Kca University
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
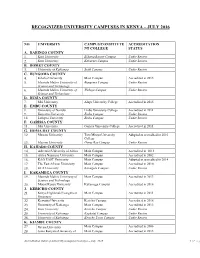
Recognized University Campuses in Kenya – July 2016
RECOGNIZED UNIVERSITY CAMPUSES IN KENYA – JULY 2016 NO. UNIVERSITY CAMPUS/CONSTITUTE ACCREDITATION NT COLLEGE STATUS A. BARINGO COUNTY 1. Kisii University Eldama Ravine Campus Under Review 2. Kisii University Kabarnet Campus Under Review B. BOMET COUNTY 3. University of Kabianga Sotik Campus Under Review C. BUNGOMA COUNTY 4. Kibabii University Main Campus Accredited in 2015 5. Masinde Muliro University of Bungoma Campus Under Review Science and Technology 6. Masinde Muliro University of Webuye Campus Under Review Science and Technology D. BUSIA COUNTY 7. Moi University Alupe University College Accredited in 2015 E. EMBU COUNTY 8. University of Nairobi Embu University College Accredited in 2011 9. Kenyatta University Embu Campus Under Review 10. Laikipia University Embu Campus Under Review F. GARISSA COUNTY 11. Moi University Garissa University College Accredited in 2011 G. HOMA BAY COUNTY 12. Maseno University Tom Mboya University Adopted as accredited in 2016 College 13. Maseno University Homa Bay Campus Under Review H. KAJIADO COUNTY 14. Adventist University of Africa Main Campus Accredited in 2013 15. Africa Nazarene University Main Campus Accredited in 2002 16. KAG EAST University Main Campus Adopted as accredited in 2014 17. The East African University Main Campus Accredited in 2010 18. KCA University Kitengela Campus Under Review I. KAKAMEGA COUNTY 19. Masinde Muliro University of Main Campus Accredited in 2013 Science and Technology 20. Mount Kenya University Kakamega Campus Accredited in 2016 J. KERICHO COUNTY 21. Kenya Highlands Evangelical Main Campus Accredited in 2011 University 22. Kenyatta University Kericho Campus Accredited in 2016 23. University of Kabianga Main Campus Accredited in 2013 24. -

MKU Career Prospectus for High School Students
www.mku.ac.ke/ mountkenyauniversity MountKenyaUni MKU Career Prospectus Mount Kenya University for High School Students Developed in conjunction with January 2021 Edition VISION MISSION PHILOSOPHY To be a Global To provide world To harness Hub of Excellence class education, knowledge in in Education, research and applied Sciences Research innovation for global and Technology and Innovation. transformation for the service of and sustainable humanity development CORE VALUES The University’s core values that form the basis of engagement, teaching and learning are: • Innovation • Integrity • Academic freedom • Equity • Competitiveness ACADEMIC CHARACTER With an emphasis on science, technology and humanities, Mount Kenya University offers an all-rounded education including moral and professional education to all persons degree courses MKU graduates ready for the job market and wealth creation VISION MISSION PHILOSOPHY To be a Global To provide world To harness Contents Hub of Excellence class education, knowledge in Students Life: A Home from Home ........................................ 1 in Education, research and applied Sciences Research innovation for global and Technology Welcome by Chancellor............................................................ 2 and Innovation. transformation for the service of Word by Vice-Chancellor ......................................................... 3 and sustainable humanity development Experts rank MKU ................................................................. 5 Testimonials ........................................................................ -

Michael Mbira Mboya P.0
Michael Mbira Mboya P.0. Box 2580 – 40100, Kisumu, Kenya E-mail Address: [email protected] Mobile No: (+254) 726 117 640 or (+254) 736 117 640 1.0 Personal Information Current Employer: University of Nairobi Position: Senior ICT Officer Qualifications: Diploma, Bsc, MA Nationality: Kenyan Gender: Male Date of Birth: February 21, 1985 2.0 Education History 2.1 Academic Background Period Institution Qualification 2016 - 2018 University of Nairobi M.A in Project Planning and Management 2012 - 2015 KCA University BSc in Information Technology 2006 – 2008 Strathmore University Diploma in Business Information Technology 2001 – 2004 St. Josephs’ High KCSE School, Rapogi 2.2 Professional Certifications and Training Year Institution Certification/Training 2019 Kenya Institute of Management Monitoring and Evaluation 2019 Kenya Institute of Management Strategic Management and Leadership 2019 Techno Brain ITIL 4 Foundation Cisco Certified Networking Associate 2008 Strathmore University (Academy - Level 1, 2 & 3) 2006 Strathmore University IT Essentials I – PC Hardware and Software Curriculum Vitae - Michael M. Mboya Page 1 of 3 3.0 Positions and Work Experience 3.1 2016 – Date: Senior ICT Officer 3.2 2018 – Date: Ag. Campus Administrator 3.3 2016: Campus Administrator 3.4 2010 – 2015: Administrative Assistant 4.0 University Committees Served 4.1 April 2019: Chairman, Quotation Opening Committee 4.2 2018 & 2019: Secretary, Campus Quality Assurance Committee 4.3 2018 & 2019: Member, Campus Anti-corruption Committee 4.4 2018 & 2019: Co-Chairperson, Campus Marketing Committee 4.5 2018 & 2019: Secretary, Campus Executive Management Committee 4.6 2018 & 2019: Secretary, Campus Management Committee 4.7 2017, 2018 & 2019: Secretary, Campus Executive Management Committee 4.8 2017, 2018 & 2019: Inspection and Acceptance Committee 4.9 June 2018: Chairman, Quotation Processing Committee 4.10 2015, 2016 & 2017: Member, Campus Marketing Committee 5.0 Trainings, Seminars and Workshops attended 5.1 Re-engineered Human Resource Information System (HRMIS). -

N O Institution's Name Public University 1 Chuka University 2 Dedan Kimathi University of Technology 3 Egerton University 4 Ja
N Institution’s Name o Public University 1 Chuka University 2 Dedan Kimathi University of Technology 3 Egerton University 4 Jaramogi Oginga Odinga University of Science and Technology 5 Jomo Kenyatta University of Agriculture & Technology (JKUAT) 6 Karatina University 7 Kenyatta University 8 Kisii University 9 Laikipia University 10 Masai Mara University 11 Maseno University 12 Masinde Muliro University of Science and Technology 13 Meru University of Science and Technology 14 Moi University 15 Multi Media University 16 Pwani University 17 South Eastern Kenya University 18 Technical Univeristy of Mombasa 19 Technical University of Kenya 20 University of Eldoret 21 University of Kabianga 22 University of Nairobi Private University 23 Adventist University of Africa 24 Africa International University 25 Africa Nazarene University 26 Aga Khan University 27 Catholic University Of Eastern Africa 28 Daystar University 29 East African University 30 Great Lakes University 31 International University of Professional Studies 32 International Leadership University 33 Kabarak University 34 KCA University 35 Kenya Methodist University 36 Mount Kenya University 37 Pan Africa Christian University 38 Pioneer International University 39 Scott Christian University 40 St Paul's University 41 Strathmore University 42 The Management University of Africa 43 The Presbyterian University of East Africa 44 Umma University 45 United States International University 46 University of Eastern Africa, Baraton University College 47 Co-operative University College 48 Embu -

Prof. William Wanjala Toili Date of Birth
1 PROFILE OF WILLIAM WANJALA TOILI PERSONAL DETAILS FULL NAME : PROF. WILLIAM WANJALA TOILI DATE OF BIRTH : 18TH APRIL 1953 NATIONALITY : Kenyan, ID NO 6140801; Passport No. A1186400 MARITAL STATUS : Married PLACE OF WORK: Masinde Muliro University of Science and Technology (MMUST) Department of Science and Mathematics Education P.O. Box 190 -50100 KAKAMEGA, KENYA Tel. (056) 20724, Mobile 0718-504614/0775-218078 Fax (056) 30153 E-mail: [email protected] CURRENT APPOINTMENT: Associate Professor in Science and Environmental Education, Department of Science and Mathematics Education Masinde Muliro University of Science & Technology CAREER GOAL : To effectively conduct research, teach and disseminate knowledge and skills in order to empower humanity to realize their potential and control their destiny. SPECIAL SKILLS - Communicates well in English, Kiswahili and Luhya - Setting personal and organizational goals and effectively implementing them. - Conducting informed guidance and counseling of both youths and adults. - Preparing effective academic and small scale research proposals and writing comprehensive reports - Developing and evaluating academic programs at all levels and sectors of education. - Citizenship action skills such as mobilizing people to conduct informed environmental conservation. - Organizing successful seminars/workshops/training. - Preparing effective institutional strategic plans. EDUCATION AND ACADEMIC QUALIFICATION 1994 – 2001: Doctor of Philosophy in Science and Environmental Education; Maseno University, Kenya. Awarded November, 2001 1988 - 1989 : Master of Education in Science and Environmental Education, School of Education, University of Leeds, England, U.K. Awarded May, 1990. 1987 : Postgraduate Certificate in Environmental Education, Moi University, Kenya. Awarded 1993. 1 2 1983 - 1985 : Master of Education in Teacher Education (Science Education and Curriculum Development); University of Nairobi, Kenya. -

Is It Terrorism Or Economic Sabotage?
KHRC’s 2014-2018 Also Inside: The Truth about Marriage Bill; Strategic Plan: discussed by the Kenyatta "...The KHRC is permanent, University Legal Aid Clinic. The issue of Anglo-Leasing, By irreversible and Mr. Joseph Agwata (KUSOL irrevocable.” Alumni) Page | 1 Is It Terrorism or Economic Sabotage? Join the conversation facebook.com/kenyanlegal; twitter.com/The_Kenyan_Legal There’s more things in Heaven and Earth than what's dreamt of in Philosophy, and on Page | 2 the other hand, Religion is what keeps the poor from killing the rich, but certainly, is there more to the Islam religion and the Salafi philosophy/ideology than to just killing in the name of ‘God’? and why Kenya in particular? What makes the other East African countries out of the premium? Find out in this issue. Now, since the whole world is watching, we at Kenyan Legal want to always give you something special; something good, like a river glory, and in that spirit, I introduce to you our panel members of the Reviewer Feedback Programme, the Kenyatta University Legal Aid Clinic, and the strategic Plan 2014-2018 of the Kenya Human Rights Commission(KHRC),and as Prof. Makau Mutua once stated,"...The KHRC is permanent, irreversible and irrevocable.”, we share the same optimism. Still progressing to give you nothing short of the best, this is Issue #8 of the Kenyan Legal Magazine; Real Kenya, Real Issues. Welcome. REGARDS, Michael Michael Opondo O. www.michaelopondo.wordpress.com Managing Editor, KENYAN LEGAL The Kenyan Legal Team The Branch Co-Ordinators The Secretariat Kenneth Kimathi: Kenyatta University Michael O. -

Influence of Media Training on the Competence of Journalists in Kenya
Influence of Media Training on the Competence of Journalists in Kenya: Perceptions of Standard Group Limited Managers and Senior Journalists Amukuzi, Marion1, Kuria, Githinji Martin2 Riara University, Kenya1, Karatina University, Kenya2 Correspondence: [email protected] Abstract A number of researches have indicated that training institutions have failed to impart skills and knowledge to students that would be transferred to the industry upon graduation and employment, hence the quality of journalists graduating is wanting. The purpose of this study was to investigate the influence of media training on the competency of journalists in Kenya. Curricula were sampled from selected Kenyan universities and adequacy of training material investigated. Non-probability sampling procedure involving purposive and snow-ball sampling methods were used to identify the 9 participants comprising media managers and senior journalists in one media organization. Data was analysed thematically and presented in a narrative form in accordance with the themes. According to the SG media managers and senior journalists, journalists trained in Kenya lack practical skills required in the job market. Consequently, media houses are recruiting graduates in other disciplines such as English, Medicine, and Law while others have resorted to re-training the new recruits. It is recommended that media training institutions, regulators and other stakeholders should revamp existing curricula with the view to making them competency based. Keyword: Influence of Media, Journalists, Perceptions Standard Group Limited, Managers and Senior Journalists. Introduction and Background of the Study The performance of media in Kenya is closely related to the level of journalism training where appropriate training provides students with knowledge and skills to write accurate, fair, balanced and impartial stories (Mbeke, 2010). -

BUSALILE JACK MWIMALI B.A.L., LL.B., LL.M., Phd, AIII, ADV
BUSALILE JACK MWIMALI B.A.L., LL.B., LL.M., PhD, AIII, ADV. ADDRESS Permanent Office P.O. Box 184, Goretti Munialo Mwimali & Co Adv Village Market, Uchumi House, 14th Flr Nairobi, Kenya P.O. Box 722 - 00100 Tel. +254720741027 Nairobi, Kenya Nationality: Kenyan Date of Birth: 25th Jan 1977 Gender: Male Marital Status: Married with one son Religion: Christian; Protestant OBJECTIVE To pursue an intellectually stimulating career and actualise a self-motivated professional life, in legal practice and research which would ensure a productive and gratifying outcome beneficial to me, my family and the society in general. 1 BACKGROUND Dr Mwimali is a law lecturer, an advocate of the High Court of Kenya and a human-rights practitioner, with an interest in legal education, litigation, and human rights advocacy. He has taught numerous courses in law at Jomo Kenyatta University of Agriculture and Technology; the University of Nairobi School of Law; Kenyatta University School of Law; Birmingham Law School; Riara Law School; KCA University; and Nazarene University School of Law. He is also experienced in human rights advocacy having worked for a number of Non-Governmental Human Rights Organisations. He is currently an advocate practicing with the law firm of Goretti Munialo Mwimali & Co. Advocates. He also serves as a senior lecturer at the School of Law, Jomo Kenyatta University of Agriculture and Technology and a part-time lecturer at Riara University School of Law. He doubles up as an international Consulting Associate with Odokel Opolot Advocates, Uganda. WORK EXPERIENCE Sept 2013 to Date: Senior Lecturer, School of law, Jomo Kenyatta University of Agriculture and Technology Teaching: Constitutional Law; Human Rights Law; Family Law; Insurance Law; Land Law; Equity; and Law of Trusts. -

Factors Influencing Students' Performance in the Kenyan Bar Examination and Proposed Interventions
KENYA SCHOOL OF LAW Factors Influencing Students’ Performance in the Kenyan Bar Examination and Proposed Interventions Final Report September 2019 i Table of Contents Executive Summary ...................................................................................... v Abbreviations and Acronyms ......................................................................... xi 1 Background and Study Context ............................................................... 1 1.1 Introduction .................................................................................. 1 1.2 Interpretation of Terms of Reference ............................................. 4 1.3 Methodological Approach ............................................................... 4 2 Evolution of Legal Education in Kenya and Institutional Frameworks ......... 9 2.1 Development of Legal Education in Kenya ...................................... 9 2.2 Functions of Legal Education System in Kenya ............................... 11 2.3 Institutional Framework for Legal Education and Training in Kenya . 11 2.3.1 The Council of Legal Education ..................................................12 2.3.2 The Kenya School of Law ..........................................................15 2.3.3 Restructuring of the Kenya School of Law and Council of Legal Education .............................................................................................16 2.3.4 The Law Society of Kenya ..........................................................17 2.3.5 The Commission for University -

Where Is FIDA?
Page | 1 KENYAN WOMEN AT DUSK: Where is FIDA? Also Inside: Main Party behind Wanguru Sacking Agenda Raila’s Return and what it means to the Ruling Join the conversation facebook.com/kenyanlegal;Coalition twitter.com/The_Kenyan_Legal Tribalism a Cake Baked By the Government The main gender identities in a family/society setting need not necessarily be positively Page | 2hostile towards each other as none of them can subsist alone but the current sound of FIDA’s silence is rather surprising because gender-based violence against women is so clearly an increasing problem in the country Kenya now taking the form of normalcy-as being part of a Kenyan woman’s life, but, the farther we penetrate into the primitive history of thought, the farther we find ourselves from a conception of progress and development which all along it resembles. To ask for action from the government is rather rhetoric but from FIDA-Kenya, I cannot help asking for something more, for some central notion which shall account not only for the elimination of gender based violence but also for its permanence. It may be doubted whether this quest can be successful. As time progresses, so do we; or rather we strive to. I therefore welcome you to the Ninth issue of Kenyan Legal magazine; this is it-It’s Real Kenya, Real Issues. Be my guest. REGARDS, Michael Michael Opondo O. www.michaelopondo.wordpress.com Managing Editor, KENYAN LEGAL The Kenyan Legal Team The Branch Co-Ordinators The Secretariat Kenneth Kimathi: Kenyatta University Michael O. Opondo: Managing Editor. (School of Law) Sheila Mokaya: Assistant Editor. -

Illusionsof Location Theory
ILLUSIONS OF LOCATION THEORY Consequences for Blue Economy in Africa Edited by Francis Onditi Riara University, Kenya and Douglas Yates American Graduate School, Paris, France Series in Politics Copyright © 2021 by the authors. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior permission of Vernon Art and Science Inc. www.vernonpress.com In the Americas: In the rest of the world: Vernon Press Vernon Press 1000 N West Street, C/Sancti Espiritu 17, Suite 1200, Wilmington, Malaga, 29006 Delaware 19801 Spain United States Series in Politics Library of Congress Control Number: 2020943381 ISBN: 978-1-64889-021-5 Product and company names mentioned in this work are the trademarks of their respective owners. While every care has been taken in preparing this work, neither the authors nor Vernon Art and Science Inc. may be held responsible for any loss or damage caused or alleged to be caused directly or indirectly by the information contained in it. Every effort has been made to trace all copyright holders, but if any have been inadvertently overlooked the publisher will be pleased to include any necessary credits in any subsequent reprint or edition. Cover design by Vernon Press using elements designed by Freepik. Table of Contents List of Figures and Tables vii Foreword ix Narnia Bohler-Muller Human Sciences Research Council; University of Fort Hare; University of Free State -

Compiled From: Gradstate
Compiled from: GradState ..................................................... gradstate.com ....................................................... List of Public Universities in Kenya Public universities are government funded and Kenya has several as listed below: University of Nairobi (UoN) Founded in 1956, the University of Nairobi is the oldest and most prestigious University in Kenya. It has its main campus in the heart of Nairobi City, several campuses within the city and major towns across the country. It boasts of a great record of achievements over the years with several public figures, for instance, Deputy President, William Ruto, forming part of its alumni. Moi University The second university to be established in Kenya after Nairobi University, Moi University boasts of eight campuses and two constituent colleges. It was established in 1984 and is located in Eldoret. It has witnessed steady growth since its inception and still has more room for growth. It shares a name with Kenya’s second president, Daniel Moi. More Info: http://maisha.gradstate.com/complete-list-universities-in-kenya/ Kenyatta University (K.U) Commonly referred to as K.U, Kenyatta University, established in 1965, is the second largest university in Kenya. It is located along the Thika super highway with campuses within the Nairobi City and other towns in Kenya. Kenyatta University boasts of having the first female Vice Chancellor in Kenya, Dr. Olive Mugenda. It is good to note that Kenya’s 3rd president, Mwai Kibaki, went through Kenyatta University. Jomo Kenyatta University of Agriculture and Technology (JKUAT) With its main campus located in Juja town, along the Thika super highway, JKUAT as it is commonly known was started in 1981.