2017 National History Bowl National Championships Playoff Round 7
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MARITIME TERRORISM THREAT in SOUTHEAST ASIA and ITS CHALLENGES by ME6 Joses Yau Meng Wee
features 32 MARITIME TERRORISM THREAT IN SOUTHEAST ASIA AND ITS CHALLENGES by ME6 Joses Yau Meng Wee Abstract: The threat of terrorism is always present, but the public was only given a wake-up call to the devastating impacts of terrorism after the September 11 attacks in the United States (US). Since then, many countries have stepped up their counter-terrorism efforts and measures. For example, the Association of Southeast Asian Nations (ASEAN) adopted a comprehensive approach to improve the regional security. In this essay, the author examines the terrorism threat in Southeast Asia, exploring the possible scenarios of a maritime terrorist attack in the region and thoroughly assesses the region’s counter-terrorism efforts that have been put in place. The author also introduces an Opportunity, Capability and Intent (OCI) framework as a form of threat assessment, to affirm his stand that the terrorist threat in Southeast Asia is indeed very real. Keywords: Terrorism; Counter-terrorism; Efforts and Measures; Regional Security; Threat Assessment INTRODUCTION This essay seeks to ascertain a common definition of ‘Maritime Terrorism’ and followed on to affirm The September 11 attacks in the US underscored that the terrorism threat in Southeast Asia is real the devastating effects of terrorism to the world. through the use of the Opportunity, Capability and The attacks on USS Cole in 2000, MV Limburg in Intent (OCI) threat assessment framework. Next, 2002, SuperFerry 14 in 2004 and the M Star in 2010 the essay will discuss eight probable scenarios of a are classified as acts of ‘Maritime Terrorism’, a stark maritime terrorist attack in Southeast Asia and attempt reminder that the world’s waterways continue to be to examine the credibility of each scenario. -

Strategic Insights No 10 DRAFT
Towards a European maritime security policy Wengelin, Mattias Published in: Strategic Insights 2008 Link to publication Citation for published version (APA): Wengelin, M. (2008). Towards a European maritime security policy. Strategic Insights, 6-13. Total number of authors: 1 General rights Unless other specific re-use rights are stated the following general rights apply: Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. • Users may download and print one copy of any publication from the public portal for the purpose of private study or research. • You may not further distribute the material or use it for any profit-making activity or commercial gain • You may freely distribute the URL identifying the publication in the public portal Read more about Creative commons licenses: https://creativecommons.org/licenses/ Take down policy If you believe that this document breaches copyright please contact us providing details, and we will remove access to the work immediately and investigate your claim. LUND UNIVERSITY PO Box 117 221 00 Lund +46 46-222 00 00 Risk Intelligence Strategic Insights Global Maritime Security Analysis No 10 - 2008 USCGC Bertholf during sea trials 8 February 2008 (USCG) Content § US Maritime Security Policy Revisited § Towards a European Maritime Security Policy? § The Maritime Operations of the Liberation Tigers of Tamil Eelam (LTTE): The Sea Tigers and Sea Pigeons § Marine Insurance for Piracy or Terrorism – Drawing a line in Water Strategic Insights No. -

Maritime Terrorism in the Indian Ocean Rim
Maritime Terrorism in the Indian Ocean Rim: Peering into the Darkness Keegan B. Steele California State University Maritime Academy April, 2017 Via CIMSEC™ MARITIME TERRORISM IN THE INDIAN OCEAN RIM Steele 1 Abstract The Indian Ocean Rim (IOR) has become a major geopolitical and security interest in the 21st century. One of the biggest issues that faces the Indian Ocean today is the swift growth of maritime related security threats. This is a major concern to not only first world nations like the United States, but also to developing states in the region. Due to the lack of stability in the region, the Horn of Africa and the Arabian Peninsula have been a breeding ground for violent non-state actors. Piracy, illicit trade, and terrorism are just a few of the non traditional maritime security threats. With instability in an already pirate-infested area, the threat of a growing maritime terrorism domain is a looming and haunting notion. This thesis will look into the history of maritime based terrorist attacks, and the potential for up and coming non-state actors, terrorist organizations, and organized crime in a region of instability. MARITIME TERRORISM IN THE INDIAN OCEAN RIM Steele 2 Introduction Maritime terrorism is a real and current threat to the world’s maritime industry. Acts of terrorism have been committed in the past, that have not only been devastating to infrastructure, but also have caused loss of life. According to (Nincic, 2012), maritime terrorism represents a very small percentage of all terrorist attacks. “A similar analysis of the RAND terrorism database supports these figures; of the 40,126 terrorist incidents recorded between 1968 and 2007, only 136 (0.34%) were against the maritime domain” (Nincic, 2012, para. -

Wh Owat Ches the Wat Chmen
WHO WATCHES THE WATCHMEN WATCHES WHO WHO WATCHES THE WATCHMEN WATCHES WHO I see powerful echoes of what I personally experienced as Director of NSA and CIA. I only wish I had access to this fully developed intellectual framework and the courses of action it suggests while still in government. —General Michael V. Hayden (retired) Former Director of the CIA Director of the NSA e problem of secrecy is double edged and places key institutions and values of our democracy into collision. On the one hand, our country operates under a broad consensus that secrecy is antithetical to democratic rule and can encourage a variety of political deformations. But the obvious pitfalls are not the end of the story. A long list of abuses notwithstanding, secrecy, like openness, remains an essential prerequisite of self-governance. Ross’s study is a welcome and timely addition to the small body of literature examining this important subject. —Gabriel Schoenfeld Senior Fellow, Hudson Institute Author of Necessary Secrets: National Security, the Media, and the Rule of Law (W.W. Norton, May 2010). ? ? The topic of unauthorized disclosures continues to receive significant attention at the highest levels of government. In his book, Mr. Ross does an excellent job identifying the categories of harm to the intelligence community associated NI PRESS ROSS GARY with these disclosures. A detailed framework for addressing the issue is also proposed. This book is a must read for those concerned about the implications of unauthorized disclosures to U.S. national security. —William A. Parquette Foreign Denial and Deception Committee National Intelligence Council Gary Ross has pulled together in this splendid book all the raw material needed to spark a fresh discussion between the government and the media on how to function under our unique system of government in this ever-evolving information-rich environment. -

Unholy Alliance. the Connection Between the East German Stasi and the Right-Wing Terrorist Odfried Hepp
Unholy Alliance. The Connection between the East German Stasi and the Right-Wing Terrorist Odfried Hepp Bernhard Blumenau Introduction On 18 February 1983, a young man, aged 23, suspected that the police were keeping his apartment under surveillance and took his rucksack, climbed onto an adjacent balcony to hide there until the police were gone. In the depth of night, he left the building and ran ceaselessly through the streets of West Berlin. Finally, to confuse his pursuers, he took several taxis, as well as the U-Bahn, to the Friedrichstraße checkpoint between West Berlin and the German Democratic Republic (GDR), where he arrived just before 6 am. Announcing himself to the East German border guards, he waited in a backroom until he was finally picked up by an officer of the East German State Security, the Stasi.1 This man, Odfried Hepp (aka ‘Friedrich’ in the Stasi files), was one of the most wanted right-wing terrorists2 in the Federal Republic of Germany (FRG) in the 1980s. What sounds like an extract from a spy novel is only one of the highlights of a story that has all the basic ingredients of a thriller: murders and bank robberies, a young man driven by – however abhorrent – political and idealistic beliefs, Cold War politics, Palestinian ‘freedom fighters’, boot camps in the Middle East, spies, and fake identities. Yet this story, which is at the centre of this article, is not fiction – it is the very real account of the life of Odfried Hepp as well as a glimpse at radicalisation and political extremism as well as right-wing terrorism in West Germany, the dimensions of the German- German Cold War struggle and the GDR’s relationship with terrorism. -

Cruising with Terrorists: Qualitative Study of Consumer Perspectives
International Journal of Safety and Security in Tourism/Hospitality Cruising with terrorists: Qualitative study of consumer perspectives Cyril Peter Facultad de Ciencias Económicas The purpose of this exploratory study on cruise ship security was to understand cruise ship passenger’s security perception; what level of security they expect as consumers and what minimum level of security they would be willing to accept. There were a total ten participants in this qualitative study using an interpretivist approach. Tourism is a major revenue generator for New Zealand and protecting this industry is of paramount importance. Once the industry understands their consumers’ security expectations, they can perhaps ‘manage’ any unexpected events accordingly and ensure minimal disruption to business. Terrorists are constantly searching for easier, more accessible, low-investment/high-return targets. They want new, fresh, high-yield targets. Terrorism is not necessarily about killing a huge number of people all at once; it is about creating fear and uncertainty amongst the audience and witnesses, and disrupting everyday life and commerce. Terrorism is about causing chaos, fear and uncertainty. Understanding the expectations of terrorists and also understanding the security needs of the cruise consumers will help the industry to provide the right balance of security without impinging on consumer’s enjoyment and hospitality experience. Hospitality security, unlike security in many other industries, is delicate, in that while it is imperative, it should be invisible. Hospitality needs to appear inviting and welcoming, while at the same time implicitly promising safety and security. Findings: 1) Participants have a laissez-faire attitudes towards security. 2) Passengers believed that security screenings at seaports were less stringent than at airports. -

Who Watches the Watchmen? the Conflict Between National Security and Freedom of the Press
WHO WATCHES THE WATCHMEN WATCHES WHO WHO WATCHES THE WATCHMEN WATCHES WHO I see powerful echoes of what I personally experienced as Director of NSA and CIA. I only wish I had access to this fully developed intellectual framework and the courses of action it suggests while still in government. —General Michael V. Hayden (retired) Former Director of the CIA Director of the NSA e problem of secrecy is double edged and places key institutions and values of our democracy into collision. On the one hand, our country operates under a broad consensus that secrecy is antithetical to democratic rule and can encourage a variety of political deformations. But the obvious pitfalls are not the end of the story. A long list of abuses notwithstanding, secrecy, like openness, remains an essential prerequisite of self-governance. Ross’s study is a welcome and timely addition to the small body of literature examining this important subject. —Gabriel Schoenfeld Senior Fellow, Hudson Institute Author of Necessary Secrets: National Security, the Media, and the Rule of Law (W.W. Norton, May 2010). ? ? The topic of unauthorized disclosures continues to receive significant attention at the highest levels of government. In his book, Mr. Ross does an excellent job identifying the categories of harm to the intelligence community associated NI PRESS ROSS GARY with these disclosures. A detailed framework for addressing the issue is also proposed. This book is a must read for those concerned about the implications of unauthorized disclosures to U.S. national security. —William A. Parquette Foreign Denial and Deception Committee National Intelligence Council Gary Ross has pulled together in this splendid book all the raw material needed to spark a fresh discussion between the government and the media on how to function under our unique system of government in this ever-evolving information-rich environment. -
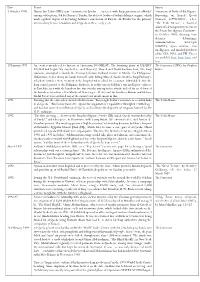
Date Event Source 1 October 1990 Usama Bin Ladin (UBL) Sent
Date Event Source 1 October 1990 Usama bin Ladin (UBL) sent “emissaries to Jordan … to meet with Iraqi government officials” ‘Summary of Body of Intelligence among a delegation, led by Hassan al-Turabi, the de facto leader of Sudan’s Islamist regime, which Reporting on Iraq-al Qaeda made a public display of defending Saddam’s annexation of Kuwait. Al-Turabi was the primary Contacts (1990-2003)’, a.k.a. intermediary between Saddam and al-Qaeda in these early years. “The Feith Memo”, a classified annex of a Pentagon report sent to the Senate Intelligence Committee in October 2003, drawing from detainee debriefings, communications intercepts (SIGINT), open sources, raw intelligence, and finished products of the CIA, NSA, and FBI. Pieces are available here, here, here, and here. 19 January 1991 An event remembered to history as Operation DOGMEAT: The bombing phase of DESERT The Connection (2004), by Stephen STORM had begun two days before, and Ahmed J. Ahmed and Abdul Kadham Saad, two Iraqi Hayes students, attempted to bomb the Thomas Jefferson Cultural Center in Manila, the Philippines. Unfortunately (for them) the bomb went off early, killing Ahmed. Saad recited the Iraqi Embassy’s telephone number from memory at the hospital when asked for a contact. Muwafak al-Ani, the Iraqi consul general at the Philippine Embassy, in reality one of Saddam’s top intelligence officers in East Asia, met with the bombers five times in the run-up to the attack; indeed his car delivered the bombers to within a few blocks of their target. Al-Ani and the brothers Husam and Hisham Abdul Sattar were ordered out of the country for involvement in this. -

The Importance of the SUA Convention in the Fight Against Violence at Sea
MASTER OF SCIENCE IN MARITIME SCIENCE MASTER DISSERTATION Academic year 2017 – 2018 The importance of the SUA Convention in the fight against violence at sea Student: Jan Van Hauwaert Submitted in partial fulfillment of the requirements for Supervisor: Prof. Dr. Frank Maes the degree of: Master of Science in Maritime Science Assessor: Klaas Willaert Master of Science in Maritime Science 2 Word of thanks Before moving on to the content of this master’s dissertation, I would like to express some words of gratitude. In the first place, I would like to thank my promotor, Prof. Dr. Frank Maes, for granting me the opportunity and the privilege to write a thesis on such an interesting topic. Also, I would like to thank him for sharing his knowledge with me and for discussing with me the best way to approach this task. I would like to express thanks to my assessor, Mr. Klaas Willaert, as well, for observing my progress and for reaching out new ideas. Finally, a word of gratitude for my family and the people around me, especially my parents, for the many support throughout the difficult process of writing a thesis. 3 List of abbreviations BCN weapons Biological, chemical and nuclear weapons ICAO International Civil Aviation Organization ICFTU International Confederation of Free Trade Unions ICS International Chamber of Shipping ISF International Shipping Federation ISPS International Ship and Port Facility Code IMO International Maritime Organization Interpol International Criminal Police Organization LNG Liquified Natural Gas MARPOL International Convention for the Prevention of Pollution from Ships NATO North-Atlantic Treaty Organization PLF Palestine Liberation Front PLO Palestine Liberation Organization SOLAS International Convention for the Safety of Life at Sea SUA Convention Convention for the Suppression of Unlawful Acts of violence at Sea against the Safety of Maritime Navigation UN United Nations UK United Kingdom USA United States of America WMD Weapons of mass destruction 4 Table of contents I. -

ABSOLUTE FINAL ONEIL Dissertation
UCLA UCLA Electronic Theses and Dissertations Title Dealing with the Devil? Explaining the Onset of Strategic State-Terrorist Negotiations Permalink https://escholarship.org/uc/item/5td7j61f Author O'Neil, Siobhan Publication Date 2014 Peer reviewed|Thesis/dissertation eScholarship.org Powered by the California Digital Library University of California UNIVERSITY OF CALIFORNIA Los Angeles Dealing with the Devil? Explaining the Onset of Strategic State-Terrorist Negotiations A dissertation submitted in partial satisfaction of the requirements for the degree Doctor of Philosophy in Political Science by Siobhan O’Neil 2014 ABSTRACT OF THE DISSERTATION Dealing with the Devil? Explaining the Onset of Strategic State-Terrorist Negotiations by Siobhan O’Neil Doctor of Philosophy in Political Science University of California, Los Angeles, 2014 Professor Arthur Stein, Chair Statesmen are quick to declare that they will not negotiate with terrorists. Yet, the empirical record demonstrates that, despite statements to the contrary, many states do eventually negotiate with their terrorist challengers. My dissertation examines the circumstances under which states employ strategic negotiations with terrorist groups to resolve violent conflict. I argue that only when faced with a credible and capable adversary and afforded relative freedom of action domestically will states negotiate with terrorists. To test this theory, I use a multi-method approach that incorporates a cross- national study of all known strategic negotiations from 1968-2006 and three within-case studies (Israel, Northern Ireland, and the Philippines). Initial results suggest that negotiations are employed in about 13% of terrorist campaigns, certain types of groups are privileged, and negotiations only occur when statesmen can overcome domestic ii obstacles, namely public and veto player opposition. -

The Guitarist and Sinking Ships
Volume 2011-2012, Issue 5 Whiting Lane School Newspaper April ~ May 2012 “Weird But True” Edition Weird but True Story: The Guitarist and Sinking Ships By Joshua Sirman Here is a weird but true story. In 1991 a musician named Moss Hills was playing on a cruise ship, the MTS Oceanos, when the boat starting tipping over in high waves near South Africa. The captain gave the order to abandon ship and then he and the crew left without helping the passengers. Moss went to the bridge of the sinking ship and radioed the South African Navy for help. The Navy asked “What rank are you?” Moss said, “I’m the guitarist, and the crew is gone.” The Navy told Moss how to organize the passengers to be rescued by helicopters. Moss and his wife, Tracey, worked to help all the passengers get off the ship using rescue lines from the helicop- ters. Moss was one of the last five people off the ship. The Oceanos sank a short time later. The captain of the Oceanos was convicted of neglecting his duty and went to jail. Moss was a hero. Now for the really weird part. Three years later, in 1994, Moss was playing guitar on another cruise ship, MS Achille Lauro. During the cruise, the ship caught fire and started to sink in the Indian Ocean. Moss used what he learned on the Oceanos and again helped passengers to safety. Moss Hills survived two major cruise ship disasters in three years, but he still plays guitar on cruise ships and says he won’t leave the sea. -

CIA Mission: Destroy the Whistleblower and Perfume the Stench of ‘Operation Merlin’
CIA Mission: Destroy the Whistleblower and Perfume the Stench of ‘Operation Merlin’ By Norman Solomon Region: USA Global Research, February 04, 2015 Theme: Intelligence Expose Facts The leak trial of CIA officer Jeffrey Sterling never got near a smoking gun, but the entire circumstantial case was a smokescreen. Prosecutors were hell-bent on torching the defendant to vindicate Operation Merlin, nine years after a book by James Risen reported that it “may have been one of the most reckless operations in the modern history of the CIA.” That bestselling book, State of War, seemed to leave an indelible stain on Operation Merlin while soiling the CIA’s image as a reasonably competent outfit. The prosecution of Sterling was a cleansing service for the Central Intelligence Agency, which joined with the Justice Department to depict the author and the whistleblower as scurrilous mud-throwers. In the courtroom, where journalist Risen was beyond the reach of the law, the CIA’s long- smoldering rage vented at the defendant. Sterling had gone through channels in 2003 to warn Senate Intelligence Committee staffers about Operation Merlin, and he was later indicted for allegedly giving Risen classified information about it. For CIA officials, the prosecution wasn’t only to punish Sterling and frighten potential whistleblowers; it was also about payback, rewriting history and assisting with a PR comeback for the operation as well as the agency. Last week, the jury — drawn from an area of Northern Virginia that is home to CIA headquarters, the Pentagon and a large number of contractors for the military-industrial- intelligence complex — came back with guilty verdicts on all counts.