Internet Users Per 100 Inhabitants
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

LACTLD REPORT the Latin American and Caribbean Cctld Publication
ISSN: 2301-1025 2nd year, 3rd edition twitter.com/lactld facebook.com/LACTLD LACTLD REPORT The Latin American and Caribbean ccTLD publication ANOTHER YEAR OF GROWTH AND CHANGES The Internet is constantly evolving. So are its challenges. The opportunities for development, participation and representation of stakeholders in the region encourage us to face 2014 with high expectations. IETF, by two regional technical experts Address: Rbla Rep. de México 6125, CP 11400, Security: personal data protection in Latin America Montevideo, Uruguay Tel.: + 598 2604 2222* (General Contact) Email: [email protected] www.lactld.org Enhanced cooperation and Internet governance EDITORIAL STAFF CONTINUED COLLABORATION: LACTLD Report LACTLD REPORT FIRST ANNIVERSARY 3rd edition 2nd year, 2013 Dear Readers, Board of Directors Eduardo Santoyo Another year ends – with plenty Luis Arancibia of debates, discussions and Víctor Abboud joint efforts to stimulate the Clara Collado ccTLD growth, both within and Frederico Neves outside the region of Latin America and the Caribbean. In Editorial Board Eduardo Santoyo this letter I would like to thank Luis Arancibia you all for your hard work and Clara Collado also invite you to continue Carolina Aguerre sharing the rewarding task of promoting Registry cooperation General Coordination and development during 2014. Marilina Esquivel The third issue of the LACTLD Report contains various articles and piece of news. A relevant announcement Editorial assistant is that the publication is now catalogued under the ISSN system, which will Sofía Zerbino enable to index and reference globally. In terms of the information, there is Art & Design information about ICANN’s new Engagement Center in Latin America and the Frida Caribbean, which opened in Montevideo, Uruguay and it aims to increase the representation of diverse stakeholders within the scope of this organization. -
Freedom on the Net 2011 1 F H
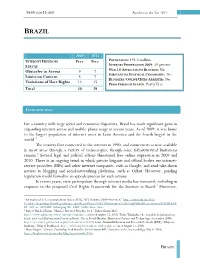
REEDOM OUSE Freedom on the Net 2011 1 F H BRAZIL 2009 2011 INTERNET FREEDOM Free Free POPULATION: 193.3 million INTERNET PENETRATION 2009: 39 percent STATUS 0 Obstacles to Access 9 7 WEB 2.0 APPLICATIONS BLOCKED: No SUBSTANTIAL POLITICAL CENSORSHIP: No Limits on Content 8 7 BLOGGERS/ONLINE USERS ARRESTED: No Violations of User Rights 13 15 PRESS FREEDOM STATUS: Partly Free Total 30 29 INTRODUCTION For a country with large social and economic disparities, Brazil has made significant gains in expanding internet access and mobile-phone usage in recent years. As of 2009, it was home to the largest population of internet users in Latin America and the fourth largest in the world.1 The country first connected to the internet in 1990, and connectivity is now available in most areas through a variety of technologies, though some infrastructural limitations remain.2 Several legal and judicial actions threatened free online expression in 2009 and 2010. There is an ongoing trend in which private litigants and official bodies sue internet- service providers (ISPs) and other internet companies, such as Google, and send take-down notices to blogging and social-networking platforms, such as Orkut. However, pending legislation would formalize an appeals process for such actions. In recent years, civic participation through internet media has increased, including in 3 response to the proposed Civil Rights Framework for the Internet in Brazil. Moreover, 1 International Telecommunications Union (ITU), “ICT Statistics 2009—Internet,” http://www.itu.int/ITU- D/icteye/Reporting/ShowReportFrame.aspx?ReportName=/WTI/InformationTechnologyPublic&ReportFormat=HTML4.0& RP_intYear=2009&RP_intLanguageID=1&RP_bitLiveData=False. -

Download File
INTERNET FOR ALL Proceedings of the Third Internet Governance Forum Hyderabad, India 3-6 December 2008 Edited by Don MacLean General Table of Contents Message by Sha Zukang, Under-Secretary-General, United Nations Department of Economic and Social Affairs (UNDESA) ……………………..i Introduction……………………………………………………………...……….ii Preface ......................................................................................................... 1 Setting the Scene ....................................................................................... 5 Opening Ceremony, 3 December 2008.....................................................6 Opening Session, 3 December 2008.......................................................16 Part 1 – Reaching the Next Billion.............................................................. 34 Chairman’s Summary of the Main Sessions..........................................35 Panel Discussion on Realizing a Multilingual Internet .........................39 Panel Discussion on Access...................................................................50 Open Dialogue on Reaching the Next Billion ........................................67 Reports of Workshops, Best Practice Forums, Open Forums and Dynamic Coalitions ..................................................................................84 Part 2 – Promoting Cyber-security and Trust ........................................... 117 Chairman’s Summary of Main Sessions ..............................................118 Panel Discussion on Dimensions of Cyber-security -

Law and Internet in Brazil
Special series Law and internet in Brazil Sérgio Branco Introduction This series is written by Sérgio Branco for canadian site DroitDu.net. In eight articles the director of ITS Rio aproaches diferent topics about Brazilian internet law, from the removal of contents on Youtube to questions regarding the “right to be forgotten” and net neutrality. The texts are translated to portuguese and published in ITS FEED, the content channel of Instituto de Tecnologia e Sociedade do Rio. Summary How a top model helped to regulate Brazilian Internet 04 Is it possible to crowdsource a law? 07 What are you liable for? 11 Why Brazil Needs a New Copyright Law 15 Nine Questions Regarding “the Right to Be Forgotten” 20 Net Neutrality: You Love it, even if you don’t Really Know what it is 25 Brazilian Internet is Partly Free 30 The Futures of the Internet 34 Special Series: Law and Internet in Brazil How a top model helped to regulate In 2006, Brazilian top model and tv presenter Brazilian Internet Daniella Cicarelli was spending some time with her boyfriend on a beach at Cadiz, south of Spain. On a sunny day and a public beach, with many sunbathers around the couple, they ended performing some intimate moments inside the sea. The event was recorded in details and soon after it was everywhere on the internet. The interest in Daniella Cicarelli was not surprising. In the year before, she got married to Ronaldo, aka Ronaldo Fenômeno, one of most famous Brazilian soccer players in the world. By that time, he played for Real Madrid, and she was a famous model. -

A Geopolítica Da Rede E a Governança Global De Internet a Partir Da Cúpula Mundial Sobre a Sociedade Da Informação
Universidade de São Paulo MICHÉLE TANCMAN CANDIDO DA SILVA A GEOPOLÍTICA DA REDE E A GOVERNANÇA GLOBAL DE INTERNET A PARTIR DA CÚPULA MUNDIAL SOBRE A SOCIEDADE DA INFORMAÇÃO SÃO PAULO 2008 MICHÉLE TANCMAN CANDIDO DA SILVA 1 A GEOPOLÍTICA DA REDE E GOVERNANÇA GLOBAL DA INTERNET A PARTIR DA CÚPULA MUNDIAL SOBRE A SOCIEDADE DA INFORMAÇÃO Tese apresentada ao Programa de Pós-Graduação Geografia Humana, da Faculdade de Filosofia, Letras e Ciências Humanas da Universidade de São Paulo, para a obtenção do título de Doutor em Geografia. Área de Concentração: Geografia Política Orientador: Dr. José William Vesentini SÃO PAULO 2008 2 MICHÉLE TANCMAN CANDIDO DA SILVA A GEOPOLÍTICA DA REDE E GOVERNANÇA GLOBAL DA INTERNET A PARTIR DA CÚPULA MUNDIAL SOBRE A SOCIEDADE DA INFORMAÇÃO Tese apresentada ao Programa de Pós- Graduação Geografia Humana, da Faculdade de Filosofia, Letras e Ciências Humanas da Universidade de São Paulo, para a obtenção do título de Doutor em Geografia. Área de Concentração: Geografia Humana APROVADA em: Banca Examinadora Prof. Dr. José Willian Vesentini Instituição: FFLCH – USP Assinatura:___________________________ Prof. Dr André Roberto Martin Instituição: FFLCH – USP Assinatura:___________________________ Prof. Dr. Hindenburgo Francisco Pires Instituição: UERJ Assinatura:___________________________ Prof. Dr. Jorge Alberto Silva Machado Instituição: EACH - USP Assinatura:___________________________ Prof. Dr. Carlos Alberto Franco da Silva Instituição: UFF Assinatura:___________________________ 3 Dedico esta tese ao meu marido e amigo Jorge Candido, às minhas filhas Nicolle e Natasha, ao meu filho Ricardo, à minha mãe Mauricette, a minha avó Memê, ao meu avô Zaida (in memorian), meus irmãos, a toda minha família e aos alunos e mestres da Geografia. -

OECD Telecommunication and Broadcasting Review of Brazil 2020 Brazil 2020 Brazil of Review Broadcasting and Telecommunication OECD
OECD Telecommunication and Broadcasting Review of azil 2020 Br OECD Telecommunication and Broadcasting Review of Brazil 2020 OECD Telecommunication and Broadcasting Review of Brazil 2020 This work is published under the responsibility of the Secretary-General of the OECD. The opinions expressed and arguments employed herein do not necessarily reflect the official views of OECD member countries. This document, as well as any data and map included herein, are without prejudice to the status of or sovereignty over any territory, to the delimitation of international frontiers and boundaries and to the name of any territory, city or area. The statistical data for Israel are supplied by and under the responsibility of the relevant Israeli authorities. The use of such data by the OECD is without prejudice to the status of the Golan Heights, East Jerusalem and Israeli settlements in the West Bank under the terms of international law. Please cite this publication as: OECD (2020), OECD Telecommunication and Broadcasting Review of Brazil 2020, OECD Publishing, Paris, https://doi.org/10.1787/30ab8568-en. ISBN 978-92-64-31744-4 (print) ISBN 978-92-64-93255-5 (pdf) Photo credits: Cover © Sarunyu_foto/Shutterstock; © ElenVD/Shutterstock. Corrigenda to publications may be found on line at: www.oecd.org/about/publishing/corrigenda.htm. © OECD 2020 The use of this work, whether digital or print, is governed by the Terms and Conditions to be found at http://www.oecd.org/termsandconditions. FOREWORD 3 Foreword The OECD Directorate for Science, Technology and Innovation (DSTI) carried out this study under the auspices of the Committee on Digital Economy Policy (CDEP) and the Working Party of Communication Infrastructures and Services Policy (WPCISP). -

The Brazilian Multistakeholderism on Internet Governance1 Abstract 1
1 The Brazilian Multistakeholderism on Internet Governance Fernanda R. Rosa Working paper – October, 03 2016 Columbia University’s School of International and Public Affairs Abstract This work analyzes the Brazilian Internet Steering Committee’s (CGI.br), a pioneering experience of multistakeholderism in the field of Internet governance, since 1995. It describes the CGI.br’s development that culminates in a self-sustainable financial model, the establishment of an election process to choose the civil society representatives, and the emergence of different kinds of multistakeholderisms within the organization. This work shows how the government has had a central role in the construction of the current CGI.br, sponsoring multistakeholder efforts since its conception, elaborating its decree and assenting to be subject to a homogeneous hierarchy among other stakeholders. It analyzes some of the controversies that emerge from the institutional design of CGI.br, its legal sponsorship and the openness to more participation, revealing the challenges of its current procedural rules. Considering the CGI.br a successful case in multistakeholderism and also in policy, this work proposes improvements, in terms of rules and design, to leverage their consistence and the diversity of interests within the organization. This work is informed by a 2-month fieldwork research conducted through participatory observations and in-depth interviews at the executive office of CGI.br and at events supported by it. Based on that, suggestions for future research are proposed. Keywords: national Internet governance, multistakeholderism, participation, representation, electoral colleges, Brazil. 1. Introduction The purpose of this study is to analyze the Brazilian Internet Steering Committee’s (CGI.br)i trajectory, an experience of multistakeholderism in the field of Internet governance at a national level. -

Latin American and Caribbean DNS Marketplace Study
Latin American and Caribbean DNS Marketplace Study Contents 1. Executive Summary ........................................................................................................................... 4 2. An Introduction to the Region .......................................................................................................... 7 2.1 Which countries are included in the Study? ................................................................................ 7 3. The Internet Environment in the LAC Region .................................................................................... 8 3.1 Factors influencing domain name uptake ................................................................................... 8 3.2 Domain name growth drivers ................................................................................................... 11 3.3 Foundations of Internet development ...................................................................................... 15 3.4 Internet users and Internet use in the region ........................................................................... 33 3.5 Local languages in the region .................................................................................................... 39 4. The Domain Name Industry in the LAC region ................................................................................ 40 4.1 Domain name registries ............................................................................................................ 41 4.2 International Registrars............................................................................................................ -

Brazil, the Internet and the Digital Bill of Rights Reviewing the State of Brazilian Internet Governance
STRATEGIC IGARAPÉ INSTITUTE PAPER a think and do tank 25 APRIL 2017 Brazil, the Internet and the Digital Bill of Rights Reviewing the State of Brazilian Internet Governance Daniel Arnaudo Brazil, the Internet and the Digital Bill of Rights - Reviewing the State of Brazilian Internet Governance Table of Contents List of Abbreviations 1 Abstract 2 Introduction and Key Findings 3 A Brief History of the MCI 5 Understanding Internet Governance through the Marco Civil 7 Freedom of Expression, Privacy and Human Rights 8 Democratic and Collaborative Governance 15 Universality, Diversity, Innovation 17 Network Neutrality 23 Infrastructure Update 25 Security, Functionality and Stability 30 Brazilian Internet Governance on the Global Stage 35 Conclusion 36 Annex: Key Articles in the Marco Civil da Internet 39 References 43 IGARAPÉ INSTITUTE | STRATEGIC PAPER 25 | APRIL 2017 List of Abbreviations MCI - Marco Civil da Internet [Internet Bill of ABIN - Agência Brasileira de Inteligência Nacional Rights] [Brazilian National Intelligence Agency] NSA - National Security Agency ANATEL - Agência Nacional de Telecomunicações [National Telecommunications PL/PLS - Proposed Law/Proposed Senate Law Agency] PNBL - Plano Nacional da Banda Larga [National ASN - Autonomous System Number Broadband Plan] BRICS - Brazil, Russia, India, China and South RIR - Regional Internet Registry Africa TLD - Top Level Domain CDCiber - Center for Cybernetic Defense WCIT - World Conference on International CGI - Comitê Gestor da Internet [Internet Steering Telecommunications Committee] -

State of the Practice of Computer Security Incident Response Teams (Csirts)
State of the Practice of Computer Security Incident Response Teams (CSIRTs) Georgia Killcrece Klaus-Peter Kossakowski Robin Ruefle Mark Zajicek October 2003 TECHNICAL REPORT CMU/SEI-2003-TR-001 ESC-TR-2003-001 Pittsburgh, PA 15213-3890 State of the Practice of Computer Security Incident Response Teams (CSIRTs) CMU/SEI-2003-TR-001 ESC-TR-2003-001 Georgia Killcrece Klaus-Peter Kossakowski Robin Ruefle Mark Zajicek October 2003 Networked Systems Survivability Program Unlimited distribution subject to the copyright. This report was prepared for the SEI Joint Program Office HQ ESC/DIB 5 Eglin Street Hanscom AFB, MA 01731-2116 The ideas and findings in this report should not be construed as an official DoD position. It is published in the interest of scientific and technical information exchange. FOR THE COMMANDER Christos Scondras Chief of Programs, XPK This work is sponsored by the U.S. Department of Defense. The Software Engineering Institute is a federally funded research and development center sponsored by the U.S. Department of Defense. Copyright 2003 Carnegie Mellon University. NO WARRANTY THIS CARNEGIE MELLON UNIVERSITY AND SOFTWARE ENGINEERING INSTITUTE MATERIAL IS FURNISHED ON AN "AS-IS" BASIS. CARNEGIE MELLON UNIVERSITY MAKES NO WARRANTIES OF ANY KIND, EITHER EXPRESSED OR IMPLIED, AS TO ANY MATTER INCLUDING, BUT NOT LIMITED TO, WARRANTY OF FITNESS FOR PURPOSE OR MERCHANTABILITY, EXCLUSIVITY, OR RESULTS OBTAINED FROM USE OF THE MATERIAL. CARNEGIE MELLON UNIVERSITY DOES NOT MAKE ANY WARRANTY OF ANY KIND WITH RESPECT TO FREEDOM FROM PATENT, TRADEMARK, OR COPYRIGHT INFRINGEMENT. Use of any trademarks in this report is not intended in any way to infringe on the rights of the trademark holder. -

Brazilian Internet Bill Of
Brazil’s Internet Bill of Rights: A Closer Look Carlos Affonso Souza, Mario Viola & Ronaldo Lemos (eds.) Brazil’s Internet Bill of Rights: A Closer Look Carlos Affonso Souza, Mario Viola & Ronaldo Lemos (eds.) Second Edition © 2017 Institute for Technology and Society of Rio de Janeiro (ITS Rio) Editing Carlos Affonso Souza, Mario Viola & Ronaldo Lemos Revision Beatriz Nunes Cover and design Thiago Dias Publication, bound and print Editar Editora Associada – Juiz de Fora – MG, Brazil +55 32 3213-2529 / +55 32 3241-2670 International data for the purposes of cataloging of the publication S719b Souza, Carlos Affonso V795b Viola, Mario L544b Lemos, Ronaldo Brazil’s Internet Bill of Rights: A Closer Look / Carlos Affonso Souza, Mario Viola & Ronaldo Lemos. ___________________ ISBN: 978-85- 7851-172- 2 1. Information technology. 2. Internet. CDD 004 CDU 004.7 License under Creative Commons 4.0 Attribution-NonCommercial-ShareAlike 4.0 International (CC BY-NC-SA 4.0) For more information: https://creativecommons.org/licenses/by-nc-sa/4.0/ Summary 5 Introduction 7 Law no. 12.965 of April 23, 2014 (The Internet Bill of Rights) 29 Brazil’s Internet Bill of Rights Regulatory Decree no. 8.771/2016 41 Ronaldo Lemos 1. The Internet Bill of Rights as an Example of Multistakeholderism 51 Sérgio Branco 2. Notes on Brazilian Internet Regulation 71 Celina M.A. Bottino and Fabro Steibel 3. A Collaborative and Open Internet Bill: the policy-making process of the Internet Bill of Rights 81 Mario Viola 4. Data Protection & Privacy in the Internet Era: the Internet Bill of Rights 89 Carlos Affonso Souza 5. -

Moving Beyond Connectivity
Improving Public Internet Access in Brazil: MMoovviinngg BBeeyyoonndd CCoonnnneeccttiivviittyy...... Martha Fuentes and Joseph Straubhaar Telecommunication and Information Policy Institute University of Texas Report for School of the Future University of São Paulo June 29, 2001 1 BRAZIL IN THE CROSSROADS... Since 1998 Latin America has exhibited the highest rates of Internet growth among all world's regions (ITU, 2000). The Latin 'net fever' is commonly measured in terms of number of Internet users and hosts1. Between 1995 and 1999, the number of Latin American Internet users climbed from 540,000 to 9 million. And only in 2000, the number of hosts increased 136 %, well above the expansion rate in North America (74 %), Asia (61 %), Europe (30 %) and Africa (18 %). Brazil is an important contributor to these statistics. With 32.4 % of the region's users and 45 % of the regional hosts, Brazil is considered the leading Latin American market by investors and marketers that set in motion the world digital economy (Elkin, 2001; Rojo, 2000). For observers less concerned with potential revenues of the e-economy, Brazil presents a contradictory trend: the deceleration of web users' growth, which has caused the country to fall in the rank of Internet penetration in the region (Table 1). The demand for Internet use is not accompanying the expansion of infrastructure that situates Brazil in the fifth place of host penetration in the region. So some factors or barriers to Internet use may be slowing the increase in new users in Brazil. Table 1. Internet Penetration Rank in Latin America Rank 1998 Users/ Rank 2000 Users/ Hosts /10,000 people 100 people 100 people (2000) 1 Uruguay 162.02 1 Uruguay 6.99 1 Chile 11.55 2 Argentina 72.98 2 Costa Rica 2.60 2 Uruguay 11.08 3 Mexico 56.55 3 Chile 1.68 3 Argentina 6.75 4 Panama 52.82 4 Brazil 1.51 4 Costa Rica 6.21 5 Brazil 51.53 5 Venezuela 1.50 5 Venezuela 3.93 6 Chile 49.11 6 Mexico 1.41 6 Brazil 2.94 7 Costa Rica 18.29 7 Panama 1.08 7 Mexico 2.74 8 Colombia 11.06 8 Colombia 0.89 8 Colombia 2.07 9 Dominican Rep.