Cyber Frauds, Scams and Their Victims
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Flipping 419 Cybercrime Scams: Targeting the Weak and the Vulnerable
Flipping 419 Cybercrime Scams: Targeting the Weak and the Vulnerable Gibson Mba Jeremiah Onaolapo Royal Holloway University College London University of London Gianluca Stringhini Lorenzo Cavallaro University College London Royal Holloway University of London ABSTRACT ans living in Nigeria. While the long history and advanced Most of cyberscam-related studies focus on threats perpe- use of Information and Communication Technology (ICT) trated against the Western society, with a particular atten- in the Western societies justify the large body of literature tion to the USA and Europe. Regrettably, no research has dealing with its misuse, the absence of detailed studies on been done on scams targeting African countries, especially other regions, such as Africa, creates the impression that Nigeria, where the notorious and (in)famous 419 advanced- these societies are immune from cyber attacks. On the con- fee scam, targeted towards other countries, originated. How- trary, there is more happening out there that has not been ever, as we know, cybercrime is a global problem affecting brought to the attention of the concerned public. Our study all parties. In this study, we investigate a form of advance aims at bridging this gap, i.e., the paucity of African unique fee fraud scam unique to Nigeria and targeted at Nigerians, contribution to the global cybercrime, by studying in de- but unknown to the Western world. For the study, we rely tail a form of 419 (advance fee fraud) scam unknown to the substantially on almost two years worth of data harvested West but unique to Africa|Nigeria in particular|targeted from an online discussion forum used by criminals. -

Cadenza Document
Statewide Convictions by Offense (Summary) FORGERY/FRAUD 1/1/1999 to 12/31/2012 1999 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 OFOF 1 1 FELC 5 7 3 11 16 10 8 18 12 15 9 8 21 27 FELD 846 926 1,229 1,279 1,155 1,104 1,184 1,171 1,008 762 716 537 646 799 AGMS 383 404 534 559 574 603 699 643 655 699 606 680 643 642 SRMS 16 15 7 15 16 12 4 20 9 20 21 16 40 58 SMMS 41 36 46 58 42 58 36 39 53 37 47 60 70 68 UNKN 87 46 27 19 12 2 Totals 1,379 1,434 1,846 1,941 1,815 1,788 1,931 1,891 1,737 1,533 1,401 1,301 1,420 1,594 FORGERY/FRAUD 1/1/1999 to 12/31/2012 1999 Convicting Chg Convicting Description Class Convictions 234.13(1)(C) FOOD STAMP FRAUD-FALSE STATEMENTS (AGMS) AGMS 1 234.13(1)(D) FOOD STAMP FRAUD-FALSE STATEMENTS (SRMS) SRMS 1 234.13(3)(E) FOOD STAMP FRAUD-UNLAWFUL COUPON USE (SMMS) SMMS 1 714.10 FRAUDULENT PRACTICE 2ND DEGREE - 1978 (FELD) FELD 82 714.11 DNU - FRAUDULENT PRACTICE IN THE THIRD DEGREE - AGMS 66 714.11(1) FRAUDULENT PRACTICE THIRD DEGREE--$500-UNDER $1000 (AGMS) AGMS 16 714.11(3) FRAUDULENT PRACTICE 3RD DEGREE-AMOUNT UNDETERMINABLE (AGMS) AGMS 6 714.12 FRAUDULENT PRACTICE 4TH DEGREE - 1978 (SRMS) SRMS 11 714.13 FRAUDULENT PRACTICE 5TH DEGREE - 1978 (SMMS) SMMS 28 714.1(3)-B DNU - THEFT BY DECEPTION (FELD) FELD 3 714.1(3)-C DNU - THEFT BY DECEPTION (AGMS) AGMS 2 714.1(3)-D DNU-THEFT BY DECEPTION (SMMS) SMMS 12 714.1(3)-E DNU-THEFT BY DECEPTION (SRMS) SRMS 3 714.9 FRAUDULENT PRACTICE 1ST DEGREE - 1978 (FELC) FELC 4 715.6 FALSE USE OF FIN. -

Doesn't Fit Any Crime Arrests
Minneapolis City of Lakes - DRAFT - Doesn’t Fit Any Crime Arrests Police Conduct Oversight Commission December 2015 DRAFT TABLE OF CONTENTS INTRODUCTION .............................................................................................................................................................. 2 BACKGROUND ................................................................................................................................................................ 3 AUGUST 11, 2015 ACLU PRESENTATION TO THE COMMISSION ...................................................................................................... 3 POLICE REPORTING SYSTEM ...................................................................................................................................................... 3 “DOESN’T FIT ANY CRIME” ....................................................................................................................................................... 4 METHODOLOGY ............................................................................................................................................................. 5 STUDY GOALS: ........................................................................................................................................................................ 5 SAMPLE COLLECTION ............................................................................................................................................................... 5 RESEARCH QUESTIONS ............................................................................................................................................................. -

Mass-Marketing Fraud
Mass-Marketing Fraud A Report to the Attorney General of the United States and the Solicitor General of Canada May 2003 ��� Binational Working Group on Cross-Border Mass-Marketing Fraud Table of Contents Executive Summary ......................................................... ii Introduction ...............................................................viii Section I: Mass-Marketing Fraud Today ........................................1 Section II: The Response to Mass-Marketing Fraud, 1998-2003 .................... 26 Section III: Current Challenges in Cross-Border Fraud - Towards A Binational Action Plan .................................................................56 Appendix - Selected Cross-Border Mass-Marketing Fraud Enforcement Actions ..... 69 i Executive Summary Section I: Mass-Marketing Fraud Today Telemarketing Fraud ! Cross-border telemarketing fraud remains one of the most pervasive forms of white-collar crime in Canada and the United States. The PhoneBusters National Call Centre estimates that on any given day, there are 500 to 1,000 criminal telemarketing boiler rooms, grossing about $1 billion a year, operating in Canada. (3) ! Several types of cross-border telemarketing fraud have increased substantially from 1997 to 2002: fraudulent prize and lottery schemes; fraudulent loan offers; and fraudulent offers of low-interest credit cards or credit-card protection. (3) ! Seven trends in cross-border telemarketing fraud since 1997 are especially noteworthy: • (1) Types of Telemarketing Fraud “Pitches”. The most prevalent among Canadian-based telemarketing fraud operations are fraudulent offers of prizes or lotteries; fraudulent loan offers; and fraudulent offers of low- interest credit cards or credit-card protection. (5) • (2) Methods of Transmitting Funds. Criminal telemarketers generally prefer their victims to use electronic payment services, such as Western Union and Travelers Express MoneyGram, to send funds for the promised goods or services. -
Section 3: Preventing Fraud
SECTION 3. Preventing Fraud There are over 50 different types of fraud – know how to protect yourself A guide for seniors 19 SECTION 3. Preventing Fraud Financial abuse of a senior is any act involving Why Seniors are Vulnerable to Fraud the misuse of the senior’s money or property Seniors are at increased risk of being targeted by without their full knowledge and consent. The con artists largely because: abuser could be a stranger, but it could be a family member, friend or neighbour. This section ¾ many seniors have substantial savings or of the guide focuses on the five most common assets categories of fraud experienced by seniors: ¾ scammers assume that seniors will be more ¿ door-to-door sales fraud, trusting ¿ investment fraud, ¾ seniors often feel they should be polite towards ¿ telemarketing fraud, strangers ¿ prize/contest fraud, and ¾ seniors are more likely to be home alone during ¿ identity fraud. the day Frauds (or scams) come in many forms. There are over 50 different types of fraud that have been classified and reported in Canada. Being familiar with the common scams will help you be prepared to detect and avoid being a victim of con artists. Phone Busters reports that Canadians lost $24,095,234 in a single calendar year on FACT mass marketing fraud. 20 A guide for seniors A. Know the Common Types of Fraud Door-to-Door Sales Fraud How to Avoid The person at your door seems ¾ Ask to see the persons license. Under the Direct genuine and will tell you they just Sellers Act, door-to-door salespersons are happened to be in the area. -

Hacks, Leaks and Disruptions | Russian Cyber Strategies
CHAILLOT PAPER Nº 148 — October 2018 Hacks, leaks and disruptions Russian cyber strategies EDITED BY Nicu Popescu and Stanislav Secrieru WITH CONTRIBUTIONS FROM Siim Alatalu, Irina Borogan, Elena Chernenko, Sven Herpig, Oscar Jonsson, Xymena Kurowska, Jarno Limnell, Patryk Pawlak, Piret Pernik, Thomas Reinhold, Anatoly Reshetnikov, Andrei Soldatov and Jean-Baptiste Jeangène Vilmer Chaillot Papers HACKS, LEAKS AND DISRUPTIONS RUSSIAN CYBER STRATEGIES Edited by Nicu Popescu and Stanislav Secrieru CHAILLOT PAPERS October 2018 148 Disclaimer The views expressed in this Chaillot Paper are solely those of the authors and do not necessarily reflect the views of the Institute or of the European Union. European Union Institute for Security Studies Paris Director: Gustav Lindstrom © EU Institute for Security Studies, 2018. Reproduction is authorised, provided prior permission is sought from the Institute and the source is acknowledged, save where otherwise stated. Contents Executive summary 5 Introduction: Russia’s cyber prowess – where, how and what for? 9 Nicu Popescu and Stanislav Secrieru Russia’s cyber posture Russia’s approach to cyber: the best defence is a good offence 15 1 Andrei Soldatov and Irina Borogan Russia’s trolling complex at home and abroad 25 2 Xymena Kurowska and Anatoly Reshetnikov Spotting the bear: credible attribution and Russian 3 operations in cyberspace 33 Sven Herpig and Thomas Reinhold Russia’s cyber diplomacy 43 4 Elena Chernenko Case studies of Russian cyberattacks The early days of cyberattacks: 5 the cases of Estonia, -
2016 Wrap-Up Cybercrime Tactics and Techniques
Cybercrime tactics and techniques 2016 wrap-up TABLE OF CONTENTS 01 Executive summary 02 Windows malware 05 Early 2017 Windows malware predictions 06 Mac malware 06 Early 2017 OS X malware predictions 07 Exploit kits 08 Early 2017 exploit kit predictions 09 Phishing and malspam 10 Early 2017 phishing and malspam predictions 11 Potentially Unwanted Programs 11 Early 2017 PUP predictions 12 Tech support scams 13 Early 2017 tech support scam predictions 14 Conclusion Introduction Last year was interesting for malware distribution and development. While we still experienced a flood of ransomware and immense distribution of malware using malspam/phishing/exploit kits, some major players, such as TeslaCrypt and Angler EK, vanished, while some new names dominated. In our first wrap-up of the threat landscape, we are going to cover the trends observed during the last few months of 2016, take an analyst’s view of the threats, and offer some predictions for the beginning of 2017. Moving forward, every quarter we will bring you a view of the threat landscape through the eyes of Malwarebytes researchers and analysts. Executive summary Ransomware dominated in 2016 and continued to do so However, it’s market share and capabilities are not quite into 2017. We expect to see very little variation in this at par with Angler, though this is likely going to change in early 2017, and if anything, it is getting worse. The as we expect to observe an increase in exploit kit most notable ransomware families of the end of 2016 activity by the middle of 2017. While late 2016 showed were Locky and Cerber, two very similar ransomware a decrease in the amount of malicious spam/phishing families that took the number one slot multiple times attacks targeting users in the wild, we are seeing greater during the last part of the year. -

Financial Crime in the Twenty-First Century: the Rise of the Virtual Collar Criminal
Financial crime in the twenty-first century: the rise of the virtual collar criminal REID, Alan <http://orcid.org/0000-0003-2019-5629> Available from Sheffield Hallam University Research Archive (SHURA) at: http://shura.shu.ac.uk/22836/ This document is the author deposited version. You are advised to consult the publisher's version if you wish to cite from it. Published version REID, Alan (2018). Financial crime in the twenty-first century: the rise of the virtual collar criminal. In: RYDER, Nic, (ed.) White collar crime and risk: Financial crime, corruption and the financial crisis. Palgrave Studies in Risk, Crime and Society . London, Palgrave Macmillan, 231-251. Copyright and re-use policy See http://shura.shu.ac.uk/information.html Sheffield Hallam University Research Archive http://shura.shu.ac.uk Financial crime in the 21st Century: The rise of the Virtual Collar Criminal Alan S Reid, Senior Lecturer in Law, Sheffield Hallam University Abstract This chapter introduces the phenomenon of virtual collar crime, that is quintessentially white collar crimes that are perpetrated entirely in cyberspace. Trust, trust dependency, high skill base criminals and opportunity zones were, and are, the hallmarks of white collar crime. The emerging paradigm of virtual collar crimes negates the requirement that perpetrators be highly skilled. Computer sagacity is no longer the sine qua non for cybercriminals - the phenomenon of 'Crime as a Service' has outsourced the skill requirement to third party providers of the required technological knowhow. Alongside the cascading down of such technical knowledge, twenty-first century society has driven headlong down the information superhighway, with hardly any area of human activity left unexposed to the effects of the ether. -
Cadenza Document
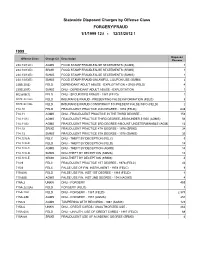
Statewide Disposed Charges by Offense Class FORGERY/FRAUD 1/1/1999 12:00:00- 12/31/2012 AM 12:00:00 AM 1999 Disposed Offense Class Charge Cd Description Charges 234.13(1)(C) AGMS FOOD STAMP FRAUD-FALSE STATEMENTS (AGMS) 1 234.13(1)(D) SRMS FOOD STAMP FRAUD-FALSE STATEMENTS (SRMS) 1 234.13(1)(E) SMMS FOOD STAMP FRAUD-FALSE STATEMENTS (SMMS) 1 234.13(3)(E) SMMS FOOD STAMP FRAUD-UNLAWFUL COUPON USE (SMMS) 2 235B.20(5) FELD DEPENDANT ADULT ABUSE - EXPLOITATION > $100 (FELD) 4 235B.20(7) SMMS DNU - DEPENDANT ADULT ABUSE - EXPLOITATION 1 502.605(1) FELD DNU - SECURITIES FRAUD - 1987 (FELD) 1 507E.3(2)(a) FELD INSURANCE FRAUD - PRESENTING FALSE INFORMATION (FELD) 5 507E.3(2)(b) FELD INSURANCE FRAUD CONSPIRACY TO PRESENT FALSE INFO (FELD) 2 714.10 FELD FRAUDULENT PRACTICE 2ND DEGREE - 1978 (FELD) 648 714.11 AGMS DNU - FRAUDULENT PRACTICE IN THE THIRD DEGREE - 153 714.11(1) AGMS FRAUDULENT PRACTICE THIRD DEGREE--$500-UNDER $1000 (AGMS) 56 714.11(3) AGMS FRAUDULENT PRACTICE 3RD DEGREE-AMOUNT UNDETERMINABLE (AGMS) 13 714.12 SRMS FRAUDULENT PRACTICE 4TH DEGREE - 1978 (SRMS) 34 714.13 SMMS FRAUDULENT PRACTICE 5TH DEGREE - 1978 (SMMS) 39 714.1(3)-A FELC DNU - THEFT BY DECEPTION (FELC) 5 714.1(3)-B FELD DNU - THEFT BY DECEPTION (FELD) 14 714.1(3)-C AGMS DNU - THEFT BY DECEPTION (AGMS) 14 714.1(3)-D SMMS DNU-THEFT BY DECEPTION (SMMS) 19 714.1(3)-E SRMS DNU-THEFT BY DECEPTION (SRMS) 4 714.9 FELC FRAUDULENT PRACTICE 1ST DEGREE - 1978 (FELC) 43 715.6 FELC FALSE USE OF FIN. -

Secureworks State of Cybercrime Report 2017
REPORT State2017 of Cybercrime Exposing the threats, techniques and markets that fuel the economy of cybercriminals Contents Foreword 3 Introduction 4 Key Findings 5 Cybercrime 1. Business Email Compromise 7 2. Ransomware 9 3. Banking Malware 12 4. Mobile Malware 20 Criminal Landscape 5. Organized Cybercrime 22 6. Diverse Roles 23 7. Gap Between Criminality and Nation-States 25 8. Money Muling 27 Online Crime — A Market Economy 9. Commodities 30 10. Spam Botnet Usage 34 11. Exploit Kit Activity Decline 37 Conclusion 39 Glossary of Terms 40 About Secureworks 41 2 © 2017 Secureworks, Inc. All rights reserved. Foreword Foreword Secureworks has been tracking cybercrime activity for more than 10 years and, as we monitor this activity to protect our clients, we collect a large amount of data on both the criminals and their infrastructure and systems. This annual report presents an overview of the cybercrime landscape and trends we observed primarily from the period of mid-2016 to May 2017, in addition to a handful of other trends ranging from 2015 to 2016. The unique and valuable intelligence shared in this report stems from the visibility gained from our thousands of clients, the machine learning and automation from our industry-leading Counter Threat Platform™, and the actionable insights from our team of elite Counter Threat Unit™ (CTU) researchers, analysts and consultants. We call this the Network Effect, and it is the unparalleled power and protection of this Network Effect which enables us to prevent security breaches, detect malicious activity in real time, respond rapidly and predict emerging threats. Secureworks’ goal in publicly sharing this report’s findings is to help all organizations better protect themselves from current and emerging cyber threats; to help make them become Collectively Smarter. -

Taking Action: an Advocate's Guide to Assisting Victims of Financial Fraud
Taking Action An Advocate’s Guide to Assisting Victims of Financial Fraud REVISED 2018 Helping Financial Fraud Victims June 2018 Financial fraud is real and can be devastating. Fortunately, in every community there are individuals in a position to provide tangible help to victims. To assist them, the Financial Industry Regulatory Authority (FINRA) Investor Education Foundation and the National Center for Victims of Crime joined forces in 2013 to develop Taking Action: An Advocate’s Guide to Assisting Victims of Financial Fraud. Prevention is an important part of combating financial fraud. We also know that financial fraud occurs in spite of preventive methods. When fraud occurs, victims are left to cope with the aftermath of compromised identities, damaged credit, and financial loss, and a painful range of emotions including anger, fear, and frustration. This guide gives victim advocates a roadmap for how to respond in the wake of a financial crime, from determining the type of fraud to reporting it to the proper authorities. The guide also includes case management tools for advocates, starting with setting reasonable expectations of recovery and managing the emotional fallout of financial fraud. Initially published in 2013, the guide was recently updated to include new tips and resources. Our hope is that this guide will empower victim advocates, law enforcement, regulators, and a wide range of community professionals to capably assist financial victims with rebuilding their lives. Sincerely, Gerri Walsh Mai Fernandez President Executive Director FINRA Investor Education Foundation National Center for Victims of Crime AN ADVOCATE’S GUIDE TO ASSISTING VICTIMS OF FINANCIAL FRAUD | i About Us The Financial Industry Regulatory Authority (FINRA) is a not-for-profit self-regulatory organization authorized by federal law to help protect investors and ensure the fair and honest operation of financial markets. -

Online Security and Safety Cybercrime and Internet Fraud
Online Security and Safety While the Internet makes many everyday tasks faster and more convenient, like shopping, banking, and communicating on the go, it's important to be safe, secure, and responsible online. Protect Your Privacy and Security You can protect your computer and personal data from theft, misuse, and destruction with some basic precautions. Scams - Learn how to recognize scams and what you can do to avoid them. Computer and online security - Defend yourself against scammers, hackers, and identity thieves by protecting your information and your computer while online. If you are a parent, you should also talk to your kids about being safe and responsible online. Visit OnGuardOnline.gov for more tips for parents and children on being safe and smart online. Cybercrime and Internet Fraud Scam artists in the U.S. and around the world defraud millions of people each year by using the Internet to trick victims into sending money or giving out personal information. Types of Internet Fraud Internet crime schemes target victims using various methods. Internet auction fraud - This scheme involves the misrepresentation of a product advertised for sale on an Internet auction site or non-delivery of merchandise. Credit card fraud - Through the unauthorized use of a credit/debit card, or card number, scammers fraudulently obtain money or property. Investment fraud - This is an offer using false claims to solicit investments or loans, or providing for the purchase, use, or trade of forged or counterfeit securities. Nigerian letter or "419" fraud - Named for the violation of Section 419 of the Nigerian Criminal Code, it combines the threat of impersonation fraud with a variation of an advance fee scheme in which a letter, e-mail, or fax is received by the victim.