Merged Cover Sheets
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Here a Causal Relationship? Contemporary Economics, 9(1), 45–60
Bibliography on Corruption and Anticorruption Professor Matthew C. Stephenson Harvard Law School http://www.law.harvard.edu/faculty/mstephenson/ March 2021 Aaken, A., & Voigt, S. (2011). Do individual disclosure rules for parliamentarians improve government effectiveness? Economics of Governance, 12(4), 301–324. https://doi.org/10.1007/s10101-011-0100-8 Aaronson, S. A. (2011a). Does the WTO Help Member States Clean Up? Available at SSRN 1922190. http://papers.ssrn.com/sol3/papers.cfm?abstract_id=1922190 Aaronson, S. A. (2011b). Limited partnership: Business, government, civil society, and the public in the Extractive Industries Transparency Initiative (EITI). Public Administration and Development, 31(1), 50–63. https://doi.org/10.1002/pad.588 Aaronson, S. A., & Abouharb, M. R. (2014). Corruption, Conflicts of Interest and the WTO. In J.-B. Auby, E. Breen, & T. Perroud (Eds.), Corruption and conflicts of interest: A comparative law approach (pp. 183–197). Edward Elgar PubLtd. http://nrs.harvard.edu/urn-3:hul.ebookbatch.GEN_batch:ELGAR01620140507 Abbas Drebee, H., & Azam Abdul-Razak, N. (2020). The Impact of Corruption on Agriculture Sector in Iraq: Econometrics Approach. IOP Conference Series. Earth and Environmental Science, 553(1), 12019-. https://doi.org/10.1088/1755-1315/553/1/012019 Abbink, K., Dasgupta, U., Gangadharan, L., & Jain, T. (2014). Letting the briber go free: An experiment on mitigating harassment bribes. JOURNAL OF PUBLIC ECONOMICS, 111(Journal Article), 17–28. https://doi.org/10.1016/j.jpubeco.2013.12.012 Abbink, Klaus. (2004). Staff rotation as an anti-corruption policy: An experimental study. European Journal of Political Economy, 20(4), 887–906. https://doi.org/10.1016/j.ejpoleco.2003.10.008 Abbink, Klaus. -

Cadenza Document
Statewide Convictions by Offense (Summary) FORGERY/FRAUD 1/1/1999 to 12/31/2012 1999 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 OFOF 1 1 FELC 5 7 3 11 16 10 8 18 12 15 9 8 21 27 FELD 846 926 1,229 1,279 1,155 1,104 1,184 1,171 1,008 762 716 537 646 799 AGMS 383 404 534 559 574 603 699 643 655 699 606 680 643 642 SRMS 16 15 7 15 16 12 4 20 9 20 21 16 40 58 SMMS 41 36 46 58 42 58 36 39 53 37 47 60 70 68 UNKN 87 46 27 19 12 2 Totals 1,379 1,434 1,846 1,941 1,815 1,788 1,931 1,891 1,737 1,533 1,401 1,301 1,420 1,594 FORGERY/FRAUD 1/1/1999 to 12/31/2012 1999 Convicting Chg Convicting Description Class Convictions 234.13(1)(C) FOOD STAMP FRAUD-FALSE STATEMENTS (AGMS) AGMS 1 234.13(1)(D) FOOD STAMP FRAUD-FALSE STATEMENTS (SRMS) SRMS 1 234.13(3)(E) FOOD STAMP FRAUD-UNLAWFUL COUPON USE (SMMS) SMMS 1 714.10 FRAUDULENT PRACTICE 2ND DEGREE - 1978 (FELD) FELD 82 714.11 DNU - FRAUDULENT PRACTICE IN THE THIRD DEGREE - AGMS 66 714.11(1) FRAUDULENT PRACTICE THIRD DEGREE--$500-UNDER $1000 (AGMS) AGMS 16 714.11(3) FRAUDULENT PRACTICE 3RD DEGREE-AMOUNT UNDETERMINABLE (AGMS) AGMS 6 714.12 FRAUDULENT PRACTICE 4TH DEGREE - 1978 (SRMS) SRMS 11 714.13 FRAUDULENT PRACTICE 5TH DEGREE - 1978 (SMMS) SMMS 28 714.1(3)-B DNU - THEFT BY DECEPTION (FELD) FELD 3 714.1(3)-C DNU - THEFT BY DECEPTION (AGMS) AGMS 2 714.1(3)-D DNU-THEFT BY DECEPTION (SMMS) SMMS 12 714.1(3)-E DNU-THEFT BY DECEPTION (SRMS) SRMS 3 714.9 FRAUDULENT PRACTICE 1ST DEGREE - 1978 (FELC) FELC 4 715.6 FALSE USE OF FIN. -

Doesn't Fit Any Crime Arrests
Minneapolis City of Lakes - DRAFT - Doesn’t Fit Any Crime Arrests Police Conduct Oversight Commission December 2015 DRAFT TABLE OF CONTENTS INTRODUCTION .............................................................................................................................................................. 2 BACKGROUND ................................................................................................................................................................ 3 AUGUST 11, 2015 ACLU PRESENTATION TO THE COMMISSION ...................................................................................................... 3 POLICE REPORTING SYSTEM ...................................................................................................................................................... 3 “DOESN’T FIT ANY CRIME” ....................................................................................................................................................... 4 METHODOLOGY ............................................................................................................................................................. 5 STUDY GOALS: ........................................................................................................................................................................ 5 SAMPLE COLLECTION ............................................................................................................................................................... 5 RESEARCH QUESTIONS ............................................................................................................................................................. -

Website Profit
Website Profit Erfolg mit Partnerprogrammen: Mehrwert und Geldquelle für die eigene Website center.de - marketing - www.affiliate ADENION NetSeller Der ADENION NetSeller „Website Profit“ ist urheberrechtlich geschützt. © Copyright 2002, 2005 ADENION GmbH. Alle Rechte vorbehalten. Autoren: Melanie Tamblé, Andreas Winkler Herausgeber: ADENION GmbH, Grevenbroich, Germany Diese Publikation darf weder ganz oder in Teilen auf irgendeine Form vervielfältigt oder reproduziert werden. Dies gilt auch für das Speichern oder die Weiterleitung auf Datenträger oder andere Speichermedien. Abdruckgenehmigungen beim Herausgeber: ADENION GmbH Merkatorstrasse 2 41515 Grevenbroich Fon: 02181/7569-140 Fax: 02181/7569-199 E-Mail: [email protected] 1. Auflage, Februar 2002 2. überarbeitete und aktualisierte Auflage, Februar 2005 Die Informationen dieses Buches wurden sorgfältig recherchiert und aufbereitet. Es können keinerlei Garantien für die Richtigkeit der Informationen gegeben werden. Weder die Autoren noch der Her- ausgeber übernehmen irgendwelche Haftungen für Fehler, Auslassungen oder anderweitige Auslegun- gen der dargestellten Themen und Sachverhalte. Aussagen und Darstellungen über Zahlen, Kosten, Konditionen oder Leistungen von Drittanbietern basieren auf Informationen und Angaben zum Zeitpunkt der Erstellung dieses Leitfadens. Es kann keine Garantie für die Richtigkeit dieser Informationen gemacht werden. Sie unterliegen ausschließ- lich den Geschäftsbestimmungen und Rechten der jeweiligen Unternehmen. Alle in diesem Buch erwähnten Domainnamen, -

Mass-Marketing Fraud
Mass-Marketing Fraud A Report to the Attorney General of the United States and the Solicitor General of Canada May 2003 ��� Binational Working Group on Cross-Border Mass-Marketing Fraud Table of Contents Executive Summary ......................................................... ii Introduction ...............................................................viii Section I: Mass-Marketing Fraud Today ........................................1 Section II: The Response to Mass-Marketing Fraud, 1998-2003 .................... 26 Section III: Current Challenges in Cross-Border Fraud - Towards A Binational Action Plan .................................................................56 Appendix - Selected Cross-Border Mass-Marketing Fraud Enforcement Actions ..... 69 i Executive Summary Section I: Mass-Marketing Fraud Today Telemarketing Fraud ! Cross-border telemarketing fraud remains one of the most pervasive forms of white-collar crime in Canada and the United States. The PhoneBusters National Call Centre estimates that on any given day, there are 500 to 1,000 criminal telemarketing boiler rooms, grossing about $1 billion a year, operating in Canada. (3) ! Several types of cross-border telemarketing fraud have increased substantially from 1997 to 2002: fraudulent prize and lottery schemes; fraudulent loan offers; and fraudulent offers of low-interest credit cards or credit-card protection. (3) ! Seven trends in cross-border telemarketing fraud since 1997 are especially noteworthy: • (1) Types of Telemarketing Fraud “Pitches”. The most prevalent among Canadian-based telemarketing fraud operations are fraudulent offers of prizes or lotteries; fraudulent loan offers; and fraudulent offers of low- interest credit cards or credit-card protection. (5) • (2) Methods of Transmitting Funds. Criminal telemarketers generally prefer their victims to use electronic payment services, such as Western Union and Travelers Express MoneyGram, to send funds for the promised goods or services. -

Regulation of Dietary Supplements Hearing
S. HRG. 108–997 REGULATION OF DIETARY SUPPLEMENTS HEARING BEFORE THE COMMITTEE ON COMMERCE, SCIENCE, AND TRANSPORTATION UNITED STATES SENATE ONE HUNDRED EIGHTH CONGRESS FIRST SESSION OCTOBER 28, 2003 Printed for the use of the Committee on Commerce, Science, and Transportation ( U.S. GOVERNMENT PUBLISHING OFFICE 20–196 PDF WASHINGTON : 2016 For sale by the Superintendent of Documents, U.S. Government Publishing Office Internet: bookstore.gpo.gov Phone: toll free (866) 512–1800; DC area (202) 512–1800 Fax: (202) 512–2104 Mail: Stop IDCC, Washington, DC 20402–0001 VerDate Nov 24 2008 11:04 May 24, 2016 Jkt 075679 PO 00000 Frm 00001 Fmt 5011 Sfmt 5011 S:\GPO\DOCS\20196.TXT JACKIE SENATE COMMITTEE ON COMMERCE, SCIENCE, AND TRANSPORTATION ONE HUNDRED EIGHTH CONGRESS FIRST SESSION JOHN MCCAIN, Arizona, Chairman TED STEVENS, Alaska ERNEST F. HOLLINGS, South Carolina, CONRAD BURNS, Montana Ranking TRENT LOTT, Mississippi DANIEL K. INOUYE, Hawaii KAY BAILEY HUTCHISON, Texas JOHN D. ROCKEFELLER IV, West Virginia OLYMPIA J. SNOWE, Maine JOHN F. KERRY, Massachusetts SAM BROWNBACK, Kansas JOHN B. BREAUX, Louisiana GORDON SMITH, Oregon BYRON L. DORGAN, North Dakota PETER G. FITZGERALD, Illinois RON WYDEN, Oregon JOHN ENSIGN, Nevada BARBARA BOXER, California GEORGE ALLEN, Virginia BILL NELSON, Florida JOHN E. SUNUNU, New Hampshire MARIA CANTWELL, Washington FRANK R. LAUTENBERG, New Jersey JEANNE BUMPUS, Republican Staff Director and General Counsel ROBERT W. CHAMBERLIN, Republican Chief Counsel KEVIN D. KAYES, Democratic Staff Director and Chief Counsel GREGG ELIAS, Democratic General Counsel (II) VerDate Nov 24 2008 11:04 May 24, 2016 Jkt 075679 PO 00000 Frm 00002 Fmt 5904 Sfmt 5904 S:\GPO\DOCS\20196.TXT JACKIE C O N T E N T S Page Hearing held on October 28, 2003 ......................................................................... -
Section 3: Preventing Fraud
SECTION 3. Preventing Fraud There are over 50 different types of fraud – know how to protect yourself A guide for seniors 19 SECTION 3. Preventing Fraud Financial abuse of a senior is any act involving Why Seniors are Vulnerable to Fraud the misuse of the senior’s money or property Seniors are at increased risk of being targeted by without their full knowledge and consent. The con artists largely because: abuser could be a stranger, but it could be a family member, friend or neighbour. This section ¾ many seniors have substantial savings or of the guide focuses on the five most common assets categories of fraud experienced by seniors: ¾ scammers assume that seniors will be more ¿ door-to-door sales fraud, trusting ¿ investment fraud, ¾ seniors often feel they should be polite towards ¿ telemarketing fraud, strangers ¿ prize/contest fraud, and ¾ seniors are more likely to be home alone during ¿ identity fraud. the day Frauds (or scams) come in many forms. There are over 50 different types of fraud that have been classified and reported in Canada. Being familiar with the common scams will help you be prepared to detect and avoid being a victim of con artists. Phone Busters reports that Canadians lost $24,095,234 in a single calendar year on FACT mass marketing fraud. 20 A guide for seniors A. Know the Common Types of Fraud Door-to-Door Sales Fraud How to Avoid The person at your door seems ¾ Ask to see the persons license. Under the Direct genuine and will tell you they just Sellers Act, door-to-door salespersons are happened to be in the area. -

Reggie Huff, Et Al Vs. Firstenergy Corp., Et Al
Case: 5:12-cv-02583-SL Doc #: 31 Filed: 09/17/13 1 of 41. PageID #: <pageID> UNITED STATES DISTRICT COURT NORTHERN DISTRICT OF OHIO EASTERN DIVISION REGGIE HUFF, et al., ) CASE NO. 5:12CV2583 ) PLAINTIFFS, ) JUDGE SARA LIOI ) vs. ) ) MEMORANDUM OPINION ) ) FIRSTENERGY CORP., et al., ) ) DEFENDANTS. ) On October 16, 2012, plaintiffs, Reggie Huff and Lisa Huff, filed a pro se complaint in this Court alleging: violations of the federal Racketeer Influenced and Corrupt Organizations Act (“federal RICO”), 18 U.S.C. §§ 1962(b), (c), and (d); violations of Ohio’s “corrupt activity” law (“Ohio RICO”), Ohio Rev. Code § 2923.32;1 conspiracy under federal and Ohio law; and violations of their civil rights under 42 U.S.C. § 1983 (Doc. No. 1, Complaint). Plaintiffs originally named eleven defendants (not counting John Doe defendants), including corporate entities, private individuals, and current and former Ohio Supreme Court justices. The complaint further alleged a vast conspiracy to deprive plaintiffs of their right to a fair disposition of a personal injury action in state court. The allegations in the 43-page complaint are confusing, rambling, and, at times, inflammatory. Although much thought and attention appears to have gone into its 1 Ohio Rev. Code § 2923.34 provides individuals with a civil cause of action for violations of § 2923.32, which is otherwise a criminal statute. Case: 5:12-cv-02583-SL Doc #: 31 Filed: 09/17/13 2 of 41. PageID #: <pageID> preparation, the complaint is ultimately held together by a string of conclusory allegations.2 These allegations were immediately met with a motion to dismiss (Doc. -

Midwinter 2005 ISSN 1534-0937 Walt Crawford
Cites & Insights Crawford at Large Libraries • Policy • Technology • Media Sponsored by YBP Library Services Volume 5, Number 2: Midwinter 2005 ISSN 1534-0937 Walt Crawford $20-$25 of 256MB for $40-$50 may be more Trends & Quick Takes typical. With XP computers typically having front-mounted USB slots, the primary setup The Hazy Crystal Ball requirement is security. It’s that time of year—time for pundits and gurus to ¾ Wireless Access: “Providing wireless access tell us what’s to come and for a few of them to spin frees up your public access computing termi- last year’s projections. nals for those who truly need them, and I was going to include snarky comments (or cred- makes your library the neighborhood ‘hot- its, when applicable) about last year’s forecasts—but I spot’ for information access.” see that last year got so confusing that I never ran a ¾ Thin Clients::: “Thin-client technology en- set of forecasts. Neither did I make one: That should ables you to extend the life of your existing be no surprise. computers, lower costs on expanding the number of patron terminals, and simplify WebJunction’s Emerging technologies maintenance procedures.” for small libraries ¾ Upgrading Your Operating Systems: “Tech- You could think of this as a counterpart to the LITA Soup Stock offers upgrades to Windows XP Top Technology Trends group, but with fewer partici- for $8 (libraries are eligible)…” The text calls pants (eight in the October 4 posting) and a small- Windows 2000 and 95 “antiquated.” library bent. The committee develops a quarterly “list of five technologies they think are worth considering Inside This Issue for your library.” I like the guidelines: “The committee Bibs & Blather.................................................................... -

SENATE—Wednesday, March 21, 2012
March 21, 2012 CONGRESSIONAL RECORD—SENATE, Vol. 158, Pt. 3 3753 SENATE—Wednesday, March 21, 2012 The Senate met at 9:30 a.m. and was SCHEDULE The uninsured people show up at hos- called to order by the Honorable Mr. REID. Madam President, fol- pitals. They are not pushed away; they KIRSTEN E. GILLIBRAND, a Senator from lowing leader remarks the Senate will are invited in. They receive the treat- the State of New York. be in a period of morning business for ment. Then they can’t pay for it. 1 hour, with the majority controlling It turns out that 63 percent of the PRAYER the first half and the Republicans con- medical care given to uninsured people The Chaplain, Dr. Barry C. Black, of- trolling the final half. in America isn’t paid for—not by them. fered the following prayer: Following morning business the Sen- It turns out the rest of us pay for it. Let us pray. ate will resume consideration of the Everyone else in America who has O God, who loves us without ceasing, capital formation bill. At approxi- health insurance has to pick up the we turn our thoughts toward You. Re- mately 10:40 this morning, there will be cost for those who did not accept their main with our Senators today so that a cloture vote on the IPO bill. personal responsibility to buy health for no single instance they will be un- insurance. f aware of Your providential power. So, so what? What difference does We thank You for Your infinite love RESERVATION OF LEADER TIME that make? It makes a difference. -

Zerohack Zer0pwn Youranonnews Yevgeniy Anikin Yes Men
Zerohack Zer0Pwn YourAnonNews Yevgeniy Anikin Yes Men YamaTough Xtreme x-Leader xenu xen0nymous www.oem.com.mx www.nytimes.com/pages/world/asia/index.html www.informador.com.mx www.futuregov.asia www.cronica.com.mx www.asiapacificsecuritymagazine.com Worm Wolfy Withdrawal* WillyFoReal Wikileaks IRC 88.80.16.13/9999 IRC Channel WikiLeaks WiiSpellWhy whitekidney Wells Fargo weed WallRoad w0rmware Vulnerability Vladislav Khorokhorin Visa Inc. Virus Virgin Islands "Viewpointe Archive Services, LLC" Versability Verizon Venezuela Vegas Vatican City USB US Trust US Bankcorp Uruguay Uran0n unusedcrayon United Kingdom UnicormCr3w unfittoprint unelected.org UndisclosedAnon Ukraine UGNazi ua_musti_1905 U.S. Bankcorp TYLER Turkey trosec113 Trojan Horse Trojan Trivette TriCk Tribalzer0 Transnistria transaction Traitor traffic court Tradecraft Trade Secrets "Total System Services, Inc." Topiary Top Secret Tom Stracener TibitXimer Thumb Drive Thomson Reuters TheWikiBoat thepeoplescause the_infecti0n The Unknowns The UnderTaker The Syrian electronic army The Jokerhack Thailand ThaCosmo th3j35t3r testeux1 TEST Telecomix TehWongZ Teddy Bigglesworth TeaMp0isoN TeamHav0k Team Ghost Shell Team Digi7al tdl4 taxes TARP tango down Tampa Tammy Shapiro Taiwan Tabu T0x1c t0wN T.A.R.P. Syrian Electronic Army syndiv Symantec Corporation Switzerland Swingers Club SWIFT Sweden Swan SwaggSec Swagg Security "SunGard Data Systems, Inc." Stuxnet Stringer Streamroller Stole* Sterlok SteelAnne st0rm SQLi Spyware Spying Spydevilz Spy Camera Sposed Spook Spoofing Splendide -
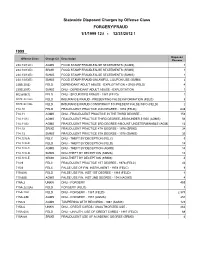
Cadenza Document
Statewide Disposed Charges by Offense Class FORGERY/FRAUD 1/1/1999 12:00:00- 12/31/2012 AM 12:00:00 AM 1999 Disposed Offense Class Charge Cd Description Charges 234.13(1)(C) AGMS FOOD STAMP FRAUD-FALSE STATEMENTS (AGMS) 1 234.13(1)(D) SRMS FOOD STAMP FRAUD-FALSE STATEMENTS (SRMS) 1 234.13(1)(E) SMMS FOOD STAMP FRAUD-FALSE STATEMENTS (SMMS) 1 234.13(3)(E) SMMS FOOD STAMP FRAUD-UNLAWFUL COUPON USE (SMMS) 2 235B.20(5) FELD DEPENDANT ADULT ABUSE - EXPLOITATION > $100 (FELD) 4 235B.20(7) SMMS DNU - DEPENDANT ADULT ABUSE - EXPLOITATION 1 502.605(1) FELD DNU - SECURITIES FRAUD - 1987 (FELD) 1 507E.3(2)(a) FELD INSURANCE FRAUD - PRESENTING FALSE INFORMATION (FELD) 5 507E.3(2)(b) FELD INSURANCE FRAUD CONSPIRACY TO PRESENT FALSE INFO (FELD) 2 714.10 FELD FRAUDULENT PRACTICE 2ND DEGREE - 1978 (FELD) 648 714.11 AGMS DNU - FRAUDULENT PRACTICE IN THE THIRD DEGREE - 153 714.11(1) AGMS FRAUDULENT PRACTICE THIRD DEGREE--$500-UNDER $1000 (AGMS) 56 714.11(3) AGMS FRAUDULENT PRACTICE 3RD DEGREE-AMOUNT UNDETERMINABLE (AGMS) 13 714.12 SRMS FRAUDULENT PRACTICE 4TH DEGREE - 1978 (SRMS) 34 714.13 SMMS FRAUDULENT PRACTICE 5TH DEGREE - 1978 (SMMS) 39 714.1(3)-A FELC DNU - THEFT BY DECEPTION (FELC) 5 714.1(3)-B FELD DNU - THEFT BY DECEPTION (FELD) 14 714.1(3)-C AGMS DNU - THEFT BY DECEPTION (AGMS) 14 714.1(3)-D SMMS DNU-THEFT BY DECEPTION (SMMS) 19 714.1(3)-E SRMS DNU-THEFT BY DECEPTION (SRMS) 4 714.9 FELC FRAUDULENT PRACTICE 1ST DEGREE - 1978 (FELC) 43 715.6 FELC FALSE USE OF FIN.