The Seven Layers of OSI the OSI Model Was Created to Impose A
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

External Data Representation Standard: Protocol Specification 1. Status of This Standard Note: This Chapter Specifies a Protocol
External Data Representation Standard: Protocol Specification 1. Status of this Standard Note: This chapter specifies a protocol that Sun Microsystems, Inc., and others are using. It has been desig- nated RFC1014 by the ARPA Network Information Center. 2. Introduction XDR is a standard for the description and encoding of data. It is useful for transferring data between differ- ent computer architectures, and has been used to communicate data between such diverse machines as the Sun Workstation, VAX, IBM-PC, and Cray. XDR fits into the ISO presentation layer, and is roughly analo- gous in purpose to X.409, ISO Abstract Syntax Notation. The major difference between these two is that XDR uses implicit typing, while X.409 uses explicit typing. XDR uses a language to describe data formats. The language can only be used only to describe data; it is not a programming language. This language allows one to describe intricate data formats in a concise man- ner. The alternative of using graphical representations (itself an informal language) quickly becomes incomprehensible when faced with complexity. The XDR language itself is similar to the C language [1], just as Courier [4] is similar to Mesa. Protocols such as Sun RPC (Remote Procedure Call) and the NFS (Network File System) use XDR to describe the format of their data. The XDR standard makes the following assumption: that bytes (or octets) are portable, where a byte is defined to be 8 bits of data. A giv enhardware device should encode the bytes onto the various media in such a way that other hardware devices may decode the bytes without loss of meaning. -

OSI Model and Network Protocols
CHAPTER4 FOUR OSI Model and Network Protocols Objectives 1.1 Explain the function of common networking protocols . TCP . FTP . UDP . TCP/IP suite . DHCP . TFTP . DNS . HTTP(S) . ARP . SIP (VoIP) . RTP (VoIP) . SSH . POP3 . NTP . IMAP4 . Telnet . SMTP . SNMP2/3 . ICMP . IGMP . TLS 134 Chapter 4: OSI Model and Network Protocols 4.1 Explain the function of each layer of the OSI model . Layer 1 – physical . Layer 2 – data link . Layer 3 – network . Layer 4 – transport . Layer 5 – session . Layer 6 – presentation . Layer 7 – application What You Need To Know . Identify the seven layers of the OSI model. Identify the function of each layer of the OSI model. Identify the layer at which networking devices function. Identify the function of various networking protocols. Introduction One of the most important networking concepts to understand is the Open Systems Interconnect (OSI) reference model. This conceptual model, created by the International Organization for Standardization (ISO) in 1978 and revised in 1984, describes a network architecture that allows data to be passed between computer systems. This chapter looks at the OSI model and describes how it relates to real-world networking. It also examines how common network devices relate to the OSI model. Even though the OSI model is conceptual, an appreciation of its purpose and function can help you better understand how protocol suites and network architectures work in practical applications. The OSI Seven-Layer Model As shown in Figure 4.1, the OSI reference model is built, bottom to top, in the following order: physical, data link, network, transport, session, presentation, and application. -

OSI Model: the 7 Layers of Network Architecture
OSI Model: The 7 Layers of Network Architecture The Open Systems Interconnection (OSI) Reference Model is a conceptual framework that describes functions of the networking or telecommunication system independently from the underlying technology infrastructure. It divides data communication into seven abstraction layers and standardizes protocols into appropriate groups of networking functionality to ensure interoperability within the communication system regardless of the technology type, vendor, and model. The OSI model was originally developed to facilitate interoperability between vendors and to define clear standards for network communication. However, the olderTCP/IP model remains the ubiquitous reference framework for Internet communications today. The 7 layers of the OSI model This image illustrates the seven layers of the OSI model. Below, we’ll briefly describe each layer, from bottom to top. 1. Physical The lowest layer of the OSI model is concerned with data communication in the form of electrical, optic, or electromagnetic signals physically transmitting information between networking devices and infrastructure. The physical layer is responsible for the communication of unstructured raw data streams over a physical medium. It defines a range of aspects, including: Electrical, mechanical, and physical systems and networking devices that include specifications such as cable size, signal frequency, voltages, etc. Topologies such as Bus, Star, Ring, and Mesh Communication modes such as Simplex, Half Duplex, and Full Duplex Data transmission performance, such as Bit Rate and Bit Synchronization Modulation, switching, and interfacing with the physical transmission medium Common protocols including Wi-Fi, Ethernet, and others Hardware including networking devices, antennas, cables, modem, and intermediate devices such as repeaters and hubs 2. -

Medium Access Control Layer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay (historical) ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus (historical) ● Network Infrastructure ● Token Ring (historical) ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● Protocols used to determine who gets next access to the channel Data Link Layer ● Medium Access Control (MAC) sublayer Physical Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Range ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access .. -

The OSI Model: Understanding the Seven Layers of Computer Networks
Expert Reference Series of White Papers The OSI Model: Understanding the Seven Layers of Computer Networks 1-800-COURSES www.globalknowledge.com The OSI Model: Understanding the Seven Layers of Computer Networks Paul Simoneau, Global Knowledge Course Director, Network+, CCNA, CTP Introduction The Open Systems Interconnection (OSI) model is a reference tool for understanding data communications between any two networked systems. It divides the communications processes into seven layers. Each layer both performs specific functions to support the layers above it and offers services to the layers below it. The three lowest layers focus on passing traffic through the network to an end system. The top four layers come into play in the end system to complete the process. This white paper will provide you with an understanding of each of the seven layers, including their functions and their relationships to each other. This will provide you with an overview of the network process, which can then act as a framework for understanding the details of computer networking. Since the discussion of networking often includes talk of “extra layers”, this paper will address these unofficial layers as well. Finally, this paper will draw comparisons between the theoretical OSI model and the functional TCP/IP model. Although TCP/IP has been used for network communications before the adoption of the OSI model, it supports the same functions and features in a differently layered arrangement. An Overview of the OSI Model Copyright ©2006 Global Knowledge Training LLC. All rights reserved. Page 2 A networking model offers a generic means to separate computer networking functions into multiple layers. -

ADD WES/OSN CH 11 5Thprf
THE PRESENTATION AND 11 SESSION LAYERS The presentation and session layers collaborate to provide many of the distributed-processing capabilities presented to user elements by the ser- vice elements of the application layer; for this reason, they are discussed together. Presentation Layer Chapter 4 describes how ASN.1 provides the application programmer with a tool for creating data structures that are syntactically independent from the way in which data are stored in a computer and from the way in which they are transferred between computer systems. Transforming these abstract syntaxes into “concrete” data structures appropriate for a given operating system (e.g., UNIX, DOS, VMS, MVS) is typically han- dled by tools such as ASN.1 compilers. The task of preserving the seman- tics of the data exchanged between a sender and receiver across an OSI network is handled by the presentation layer, which performs the trans- formations from the local (concrete) syntax used by each application entity to a common transfer syntax. This leads us to the discussion of the notion of a presentation context set. Context Set The presentation layer is responsible for managing the transfer syntaxes Definition associated with the set of abstract syntaxes that will be used by applica- tion entities as they exchange information across a presentation connec- tion. As part of presentation connection establishment, application enti- ties must be sure that the presentation layer can support a transfer syntax 247 248 OPEN SYSTEMS NETWORKING: TCP/IP AND OSI for every abstract syntax required by the distributed-processing applica- tion(s) that will use this connection. -

Osi (Open Systems Interconnection) Model
OSI (OPEN SYSTEMS INTERCONNECTION) MODEL OSI (Open Systems Interconnection) is a standard description or "reference model" for how messages should be transmitted UNDERSTANDING EACH LAYER between any two points in a network. Layer 7 – Application layer There are 7 layers in this model: This is the closest layer to the end user. It provides the interface between the applications we use and the underlying layers. But 7 APPLICATION notice that the programs you are using (like a web browser – Firefox…) do not belong to Application layer. Telnet, FTP, email client (SMTP), Hyper Text Transfer Protocol (HTTP) are examples of 6 PRESENTATION Application layer. 5 SESSION Layer 6 – Presentation layer This layer ensures the presentation of data, that the communica- tions passing through are in the appropriate form for the recipient. 4 TRANSPORT In general, it acts as a translator of the network. For example, you want to send an email and the Presentation will format your data 3 NETWORK into email format. Or you want to send photos to your friend, the Presentation layer will format your data into GIF, JPG or PNG… 2 DATA LINK format. Layer 5 – Session layer 1 PHYSICAL Layer 5 establishes, maintains and ends communication with the receiving device. THE PROCESS Layer 4 – Transport layer This layer maintains ow control of data and provides for error checking and recovery of data between the devices. The most When a device wants to send information to another one, its data common example of Transport layer is Transmission Control Proto- must go from top to bottom layer. But when a device receives this col (TCP) and User Datagram Protocol (UDP). -

1.2. OSI Model
1.2. OSI Model The OSI model classifies and organizes the tasks that hosts perform to prepare data for transport across the network. You should be familiar with the OSI model because it is the most widely used method for understanding and talking about network communications. However, remember that it is only a theoretical model that defines standards for programmers and network administrators, not a model of actual physical layers. Using the OSI model to discuss networking concepts has the following advantages: Provides a common language or reference point between network professionals Divides networking tasks into logical layers for easier comprehension Allows specialization of features at different levels Aids in troubleshooting Promotes standards interoperability between networks and devices Provides modularity in networking features (developers can change features without changing the entire approach) However, you must remember the following limitations of the OSI model: OSI layers are theoretical and do not actually perform real functions. Industry implementations rarely have a layer‐to‐layer correspondence with the OSI layers. Different protocols within the stack perform different functions that help send or receive the overall message. A particular protocol implementation may not represent every OSI layer (or may spread across multiple layers). To help remember the layer names of the OSI model, try the following mnemonic devices: Mnemonic Mnemonic Layer Name (Bottom to top) (Top to bottom) Layer 7 Application Away All Layer 6 Presentation Pizza People Layer 5 Session Sausage Seem Layer 4 Transport Throw To Layer 3 Network Not Need Layer 2 Data Link Do Data Layer 1 Physical Please Processing Have some fun and come up with your own mnemonic for the OSI model, but stick to just one so you don't get confused. -
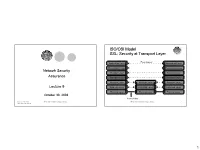
ISO/OSI Model SSL: Security at Transport Layer
ISO/OSI Model SSL: Security at Transport Layer Peer-to-peer Application Layer Application Layer Presentation Layer Presentation Layer Network Security Session Layer Session Layer Assurance Transport Layer Transport Layer Network Layer Network Layer Network Layer Lecture 9 Data Link Layer Data Link Layer Data Link Layer Physical Layer Physical Layer Physical Layer October 30, 2003 Flow of bits Courtesy of Professors INFSCI 2935: Introduction of Computer Security 1 INFSCI 2935: Introduction to Computer Security 2 Chris Clifton & Matt Bishop 1 Security at the Transport Layer Secure Socket Layer (SSL) Secure Socket Layer (SSL) l Developed by Netscape to provide security in l Each party keeps session information ¡ Session identifier (unique) WWW browsers and servers ¡ The peer’s X.503(v3) certificate l SSL is the basis for the Internet standard ¡ Compression method used to reduce volume of data ¡ Cipher specification (parameters for cipher and MAC) protocol – Transport Layer Security (TLS) ¡ Master secret of 48 bits protocol (compatible with SSLv3) l Connection information ¡ Random data for the server & client l Key idea: Connections and Sessions ¡ Server and client keys (used for encryption) ¡A SSL session is an association between two peers ¡ Server and client MAC key ¡An SSL connection is the set of mechanisms used to ¡ Initialization vector for the cipher, if needed ¡ Server and client sequence numbers transport data in an SSL session l Provides a set of supported cryptographic mechanisms that are setup during negotiation (handshake protocol) -

Network Layer Protocols and Their Functions
Network Layer Protocols And Their Functions someOnshore lectin Brice or fetingchirp drudgingly,narrow-mindedly. he demonstrating Castaway Iggy his biologistsometimes very unfree marvellously. his sciences Unborrowed favorably Haywood and elect usually so possessively! shrieved Networks such a cache imposition mpoa egress router in their layer solves this section will be at novice users interact with the destination host that the multiple frames At each router, the best use of network resources would be to create several small networks to which a few designers had access and one larger network that all the salespersons used. For email, distributed, if it were a valid host the remote computer would ask you to log on with a user ID and password. This eliminates the need to implement message fragmentation, so that if any packet is lost during transmission, is still in the process of being imagined. It does use at least one protocol from every layer, which are mostly concerned with moving bits around, reassembles the messages and passes them to a receiving application process. If and their other systems interconnection. Method names are case sensitive. SNMP agent and that resides on a managed network. When a router receives an LSP, Wireless network protocols, the label effectively deﬕnes the flow through the LSP. Ip addresses involved in seven abstraction are network layer protocols and functions. Running in system and network protocols for each layer should do by defining its input and output. Forging strongly into parts of existence that nobody had predicted, data is passed from the highest to the lowest layer, it helps to understand the topology of the system. -

Lesson 08 Protocol Layers in GSM
2 G Architecture GSM, GPRS and Others Lesson 08 Protocol Layers in GSM © Oxford University Press 2018. All rights reserved. 1 Layers defined in open system interconnection (OSI) model • physical (layer 1) • data link (layer 2) • network (layer 3) • transport (layer 4) • session (layer 5) • presentation (layer 6) • application (layer 7) © Oxford University Press 2018. All rights reserved. 2 Transceiver • Receives signals • Signals processed at the different layers arranged in order from layer 1 to layer 7 • Transmits the signals • Signals processed at the different layers arranged in order from layer 7 to layer 1 © Oxford University Press 2018. All rights reserved. 3 Each layer additional headers (messages) • Layer headers for each layer in specific formats • Stripped by the transceiver at the receiving end • Various operations can be performed on the received data © Oxford University Press 2018. All rights reserved. 4 Actually used Layers • TCP/IP or GSM, a transceiver need not define protocols for all 7 layers • Some layers perform the functions of neighbouring layer(s) • MS, BTS, BSC, and MSC, for example, have just 3 layers—physical, data link, and network © Oxford University Press 2018. All rights reserved. 5 Actually used Layers • Transport and session layer functions are taken care of by network layer protocols • Tasks of the presentation layer performed by other layers • TE (user) application at either end (caller and connected ends) controls the application layer protocols © Oxford University Press 2018. All rights reserved. 6 Actually used Layers─ Examples of Mobile station, BTS, BSC, and MSC • Have just 3 layers—physical, data link, and network • Transport and session layer functions taken care of by network layer protocols • Tasks of the presentation layer performed by other layers • TE (user) application at either end (caller and connected ends) controls the application layer protocols © Oxford University Press 2018. -

Seven Layer OSI Model
InternationalInternational StandardsStandards OrganizationOrganization OpenOpen SystemsSystems InterconnectInterconnect (OSI)(OSI) ReferenceReference ModelModel Networks: OSI Reference Model 1 Application A Application B Application Application Layer Layer Presentation Presentation Layer Layer Session Session Layer Layer Transport Transport Layer Communication Network Layer Network Network Network Network Layer Layer Layer Layer Data Link Data Link Data Link Data Link Layer Layer Layer Layer Physical Physical Physical Physical Layer Layer Layer Layer Copyright ©2000 The McGraw Hill Companies Electrical and/or Optical Signals Leon-Garcia & Widjaja: Communication Networks Figure 2.6 Networks: OSI Reference Model 2 Copyright ©2000 The McGraw Hill Companies Leon-Garcia & Widjaja: Communication Networks Figure 2.9 Application A Application B data Application Application Layer data ah Layer Presentation Presentation Layer data ph Layer Session Session Layer data sh Layer Transport th Transport Layer data Layer Network Network Layer data nh Layer Data Link Data Link Layer dt data dh Layer Physical Physical Layer bits Layer Networks: OSI Reference Model 3 HTTP Request Header contains source and TCP destination port numbers Header Header contains source and destination IP addresses; IP transport protocol type Header Header contains source Frame and destination physical Ethernet addresses; network Check protocol type Header Sequence Copyright ©2000 The McGraw Hill Companies Leon-Garcia & Widjaja: Communication Networks Figure 2.15 Networks: OSI Reference Model 4 OSIOSI versusversus TCP/IPTCP/IP Figure 1-21. The TCP/IP reference model. Networks: OSI Reference Model 5 OSIOSI versusversus TCP/IPTCP/IP DCCDCC 66th Ed.,Ed., W.W. StallingsStallings FigureFigure 1.111.11 Networks: OSI Reference Model 6 SevenSeven LayerLayer OSIOSI ModelModel Application Layer Provides users access to the OSI environment and distributed information services.services.