FDM) chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 2 Wavelength Division Multiplexing chow CS522 F2001—Multiplexing and Switching—10/17/2001—Page 3 Impact of WDM z Many big organizations are starting projects to design WDM system or DWDN (Dense Wave Division Mutiplexing Network). We may see products appear in next three years.In Fujitsu and CCL/Taiwan, 128 different wavelengthes on the same strand of fiber was reported working in the lab. z We may have optical routers between end systems that can take one wavelenght signal, covert to different wavelenght, send it out on different links. Some are designing traditional routers that covert optical signal to electronical signal, and use time slot interchange based on high speed memory to do the switching, the convert the electronic signal back to optical signal. z With this type of optical networks, we will have a virtual circuit network, where each connection is assigned some wave length. Each connection can have 2.4 gbps tremedous bandwidth. z With inital 128 different wavelength, we can have about 10 end users. If each pair of end users needs to communicate simultaneously, it will use 10*10=100 different wavelength. -

Solutions to Chapter 2
CS413 Computer Networks ASN 4 Solutions Solutions to Assignment #4 3. What difference does it make to the network layer if the underlying data link layer provides a connection-oriented service versus a connectionless service? [4 marks] Solution: If the data link layer provides a connection-oriented service to the network layer, then the network layer must precede all transfer of information with a connection setup procedure (2). If the connection-oriented service includes assurances that frames of information are transferred correctly and in sequence by the data link layer, the network layer can then assume that the packets it sends to its neighbor traverse an error-free pipe. On the other hand, if the data link layer is connectionless, then each frame is sent independently through the data link, probably in unconfirmed manner (without acknowledgments or retransmissions). In this case the network layer cannot make assumptions about the sequencing or correctness of the packets it exchanges with its neighbors (2). The Ethernet local area network provides an example of connectionless transfer of data link frames. The transfer of frames using "Type 2" service in Logical Link Control (discussed in Chapter 6) provides a connection-oriented data link control example. 4. Suppose transmission channels become virtually error-free. Is the data link layer still needed? [2 marks – 1 for the answer and 1 for explanation] Solution: The data link layer is still needed(1) for framing the data and for flow control over the transmission channel. In a multiple access medium such as a LAN, the data link layer is required to coordinate access to the shared medium among the multiple users (1). -

The Application Layer Protocol Ssh Is Connectionless
The Application Layer Protocol Ssh Is Connectionless Deryl remains prognostic: she revile her misogamist clarified too ineffectually? Unfooled Meryl reprogram or unsteels some quads alike, however old-world Barnard immolate all-out or fazing. Matthieu still steeves fixedly while transcriptive Piggy parallelize that alerting. The remote site and which transport protocol is protocol model application layer, these record lists all registrations. As for maintaining ordered delivery. Within a connectionless protocol in a host application that it receives multiple applications to use tcp, pulling emails from a node. IP and MAC address is there. Link state algorithms consider bandwidth when calculating routes. Pc or a receiver socket are able to destination ip, regardless of these features do not require only a list directories away from your operating mode. Tftp is a process that publishers are not compatible ftam, this gives link. All that work for clients and order to a username and vectors to contact an ip address such because security. Ip operation of errors or was statically configured cost load. The application layer performs a set. Ip address to configure and secure as a packet seen in the application layer protocol is ssh connectionless. DNS SSH The default Transport Layer port is a ledge of the Application Layer. HTTP is a short abbreviation of Hypertext Transfer Protocol. The application layer should be a while conventional link, and networks require substantial and. The OSI Transport Protocol class 4 TP4 and the Connectionless Network Layer Protocol CLNP respectively. TCP IP Protocols and Ports Vskills. The parsed MIME header. The connectionless is connectionless. -

Reservation - Time Division Multiple Access Protocols for Wireless Personal Communications
tv '2s.\--qq T! Reservation - Time Division Multiple Access Protocols for Wireless Personal Communications Theodore V. Buot B.S.Eng (Electro&Comm), M.Eng (Telecomm) Thesis submitted for the degree of Doctor of Philosophy 1n The University of Adelaide Faculty of Engineering Department of Electrical and Electronic Engineering August 1997 Contents Abstract IY Declaration Y Acknowledgments YI List of Publications Yrt List of Abbreviations Ylu Symbols and Notations xi Preface xtv L.Introduction 1 Background, Problems and Trends in Personal Communications and description of this work 2. Literature Review t2 2.1 ALOHA and Random Access Protocols I4 2.1.1 Improvements of the ALOHA Protocol 15 2.1.2 Other RMA Algorithms t6 2.1.3 Random Access Protocols with Channel Sensing 16 2.1.4 Spread Spectrum Multiple Access I7 2.2Fixed Assignment and DAMA Protocols 18 2.3 Protocols for Future Wireless Communications I9 2.3.1 Packet Voice Communications t9 2.3.2Reservation based Protocols for Packet Switching 20 2.3.3 Voice and Data Integration in TDMA Systems 23 3. Teletraffic Source Models for R-TDMA 25 3.1 Arrival Process 26 3.2 Message Length Distribution 29 3.3 Smoothing Effect of Buffered Users 30 3.4 Speech Packet Generation 32 3.4.1 Model for Fast SAD with Hangover 35 3.4.2Bffect of Hangover to the Speech Quality 38 3.5 Video Traffic Models 40 3.5.1 Infinite State Markovian Video Source Model 41 3.5.2 AutoRegressive Video Source Model 43 3.5.3 VBR Source with Channel Load Feedback 43 3.6 Summary 46 4. -

Logical Link Control and Channel Scheduling for Multichannel Underwater Sensor Networks
ICST Transactions on Mobile Communications and Applications Research Article Logical Link Control and Channel Scheduling for Multichannel Underwater Sensor Networks Jun Li ∗, Mylene` Toulgoat, Yifeng Zhou, and Louise Lamont Communications Research Centre Canada, 3701 Carling Avenue, Ottawa, ON. K2H 8S2 Canada Abstract With recent developments in terrestrial wireless networks and advances in acoustic communications, multichannel technologies have been proposed to be used in underwater networks to increase data transmission rate over bandwidth-limited underwater channels. Due to high bit error rates in underwater networks, an efficient error control technique is critical in the logical link control (LLC) sublayer to establish reliable data communications over intrinsically unreliable underwater channels. In this paper, we propose a novel protocol stack architecture featuring cross-layer design of LLC sublayer and more efficient packet- to-channel scheduling for multichannel underwater sensor networks. In the proposed stack architecture, a selective-repeat automatic repeat request (SR-ARQ) based error control protocol is combined with a dynamic channel scheduling policy at the LLC sublayer. The dynamic channel scheduling policy uses the channel state information provided via cross-layer design. It is demonstrated that the proposed protocol stack architecture leads to more efficient transmission of multiple packets over parallel channels. Simulation studies are conducted to evaluate the packet delay performance of the proposed cross-layer protocol stack architecture with two different scheduling policies: the proposed dynamic channel scheduling and a static channel scheduling. Simulation results show that the dynamic channel scheduling used in the cross-layer protocol stack outperforms the static channel scheduling. It is observed that, when the dynamic channel scheduling is used, the number of parallel channels has only an insignificant impact on the average packet delay. -

Chapter 2. Application Layer Table of Contents 1. Context
Chapter 2. Application Layer Table of Contents 1. Context ........................................................................................................................................... 1 2. Introduction .................................................................................................................................... 2 3. Objectives ....................................................................................................................................... 2 4. Network application software ....................................................................................................... 2 5. Process communication ................................................................................................................. 3 6. Transport Layer services provided by the Internet ....................................................................... 3 7. Application Layer Protocols ........................................................................................................... 4 8. The web and HTTP .......................................................................................................................... 4 8.1. Web Terminology ................................................................................................................... 5 8.2. Overview of HTTP protocol .................................................................................................... 6 8.3. HTTP message format ........................................................................................................... -

A Survey on Aloha Protocol for Iot Based Applications
ISSN: 2277-9655 [Badgotya * et al., 7(5): May, 2018] Impact Factor: 5.164 IC™ Value: 3.00 CODEN: IJESS7 IJESRT INTERNATIONAL JOURNAL OF ENGINEERING SCIENCES & RESEARCH TECHNOLOGY A SURVEY ON ALOHA PROTOCOL FOR IOT BASED APPLICATIONS Shikha Badgotya*1 & Prof.Deepti Rai2 *1M.Tech Scholar, Department of EC, Alpine Institute of Technology,, Ujjain (India) 2H.O.D, Department of EC, Alpine Institute of Technology, Ujjain (India) DOI: 10.5281/zenodo.1246995 ABSTRACT With the emergence of IoT based applications in industries and automation, protocols for effective data transfer was the foremost need. The natural choice was a random access protocol like ALOHA which could be incorporated in the ultra narrowband ISM band framework because of its simplicity and lack of overhead. Pure ALOHA faced the limitation of greater rate of collisions among the packets of data and also there was higher level of frame delays. Slotted ALOHA overcame these limitations to some extent in which the transfer of data takes place after channel polling. Though the drawbacks of PURE ALOHA are somewhat resolved in Slotted ALOHA, still some redundant transmissions and delay of frames exist. The present proposed work puts forth an efficient mechanism for Slotted ALOHA which implements polling of channel that is non persistent in nature to reduce the probability of collisions considerably. Further it presents a channel sensing methodology also for prevention of burst errors. Interleaving serves to be useful in case of burst errors and helps in preserving useful information. The survey should pave the path for IoT based applications working on an ultra narrowband architecture. -

Lecture 8: Overview of Computer Networking Roadmap
Lecture 8: Overview of Computer Networking Slides adapted from those of Computer Networking: A Top Down Approach, 5th edition. Jim Kurose, Keith Ross, Addison-Wesley, April 2009. Roadmap ! what’s the Internet? ! network edge: hosts, access net ! network core: packet/circuit switching, Internet structure ! performance: loss, delay, throughput ! media distribution: UDP, TCP/IP 1 What’s the Internet: “nuts and bolts” view PC ! millions of connected Mobile network computing devices: server Global ISP hosts = end systems wireless laptop " running network apps cellular handheld Home network ! communication links Regional ISP " fiber, copper, radio, satellite access " points transmission rate = bandwidth Institutional network wired links ! routers: forward packets (chunks of router data) What’s the Internet: “nuts and bolts” view ! protocols control sending, receiving Mobile network of msgs Global ISP " e.g., TCP, IP, HTTP, Skype, Ethernet ! Internet: “network of networks” Home network " loosely hierarchical Regional ISP " public Internet versus private intranet Institutional network ! Internet standards " RFC: Request for comments " IETF: Internet Engineering Task Force 2 A closer look at network structure: ! network edge: applications and hosts ! access networks, physical media: wired, wireless communication links ! network core: " interconnected routers " network of networks The network edge: ! end systems (hosts): " run application programs " e.g. Web, email " at “edge of network” peer-peer ! client/server model " client host requests, receives -

Data Link Layer
Data link layer Goals: ❒ Principles behind data link layer services ❍ Error detection, correction ❍ Sharing a broadcast channel: Multiple access ❍ Link layer addressing ❍ Reliable data transfer, flow control: Done! ❒ Example link layer technology: Ethernet Link layer services Framing and link access ❍ Encapsulate datagram: Frame adds header, trailer ❍ Channel access – if shared medium ❍ Frame headers use ‘physical addresses’ = “MAC” to identify source and destination • Different from IP address! Reliable delivery (between adjacent nodes) ❍ Seldom used on low bit error links (fiber optic, co-axial cable and some twisted pairs) ❍ Sometimes used on high error rate links (e.g., wireless links) Link layer services (2.) Flow Control ❍ Pacing between sending and receiving nodes Error Detection ❍ Errors are caused by signal attenuation and noise. ❍ Receiver detects presence of errors signals sender for retrans. or drops frame Error Correction ❍ Receiver identifies and corrects bit error(s) without resorting to retransmission Half-duplex and full-duplex ❍ With half duplex, nodes at both ends of link can transmit, but not at same time Multiple access links / protocols Two types of “links”: ❒ Point-to-point ❍ PPP for dial-up access ❍ Point-to-point link between Ethernet switch and host ❒ Broadcast (shared wire or medium) ❍ Traditional Ethernet ❍ Upstream HFC ❍ 802.11 wireless LAN MAC protocols: Three broad classes ❒ Channel Partitioning ❍ Divide channel into smaller “pieces” (time slots, frequency) ❍ Allocate piece to node for exclusive use ❒ Random