2006 Legislative Priorites For
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Port Security
S. HRG. 107–593 PORT SECURITY HEARING BEFORE A SUBCOMMITTEE OF THE COMMITTEE ON APPROPRIATIONS UNITED STATES SENATE ONE HUNDRED SEVENTH CONGRESS SECOND SESSION SPECIAL HEARING APRIL 4, 2002—SEATTLE, WA Printed for the use of the Committees on Appropriations ( Available via the World Wide Web: http://www.access.gpo.gov/congress/senate U.S. GOVERNMENT PRINTING OFFICE 81–047 PDF WASHINGTON : 2002 For sale by the Superintendent of Documents, U.S. Government Printing Office Internet: bookstore.gpo.gov Phone: toll free (866) 512–1800; DC area (202) 512–1800 Fax: (202) 512–2250 Mail: Stop SSOP, Washington, DC 20402–0001 VerDate 21-JUN-2000 10:09 Oct 23, 2002 Jkt 081047 PO 00000 Frm 00001 Fmt 5011 Sfmt 5011 U:\12HEAR\2003\081047.XXX CHERYLM PsN: CHERYLM COMMITTEE ON APPROPRIATIONS ROBERT C. BYRD, West Virginia, Chairman DANIEL K. INOUYE, Hawaii TED STEVENS, Alaska ERNEST F. HOLLINGS, South Carolina THAD COCHRAN, Mississippi PATRICK J. LEAHY, Vermont ARLEN SPECTER, Pennsylvania TOM HARKIN, Iowa PETE V. DOMENICI, New Mexico BARBARA A. MIKULSKI, Maryland CHRISTOPHER S. BOND, Missouri HARRY REID, Nevada MITCH MCCONNELL, Kentucky HERB KOHL, Wisconsin CONRAD BURNS, Montana PATTY MURRAY, Washington RICHARD C. SHELBY, Alabama BYRON L. DORGAN, North Dakota JUDD GREGG, New Hampshire DIANNE FEINSTEIN, California ROBERT F. BENNETT, Utah RICHARD J. DURBIN, Illinois BEN NIGHTHORSE CAMPBELL, Colorado TIM JOHNSON, South Dakota LARRY CRAIG, Idaho MARY L. LANDRIEU, Louisiana KAY BAILEY HUTCHISON, Texas JACK REED, Rhode Island MIKE DEWINE, Ohio TERRENCE E. SAUVAIN, Staff Director CHARLES KIEFFER, Deputy Staff Director STEVEN J. CORTESE, Minority Staff Director LISA SUTHERLAND, Minority Deputy Staff Director SUBCOMMITTEE ON TRANSPORTATION AND RELATED AGENCIES PATTY MURRAY, Washington, Chairman ROBERT C. -

Coast Guard Awards CIM 1560 25D(PDF)
Medals and Awards Manual COMDTINST M1650.25D MAY 2008 THIS PAGE INTENTIONALLY LEFT BLANK. Commandant 1900 Half Street, S.W. United States Coast Guard Washington, DC 20593-0001 Staff Symbol: CG-12 Phone: (202) 475-5222 COMDTINST M1650.25D 5 May 2008 COMMANDANT INSTRUCTION M1625.25D Subj: MEDALS AND AWARDS MANUAL 1. PURPOSE. This Manual publishes a revision of the Medals and Awards Manual. This Manual is applicable to all active and reserve Coast Guard members and other Service members assigned to duty within the Coast Guard. 2. ACTION. Area, district, and sector commanders, commanders of maintenance and logistics commands, Commander, Deployable Operations Group, commanding officers of headquarters units, and assistant commandants for directorates, Judge Advocate General, and special staff offices at Headquarters shall ensure that the provisions of this Manual are followed. Internet release is authorized. 3. DIRECTIVES AFFECTED. Coast Guard Medals and Awards Manual, COMDTINST M1650.25C and Coast Guard Rewards and Recognition Handbook, CG Publication 1650.37 are cancelled. 4. MAJOR CHANGES. Major changes in this revision include: clarification of Operational Distinguishing Device policy, award criteria for ribbons and medals established since the previous edition of the Manual, guidance for prior service members, clarification and expansion of administrative procedures and record retention requirements, and new and updated enclosures. 5. ENVIRONMENTAL ASPECTS/CONSIDERATIONS. Environmental considerations were examined in the development of this Manual and have been determined to be not applicable. 6. FORMS/REPORTS: The forms called for in this Manual are available in USCG Electronic Forms on the Standard Workstation or on the Internet: http://www.uscg.mil/forms/, CG Central at http://cgcentral.uscg.mil/, and Intranet at http://cgweb2.comdt.uscg.mil/CGFORMS/Welcome.htm. -

U.S. Coast Guard Boat Operations and Training (Boat) Manual, Volume Ii
U.S. Coast Guard Boat Operations and Training (BOAT) Manual Volume II “Train, Maintain, Operate” COMDTINST M16114.33D February 2020 Commandant US Coast Guard Stop 7324 United States Coast Guard 2703 Martin Luther King Jr Ave SE Washington, DC 20593-7324 Staff Symbol: CG-731 Phone: (202) 372-2515 COMDTINST M16114.33D 05 FEB 2020 COMMANDANT INSTRUCTION M16114.33D Subj: U.S. COAST GUARD BOAT OPERATIONS AND TRAINING (BOAT) MANUAL, VOLUME II Ref: a. U.S. Coast Guard Boat Operations and Training (BOAT) Manual Volume I, COMDTINST M16114.32 (series) b. Performance, Training, and Education Manual, COMDTINST M1500.10 (series) c. Rescue and Survival Systems Manual, COMDTINST M10470.10 (series) d. U.S. Coast Guard Boat Operations and Training (BOAT) Manual, Volume III, COMDTINST M16114.42 (series) e. U.S. Coast Guard Competency Dictionary f. U.S. Coast Guard Competency Management System Manual, COMDTINST M5300.2 (series) g. United States Coast Guard Regulations 1992, COMDTINST M5000.3 (series) h. Military Separations, COMDTINST M1000.4 (series) i. U.S. Coast Coast Guard Addendum to the National Search and Rescue Supplement (NSS) to the International Aeronautical and Maritime Search and Rescue Manual (IAMSAR), COMDTINST M16130.2 (series) j. Coast Guard Medical Manual, COMDTINST M6000.1 (series) k. Ordnance Manual, COMDTINST M8000.2 (series) l. Risk Management (RM), COMDTINST 3500.3 (series) m. Naval Engineering Manual, COMDTINST M9000.6 (series) n. Coatings and Color Manual, COMDTINST M10360.3 (series) DISTRIBUTION – SDL 170 a b c d e f g h i j k l m n o p q r s t u v w x y z A X X X X X X B X X X X C X X X X D X X E X X X X F G X X H X NON-STANDARD DISTRIBUTION LIST: COMDTINST M16114.33D 1. -

U.S. Coast Guard Port Security Unit History
U.S. Coast Guard Port Security Unit History Early Roots The roots of the Coast Guard's deployable port security mission are traced back to World War I and World War II and the traditional CONUS port safety and security duties of the Captain of the Port (COTP). During World War II, some overseas COTP-type operations were carried out by the Coast Guard in both the Pacific and European Theaters. Experiences in Vietnam demonstrated that a need for Coast Guard port security capabilities in overseas ports continued to exist. During the early 1980's, DoD planners formally identified the need for port security forces in OCONUS seaports of debarkation. Dialogue began between the Army, Navy, and Coast Guard, and the concept of the deployable Port Security Unit (PSU) was born. In January 1985 the Commandant approved three notional PSUs to respond to the requirements of DoD operations plans. The three units were located in the Ninth Coast Guard District at Buffalo, NY, Cleveland, OH, and Milwaukee, WI. Mission Defined PSUs are organized, equipped, and trained to operate in joint security areas, specifically in accessible (ice-free) harbors and port areas worldwide in support of regional Combatant Commanders’ requirements, and in company with DoD for national defense regional contingencies. PSUs provide 24-hour operations under all environmental conditions within the limits of equipment and personnel. PSUs normally protect vessels in transit, at the pier/port complex, or along the waterfront facility. Harbor defense and port security operations are frequently characterized by confined and traffic-congested water and air space. Notional Mission Assessment In the years between the approval of the three notional PSUs and their first deployment in 1990, the PSUs suffered from inconsistent budgetary, programmatic, and training support. -

Live Fire Corpsmen Qualifications Birthday Ball Annual Course Takes U.S
JUNE 26, 2015 PORT SECURITY PHOTO STORY PHOTO LIVE FIRE CORPSMEN QUALIFICATIONS BIRTHDAY BALL ANNUAL COURSE TAKES U.S. NAVAL HOSPITAL SERVICE COAST GUARDSMEN OFF SHORE, MEMBERS CELEBRATE 117 TESTS THEIR WEAPONS SKILLS YEARS OF SACRIFICE SOME GIFTS VOLLEYBALL TOURNAMENT CAN HURT LIBERTY CENTER SPONSORS BE MINDFUL OF GIFTS THAT A SANDY SPORTS BATTLE AT CAN TRIGGER GOVERNMENT G.J. DENICH GYM ETHICS, RULES VIOLATIONS CARIBBEAN-AMERICAN FLAG FOOTBALL HERITAGE MONTH CHAMPIONSHIP CELEBRATE THE DIVERSE HNL, GUNSLINGERS GO HEAD- COMMUNITY THAT HELPS MAKE TO-HEAD IN PIG-SKINNED UP GUANTANAMO BAY BATTLE AT COOPER FIELD LEADERSHIP SPOTLIGHT MORAL COURAGE DEFINES OUR CHARACTER, SERVICE character,” said Gen. Charles C. Krulak. Our mission reminds us to be constantly He goes on to say that moral cowards never vigilant and prepared for threats to our nation’s win in war; moral cowards never win in life. security and to cherish the gift of freedom that They might believe that they are winning a few we enjoy today. battles here and there, but their victories are To all Sailors, continue with your strong sense never sweet, they never stand the test of time of duty: honor, courage and commitment to the and never serve to inspire others. It takes moral United States Navy, NON SIBI SED PATRIAE, courage to hold your ideas above yourself. It is (not for self, but for country). Together, we the defining aspect of your character. So what define the American spirit through our strength. of your character, who are you really and what May god bless you and continue to bless our do you stand for? What is the essence of your wonderful country we have sworn an oath to character? Where is your moral compass pointing protect. -

The QUARTERDECK LOG Membership Publication of the Coast Guard Combat Veterans Association
the QUARTERDECK LOG Membership publication of the Coast Guard Combat Veterans Association. Publishes quarterly— Spring, Summer, Fall and Winter. Not sold on a subscription basis. The Coast Guard Combat Veterans Association is a Non-Profit Association of Active Duty, Retired, Reserve and Honorably Discharged Former Members of the United States Coast Guard who served in, or provided direct support to, combat situations recognized by an appropriate military award while serving as a member of the United States Coast Guard. Volume 33, Number 1 Spring 2018 USCGC JOSEPH GERCZAK COMMISSIONED AND HOMEPORTED IN HAWAII The new Sentinel Class Coast Guard Cutter Joseph Gerczak was commissioned March 9th, 2018 and is headed to Coast Guard Base Honolulu to begin its first deployment. The CGC Joseph Gerczak is a Fast Response Cutter with a maximum speed of 28 knots and a range of nearly 3,000 nautical miles, which is crucial to curbing illegal maritime activity. The Sentinel Class cutters perform or assist with a variety of missions, including law enforcement, counter-drug patrols, search and rescue, and enforcement of fisheries regulations. This new cutter was named in honor of Joseph Gerczak, who was killed during World War II while defending the tank landing ship USS LST-66 from a Japanese air attack during the American assault on Borgen Bay during the Battle of New Britain on December 26, 1943. (Story on Page 6) In This Issue: Cover Story Pages 1, 6-8 From The President Page 2, 3 From the Vice President Page 3 From the Secretary/Treasurer Page 4 Auxiliary News Page 5 Notices & Association News Pages 9-11 Convention information Pages 12-16 Featured Articles Pages 17-28 Sea Stories Page 29 Ship’s Store Page 30 CGCVA Membership Form Inside back-cover FROM THE NATIONAL PRESIDENT FROM THE NATIONAL PRESIDENT STEPHEN PETERSEN. -
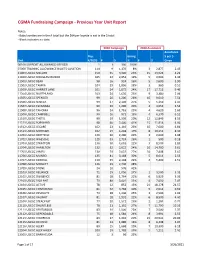
Previous Year 2020 Report
CGMA Fundraising Campaign ‐ Previous Year Unit Report Notes: ‐ Baby layettes are in the # total but the $64 per layette is not in the $ total. ‐ Blank indicates no data. 2020 Campaign 2020 Assistance Assistance Pop. Giving $ per $ Unit 4/2020 # $ %# $ Given 00100 SUPPORT ALLOWANCE‐OFFICER 1 1 300 100% 07000 TRAINING ALLOWANCE BILLETS‐AVIATION 114 9 1,176 8% 3 2,877 2.45 11403 USCGC MELLON 150 35 3,306 23% 15 13,924 4.21 11410 USCGC DOUGLAS MUNRO 165 32 2,952 19% 5 4,000 1.36 11501 USCGC BEAR 98 16 924 16% 5 3,600 3.90 11502 USCGC TAMPA 104 29 1,896 28% 3 960 0.51 11503 USCGC HARRIET LANE 101 24 1,872 24% 17 17,712 9.46 11504 USCGC NORTHLAND 103 24 1,656 23% 9 3,380 2.04 11505 USCGC SPENCER 99 26 1,200 26% 10 9,010 7.51 11506 USCGC SENECA 99 27 2,106 27% 5 5,150 2.45 11507 USCGC ESCANABA 99 20 1,200 20% 4 3,052 2.54 11508 USCGC TAHOMA 96 24 1,716 25% 4 4,620 2.69 11509 USCGC CAMPBELL 99 16 972 16% 4 6,370 6.55 11510 USCGC THETIS 99 20 1,506 20% 12 12,849 8.53 11511 USCGC FORWARD 98 40 2,400 41% 15 11,914 4.96 11512 USCGC LEGARE 102 23 1,116 23% 10 7,600 6.81 11513 USCGC MOHAWK 102 19 1,248 19% 8 10,352 8.30 11701 USCGC BERTHOLF 129 30 2,400 23% 3 2,600 1.08 11702 USCGC WAESCHE 129 33 2,724 26% 1 500 0.18 11703 USCGC STRATTON 136 30 4,692 22% 3 8,599 1.83 11704 USCGC HAMILTON 132 32 2,622 24% 10 14,700 5.61 11705 USCGC JAMES 130 29 2,052 22% 10 7,498 3.65 11706 USCGC MUNRO 135 41 3,168 30% 5 8,014 2.53 11707 USCGC KIMBALL 130 29 2,148 22% 2 5,400 2.51 11708 USCGC MIDGETT 126 35 2,730 28% 11709 USCGC STONE 24 10 576 42% 12101 USCGC RELIANCE -

Project Overview
U.S. Dept of Transportation United States Coast Guard Port Security Unit (PSU) Tactical Action Officer (TAO) Front End Analysis Report Performance Technology Center U.S. Coast Guard Training Center Yorktown, VA July 2002 TAO FEA Report Table of Contents Page Executive Summary Project Goal ……………………………....……………………………….. 2 Methodology ………………………….……………………………………. 2 Recommendations ………………….…………………………………….. 2 Project Background ..…………….....………………………………………. 4 Review of Alignment Requestor ………………………….………………………………………. 6 Roles in the Project ……………..………………………………………… 6 Project Responsibilities ………….……………………………………….. 6 Funding Agreements ……………………………………………………… 7 Scope ………………………………………………………………………. 7 Methodology Analysis Type ……………………………………………………………… 8 Documentation Reviewed ………………………………………………... 8 Selection of Accomplished Performers …………………………………. 10 Interviewees & Sites Visited ……………………………………………... 10 Major Accomplishments and Tasks ...............……………………………. 11 Findings ………………………………………………………………………. 13 Recommendations ...………………………………………………………... 17 Plans for Next Phase Next Phase ………………………………….…………………………… 21 Future Action ………………………………….…………….. 21 Coast Guard-wide Impact ………………………………….…………….. 22 Appendix A – Performance Interventions for Major Accomplishments 23 and Tasks Appendix B – Design Input for Performance Interventions 26 Appendix C – Positive and Negative Influences on Performance of 65 Tactical Action Officer (TAO) 1 TAO FEA Report Executive Summary Project Goal The goal of this analysis project was to determine the performance requirements -

MDI Process Guide
MISSION DEPENDENCY INDEX ASSESSMENT PROCESS GUIDE CGTO PG-43-00-40 July 3, 2008 MDI Process Guide TABLE OF CONTENTS CHAPTER 1: OVERVIEW .......................................................................................................................... 1 A. Purpose ............................................................................................................................................. 1 A.1 Scope ................................................................................................................................... 1 A.2 Objective ............................................................................................................................. 1 A.3 Applications ........................................................................................................................ 1 B. References ........................................................................................................................................ 2 C. Background ...................................................................................................................................... 2 D. Roles and Responsibilities ............................................................................................................... 3 E. Definitions ....................................................................................................................................... 4 CHAPTER 2: ASSESSMENT PROCEDURES ......................................................................................... -

Military Medals and Awards Manual, Comdtinst M1650.25E
Coast Guard Military Medals and Awards Manual COMDTINST M1650.25E 15 AUGUST 2016 COMMANDANT US Coast Guard Stop 7200 United States Coast Guard 2703 Martin Luther King Jr Ave SE Washington, DC 20593-7200 Staff Symbol: CG PSC-PSD-ma Phone: (202) 795-6575 COMDTINST M1650.25E 15 August 2016 COMMANDANT INSTRUCTION M1650.25E Subj: COAST GUARD MILITARY MEDALS AND AWARDS MANUAL Ref: (a) Uniform Regulations, COMDTINST M1020.6 (series) (b) Recognition Programs Manual, COMDTINST M1650.26 (series) (c) Navy and Marine Corps Awards Manual, SECNAVINST 1650.1 (series) 1. PURPOSE. This Manual establishes the authority, policies, procedures, and standards governing the military medals and awards for all Coast Guard personnel Active and Reserve and all other service members assigned to duty with the Coast Guard. 2. ACTION. All Coast Guard unit Commanders, Commanding Officers, Officers-In-Charge, Deputy/Assistant Commandants and Chiefs of Headquarters staff elements must comply with the provisions of this Manual. Internet release is authorized. 3. DIRECTIVES AFFECTED. Medals and Awards Manual, COMDTINST M1650.25D is cancelled. 4. DISCLAIMER. This guidance is not a substitute for applicable legal requirements, nor is it itself a rule. It is intended to provide operational guidance for Coast Guard personnel and is not intended to nor does it impose legally-binding requirements on any party outside the Coast Guard. 5. MAJOR CHANGES. Major changes to this Manual include: Renaming of the manual to distinguish Military Medals and Awards from other award programs; removal of the Recognition Programs from Chapter 6 to create the new Recognition Manual, COMDTINST M1650.26; removal of the Department of Navy personal awards information from Chapter 2; update to the revocation of awards process; clarification of the concurrent clearance process for issuance of awards to Coast Guard Personnel from other U.S. -

Coast Guard Operations During Operation Iraqi Freedom
CRM D0010862.A2/Final October 2004 Coast Guard Operations During Operation Iraqi Freedom Basil Tripsas • Patrick Roth • Renee Fye 4825 Mark Center Drive • Alexandria, Virginia 22311-1850 Approved for distribution: October 2004 This document represents the best opinion of CNA at the time of issue. It does not necessarily represent the opinion of the Department of the Navy. Distribution limited to DOD agencies. Specific authority: N00014-00-D-0700. For copies of this document call: CNA Document Control and Distribution Section at 703-824-2123. Copyright 2004 The CNA Corporation Contents Introduction . 1 Activities . 2 Summary of observations . 3 Data sources . 5 Interviews . 5 Messages and situation reports . 7 Reconstructions . 8 Coast Guard forces used in OIF . 9 Forces involved . 9 Units deployed to the Arabian Gulf . 10 Training and deployment . 17 Training & equipment . 17 Deployment. 18 Summary . 21 Command and control . 23 Chain of command. 23 Communications equipment and connectivity . 25 Operations . 27 Boutwell. 28 Walnut . 29 Patrol boats . 30 PSUs. 31 Summary . 33 Out-load security . 35 Summary of major issues . 39 Training . 39 Equipment . 40 i Supply. 41 Operations . 41 Appendix A . 45 Walnut . 45 Patrol boats . 46 Boutwell. 47 Port security Units . 48 Glossary . 49 References . 51 List of figures . 53 ii Introduction In late 2002, the United States Coast Guard (USCG) began prepara- tions for its participation in Operation Iraqi Freedom (OIF). This became its largest overseas deployment since the Vietnam War. The USCG sent two major cutters, a buoy tender, eight patrol boats, numerous port security units, and their support units out of country in support of this war. -

The QUARTERDECK LOG
the QUARTERDECK LOG Membership publication of the Coast Guard Combat Veterans Association. Publishes quarterly— Spring, Summer, Fall and Winter. Not sold on a subscription basis. The Coast Guard Combat Veterans Association is a Non-Profit Association of Active Duty, Retired, Reserve and Honorably Discharged Former Members of the United States Coast Guard who served in, or provided direct support to, combat situations recognized by an appropriate military award while serving as a member of the United States Coast Guard. Volume 33, Number 4 Winter 2018 COMMEMORATING COAST GUARD SERVICE IN VIETNAM MORE THAN 50 YEARS AGO AND REMEMBERING THE COAST GUARDSMEN WHO GAVE ALL IN SERVICE TO THE NATION On April 29, 1965, Coast Guard Squadron One was formed following President Johnson’s signing a Memorandum for the President that authorized the U.S. Coast Guard to assist U.S. Naval Forces operating off the coast of South Vietnam to prevent seaborne infiltration by communist forces of North Vietnam. President Johnson stated that the Coast Guard’s operating forces are “well-suited” for the mission. Squadron One (RONONE) consisted of 26 “Point” class 82 foot patrol boats, with 47 officers and 198 enlisted. During the five years of RONONE’s operations, these patrol craft designed for search and rescue and law enforcement, cruised more than four million miles, inspected over 280,000 vessels and were operational approximately 80 percent of their time in theater. (Cont’d page 9) In This Issue: Cover Story Pages 1, 9-18 From The President Page 2, 3 From the