Yan, Zheng Physical Layer Key Generation Between Backscatter Devices Over Ambient RF Signals
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SSA1208 / GES1005 – Everyday Life of Chinese Singaporeans: Past and Present
SSA1208 / GES1005 – Everyday Life of Chinese Singaporeans: Past and Present Group Essay Ho Lim Keng Temple Prepared By: Tutorial [D5] Chew Si Hui (A0130382R) Kwek Yee Ying (A0130679Y) Lye Pei Xuan (A0146673X) Soh Rolynn (A0130650W) Submission Date: 31th March 2017 1 Content Page 1. Introduction to Ho Lim Keng Temple 3 2. Exterior & Courtyard 3 3. Second Level 3 4. Interior & Main Hall 4 5. Main Gods 4 6. Secondary Gods 5 7. Our Views 6 8. Experiences Encountered during our Temple Visit 7 9. References 8 10. Appendix 8 2 1. Introduction to Ho Lim Keng Temple Ho Lim Keng Temple is a Taoist temple and is managed by common surname association, Xu (许) Clan. Chinese clan associations are benevolent organizations of popular origin found among overseas Chinese communities for individuals with the same surname. This social practice arose several centuries ago in China. As its old location was acquisited by the government for redevelopment plans, they had moved to a new location on Outram Hill. Under the leadership of 许木泰宗长 and other leaders, along with the clan's enthusiastic response, the clan managed to raise a total of more than $124,000, and attained their fundraising goal for the reconstruction of the temple. Reconstruction works commenced in 1973 and was completed in 1975. Ho Lim Keng Temple was advocated by the Xu Clan in 1961, with a board of directors to manage internal affairs. In 1966, Ho Lim Keng Temple applied to the Registrar of Societies and was approved on February 28, 1967 and then was published in the Government Gazette on March 3. -

I Want to Be More Hong Kong Than a Hongkonger”: Language Ideologies and the Portrayal of Mainland Chinese in Hong Kong Film During the Transition
Volume 6 Issue 1 2020 “I Want to be More Hong Kong Than a Hongkonger”: Language Ideologies and the Portrayal of Mainland Chinese in Hong Kong Film During the Transition Charlene Peishan Chan [email protected] ISSN: 2057-1720 doi: 10.2218/ls.v6i1.2020.4398 This paper is available at: http://journals.ed.ac.uk/lifespansstyles Hosted by The University of Edinburgh Journal Hosting Service: http://journals.ed.ac.uk/ “I Want to be More Hong Kong Than a Hongkonger”: Language Ideologies and the Portrayal of Mainland Chinese in Hong Kong Film During the Transition Charlene Peishan Chan The years leading up to the political handover of Hong Kong to Mainland China surfaced issues regarding national identification and intergroup relations. These issues manifested in Hong Kong films of the time in the form of film characters’ language ideologies. An analysis of six films reveals three themes: (1) the assumption of mutual intelligibility between Cantonese and Putonghua, (2) the importance of English towards one’s Hong Kong identity, and (3) the expectation that Mainland immigrants use Cantonese as their primary language of communication in Hong Kong. The recurrence of these findings indicates their prevalence amongst native Hongkongers, even in a post-handover context. 1 Introduction The handover of Hong Kong to the People’s Republic of China (PRC) in 1997 marked the end of 155 years of British colonial rule. Within this socio-political landscape came questions of identification and intergroup relations, both amongst native Hongkongers and Mainland Chinese (Tong et al. 1999, Brewer 1999). These manifest in the attitudes and ideologies that native Hongkongers have towards the three most widely used languages in Hong Kong: Cantonese, English, and Putonghua (a standard variety of Mandarin promoted in Mainland China by the Government). -

The Later Han Empire (25-220CE) & Its Northwestern Frontier
University of Pennsylvania ScholarlyCommons Publicly Accessible Penn Dissertations 2012 Dynamics of Disintegration: The Later Han Empire (25-220CE) & Its Northwestern Frontier Wai Kit Wicky Tse University of Pennsylvania, [email protected] Follow this and additional works at: https://repository.upenn.edu/edissertations Part of the Asian History Commons, Asian Studies Commons, and the Military History Commons Recommended Citation Tse, Wai Kit Wicky, "Dynamics of Disintegration: The Later Han Empire (25-220CE) & Its Northwestern Frontier" (2012). Publicly Accessible Penn Dissertations. 589. https://repository.upenn.edu/edissertations/589 This paper is posted at ScholarlyCommons. https://repository.upenn.edu/edissertations/589 For more information, please contact [email protected]. Dynamics of Disintegration: The Later Han Empire (25-220CE) & Its Northwestern Frontier Abstract As a frontier region of the Qin-Han (221BCE-220CE) empire, the northwest was a new territory to the Chinese realm. Until the Later Han (25-220CE) times, some portions of the northwestern region had only been part of imperial soil for one hundred years. Its coalescence into the Chinese empire was a product of long-term expansion and conquest, which arguably defined the egionr 's military nature. Furthermore, in the harsh natural environment of the region, only tough people could survive, and unsurprisingly, the region fostered vigorous warriors. Mixed culture and multi-ethnicity featured prominently in this highly militarized frontier society, which contrasted sharply with the imperial center that promoted unified cultural values and stood in the way of a greater degree of transregional integration. As this project shows, it was the northwesterners who went through a process of political peripheralization during the Later Han times played a harbinger role of the disintegration of the empire and eventually led to the breakdown of the early imperial system in Chinese history. -

中国人的姓名 王海敏 Wang Hai Min
中国人的姓名 王海敏 Wang Hai min last name first name Haimin Wang 王海敏 Chinese People’s Names Two parts Last name First name 姚明 Yao Ming Last First name name Jackie Chan 成龙 cheng long Last First name name Bruce Lee 李小龙 li xiao long Last First name name The surname has roughly several origins as follows: 1. the creatures worshipped in remote antiquity . 龙long, 马ma, 牛niu, 羊yang, 2. ancient states’ names 赵zhao, 宋song, 秦qin, 吴wu, 周zhou 韩han,郑zheng, 陈chen 3. an ancient official titles 司马sima, 司徒situ 4. the profession. 陶tao,钱qian, 张zhang 5. the location and scene in residential places 江jiang,柳 liu 6.the rank or title of nobility 王wang,李li • Most are one-character surnames, but some are compound surname made up of two of more characters. • 3500Chinese surnames • 100 commonly used surnames • The three most common are 张zhang, 王wang and 李li What does my name mean? first name strong beautiful lively courageous pure gentle intelligent 1.A person has an infant name and an official one. 2.In the past,the given names were arranged in the order of the seniority in the family hierarchy. 3.It’s the Chinese people’s wish to give their children a name which sounds good and meaningful. Project:Search on-Line www.Mandarinintools.com/chinesename.html Find Chinese Names for yourself, your brother, sisters, mom and dad, or even your grandparents. Find meanings of these names. ----What is your name? 你叫什么名字? ni jiao shen me ming zi? ------ 我叫王海敏 wo jiao Wang Hai min ------ What is your last name? 你姓什么? ni xing shen me? (你贵姓?)ni gui xing? ------ 我姓 王,王海敏。 wo xing wang, Wang Hai min ----- What is your nationality? 你是哪国人? ni shi na guo ren? ----- I am chinese/American 我是中国人/美国人 Wo shi zhong guo ren/mei guo ren 百家 姓 bai jia xing 赵(zhào) 钱(qián) 孙(sūn) 李(lǐ) 周(zhōu) 吴(wú) 郑(zhèng) 王(wán 冯(féng) 陈(chén) 褚(chǔ) 卫(wèi) 蒋(jiǎng) 沈(shěn) 韩(hán) 杨(yáng) 朱(zhū) 秦(qín) 尤(yóu) 许(xǔ) 何(hé) 吕(lǚ) 施(shī) 张(zhāng). -
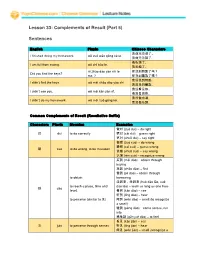
Lesson 33: Complements of Result (Part 5) Sentences
Lesson 33: Complements of Result (Part 5) Sentences English Pinyin Chinese Characters 我做完功课了。 I finished doing my homework. wǒ zuò wán ɡōnɡ kè le. 我做完功課了。 我吃饱了。 I am full from eating. wǒ chī bǎo le. 我吃飽了。 nǐ zhǎo dào yào shi le 你找到钥匙了吗? Did you find the keys? mɑ ? 你找到鑰匙了嗎? 我没找到钥匙。 I didn’t find the keys. wǒ méi zhǎo dào yào shi. 我沒找到鑰匙。 我没看见你。 I didn’t see you. wǒ méi kàn jiàn nǐ. 我沒看見你。 我没做功课。 I didn’t do my homework. wǒ méi zuò ɡōnɡ kè. 我沒做功課。 Common Complements of Result (Resultative Suffix) Characters Pinyin Meaning Examples 做对 (zuò duì) – do right 对 duì to do correctly 猜对 (cāi duì) – guess right 说对 (shuō duì) – say right 做错 (zuò cuò) – do wrong 猜错 (cāi cuò) – guess wrong 错 cuò to do wrong, to be mistaken 说错 (shuō cuò) – say wrong 认错 (rèn cuò) – recognize wrong 买到 (mǎi dào) – obtain through buying 找到 (zhǎo dào) – find 借到 (jiè dào) – obtain through to obtain borrowing 活到老,学到老 (huó dào lǎo, xué to reach a place, time and dào lǎo) – learn as long as one lives 到 dào level, 看到 (kàn dào) – see 听到 (tīng dào) – hear to perceive (similar to 见) 闻到 (wén dào) – smell (to recognize a smell) 碰到 (pèng dào) – come across, run into 感觉到 (gǎn jué dào) – to feel 看见 (kàn jiàn) – see 见 jiàn to perceive through senses 听见 (tīng jiàn) – hear 闻见 (wén jiàn) – smell (recognize a smell) 碰见 (pèng jiàn) – run into / to come across 学会 (xué huì) – know how through learning know how to (do something) 看会 (kàn huì) – know how through 会 huì have the ability to do sth reading 听会 (tīng huì) – know how through listening 分成 (fēn chéng) – divide into 切成 (qiē chéng) – cut into 看成 (kàn chéng) –view (something) as 变成 (biàn chéng) – change to, to change or turn something 成 chéng convert to into something else 翻译成 (fān yì chéng) – translate to 说成 (shuō chéng) – describe as 当成 (dāng chéng ) – treat as 想像成 (xiǎng xiàng chéng) – imagine as 吃完 (chī wán) – finish eating 做完 (zuò wán) – finish doing 完 wán to finish 写完 (xiě wán) – finish writing 卖完 (mài wán) – finish selling (sold out) 准备好 (zhǔn bèi hǎo) – ready The action is finished. -

• Xue Long 2 Sea Trials Successfully Completed • New LNG Bunkering Vessel Concept • Boris Sokolov Tested in Arctic Ice • Ice Load Monitoring System Installed
Arctic Passion News No. 2 | 2019 | issue 18 • Xue Long 2 sea trials successfully completed • New LNG bunkering vessel concept • Boris Sokolov tested in arctic ice • Ice Load Monitoring System installed In this issue Page 4 Page 8 Page 10 Page 16 Xue Long 2 enters into service LNG bunkering Full-scale ice trials Ice load monitoring vessel system installed Table of contents Front cover China’s first domestically built icebreaking research vessel, Xue Long 2, successfully completed her sea From the Managing Director.................................. 3 trials in June this year, where all design requirements Xue Long 2 enters into service............................... 4 were verified. She was delivered in July at the Jiangnan Shipyard in China and will in October depart for her LNG bunkering vessel for use in ice....................... 8 maiden voyage to Antarctica, where the full-scale ice Boris Sokolov in ice trials...................................... 10 trials will take place. Read more on page 4. Full-scale tests for passenger ferries................…. 13 Ice risk assessment of Qajaq W........................ ….15 Ice Load Monitoring System installed ..................16 Contact details EEDI ships need more assistance..........................18 AKER ARCTIC TECHNOLOGY INC EEDI bow with better ice performance.................19 Merenkulkijankatu 6, FI-00980 HELSINKI Lower steel weight is possible.............................. 20 Tel.: +358 10 323 6300 Measurement methods for brash ice.................... 21 Fax: +358 10 323 6400 Announcements.................................................... 23 www.akerarctic.fi News in brief......................................................... 23 Arctic Passion Seminar 2019................................. 24 Join our subscription list Our services Please send your message to www.akerarctic.fi [email protected] 17 – 18 September Gastech, Houston, USA Meet us here 17 – 20 September NEVA 2019, St. -

Origin Narratives: Reading and Reverence in Late-Ming China
Origin Narratives: Reading and Reverence in Late-Ming China Noga Ganany Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in the Graduate School of Arts and Sciences COLUMBIA UNIVERSITY 2018 © 2018 Noga Ganany All rights reserved ABSTRACT Origin Narratives: Reading and Reverence in Late Ming China Noga Ganany In this dissertation, I examine a genre of commercially-published, illustrated hagiographical books. Recounting the life stories of some of China’s most beloved cultural icons, from Confucius to Guanyin, I term these hagiographical books “origin narratives” (chushen zhuan 出身傳). Weaving a plethora of legends and ritual traditions into the new “vernacular” xiaoshuo format, origin narratives offered comprehensive portrayals of gods, sages, and immortals in narrative form, and were marketed to a general, lay readership. Their narratives were often accompanied by additional materials (or “paratexts”), such as worship manuals, advertisements for temples, and messages from the gods themselves, that reveal the intimate connection of these books to contemporaneous cultic reverence of their protagonists. The content and composition of origin narratives reflect the extensive range of possibilities of late-Ming xiaoshuo narrative writing, challenging our understanding of reading. I argue that origin narratives functioned as entertaining and informative encyclopedic sourcebooks that consolidated all knowledge about their protagonists, from their hagiographies to their ritual traditions. Origin narratives also alert us to the hagiographical substrate in late-imperial literature and religious practice, wherein widely-revered figures played multiple roles in the culture. The reverence of these cultural icons was constructed through the relationship between what I call the Three Ps: their personas (and life stories), the practices surrounding their lore, and the places associated with them (or “sacred geographies”). -

A Hypothesis on the Origin of the Yu State
SINO-PLATONIC PAPERS Number 139 June, 2004 A Hypothesis on the Origin of the Yu State by Taishan Yu Victor H. Mair, Editor Sino-Platonic Papers Department of East Asian Languages and Civilizations University of Pennsylvania Philadelphia, PA 19104-6305 USA [email protected] www.sino-platonic.org SINO-PLATONIC PAPERS FOUNDED 1986 Editor-in-Chief VICTOR H. MAIR Associate Editors PAULA ROBERTS MARK SWOFFORD ISSN 2157-9679 (print) 2157-9687 (online) SINO-PLATONIC PAPERS is an occasional series dedicated to making available to specialists and the interested public the results of research that, because of its unconventional or controversial nature, might otherwise go unpublished. The editor-in-chief actively encourages younger, not yet well established, scholars and independent authors to submit manuscripts for consideration. Contributions in any of the major scholarly languages of the world, including romanized modern standard Mandarin (MSM) and Japanese, are acceptable. In special circumstances, papers written in one of the Sinitic topolects (fangyan) may be considered for publication. Although the chief focus of Sino-Platonic Papers is on the intercultural relations of China with other peoples, challenging and creative studies on a wide variety of philological subjects will be entertained. This series is not the place for safe, sober, and stodgy presentations. Sino- Platonic Papers prefers lively work that, while taking reasonable risks to advance the field, capitalizes on brilliant new insights into the development of civilization. Submissions are regularly sent out to be refereed, and extensive editorial suggestions for revision may be offered. Sino-Platonic Papers emphasizes substance over form. We do, however, strongly recommend that prospective authors consult our style guidelines at www.sino-platonic.org/stylesheet.doc. -

Names of Chinese People in Singapore
101 Lodz Papers in Pragmatics 7.1 (2011): 101-133 DOI: 10.2478/v10016-011-0005-6 Lee Cher Leng Department of Chinese Studies, National University of Singapore ETHNOGRAPHY OF SINGAPORE CHINESE NAMES: RACE, RELIGION, AND REPRESENTATION Abstract Singapore Chinese is part of the Chinese Diaspora.This research shows how Singapore Chinese names reflect the Chinese naming tradition of surnames and generation names, as well as Straits Chinese influence. The names also reflect the beliefs and religion of Singapore Chinese. More significantly, a change of identity and representation is reflected in the names of earlier settlers and Singapore Chinese today. This paper aims to show the general naming traditions of Chinese in Singapore as well as a change in ideology and trends due to globalization. Keywords Singapore, Chinese, names, identity, beliefs, globalization. 1. Introduction When parents choose a name for a child, the name necessarily reflects their thoughts and aspirations with regards to the child. These thoughts and aspirations are shaped by the historical, social, cultural or spiritual setting of the time and place they are living in whether or not they are aware of them. Thus, the study of names is an important window through which one could view how these parents prefer their children to be perceived by society at large, according to the identities, roles, values, hierarchies or expectations constructed within a social space. Goodenough explains this culturally driven context of names and naming practices: Department of Chinese Studies, National University of Singapore The Shaw Foundation Building, Block AS7, Level 5 5 Arts Link, Singapore 117570 e-mail: [email protected] 102 Lee Cher Leng Ethnography of Singapore Chinese Names: Race, Religion, and Representation Different naming and address customs necessarily select different things about the self for communication and consequent emphasis. -

LIU Brooklyn
LIU Brooklyn 2018 - 2019 Undergraduate Bulletin 1 University Plaza, Brooklyn, N.Y. 11201-5372 General Information: 718-488-1000 www.liu.edu/brooklyn Admissions: 718-488-1011 Email: [email protected] Notice to Students: The information in this publication is accurate as of September 1, 2018. However, circumstances may require that a given course be withdrawn or alternate offerings be made. Therefore, LIU reserves the right to amend the courses described herein and cannot guarantee enrollment into any specific course section. All applicants are reminded that the University is subject to policies promulgated by its Board of Trustees, as well as New York State and federal regulation. The University therefore reserves the right to effect changes in the curriculum, administration, tuition and fees, academic schedule, program offerings and other phases of school activity, at any time, without prior notice. The University assumes no liability for interruption of classes or other instructional activities due to fire, flood, strike, war or other force majeure. The University expects each student to be knowledgeable about the information presented in this bulletin and other official publications pertaining to his/her course of study and campus life. For additional information or specific degree requirements, prospective students should call the campus Admissions Office. Registered students should speak with their advisors. Bulletin 2018 - 2019 AWARDS 25 TABLE OF CONTENTS Departmental Awards 25 LIU 4 Special Awards 25 ABOUT LIU BROOKLYN 5 Blackbird Leadership Awards 27 Mission Statement 5 Athletic Awards 27 Overview 5 REGISTRATION 28 Undergraduate and Graduate Offerings 5 Course Registration 28 University Policies 6 Matriculation 28 DIRECTORY 7 Leave of Absence 28 ACADEMIC CALENDAR 2018-2019 9 Withdrawal 28 ADMISSION 11 Auditing of Courses 29 Freshman Admissions 11 Student Access to Educational Records 29 Advanced Standing 11 Administrative Matters 30 Program for Academic Success 11 TUITION AND FEES 31 International Admissions 12 Rate Schedule 31 Arthur O. -

A Comparison of the Korean and Japanese Approaches to Foreign Family Names
15 A Comparison of the Korean and Japanese Approaches to Foreign Family Names JIN Guanglin* Abstract There are many foreign family names in Korean and Japanese genealogies. This paper is especially focused on the fact that out of approximately 280 Korean family names, roughly half are of foreign origin, and that out of those foreign family names, the majority trace their beginnings to China. In Japan, the Newly Edited Register of Family Names (新撰姓氏錄), published in 815, records that out of 1,182 aristocratic clans in the capital and its surroundings, 326 clans—approximately one-third—originated from China and Korea. Does the prevalence of foreign family names reflect migration from China to Korea, and from China and Korea to Japan? Or is it perhaps a result of Korean Sinophilia (慕華思想) and Japanese admiration for Korean and Chinese cultures? Or could there be an entirely distinct explanation? First I discuss premodern Korean and ancient Japanese foreign family names, and then I examine the formation and characteristics of these family names. Next I analyze how migration from China to Korea, as well as from China and Korea to Japan, occurred in their historical contexts. Through these studies, I derive answers to the above-mentioned questions. Key words: family names (surnames), Chinese-style family names, cultural diffusion and adoption, migration, Sinophilia in traditional Korea and Japan 1 Foreign Family Names in Premodern Korea The precise number of Korean family names varies by record. The Geography Annals of King Sejong (世宗實錄地理志, 1454), the first systematic register of Korean family names, records 265 family names, but the Survey of the Geography of Korea (東國輿地勝覽, 1486) records 277. -

A Guide to Names and Naming Practices
March 2006 AA GGUUIIDDEE TTOO NN AAMMEESS AANNDD NNAAMMIINNGG PPRRAACCTTIICCEESS This guide has been produced by the United Kingdom to aid with difficulties that are commonly encountered with names from around the globe. Interpol believes that member countries may find this guide useful when dealing with names from unfamiliar countries or regions. Interpol is keen to provide feedback to the authors and at the same time develop this guidance further for Interpol member countries to work towards standardisation for translation, data transmission and data entry. The General Secretariat encourages all member countries to take advantage of this document and provide feedback and, if necessary, updates or corrections in order to have the most up to date and accurate document possible. A GUIDE TO NAMES AND NAMING PRACTICES 1. Names are a valuable source of information. They can indicate gender, marital status, birthplace, nationality, ethnicity, religion, and position within a family or even within a society. However, naming practices vary enormously across the globe. The aim of this guide is to identify the knowledge that can be gained from names about their holders and to help overcome difficulties that are commonly encountered with names of foreign origin. 2. The sections of the guide are governed by nationality and/or ethnicity, depending on the influencing factor upon the naming practice, such as religion, language or geography. Inevitably, this guide is not exhaustive and any feedback or suggestions for additional sections will be welcomed. How to use this guide 4. Each section offers structured guidance on the following: a. typical components of a name: e.g.