Tactical and Technological Innovation in Terrorist Campaigns
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Burn It Down! Anarchism, Activism, and the Vancouver Five, 1967–1985
Burn it Down! Anarchism, Activism, and the Vancouver Five, 1967–1985 by Eryk Martin M.A., University of Victoria, 2008 B.A. (Hons.), University of Victoria, 2006 Dissertation Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy in the Department of History Faculty of Arts and Social Sciences © Eryk Martin 2016 SIMON FRASER UNIVERSITY Spring 2016 Approval Name: Eryk Martin Degree: Doctor of Philosophy (History) Title: Burn it Down! Anarchism, Activism, and the Vancouver Five, 1967–1985 Examining Committee: Chair: Dimitris Krallis Associate Professor Mark Leier Senior Supervisor Professor Karen Ferguson Supervisor Professor Roxanne Panchasi Supervisor Associate Professor Lara Campbell Internal Examiner Professor Gender, Sexuality, and Women’s Studies Joan Sangster External Examiner Professor Gender and Women’s Studies Trent University Date Defended/Approved: January 15, 2016 ii Ethics Statement iii Abstract This dissertation investigates the experiences of five Canadian anarchists commonly knoWn as the Vancouver Five, Who came together in the early 1980s to destroy a BC Hydro power station in Qualicum Beach, bomb a Toronto factory that Was building parts for American cruise missiles, and assist in the firebombing of pornography stores in Vancouver. It uses these events in order to analyze the development and transformation of anarchist activism between 1967 and 1985. Focusing closely on anarchist ideas, tactics, and political projects, it explores the resurgence of anarchism as a vibrant form of leftWing activism in the late tWentieth century. In addressing the ideological basis and contested cultural meanings of armed struggle, it uncovers Why and how the Vancouver Five transformed themselves into an underground, clandestine force. -
![[Japan] SALA GIOCHI ARCADE 1000 Miglia](https://docslib.b-cdn.net/cover/3367/japan-sala-giochi-arcade-1000-miglia-393367.webp)
[Japan] SALA GIOCHI ARCADE 1000 Miglia
SCHEDA NEW PLATINUM PI4 EDITION La seguente lista elenca la maggior parte dei titoli emulati dalla scheda NEW PLATINUM Pi4 (20.000). - I giochi per computer (Amiga, Commodore, Pc, etc) richiedono una tastiera per computer e talvolta un mouse USB da collegare alla console (in quanto tali sistemi funzionavano con mouse e tastiera). - I giochi che richiedono spinner (es. Arkanoid), volanti (giochi di corse), pistole (es. Duck Hunt) potrebbero non essere controllabili con joystick, ma richiedono periferiche ad hoc, al momento non configurabili. - I giochi che richiedono controller analogici (Playstation, Nintendo 64, etc etc) potrebbero non essere controllabili con plance a levetta singola, ma richiedono, appunto, un joypad con analogici (venduto separatamente). - Questo elenco è relativo alla scheda NEW PLATINUM EDITION basata su Raspberry Pi4. - Gli emulatori di sistemi 3D (Playstation, Nintendo64, Dreamcast) e PC (Amiga, Commodore) sono presenti SOLO nella NEW PLATINUM Pi4 e non sulle versioni Pi3 Plus e Gold. - Gli emulatori Atomiswave, Sega Naomi (Virtua Tennis, Virtua Striker, etc.) sono presenti SOLO nelle schede Pi4. - La versione PLUS Pi3B+ emula solo 550 titoli ARCADE, generati casualmente al momento dell'acquisto e non modificabile. Ultimo aggiornamento 2 Settembre 2020 NOME GIOCO EMULATORE 005 SALA GIOCHI ARCADE 1 On 1 Government [Japan] SALA GIOCHI ARCADE 1000 Miglia: Great 1000 Miles Rally SALA GIOCHI ARCADE 10-Yard Fight SALA GIOCHI ARCADE 18 Holes Pro Golf SALA GIOCHI ARCADE 1941: Counter Attack SALA GIOCHI ARCADE 1942 SALA GIOCHI ARCADE 1943 Kai: Midway Kaisen SALA GIOCHI ARCADE 1943: The Battle of Midway [Europe] SALA GIOCHI ARCADE 1944 : The Loop Master [USA] SALA GIOCHI ARCADE 1945k III SALA GIOCHI ARCADE 19XX : The War Against Destiny [USA] SALA GIOCHI ARCADE 2 On 2 Open Ice Challenge SALA GIOCHI ARCADE 4-D Warriors SALA GIOCHI ARCADE 64th. -

2017 National History Bowl National Championships Playoff Round 7
2017 National History Bowl National Championships Playoff Round 7 Round: Playoffs 7 Supergroup Group Room: Reader: Scorekeep: Team Names, including letter designation if needed, go in the large boxes to the right. TU# Bonus Bonus Points Cumulative Score Bonus Points Cumulative Score 1 Quarter 1 2 Tossups Only 3 4 Put a "10" in the 5 column of the team 6 that answers correctly. 7 Otherwise leave box 8 blank. 9 10 1 Quarter 2 2 Tossups and bonuses 3 Put "10" in the team's 4 column. Otherwise, 5 leave box blank. 6 For bonuses, put "0" or 7 Substitutions allowed between Qtrs all "10" in the bonus 8 column. 9 10 Quarter 3 points points 60 sec. rds - trailing team Lightning Lightning goes first. 10 pts each. Bounceback Bounceback 20 pt bonus for sweep! Total Total 1 Quarter 4 2 Tossups worth 30, 20, or 3 10 points each 4 Put the appropriate 5 number in the column of 6 the team that answers 7 correctly. Otherwise leave 8 box blank. 9 10 Tiebreakers 1 Tiebreak questions Tie Breaker (Sudden are only used 2 have no point value Victory) to determine winner! 3 at all! Final Score NHBB Nationals Bowl 2016-2017 Bowl Playoff Packet 7 Bowl Playoff Packet 7 First Quarter (1) Description acceptable. This event was thought to have occurred in retaliation for the bombing of the perpetrator's Tunisian headquarters in Operation Wooden Leg. Muhammad Zaidan organized this event, which involved the redirection of a vessel to Tartus, Syria. A John Adams opera focusing on this event opens with two choruses of exiles and is named after its only casualty, the 69-year old Leon Klinghoffer. -

Unholy Alliance. the Connection Between the East German Stasi and the Right-Wing Terrorist Odfried Hepp
Unholy Alliance. The Connection between the East German Stasi and the Right-Wing Terrorist Odfried Hepp Bernhard Blumenau Introduction On 18 February 1983, a young man, aged 23, suspected that the police were keeping his apartment under surveillance and took his rucksack, climbed onto an adjacent balcony to hide there until the police were gone. In the depth of night, he left the building and ran ceaselessly through the streets of West Berlin. Finally, to confuse his pursuers, he took several taxis, as well as the U-Bahn, to the Friedrichstraße checkpoint between West Berlin and the German Democratic Republic (GDR), where he arrived just before 6 am. Announcing himself to the East German border guards, he waited in a backroom until he was finally picked up by an officer of the East German State Security, the Stasi.1 This man, Odfried Hepp (aka ‘Friedrich’ in the Stasi files), was one of the most wanted right-wing terrorists2 in the Federal Republic of Germany (FRG) in the 1980s. What sounds like an extract from a spy novel is only one of the highlights of a story that has all the basic ingredients of a thriller: murders and bank robberies, a young man driven by – however abhorrent – political and idealistic beliefs, Cold War politics, Palestinian ‘freedom fighters’, boot camps in the Middle East, spies, and fake identities. Yet this story, which is at the centre of this article, is not fiction – it is the very real account of the life of Odfried Hepp as well as a glimpse at radicalisation and political extremism as well as right-wing terrorism in West Germany, the dimensions of the German- German Cold War struggle and the GDR’s relationship with terrorism. -

The Anglo/American - Nazi War
The Anglo/American - Nazi War By CalBear Preface (Page 1) Before examining the actual final conflict between the Western democracies, chiefly Canada, Great Britain, and the United States and Nazi Germany, it is worth reviewing the circumstances that brought the world to that critical juncture. In 1939 Nazi Germany, then also called the “Third Reich” or simply the Reich, had initiated the European Phase of the Second World War with the invasion of Poland. At the time of the invasion Germany was in a state of near alliance with the Soviet Union with Soviet oil and agriculture providing much of Reich’s fuel and food. Poland was supported by both France and Great Britain and the two Western states had made clear that an attack on Poland would lead to war. It has long been debated why the Democracies waited until the Polish crisis to confront the still developing German war machine, but the decisions made in both London and Paris in late summer of 1939 were resolute and both nations believed that their combined power would be sufficient to deter Adolph Hitler’s Germany from aggression against Poland. On September 1, 1939 Hitler demonstrated his contempt for, and disbelief in, the Democracies statements and warnings when the German military (or, as it was known at the time, the Wehrmacht) crossed the international frontier separating Germany and Poland, and unleashed an early version of mechanized warfare against the Polish Army. Shortly after the Reich’s invasion of Poland, its quasi-ally the Soviet Union entered Poland and annexed a significant portion of the country’s eastern provinces. -
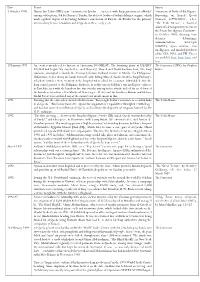
Date Event Source 1 October 1990 Usama Bin Ladin (UBL) Sent
Date Event Source 1 October 1990 Usama bin Ladin (UBL) sent “emissaries to Jordan … to meet with Iraqi government officials” ‘Summary of Body of Intelligence among a delegation, led by Hassan al-Turabi, the de facto leader of Sudan’s Islamist regime, which Reporting on Iraq-al Qaeda made a public display of defending Saddam’s annexation of Kuwait. Al-Turabi was the primary Contacts (1990-2003)’, a.k.a. intermediary between Saddam and al-Qaeda in these early years. “The Feith Memo”, a classified annex of a Pentagon report sent to the Senate Intelligence Committee in October 2003, drawing from detainee debriefings, communications intercepts (SIGINT), open sources, raw intelligence, and finished products of the CIA, NSA, and FBI. Pieces are available here, here, here, and here. 19 January 1991 An event remembered to history as Operation DOGMEAT: The bombing phase of DESERT The Connection (2004), by Stephen STORM had begun two days before, and Ahmed J. Ahmed and Abdul Kadham Saad, two Iraqi Hayes students, attempted to bomb the Thomas Jefferson Cultural Center in Manila, the Philippines. Unfortunately (for them) the bomb went off early, killing Ahmed. Saad recited the Iraqi Embassy’s telephone number from memory at the hospital when asked for a contact. Muwafak al-Ani, the Iraqi consul general at the Philippine Embassy, in reality one of Saddam’s top intelligence officers in East Asia, met with the bombers five times in the run-up to the attack; indeed his car delivered the bombers to within a few blocks of their target. Al-Ani and the brothers Husam and Hisham Abdul Sattar were ordered out of the country for involvement in this. -

A Day in the Salient with Bernard Comyn by Ian Chambers, August 2007
A Day in the Salient with Bernard Comyn by Ian Chambers, August 2007 Bernard is a friend of Harry Canvin, and knowing that I was spending a few days in the Salient, Harry arranged for Gary and me to spend a day with him. Bernard, (pictured here with my son Gary) is, I would guess, in his early seventies and was born in Zillebeke, where he still lives. He is a walking encyclopaedia on the war in the Salient and once you have spent a little time with him it soon becomes clear that he gets great enjoyment from passing that knowledge on. Our first stop was Hill 60, which is on the outskirts of Zillebeke. This mound, 60 metres high, was of great importance bearing in mind the general low lying nature of most of the area. It was held by the Germans until 7 June 1917 when a series of mines was detonated over the Messines Ridge area to signal the start of what became known as the Battle of Messines. The tunnel to Hill 60 was 1,380 feet long and was officially known as The Berlin Sap, just before it reached Hill 60 the tunnel branched off to run under another German position known as The Caterpillar which was a second "hill" formed from the spoil from the railway cutting. In total 123,500 pounds of ammonal and guncotton was placed under the two hills and when both mines exploded as planned, this allowed British troops to storm and capture them and they remained in British hands until the German advance of 1918. -

Book XVIII Prizes and Organizations Editor: Ramon F
8 88 8 88 Organizations 8888on.com 8888 Basic Photography in 180 Days Book XVIII Prizes and Organizations Editor: Ramon F. aeroramon.com Contents 1 Day 1 1 1.1 Group f/64 ............................................... 1 1.1.1 Background .......................................... 2 1.1.2 Formation and participants .................................. 2 1.1.3 Name and purpose ...................................... 4 1.1.4 Manifesto ........................................... 4 1.1.5 Aesthetics ........................................... 5 1.1.6 History ............................................ 5 1.1.7 Notes ............................................. 5 1.1.8 Sources ............................................ 6 1.2 Magnum Photos ............................................ 6 1.2.1 Founding of agency ...................................... 6 1.2.2 Elections of new members .................................. 6 1.2.3 Photographic collection .................................... 8 1.2.4 Graduate Photographers Award ................................ 8 1.2.5 Member list .......................................... 8 1.2.6 Books ............................................. 8 1.2.7 See also ............................................ 9 1.2.8 References .......................................... 9 1.2.9 External links ......................................... 12 1.3 International Center of Photography ................................. 12 1.3.1 History ............................................ 12 1.3.2 School at ICP ........................................ -

Digest of Terrorist Cases
back to navigation page Vienna International Centre, PO Box 500, 1400 Vienna, Austria Tel.: (+43-1) 26060-0, Fax: (+43-1) 26060-5866, www.unodc.org Digest of Terrorist Cases United Nations publication Printed in Austria *0986635*V.09-86635—March 2010—500 UNITED NATIONS OFFICE ON DRUGS AND CRIME Vienna Digest of Terrorist Cases UNITED NATIONS New York, 2010 This publication is dedicated to victims of terrorist acts worldwide © United Nations Office on Drugs and Crime, January 2010. The designations employed and the presentation of material in this publication do not imply the expression of any opinion whatsoever on the part of the Secretariat of the United Nations concerning the legal status of any country, territory, city or area, or of its authorities, or concerning the delimitation of its frontiers or boundaries. This publication has not been formally edited. Publishing production: UNOV/DM/CMS/EPLS/Electronic Publishing Unit. “Terrorists may exploit vulnerabilities and grievances to breed extremism at the local level, but they can quickly connect with others at the international level. Similarly, the struggle against terrorism requires us to share experiences and best practices at the global level.” “The UN system has a vital contribution to make in all the relevant areas— from promoting the rule of law and effective criminal justice systems to ensuring countries have the means to counter the financing of terrorism; from strengthening capacity to prevent nuclear, biological, chemical, or radiological materials from falling into the -

Narcotics Funded Terrorists/Extremist Groups
A GLOBAL OVERVIEW OF NARCOTICS-FUNDED TERRORIST AND OTHER EXTREMIST GROUPS A Report Prepared by the Federal Research Division, Library of Congress under an Interagency Agreement with the Department of Defense May 2002 Researchers: LaVerle Berry Glenn E. Curtis Rex A. Hudson Nina A. Kollars Project Manager: Rex A. Hudson Federal Research Division Library of Congress Washington, D.C. 20540−4840 Tel: 202−707−3900 Fax: 202−707−3920 E-Mail: [email protected] Homepage: http://www.loc.go v/rr/frd/ Library of Congress – Federal Research Division Narcotics-Funded Terrorist/Extremist Groups PREFACE This global survey, based entirely on open sources, is intended to provide an assessment of the nexus between selected anti-U.S. terrorist and extremist groups in the world and organized crime, specifically drug trafficking, and how this relationship might be vulnerable to countermeasures. More specifically, the aim is to help develop a causal model for identifying critical nodes in terrorist and other extremist networks that can be exploited by Allied technology, just as counterdrug technology has been used in the war against drug trafficking. To this end, the four analysts involved in this study have examined connections between extremist groups and narcotics trafficking in the following countries, listed by region in order of discussion in the text: Latin America: Triborder Region (Argentina, Brazil, and Paraguay), Colombia, and Peru; the Middle East: Lebanon; Southern Europe (Albania and Macedonia); Central Asia: Kyrgyzstan, Tajikistan, and Uzbekistan; and East Asia: Philippines. These are preliminary, not definitive, surveys. Most of the groups examined in this study have been designated foreign terrorist organizations by the U.S. -

Hijacking of Air France Airbus by Followers of Popular Front for The
Keesing's Record of World Events (formerly Keesing's Contemporary Archives), Volume 22, August, 1976 France, Israeli, Ugandan, Britain, Kenya, Uganda, Page 27888 © 1931-2006 Keesing's Worldwide, LLC - All Rights Reserved. Hijacking of Air France Airbus by Followers of Popular Front for the Liberation of Palestine - Israeli Action to liberate Hostages held at Entebbe Airport - Inconclusive Debate at UN security Council - Ugandan Recriminations against Britain and Kenya - Severance of Diplomatic Relations with Uganda by Britain An Air France A300-B airbus, under way from Tel Aviv to Paris and carrying a crew of 12 and 247 passengers, was hijacked shortly after it had taken off from Athens at 11.55 a.m. on June 27, 1976, by an armed group of three men and a woman calling itself the Che Guevara cell of the Haifa section of the Popular Front for the Liberation of Palestine (PFLP). A spokesman for the PFLP in Damascus telephoned the Reuter office in Kuwait on the same day to announce his organization's responsibility for the hijacking, but a Beirut spokesman for the PFLP denied on June 28 that it had anything to do with the action. The PFLP led by Dr George Habash, is part of the "rejection front" whwich opposes any "partal" settlement which would guuarantee the existence of a Jewish state on the territory of Plestine—see 26961.] The leader of the hijackers was Herr Wilfried Bose (27), a West German lawyer who had been part of the PFLP network, for whose terrorist activities in Europe Sr Ilich Ramirez Sánchez (alias Carlos Martínez or "The Jackal") had been responsible [see 27587]. -

Commerce in Explosives; 2020 Annual Those on the Annual List
Federal Register / Vol. 85, No. 247 / Wednesday, December 23, 2020 / Notices 83999 inspection at the Office of the Secretary or synonyms in brackets. This list Black powder substitutes. and on EDIS.3 supersedes the List of Explosive *Blasting agents, nitro-carbo-nitrates, This action is taken under the Materials published in the Federal including non-cap sensitive slurry and authority of section 337 of the Tariff Act Register on January 2, 2020 (Docket No. water gel explosives. of 1930, as amended (19 U.S.C. 1337), 2019R–04, 85 FR 128). Blasting caps. and of §§ 201.10 and 210.8(c) of the The 2020 List of Explosive Materials Blasting gelatin. Commission’s Rules of Practice and is a comprehensive list, but is not all- Blasting powder. Procedure (19 CFR 201.10, 210.8(c)). inclusive. The definition of ‘‘explosive BTNEC [bis (trinitroethyl) carbonate]. materials’’ includes ‘‘[e]xplosives, BTNEN [bis (trinitroethyl) nitramine]. By order of the Commission. BTTN [1,2,4 butanetriol trinitrate]. Issued: December 18, 2020. blasting agents, water gels and detonators. Explosive materials, Bulk salutes. William Bishop, include, but are not limited to, all items Butyl tetryl. Supervisory Hearings and Information in the ‘List of Explosive Materials’ Officer. C provided for in § 555.23.’’ 27 CFR Calcium nitrate explosive mixture. [FR Doc. 2020–28458 Filed 12–22–20; 8:45 am] 555.11. Accordingly, the fact that an BILLING CODE 7020–02–P Cellulose hexanitrate explosive explosive material is not on the annual mixture. list does not mean that it is not within Chlorate explosive mixtures. coverage of the law if it otherwise meets DEPARTMENT OF JUSTICE Composition A and variations.