Intellectual Property on the Internet: a Survey of Issues
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Internet Economy 25 Years After .Com
THE INTERNET ECONOMY 25 YEARS AFTER .COM TRANSFORMING COMMERCE & LIFE March 2010 25Robert D. Atkinson, Stephen J. Ezell, Scott M. Andes, Daniel D. Castro, and Richard Bennett THE INTERNET ECONOMY 25 YEARS AFTER .COM TRANSFORMING COMMERCE & LIFE March 2010 Robert D. Atkinson, Stephen J. Ezell, Scott M. Andes, Daniel D. Castro, and Richard Bennett The Information Technology & Innovation Foundation I Ac KNOW L EDGEMEN T S The authors would like to thank the following individuals for providing input to the report: Monique Martineau, Lisa Mendelow, and Stephen Norton. Any errors or omissions are the authors’ alone. ABOUT THE AUTHORS Dr. Robert D. Atkinson is President of the Information Technology and Innovation Foundation. Stephen J. Ezell is a Senior Analyst at the Information Technology and Innovation Foundation. Scott M. Andes is a Research Analyst at the Information Technology and Innovation Foundation. Daniel D. Castro is a Senior Analyst at the Information Technology and Innovation Foundation. Richard Bennett is a Research Fellow at the Information Technology and Innovation Foundation. ABOUT THE INFORMATION TECHNOLOGY AND INNOVATION FOUNDATION The Information Technology and Innovation Foundation (ITIF) is a Washington, DC-based think tank at the cutting edge of designing innovation policies and exploring how advances in technology will create new economic opportunities to improve the quality of life. Non-profit, and non-partisan, we offer pragmatic ideas that break free of economic philosophies born in eras long before the first punch card computer and well before the rise of modern China and pervasive globalization. ITIF, founded in 2006, is dedicated to conceiving and promoting the new ways of thinking about technology-driven productivity, competitiveness, and globalization that the 21st century demands. -

Content Regulation in the Digital
Content Regulation in the Digital Age Submission to the United Nations Special Rapporteur on the Right to Freedom of Opinion and Expression by the Association for Progressive Communications (APC) February 2018 Introduction 1 I. Company compliance with State laws 2 Terrorism-related and extremist content 3 False news, disinformation and propaganda 4 The “right to be forgotten” framework? 7 How should companies respond to State content regulation laws and measures that may be inconsistent with international human rights standards? 8 II. Other State Requests 9 State requests based on platform terms of service (ToS) and “shadow” requests 9 Non-transparent agreements with companies 10 III. Global removals 11 IV. Individuals at risk 12 V. Content regulation processes 15 VI. Bias and non-discrimination 16 VII. Appeals and remedies 17 VIII. Automation and content moderation 17 IX. Transparency 18 X. General recommendations from APC 19 Introduction The Association for Progressive Communications (APC) is an international network and non- profit organisation founded in 1990 that works to help ensure everyone has affordable access to a free and open internet to improve lives, realise human rights and create a more just world. We welcome this topic because it is current and integral to our work. On the one hand there is a lot of ‘noise’ in the mainstream media about so-called “fake news” and what appears to be a fairly rushed response from platforms consisting of increasing in-house regulation of content. On the other hand, human rights defenders and activists we work with express concern that 1 platforms are removing some of their content in a manner that suggests political bias and reinforcing of societal discrimination. -

To E-Commerce EC4E Ch 01 WA 11-23.Qxd 12/10/2007 5:16 PM Page 2
EC4E_Ch_01_WA_11-23.qxd 12/10/2007 5:16 PM Page 1 PART 1 CHAPTER 1 The Revolution Is Just Beginning CHAPTER 2 E-commerce Business Models and Concepts Introduction to E-commerce EC4E_Ch_01_WA_11-23.qxd 12/10/2007 5:16 PM Page 2 CHAPTER11 The Revolution Is Just Beginning LEARNING OBJECTIVES After reading this chapter, you will be able to: ■ Define e-commerce and describe how it differs from e-business. ■ Identify and describe the unique features of e-commerce technology and discuss their business significance. ■ Recognize and describe Web 2.0 applications. ■ Describe the major types of e-commerce. ■ Discuss the origins and growth of e-commerce. ■ Understand the evolution of e-commerce from its early years to today. ■ Identify the factors that will define the future of e-commerce. ■ Describe the major themes underlying the study of e-commerce. ■ Identify the major academic disciplines contributing to e-commerce. EC4E_Ch_01_WA_11-23.qxd 12/10/2007 5:16 PM Page 3 MySpace and Facebook: It’s All About You ow many people watched the final episode of the most popular American Htelevision show in history, the Sopranos? Answer: about 12 million (out of a total television audience size of 111 million). Only once in American history has a television show drawn more simultaneous viewers—13 million for NBC’s “America’s Got Talent” premiere in 2006. How many people visit MySpace each month? About 70 million. There are now more than 100 million personal profiles on MySpace. Almost 40 million visit MySpace’s closest social network rival, Facebook, each month. -

LACTLD REPORT the Latin American and Caribbean Cctld Publication
ISSN: 2301-1025 2nd year, 3rd edition twitter.com/lactld facebook.com/LACTLD LACTLD REPORT The Latin American and Caribbean ccTLD publication ANOTHER YEAR OF GROWTH AND CHANGES The Internet is constantly evolving. So are its challenges. The opportunities for development, participation and representation of stakeholders in the region encourage us to face 2014 with high expectations. IETF, by two regional technical experts Address: Rbla Rep. de México 6125, CP 11400, Security: personal data protection in Latin America Montevideo, Uruguay Tel.: + 598 2604 2222* (General Contact) Email: [email protected] www.lactld.org Enhanced cooperation and Internet governance EDITORIAL STAFF CONTINUED COLLABORATION: LACTLD Report LACTLD REPORT FIRST ANNIVERSARY 3rd edition 2nd year, 2013 Dear Readers, Board of Directors Eduardo Santoyo Another year ends – with plenty Luis Arancibia of debates, discussions and Víctor Abboud joint efforts to stimulate the Clara Collado ccTLD growth, both within and Frederico Neves outside the region of Latin America and the Caribbean. In Editorial Board Eduardo Santoyo this letter I would like to thank Luis Arancibia you all for your hard work and Clara Collado also invite you to continue Carolina Aguerre sharing the rewarding task of promoting Registry cooperation General Coordination and development during 2014. Marilina Esquivel The third issue of the LACTLD Report contains various articles and piece of news. A relevant announcement Editorial assistant is that the publication is now catalogued under the ISSN system, which will Sofía Zerbino enable to index and reference globally. In terms of the information, there is Art & Design information about ICANN’s new Engagement Center in Latin America and the Frida Caribbean, which opened in Montevideo, Uruguay and it aims to increase the representation of diverse stakeholders within the scope of this organization. -

Claiming and Reclaiming the Digital World As a Public Space
Claiming and Reclaiming the Digital World as a Public Space Experiences and insights from feminists in the Middle East and North Africa www.oxfam.org OXFAM DISCUSSION PAPER – NOVEMBER 2020 This paper seeks to highlight the experiences and aspirations of young women and feminist activists in the MENA region around digital spaces, safety and rights. It explores individual women’s experiences engaging with the digital world, the opportunities and challenges that women’s rights and feminist organizations find in these platforms, and the digital world as a space of resistance, despite restrictions on civic space. Drawing on interviews with feminist activists from the region, the paper sheds light on women’s online experiences and related offline risks, and illustrates patterns and behaviours that prevailed during the COVID-19 pandemic. © Oxfam International November 2020 This paper was written by Francesca El Asmar. Oxfam acknowledges the assistance of Hadeel Qazzaz, Manal Wardé, Neus Tirado Gual, Salma Jrad, Joane Cremesty, Suzan Al Ostaz, Fadi Touma and Mounia Semlali in its production, as well as the contributions of the interviewees who participated in the research process. It is part of a series of papers written to inform public debate on development and humanitarian policy issues. For further information on the issues raised in this paper please email [email protected] This publication is copyright but the text may be used free of charge for the purposes of advocacy, campaigning, education, and research, provided that the source is acknowledged in full. The copyright holder requests that all such use be registered with them for impact assessment purposes. -

The Social Economy
McKinsey Global Institute McKinsey Global Institute The social economy: Unlocking value and productivity through social technologies social through productivity and value Unlocking economy: The social July 2012 The social economy: Unlocking value and productivity through social technologies The McKinsey Global Institute The McKinsey Global Institute (MGI), the business and economics research arm of McKinsey & Company, was established in 1990 to develop a deeper understanding of the evolving global economy. Our goal is to provide leaders in the commercial, public, and social sectors with the facts and insights on which to base management and policy decisions. MGI research combines the disciplines of economics and management, employing the analytical tools of economics with the insights of business leaders. Our “micro-to-macro” methodology examines microeconomic industry trends to better understand the broad macroeconomic forces affecting business strategy and public policy. MGI’s in-depth reports have covered more than 20 countries and 30 industries. Current research focuses on six themes: productivity and growth; the evolution of global financial markets; the economic impact of technology and innovation; urbanization; the future of work; and natural resources. Recent reports have assessed job creation, resource productivity, cities of the future, and the impact of big data. MGI is led by three McKinsey & Company directors: Richard Dobbs, James Manyika, and Charles Roxburgh. Susan Lund serves as director of research. Project teams are led by a group of senior fellows and include consultants from McKinsey’s offices around the world. These teams draw on McKinsey’s global network of partners and industry and management experts. In addition, leading economists, including Nobel laureates, act as research advisers. -

Business Process Outsourcing Connecting with New Markets
Business Process Outsourcing Connecting with new markets Edition 2017/2018 KEY FACTS Official name: Inflation rate, 2016: The Republic of Moldova 6.4 % Autonomous Territorial Unit of Gagauzia (ATU) Unique tax of 7% for IT park residents Area: 1,848 km² Corporate tax: in Free Economic Zones: 12 % 6%, 0% Population: 162,000 inhabitants VAT: in Free Economic Zones: 20%, 8% 0% Language: Gagauzian (Turkic Language Family), Employment rate: Russian and Romanian are most 32% commonly spoken languages in Gagauzia The average gross monthly wage in IT sector:* Capital of ATU Gagauzia: 650 EUR Comrat (26,200 inhabitants) Currency: Moldovan Leu (MDL) *Source: www.statistica.md CONTENT Key Facts 1 Why bussiness process outsoursing to Gagauzia? 3 Bussines process outsourcing (BPO) and ICT 5 Telecommunications 8 Telephony 9 Internet 9 Incentives in ICT sector 11 Bussiness partners 12 Association of ICT companies 12 Invest in Moldova & Invest Gagauzia help you 13 WHY BUSINESS PROCESS OUTSOURCING TO GAGAUZIA? Human capital • Gagauzia is an autonomous region of the Republic of Moldova. The region has a population of 162,000 inhabitants. Comrat municipality is the administrative center of Autonomous Territorial Unit with 23,556 inhabitants. Over 80 percent of the total population speaks Gagauz language which is closely linked to Turkic language family. That enables Gagauz people to speak and understand Turkish and Azerbaijani languages. Russian and Romanian are second most spoken languages in Gagauzia. English is widely spoken and understood by the youth; • Work force – the employable population constitutes 104.8 thousand people, which make up for 64.8 % of total population; • Yearly, circa 750 students graduate from the State University of Comrat, two colleges and three vocational schools. -

Digitalization of Public Services in Moldova in the Covid-19 Era
UNITED NATIONS DEVELOPMENT PROGRAMME DIGITALIZATION OF PUBLIC SERVICES IN MOLDOVA IN THE COVID-19 ERA The Impact of COVID-19 It is now six months since the COVID-19 pandemic engulfed our world. It has now become clear that our lives are unlikely to return quickly, if ever, to our previous normality. The COVID-19 pandemic has exposed flaws and limitations in our existing systems and norms. Everybody has either witnessed or experienced large-scale lockdowns. And although the world is re-opening now, COVID-19 is still spreading around the world. Our societies will have to adapt to a “new normal” in practically everything we do. Public services are vital for people’s livelihoods. Everyday people need public services to help them access services, register for retraining programmes or receive social benefits. In this “new normal” the government should make long-term improvements to public services, with a focus on filling the gaps in infrastructure and designing personalized public services. Virtual communication and connectedness will not end with the end of the lockdown. Face-to-face communication will still be important in service provision. However, the government should gradually create the conditions when people will not feel a radical difference between virtual (digital) and physical delivery of public services. To achieve this, it is crucial for the Government to bring the spirit of human interaction and connectedness to digital public services. How do we combine all of this and make public services efficient, personalized, trustworthy, human and most importantly safe in the post-COVID era in Moldova? We attempt to address these questions in this brief. -

Multimedia, Internet, On-Line
Section IV: Multimedia, the Internet, and On-Line Services High-End Digital Video Applications Larry Amiot Electronic and Computing Technologies Division Argonne National Laboratory The emphasis of this paper is on the high-end applications Internet and Intranet that are driving digital video. The research with which I am involved at Argonne National Laboratory is not done on dig- The packet video networks which currently support many ital video per se, but rather on how the research applications applications such as file transfer, Mbone video (talking at the laboratory drive its requirements for digital video. The heads), and World Wide Web browsing are limiting for high- paper will define what digital video is, what some of its com- quality video because of the low throughput one can achieve ponents are, and then discuss a few applications that are dri- via the Internet or intranets. Examples of national packet ving the development of these components. The focus will be switched networks developed in the last several years include on what digital video means to individuals in the research the National Science Foundation Network (NSFNet). The and education community. Department of Energy had its own network called ESNET, and the National Aeronautics and Space Administration The Digital Video Environment (NASA) had a network as well. Recently, the NSFNet was de- commissioned, and commercial interests are now starting to In 1996, a group of people from several universities in the fill that void. Research and education communities are find- Midwest and from Argonne formed a Video Working Group. ing, however, that this new commercial Internet is too re- This body tried to define the areas of digital video of impor- stricting and does not meet their throughput requirements; it tance to their institutions. -
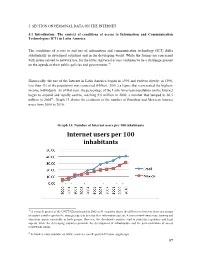
Internet Users Per 100 Inhabitants
5. SECTION ON PERSONAL DATA ON THE INTERNET 5.1 Introduction: The context of conditions of access to Information and Communication Technologies (ICT) in Latin America The conditions of access to and use of information and communication technology (ICT) differ substantially in developed countries and in the developing world. While the former are concerned with issues related to network use, for the latter, universal access continues to be a challenge present on the agenda of their public policies and governments.40 Historically, the use of the Internet in Latin America begins in 1996 and evolves slowly: in 1998, less than 1% of the population was connected (Hilbert, 2001,) a figure that represented the highest- income individuals. As of that year, the percentage of the Latin American population on the Internet began to expand and rapidly evolve, reaching 9.9 million in 2000, a number that jumped to 60.5 million in 200541. Graph 13 shows the evolution of the number of Brazilian and Mexican Internet users from 2000 to 2010: Graph 13: Number of Internet users per 100 inhabitants Internet users per 100 inhabitants 40 A research project of the UNCTAD performed in 2002 in 51 countries shows the differences between these two groups of countries with regard to the strategies used to develop their information society. A concern with awareness, training and education appear repeatedly in both groups. However, the developed countries tend to prioritize regulatory and legal aspects, while the developing countries prioritize the development of infrastructure and the universalization of access (UNCTAD, 2002). 41 E-Marketer data available at: www.emarketer.com/Reports/All?Latam_aug06.aspx. -

Intellectual Privacy and Censorship of the Internet
Georgetown University Law Center Scholarship @ GEORGETOWN LAW 1998 Intellectual Privacy and Censorship of the Internet Julie E. Cohen Georgetown University Law Center, [email protected] This paper can be downloaded free of charge from: https://scholarship.law.georgetown.edu/facpub/1963 8 Seton Hall Const. L.J. 693 (1997-1998) This open-access article is brought to you by the Georgetown Law Library. Posted with permission of the author. Follow this and additional works at: https://scholarship.law.georgetown.edu/facpub Part of the First Amendment Commons, and the Intellectual Property Law Commons 1998 INTERNET SYMPOSIUM INTELLECTUAL PRIVACY AND CENSORSHIP OF THE INTERNET ProfessorJulie E. Cohen Good morning. I would like to thank the Constitutional Law Journal for inviting me to be here today. I am not a First Amendment lawyer. I am not really a constitutional law- yer, so why am I here? I think that after having heard Dan Burk's presenta- tion, you should realize that intellectual property lawyers need to be First Amendment lawyers as well. You have all heard the aphorism that the Internet interprets censorship as a malfunction and routes around it.' You also may have heard that censorship on the Internet is a terrible thing; in particular, you may have heard this in the context of debates about pornography on the Inter- net or hate speech on the Internet. I would like to suggest to you today, how- ever, that the single most prevalent problem involving censorship on the Inter- net has to do with the protection of intellectual property. If you think about it, intellectual property protection, and particularly copy- right protection, is a form of censorship. -

The Right to Privacy in the Digital Age
The Right to Privacy in the Digital Age April 9, 2018 Dr. Keith Goldstein, Dr. Ohad Shem Tov, and Mr. Dan Prazeres Presented on behalf of Pirate Parties International Headquarters, a UN ECOSOC Consultative Member, for the Report of the High Commissioner for Human Rights Our Dystopian Present Living in modern society, we are profiled. We accept the necessity to hand over intimate details about ourselves to proper authorities and presume they will keep this information secure- only to be used under the most egregious cases with legal justifications. Parents provide governments with information about their children to obtain necessary services, such as health care. We reciprocate the forfeiture of our intimate details by accepting the fine print on every form we sign- or button we press. In doing so, we enable second-hand trading of our personal information, exponentially increasing the likelihood that our data will be utilized for illegitimate purposes. Often without our awareness or consent, detection devices track our movements, our preferences, and any information they are capable of mining from our digital existence. This data is used to manipulate us, rob from us, and engage in prejudice against us- at times legally. We are stalked by algorithms that profile all of us. This is not a dystopian outlook on the future or paranoia. This is present day reality, whereby we live in a data-driven society with ubiquitous corruption that enables a small number of individuals to transgress a destitute mass of phone and internet media users. In this paper we present a few examples from around the world of both violations of privacy and accomplishments to protect privacy in online environments.