Improving Internet Usability – a Framework for Domain Name Policy Evaluation
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

SEARCH CONTENT File P3 OPTIMISATION Why Aussie Websites Are How Do Aussie Websites Missing Prime Content Fare? P10 Opportunities P9
Edition 5, Nov 2015 BEHIND THE DOT state of the .au domain ONLINE SUCCESS Our nation’s best websites - 8 common traits p8 zone ahead A comprehensive analysis of the WEBSITE .au zone SEARCH CONTENT file p3 OPTIMISATION Why Aussie websites are How do Aussie websites missing prime content fare? p10 opportunities p9 @AusRegistry_au ausregistry.com.au Behind the Dot - State of the .au Domain is a quarterly magazine presenting .au statistics, expert commentary, analysis, industry related articles and feature stories. Publisher: AusRegistry Editor in Chief: George Pongas Managing Editor: Maggie Whitnall Regular Contributors: Maggie Whitnall, Alison Coffa, Michael Korjen, Adrian Kinderis, George Pongas, Jo Lim Data Analysis: Penelope Green Account Management and Circulation: Courtney Fabian Creative Director: Michelle O’Reilly ____________ Advertising Sales: [email protected] Contents DEPARTMENTS CHARTS & TABLES Under the Microscope ........................................................................1 .au Domains Under Management .......................................................1 An overview of the number of .au domains currently under .au Monthly Creates ............................................................................1 management (open 2LDs), monthly registrations, renewals by age of domain and APTLD statistics. Renewal Rates by Domain Age ...........................................................2 .au Research and Surveys ....................................................................2 Domain Numbers -

LACTLD REPORT the Latin American and Caribbean Cctld Publication
ISSN: 2301-1025 2nd year, 3rd edition twitter.com/lactld facebook.com/LACTLD LACTLD REPORT The Latin American and Caribbean ccTLD publication ANOTHER YEAR OF GROWTH AND CHANGES The Internet is constantly evolving. So are its challenges. The opportunities for development, participation and representation of stakeholders in the region encourage us to face 2014 with high expectations. IETF, by two regional technical experts Address: Rbla Rep. de México 6125, CP 11400, Security: personal data protection in Latin America Montevideo, Uruguay Tel.: + 598 2604 2222* (General Contact) Email: [email protected] www.lactld.org Enhanced cooperation and Internet governance EDITORIAL STAFF CONTINUED COLLABORATION: LACTLD Report LACTLD REPORT FIRST ANNIVERSARY 3rd edition 2nd year, 2013 Dear Readers, Board of Directors Eduardo Santoyo Another year ends – with plenty Luis Arancibia of debates, discussions and Víctor Abboud joint efforts to stimulate the Clara Collado ccTLD growth, both within and Frederico Neves outside the region of Latin America and the Caribbean. In Editorial Board Eduardo Santoyo this letter I would like to thank Luis Arancibia you all for your hard work and Clara Collado also invite you to continue Carolina Aguerre sharing the rewarding task of promoting Registry cooperation General Coordination and development during 2014. Marilina Esquivel The third issue of the LACTLD Report contains various articles and piece of news. A relevant announcement Editorial assistant is that the publication is now catalogued under the ISSN system, which will Sofía Zerbino enable to index and reference globally. In terms of the information, there is Art & Design information about ICANN’s new Engagement Center in Latin America and the Frida Caribbean, which opened in Montevideo, Uruguay and it aims to increase the representation of diverse stakeholders within the scope of this organization. -

Chapter 7: Protecting the Integrity of the Internet
7 Protecting the Integrity of the Internet Introduction 7.1 This chapter discusses current and future initiatives for promoting a more secure Internet environment. In particular, it considers the role of the Australian Communications and Media Authority (ACMA), Internet Service Providers (ISPs), and Domain Name Registrars and Resellers in promoting greater resilience within the Australian Internet networks. 7.2 The chapter focuses on six key issues: the effectiveness of the Australian Internet Security Initiative (AISI) to detect and drive the remediation of bots; the role of ISPs in the AISI and the proposed Internet industry e- security code of practice; remediation of infected computers; ACMA‟s capacity to respond to the threat of compromised websites; ACMA‟s spam reporting initiative and the role of ISPs under the Spam Code of Practice; and e-security and the Domain Name Registration System. Australian Internet Security Initiative 7.3 The ACMA is a statutory authority within the Australian Government portfolio of Broadband, Communications and the Digital Economy. The 128 HACKERS, FRAUDSTERS AND BOTNETS: TACKLING THE PROBLEM OF CYBER CRIME ACMA is responsible for regulating broadcasting, the Internet, radio communications and telecommunications.1 7.4 The ACMA developed the AISI in 2005. The AISI identifies computers operating on the Australian Internet that have been infected by malware and are able to be controlled for illegal activities.2 The Committee was told that AISI has been progressively expanded over time and has attracted international interest.3 7.5 As noted previously in this report, 99 per cent of spam is sent from botnets.4 Spam email is one of the primary vectors of malware and the dissemination of scams and phishing attacks on end users. -
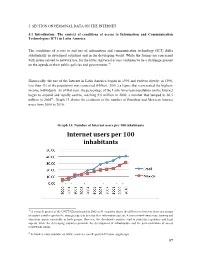
Internet Users Per 100 Inhabitants
5. SECTION ON PERSONAL DATA ON THE INTERNET 5.1 Introduction: The context of conditions of access to Information and Communication Technologies (ICT) in Latin America The conditions of access to and use of information and communication technology (ICT) differ substantially in developed countries and in the developing world. While the former are concerned with issues related to network use, for the latter, universal access continues to be a challenge present on the agenda of their public policies and governments.40 Historically, the use of the Internet in Latin America begins in 1996 and evolves slowly: in 1998, less than 1% of the population was connected (Hilbert, 2001,) a figure that represented the highest- income individuals. As of that year, the percentage of the Latin American population on the Internet began to expand and rapidly evolve, reaching 9.9 million in 2000, a number that jumped to 60.5 million in 200541. Graph 13 shows the evolution of the number of Brazilian and Mexican Internet users from 2000 to 2010: Graph 13: Number of Internet users per 100 inhabitants Internet users per 100 inhabitants 40 A research project of the UNCTAD performed in 2002 in 51 countries shows the differences between these two groups of countries with regard to the strategies used to develop their information society. A concern with awareness, training and education appear repeatedly in both groups. However, the developed countries tend to prioritize regulatory and legal aspects, while the developing countries prioritize the development of infrastructure and the universalization of access (UNCTAD, 2002). 41 E-Marketer data available at: www.emarketer.com/Reports/All?Latam_aug06.aspx. -

CPS December 1994 - Publications - U.S
CPS December 1994 - Publications - U.S. Census Bureau Publications You are here: Census.gov › Publications › Current Population Survey, December 1994: Lead Paint Survey E Publications Main Current Population Survey, December 1994: Lead Paint Survey E TECHNICAL DOCUMENTATION - CPS-94 Current Population Survey, December 1994: Lead Paint Survey [machine-readable data file] / conducted by the Bureau of the Census for the Department of Housing and Urban Development. --Washington: Bureau of the Census [producer and distributor], 1997. This file documentation consists of the following materials: Attachment 1 - Abstract Type of File: Microdata; unit of observation is individuals within housing units. Universe Description: The universe consists of all persons in the civilian noninstitutional population of the United States living in households. The probability sample selected to represent the universe consists of approximately 57,000 households. Subject-Matter Description: Data are provided on labor force activity for the week prior to the survey. Comprehensive data are available on the employment status, occupation, and industry of persons 15 years old and over. Also shown are personal characteristics such as age, sex, race, marital status, veteran status, household relationship, educational background, and Hispanic origin. The lead paint questions were asked for the household. They provide information on the current awareness of the health hazards associated with lead-based paint. Geographic Coverage: State of residence is uniquely identified as well as census geographic division and region. The 113 largest metropolitan areas (CMSA's or MSA's), 89 selected MSA's, 66 selected PMSA's, and 30 central cities in multi-central city MSA's or PMSA's also are uniquely identified.1 Within confidentiality restrictions, indicators are provided for MSA-PMSA/non-MSA-PMSA, central city/noncentral city, farm/non-farm, and MSA/CMSA size. -

An Analysis of the Nature of Groups Engaged in Cyber Crime
International Journal of Cyber Criminology Vol 8 Issue 1 January - June 2014 Copyright © 2014 International Journal of Cyber Criminology (IJCC) ISSN: 0974 – 2891 January – June 2014, Vol 8 (1): 1–20. This is an Open Access paper distributed under the terms of the Creative Commons Attribution-Non- Commercial-Share Alike License, which permits unrestricted non-commercial use, distribution, and reproduction in any medium, provided the original work is properly cited. This license does not permit commercial exploitation or the creation of derivative works without specific permission. Organizations and Cyber crime: An Analysis of the Nature of Groups engaged in Cyber Crime Roderic Broadhurst,1 Peter Grabosky,2 Mamoun Alazab3 & Steve Chon4 ANU Cybercrime Observatory, Australian National University, Australia Abstract This paper explores the nature of groups engaged in cyber crime. It briefly outlines the definition and scope of cyber crime, theoretical and empirical challenges in addressing what is known about cyber offenders, and the likely role of organized crime groups. The paper gives examples of known cases that illustrate individual and group behaviour, and motivations of typical offenders, including state actors. Different types of cyber crime and different forms of criminal organization are described drawing on the typology suggested by McGuire (2012). It is apparent that a wide variety of organizational structures are involved in cyber crime. Enterprise or profit-oriented activities, and especially cyber crime committed by state actors, appear to require leadership, structure, and specialisation. By contrast, protest activity tends to be less organized, with weak (if any) chain of command. Keywords: Cybercrime, Organized Crime, Crime Groups; Internet Crime; Cyber Offenders; Online Offenders, State Crime. -

December 2013 Feature Article: the Year of Surviving Dangerously: Highlights from We Live Security 2013
December 2013 Feature Article: The Year of Surviving Dangerously: Highlights from We Live Security 2013 Table of Contents The Year of Surviving Dangerously: Highlights from We Live Security 2013 .............................................................3 2013: a Scammer’s Eye View ................................................................................................................................... 11 ESET Corporate News .............................................................................................................................................. 18 The Top Ten Threats ................................................................................................................................................ 18 Top Ten Threats at a Glance (graph) ....................................................................................................................... 21 About ESET .............................................................................................................................................................. 22 Additional Resources ............................................................................................................................................... 22 This month we decided to present a retrospective of all 2013, pertained to Java vulnerability CVE-2013-0422 being added to a so we develop and delve into the most prominent threats that couple of popular exploit packs, thus making it more accessible each month had. Also published an article that specifically -

Registry Operator's Report
REGISTRY OPERATOR’S REPORT July 2007 Afilias Limited Monthly Operator Report – July 2007 As required by the ICANN/Afilias Limited Registry Agreement (Section 3.1(c)(iv)) this report provides an overview of Afilias Limited activity through the end of the reporting month. The information is primarily presented in table and chart format with text explanations as deemed necessary. Information is provided in order as listed in Appendix 4 of the Registry Agreement. Report Index Section 1 Accredited Registrar Status Section 2 Service Level Agreement Performance Section 3 INFO Zone File Access Activity Section 4 Completed SRS/System Software Releases Section 5 WhoIs Service Activity Section 6 Total Number of Transactions by Subcategory by Month Section 7 Daily Transaction Range Copyright © 2001-2007 Afilias Limited Page 2 of 9 Afilias Limited Monthly Operator Report – July 2007 Section 1 – Accredited Registrar Status – July 2007 The following table displays the current number and status of the ICANN accredited registrars. The registrars are grouped into three categories: 1.Operational registrars: Those who have authorized access into the Shared Registration System (SRS) for processing domain name registrations. 2.Registrars in the Ramp-up Period: Those who have received a password to the Afilias Operational Test and Evaluation (OT&E) environment. The OT&E environment is provided to allow registrars to develop and test their systems with the SRS. 3.Registrars in the Pre-Ramp-up Period: Those who have been sent a welcome letter from Afilias, but have not yet executed the Registry Confidentiality Agreement and/or have not yet submitted a completed Registrar Information Sheet. -
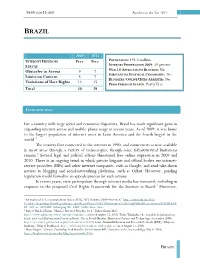
Freedom on the Net 2011 1 F H
REEDOM OUSE Freedom on the Net 2011 1 F H BRAZIL 2009 2011 INTERNET FREEDOM Free Free POPULATION: 193.3 million INTERNET PENETRATION 2009: 39 percent STATUS 0 Obstacles to Access 9 7 WEB 2.0 APPLICATIONS BLOCKED: No SUBSTANTIAL POLITICAL CENSORSHIP: No Limits on Content 8 7 BLOGGERS/ONLINE USERS ARRESTED: No Violations of User Rights 13 15 PRESS FREEDOM STATUS: Partly Free Total 30 29 INTRODUCTION For a country with large social and economic disparities, Brazil has made significant gains in expanding internet access and mobile-phone usage in recent years. As of 2009, it was home to the largest population of internet users in Latin America and the fourth largest in the world.1 The country first connected to the internet in 1990, and connectivity is now available in most areas through a variety of technologies, though some infrastructural limitations remain.2 Several legal and judicial actions threatened free online expression in 2009 and 2010. There is an ongoing trend in which private litigants and official bodies sue internet- service providers (ISPs) and other internet companies, such as Google, and send take-down notices to blogging and social-networking platforms, such as Orkut. However, pending legislation would formalize an appeals process for such actions. In recent years, civic participation through internet media has increased, including in 3 response to the proposed Civil Rights Framework for the Internet in Brazil. Moreover, 1 International Telecommunications Union (ITU), “ICT Statistics 2009—Internet,” http://www.itu.int/ITU- D/icteye/Reporting/ShowReportFrame.aspx?ReportName=/WTI/InformationTechnologyPublic&ReportFormat=HTML4.0& RP_intYear=2009&RP_intLanguageID=1&RP_bitLiveData=False. -

Technical Report RHUL–MA–2014– 2 01 September 2014
Leveraging knowledge sharing for preventing and investigating on-line banking frauds: On-line Fraud Centre Salvatore Camillo Zammataro Technical Report RHUL–MA–2014– 2 01 September 2014 Information Security Group Royal Holloway, University of London Egham, Surrey TW20 0EX, United Kingdom www.ma.rhul.ac.uk/tech Salvatore Camillo “Toto” Zammataro Leveraging knowledge sharing for preventing and investigating on-line banking frauds: On-line Fraud Centre MSc Information Security Project Report Supervisor: Dr John Austen Submitted as part of the requirements for the award of the MSc in Information Security at Royal Holloway, University of London. 1 EXECUTIVE SUMMARY For social, technological and political reasons electronic transactions are now the most used payment method in Europe. As such, fraudsters have been focusing on On-Line transactions to gain money through Phishing and Crimeware. These kind of frauds generates losses for EU citizen of an estimated value of 250M€/year. Banks and Law Enforcement Agencies are engaged in the prevention, detection and prosecution of this crime. Some limit of actual legislation (i.e. Data Protection, International Treaties on cyber-crime, Fraud prosecution laws), low speed of communication between Banks and LEAs, and the fraudster’s speed in taking advantage of weaknesses of the system leave the space for improvement. To improve the countermeasures that Banks and LEAs have deployed, this paper suggests the adoption of an InfoSharing Service between national banking system and Law Enforcement Agencies. This service uses a “hub-and-spoke” framework, where LEA is the hub and banks are the spokes. Target of the service is to shorten the time needed to communicate from Banking Fraud Managers to LEAs, and to share the relevant information on fraudster accounts in the whole banking industry. -

Public Interest Registry Chief Technology Officer
Public Interest Registry Appointment of Chief Technology Officer August 2021 Introduction At Public Interest Registry (PIR), the role of the In preparation for this roadmap, our team is Chief Technology Officer is critical in positioning currently addressing the many operational needs .ORG as a leading-edge TLD in technical of our internal IT systems. This includes areas. We are looking for a seasoned leader implementing security review recommendations, executing a plan to shift as much into the cloud as with excellent experience in and understanding possible and integrate the many cloud services to of both the domain name industry and modern which we subscribe, and reviewing our provisioning IT in general. processes for new systems, tools and apps. PIR has a Data Analytics department that has developed and is executing on a roadmap to bring Our core registry system is outsourced to Afilias, machine learning and data science skills to our oneof the world leaders in registry systems. Your organization and promote data-driven decision role will be to represent PIR in that relationship as making. The team is growing and currently consists our technical expert and ensure that future registry of a Senior Director of Data Analytics, Data Scientist, system enhancements align with our strategy. The Data Engineer, and BI Specialist. This team works greatest opportunities lie in areas such as technical closely with our business operations teams and you research and data analytics. Information security will provide support for this area and serve as an remains a high level priority within PIR with direct advocate for continuing to mature our data board oversight. -

Registry Operator's MONTHLY REPORT
Registry Operator’s MONTHLY REPORT September 2006 Prepared: October 12, 2006 VeriSign Information Services 21345 Ridgetop Circle Dulles, VA 20166-6503 VeriSign Registry Operator’s Monthly Report September 2006 As required by the ICANN/VeriSign Registry Agreements (Section 8 for .com; Section 3.1(c)(iv) for .net), this report provides an overview of VeriSign Registry activity through the end of the reporting month. The information is primarily presented in table and chart format with text explanations as deemed necessary. The information is provided to satisfy requirements listed in Appendix T of the .com Registry Agreement and Appendix 4 of the .net Registry Agreement. Pursuant to the agreements, “…items 5 - 12 shall be kept confidential by ICANN until three months after the end of the month to which the report relates.". It has been agreed by ICANN that any additional information required under the .net Registry Agreement, Appendix 4, Item 8 will be provided on a quarterly basis until further notice. Information is organized as follows: 1. Accredited Registrar Status................................................................................................................. 3 Table 1 – Accredited Registrar Status – September 2006 ................................................3 2. Service Level Agreement Performance............................................................................................... 3 Table 2 – Service Level Agreement Performance – September 2006..............................3 3. TLD Zone File Access Activity