Internet Governance and Regulations in Latin America
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CCIA Comments in ITU CWG-Internet OTT Open Consultation.Pdf
CCIA Response to the Open Consultation of the ITU Council Working Group on International Internet-related Public Policy Issues (CWG-Internet) on the “Public Policy considerations for OTTs” Summary. The Computer & Communications Industry Association welcomes this opportunity to present the views of the tech sector to the ITU’s Open Consultation of the CWG-Internet on the “Public Policy considerations for OTTs”.1 CCIA acknowledges the ITU’s expertise in the areas of international, technical standards development and spectrum coordination and its ambition to help improve access to ICTs to underserved communities worldwide. We remain supporters of the ITU’s important work within its current mandate and remit; however, we strongly oppose expanding the ITU’s work program to include Internet and content-related issues and Internet-enabled applications that are well beyond its mandate and core competencies. Furthermore, such an expansion would regrettably divert the ITU’s resources away from its globally-recognized core competencies. The Internet is an unparalleled engine of economic growth enabling commerce, social development and freedom of expression. Recent research notes the vast economic and societal benefits from Rich Interaction Applications (RIAs), a term that refers to applications that facilitate “rich interaction” such as photo/video sharing, money transferring, in-app gaming, location sharing, translation, and chat among individuals, groups and enterprises.2 Global GDP has increased US$5.6 trillion for every ten percent increase in the usage of RIAs across 164 countries over 16 years (2000 to 2015).3 However, these economic and societal benefits are at risk if RIAs are subjected to sweeping regulations. -

LACTLD REPORT the Latin American and Caribbean Cctld Publication
ISSN: 2301-1025 2nd year, 3rd edition twitter.com/lactld facebook.com/LACTLD LACTLD REPORT The Latin American and Caribbean ccTLD publication ANOTHER YEAR OF GROWTH AND CHANGES The Internet is constantly evolving. So are its challenges. The opportunities for development, participation and representation of stakeholders in the region encourage us to face 2014 with high expectations. IETF, by two regional technical experts Address: Rbla Rep. de México 6125, CP 11400, Security: personal data protection in Latin America Montevideo, Uruguay Tel.: + 598 2604 2222* (General Contact) Email: [email protected] www.lactld.org Enhanced cooperation and Internet governance EDITORIAL STAFF CONTINUED COLLABORATION: LACTLD Report LACTLD REPORT FIRST ANNIVERSARY 3rd edition 2nd year, 2013 Dear Readers, Board of Directors Eduardo Santoyo Another year ends – with plenty Luis Arancibia of debates, discussions and Víctor Abboud joint efforts to stimulate the Clara Collado ccTLD growth, both within and Frederico Neves outside the region of Latin America and the Caribbean. In Editorial Board Eduardo Santoyo this letter I would like to thank Luis Arancibia you all for your hard work and Clara Collado also invite you to continue Carolina Aguerre sharing the rewarding task of promoting Registry cooperation General Coordination and development during 2014. Marilina Esquivel The third issue of the LACTLD Report contains various articles and piece of news. A relevant announcement Editorial assistant is that the publication is now catalogued under the ISSN system, which will Sofía Zerbino enable to index and reference globally. In terms of the information, there is Art & Design information about ICANN’s new Engagement Center in Latin America and the Frida Caribbean, which opened in Montevideo, Uruguay and it aims to increase the representation of diverse stakeholders within the scope of this organization. -
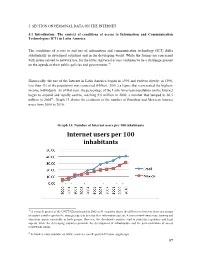
Internet Users Per 100 Inhabitants
5. SECTION ON PERSONAL DATA ON THE INTERNET 5.1 Introduction: The context of conditions of access to Information and Communication Technologies (ICT) in Latin America The conditions of access to and use of information and communication technology (ICT) differ substantially in developed countries and in the developing world. While the former are concerned with issues related to network use, for the latter, universal access continues to be a challenge present on the agenda of their public policies and governments.40 Historically, the use of the Internet in Latin America begins in 1996 and evolves slowly: in 1998, less than 1% of the population was connected (Hilbert, 2001,) a figure that represented the highest- income individuals. As of that year, the percentage of the Latin American population on the Internet began to expand and rapidly evolve, reaching 9.9 million in 2000, a number that jumped to 60.5 million in 200541. Graph 13 shows the evolution of the number of Brazilian and Mexican Internet users from 2000 to 2010: Graph 13: Number of Internet users per 100 inhabitants Internet users per 100 inhabitants 40 A research project of the UNCTAD performed in 2002 in 51 countries shows the differences between these two groups of countries with regard to the strategies used to develop their information society. A concern with awareness, training and education appear repeatedly in both groups. However, the developed countries tend to prioritize regulatory and legal aspects, while the developing countries prioritize the development of infrastructure and the universalization of access (UNCTAD, 2002). 41 E-Marketer data available at: www.emarketer.com/Reports/All?Latam_aug06.aspx. -

Viral Triggers
Viral Triggers Instant Messaging Ilia Mirkin [email protected] January 26, 2005 Instant Messaging ! Talk: Communications between terminals ! Zephyr: Developed at MIT; little use outside ! ICQ: First popular IM service ! AIM: At first for AOL members only, later free service to all, but with ads for non-AOL members ! Jabber: Open IM architecture, though similar to AIM in most respects ! MSN/Yahoo/etc: Proprietary but free services similar to AIM ! Rendezvous: Can be used for messaging in LANs ! Skype: Peer-to-peer application for both voice and text Talk ! Originally developed for Multics, in 1973 ! Became a standard UNIX command with 4.2BSD ! Further enhancements to connect terminals over a network, and later, to be able to connect more than 2 parties (Ytalk - 1990) ! Was popular amongst UNIX users since its existence, though no concrete usage statistics are available ! Has become marginalized by other IM systems that do not require people to be logged in on terminals Zephyr Developed at MIT under Project Athena Designed to run under Unix, there are few clients available, as well as few users outside universities Started in the 1980's, has not gained widespread acceptance. However it does provide various security enhancements, such as interoperability with Kerberos Protocol specifications available freely, open source clients ICQ (“I Seek You”) Created by Mirabilis, Inc., in 1996 First IM service to gain wide acceptance, mostly via member- driven advertising Used numbers to identify members (much like Compuserve) Allowed messages to be stored on server and delivered them when the target user would log on Overtaken in popularity by AIM, which allowed people to pick any username Currently accepts new users, but the service has become very similar to AIM, and uses the same servers AOL IM AOL bought up Mirabilis, and recreated ICQ as AIM Two protocols: OSCAR and TOC OSCAR included all the features of AIM, but was closed. -

Omnisense™ Analysis Help
Zephyr Technology OmniSense Analysis Help © 2016 Zephyr Technology OmniSense Help This is the printed version of the OmniSense Help file. Content has been optimised for screen display. In the printed version, page breaks may interrupt continuity. © 2016 Zephyr Technology All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or mechanical, including photocopying, recording, taping, or information storage and retrieval systems - without the written permission of the publisher. Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners. The publisher and the author make no claim to these trademarks. While every precaution has been taken in the preparation of this document, the publisher and the author assume no responsibility for errors or omissions, or for damages resulting from the use of information contained in this document or from the use of programs and source code that may accompany it. In no event shall the publisher and the author be liable for any loss of profit or any other commercial damage caused or alleged to have been caused directly or indirectly by this document. Printed: April 2016 4 Table of Contents Foreword 9 Section 1 Getting Started 10 1 Conta..c.t. .Z..e..p..h..y..r.................................................................................................................... 11 2 New F..e..a..t.u..r..e..s...................................................................................................................... 11 3 Using. .T..h..i.s.. .G..u..i.d..e.................................................................................................................. 16 Section 2 Overview 18 1 Toolb.a..r.. .B..u..t.t.o..n..s................................................................................................................... 20 2 Prefe.r.e..n..c..e..s........................................................................................................................ -

Forensic Artefacts Left by Pidgin Messenger 2.0
digital investigation 4 (2007) 138–145 available at www.sciencedirect.com journal homepage: www.elsevier.com/locate/diin Forensic artefacts left by Pidgin Messenger 2.0 Wouter S. van Dongen Fox-IT Forensic IT Experts, Olof Palmestraat 6, 2616 LM Delft, The Netherlands article info abstract Article history: Pidgin, formerly known as Gaim, is a multi-protocol instant messaging (IM) client that sup- Received 23 July 2007 ports communication on most of the popular IM networks. Pidgin is chiefly popular under Revised 23 November 2007 Linux, and is available for Windows, BSD and other UNIX versions. This article presents Accepted 21 January 2008 a number of traces that are left behind after the use of Pidgin on Linux, enabling digital in- vestigators to search for and interpret instant messaging activities, including online con- Keywords: versations and file transfers. Specifically, the contents and structures of user settings, log Pidgin files, contact files and the swap partition are discussed. In addition looking for such infor- Gaim mation in active files on a computer, forensic examiners can recover deleted items by Instant messenger searching a hard drive for file signatures and known file structures detailed in this article. Internet chat ª 2008 Elsevier Ltd. All rights reserved. Linux messenger MSN ICQ Yahoo! IRC 1. Introduction Gaim would become Pidgin, libgaim would become libpurple, and gaim-text would become finch. The name Pidgin was cho- This article is a continuation of the series of articles dealing sen as a reference to the term ‘Pidgin’, which describes com- with artefacts left by popular instant messaging clients. -
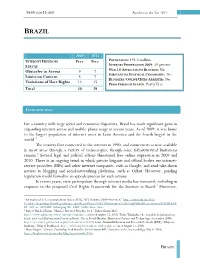
Freedom on the Net 2011 1 F H
REEDOM OUSE Freedom on the Net 2011 1 F H BRAZIL 2009 2011 INTERNET FREEDOM Free Free POPULATION: 193.3 million INTERNET PENETRATION 2009: 39 percent STATUS 0 Obstacles to Access 9 7 WEB 2.0 APPLICATIONS BLOCKED: No SUBSTANTIAL POLITICAL CENSORSHIP: No Limits on Content 8 7 BLOGGERS/ONLINE USERS ARRESTED: No Violations of User Rights 13 15 PRESS FREEDOM STATUS: Partly Free Total 30 29 INTRODUCTION For a country with large social and economic disparities, Brazil has made significant gains in expanding internet access and mobile-phone usage in recent years. As of 2009, it was home to the largest population of internet users in Latin America and the fourth largest in the world.1 The country first connected to the internet in 1990, and connectivity is now available in most areas through a variety of technologies, though some infrastructural limitations remain.2 Several legal and judicial actions threatened free online expression in 2009 and 2010. There is an ongoing trend in which private litigants and official bodies sue internet- service providers (ISPs) and other internet companies, such as Google, and send take-down notices to blogging and social-networking platforms, such as Orkut. However, pending legislation would formalize an appeals process for such actions. In recent years, civic participation through internet media has increased, including in 3 response to the proposed Civil Rights Framework for the Internet in Brazil. Moreover, 1 International Telecommunications Union (ITU), “ICT Statistics 2009—Internet,” http://www.itu.int/ITU- D/icteye/Reporting/ShowReportFrame.aspx?ReportName=/WTI/InformationTechnologyPublic&ReportFormat=HTML4.0& RP_intYear=2009&RP_intLanguageID=1&RP_bitLiveData=False. -

American Indian Health Commission for Washington State “Improving Indian Health Through Tribal-State Collaboration”
Administrations and Divisions: Home & Community Services (HCS), Residential Community Services (RCS), Behavioral Health Administration (BHA), Developmental Disabilities Administration (DDA), Division of Behavioral Health and Recovery (DBHR), Office of the Deaf & Hard of Hearing (ODHH May 12, 2020 from 9 a.m. – noon No In-Person Locations available. Please register for IPAC Subcommittee ALTSA/BHA/DDA on May 12, 2020 starting at 9:00 AM PST at: https://attendee.gotowebinar.com/register/7982740694599152141 After registering, you will receive a confirmation email containing information about joining the webinar. Welcome and Introductions – Office of Indian Policy Dr. Marie Natrall/Brenda Francis-Thomas • Welcoming • Invocation • Announcements • Roll Call Aging and Long-Term Services Administration – Marietta Bobba; Ann Dahl • Covid-19 check-in and sharing- Alec Graham, ALTSA HCS; • Tribal Initiative Updates o Squaxin Island Tribe o Nisqually Tribe o Makah Tribe o Lummi Nation o American Indian Community Center • Aging & Disability Resource Center Outreach – American Indian Health Commission • Health Homes • Adult Protective Services Check-In – APS staff • Traumatic Brain Injury Council opening Developmental Disabilities Administration – Justin Chan • 2020 Community Summit Update • DDA clients with tribal affiliation (self-identified) and receiving DDA services • Community residential providers are contracted statewide with the DDA to provide residential services to adult clients. Services include: o Supported Living o State Operated Living Alternatives o Group Training Homes or Group Homes o Alternative Living o Companion Homes To receive services an individual must be: o At least 18 year of age o Eligible and enrolled in DDA services and Medicaid o On or approved for the CORE Waiver or the Community Protection Waiver o Assessed by DDA as needing services in a supported living setting • Group Training Homes and Group Homes: Community-based, residential facilities who typically serve 5-12 adults. -

Zephyr: Hiding Metadata in a Messaging System
Zephyr: Hiding Metadata in a Messaging System Friedrich Doku Irondale High School Email: [email protected] Abstract—Private messaging over internet related services is To communicate with other users Zephyr utilizes identity- difficult to implement. Regular end-to-end encryption messaging based encryption. Users only need to know the email address systems are prone to man in the middle attacks and only hide of the other user they wish to talk to. The public key of messages but not the identity of its users. For example, WhatsApp offers a strong privacy guarantee but does not hide much the recipient is computed with the recipients email address Metadata because it uses end-to-end encryption. Other messaging and a master public key [3]. Identity-based encryption allows systems such as Skype can be monitored by government agencies Zephyr to compute a recipient’s public key without revealing and have backdoors implemented into its software. the recipient’s identity. Zephyr is an anonymous messaging system that protects the Zephyr is a synchronous algorithm and at the end of privacy of message contents and message metadata. Users that every round of exchanging messages the users messages are use Zephyr do not reveal who they are talking to or the contents of their messages. The goal of Zephyr is to decrease the amount uploaded to mailbox servers. These mailboxes can be shared of information being sent by the user and hide as much metadata by many different users. Each user will download all the as possible. contents of her mailbox and attempt to decrypt every single message until the intended message is found. -

RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.1 | June 2016 UFED LOGICAL ANALYZER
NOW SUPPORTING 19,776 DEVICE PROFILES +1,729 APP VERSIONS UFED TOUCH, UFED 4PC, RELEASE NOTES UFED PHYSICAL ANALYZER, Version 5.1 | June 2016 UFED LOGICAL ANALYZER HIGHLIGHTS Known for its breakthroughs in mobile data technology, Cellebrite is the industry’s leader – delivering comprehensive and innovative solutions for mobile forensics. Staying true to our DEVICE SUPPORT vision, UFED 5.1 introduces unique and exclusive capabilities, ◼ Cellebrite introduces physical extraction while bypassing providing unmatched access to case-critical evidence. user lock for 22 Samsung Galaxy devices including Galaxy S6, S6 Edge and Note 5 – with forensic recovery partition. Cellebrite introduces physical extraction ◼ A unique lock-bypassing method that allows physical while bypassing user lock for Samsung extraction of more than 140 LG models, including 22 Galaxy S6, S6 Edge and Note 5. previously-unsupported models, such as the MS330 and VS880. This method additionally allows the removal and restoration of the user screen lock. EXCLUSIVE - ONLY AT CELLEBRITE: ◼ A unique user screen lock removal method supporting A unique lock-bypassing method that 137 Samsung device (for some devices, there is more allows physical extraction of more than than 1 method).* 140 LG models, including 22 previously- ◼ First in Industry – Physical extraction while bypassing unsupported models, such as the MS330 lock and decoding support for 19 Huawei devices. and VS880. ◼ A unique user screen lock removal method supporting 17 selected LG devices, including the G5. A user screen lock removal method ◼ Cellebrite introduces physical extraction while bypassing supporting 137 Samsung devices. user lock as well as decoding support for 3 Nokia 105 devices: RM-1133, RM-1134 and RM-1135. -

Download File
INTERNET FOR ALL Proceedings of the Third Internet Governance Forum Hyderabad, India 3-6 December 2008 Edited by Don MacLean General Table of Contents Message by Sha Zukang, Under-Secretary-General, United Nations Department of Economic and Social Affairs (UNDESA) ……………………..i Introduction……………………………………………………………...……….ii Preface ......................................................................................................... 1 Setting the Scene ....................................................................................... 5 Opening Ceremony, 3 December 2008.....................................................6 Opening Session, 3 December 2008.......................................................16 Part 1 – Reaching the Next Billion.............................................................. 34 Chairman’s Summary of the Main Sessions..........................................35 Panel Discussion on Realizing a Multilingual Internet .........................39 Panel Discussion on Access...................................................................50 Open Dialogue on Reaching the Next Billion ........................................67 Reports of Workshops, Best Practice Forums, Open Forums and Dynamic Coalitions ..................................................................................84 Part 2 – Promoting Cyber-security and Trust ........................................... 117 Chairman’s Summary of Main Sessions ..............................................118 Panel Discussion on Dimensions of Cyber-security -

Law and Internet in Brazil
Special series Law and internet in Brazil Sérgio Branco Introduction This series is written by Sérgio Branco for canadian site DroitDu.net. In eight articles the director of ITS Rio aproaches diferent topics about Brazilian internet law, from the removal of contents on Youtube to questions regarding the “right to be forgotten” and net neutrality. The texts are translated to portuguese and published in ITS FEED, the content channel of Instituto de Tecnologia e Sociedade do Rio. Summary How a top model helped to regulate Brazilian Internet 04 Is it possible to crowdsource a law? 07 What are you liable for? 11 Why Brazil Needs a New Copyright Law 15 Nine Questions Regarding “the Right to Be Forgotten” 20 Net Neutrality: You Love it, even if you don’t Really Know what it is 25 Brazilian Internet is Partly Free 30 The Futures of the Internet 34 Special Series: Law and Internet in Brazil How a top model helped to regulate In 2006, Brazilian top model and tv presenter Brazilian Internet Daniella Cicarelli was spending some time with her boyfriend on a beach at Cadiz, south of Spain. On a sunny day and a public beach, with many sunbathers around the couple, they ended performing some intimate moments inside the sea. The event was recorded in details and soon after it was everywhere on the internet. The interest in Daniella Cicarelli was not surprising. In the year before, she got married to Ronaldo, aka Ronaldo Fenômeno, one of most famous Brazilian soccer players in the world. By that time, he played for Real Madrid, and she was a famous model.