Domain Time II Configuration Settings Using the Utilities About Settings (.Reg) Files on This Page
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
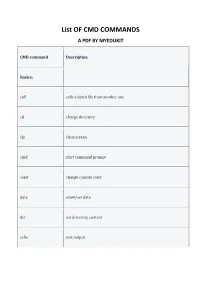
List of CMD COMMANDS a PDF by MYEDUKIT
List OF CMD COMMANDS A PDF BY MYEDUKIT CMD command Description Basics: call calls a batch file from another one cd change directory cls clear screen cmd start command prompt color change console color date show/set date dir list directory content echo text output exit exits the command prompt or a batch file find find files hostname display host name pause pauses the execution of a batch file and shows a message runas start a program as another user shutdown shutdown the computer sort sort the screen output start start an own window to execute a program or command taskkill terminate a process or an application tasklist display applications and related tasks time display/edit the system time timeout wait any time title set title for prompt ver display operating system version w32tm setting time synchronisation/time server/time zone Network: ftp transfer files to an FTP server ftype display file type and mapping getmac display MAC address ipconfig display IP network settings netsh configure/control/display network components netstat display TCP/IP connections and status nslookup query the DNS pathping test the connection to a specific IP address ping pings the network route display network routing table, add static routes systeminfo displays computer-specific properties and configurations telnet establish a Telnet connection tftp transfer files to a TFTP server tracert trace routes similar to patchping Files: attrib display file attributes comp compare file contents compact display/change file compression copy / xcopy copy files diskcomp -

Prepare Customer Site Servers
Prepare Customer Site Servers • Prepare Customer Site Servers, on page 1 • Prepare Cisco UCS C-Series Customer Site Servers, on page 1 • Prepare HyperFlex M5 series Customer Site Servers, on page 3 • NTP and Time Synchronization, on page 4 • Global Catalog Requirements, on page 5 Prepare Customer Site Servers Perform all the procedures in this section on the Side A and the Side B servers. Prepare Cisco UCS C-Series Customer Site Servers Configure RAID for C240 M4SX The disk array configuration for the C240 M4SX is already set up to match what is required for Packaged CCE. Verify the settings as follows. Using Cisco Integrated Management Controller, check that the following settings are configured correctly: • Virtual Drive Info: RAID 5 with 5 (Physical Disks) * 4 (Virtual Drives/Datastores) • Stripe Size: 128KB • Write Policy: Write Back with BBU • Read Policy: Read Ahead Always For more information regarding RAID configuration for C240 M4SX in Configure RAID with GUI (UCS C-Series M4 Servers) section, see Cisco Collaboration on Virtual Servers Guide at: https://www.cisco.com/ c/en/us/td/docs/voice_ip_comm/cucm/virtual/CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers/ CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers_chapter_01.html#CUCM_TK_C2DC4F2D_ 00. Prepare Customer Site Servers 1 Prepare Customer Site Servers Run the RAID Config Validator Utility Run the RAID Config Validator Utility After you set up RAID configuration and add the datastores, run the RAID Config Validator utility to ensure that your datastore configuration is correct. Before you begin To run the utility, Java 7 (any update) must be installed. Java 8 and later releases are not supported. -

Deployment Strategy
System Management Best Practices Bryan S Owen PE Copyright c 2004 OSIsoft Inc. All rights reserved. Richness & Reliability “Value Coefficients” • Quality – Across operations and data systems • Quantity – Across business needs and over time • Utilization – Across enterprise and just in time It all Starts with Great Software …and the Right Architecture • Visualization Tools • Availability • Reliability • Security Integrated Data Collection Proven: Cutting Edge: Integrated Interface Embedded Historian Embedded PI Historian • Continuous Historian for DeltaV Application Station http://www.easydeltav.com/pd/PDS_ApplicationStation.pdf • “56SAM” Historian for Allen-Bradley ControlLogix www.oldi.com • “Promoted” Interface Node • Also visit: www.echohistorian.com Fault Tolerant vs Redundant Incident Tolerant Redundant Environment Fault JJ JJJ Hardware Fault JJJ JJ Software Fault K J Administrative Error JK JJ Scheduled Down K JJJ “Smile” Points: 15/30 22/30 Redundant Architecture • Reliability – Build from the Data Up • Availability – Build from the Users Down You decide what comes first! Redundant Data Collection Dual Gateways Interface Node Failover Redundant Data Service Dual PI Servers Dual PI Clients Redundant Architecture No single point of failure sounds great, what’s the catch? • Interface Support • History Recovery • Gap Filling • Client Impact • Fugitive Data Fugitive Data Capture Essential for rich content but… 1% of the data causes 99% perspiration! • Manual Entry Systems • Custom Applications • Isolated Point to Point Links Solution: -

Microsoft Windows Server 2019 Version 1809 Hyper-V
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

Arm Arhitektura Napreduje – No Postoje Izazovi
ARM ARHITEKTURA NAPREDUJE – NO POSTOJE IZAZOVI SAŽETAK Procesori ARM ISA arhitekture ne koriste se više "samo" za mobitele i tablete, nego i za serverska računala (pa i superračunala), te laptop / desktop računala. I Apple je kod Macintosh računala prešao sa Intel arhitekture na ARM arhitekturu. Veliki izazov kod tog prelaska bio je - kako omogućiti da se programski kod pisan za Intelovu ISA arhitekturu, izvršava na procesoru M1 koji ima ARM arhitekturu. Općenito, želja je da se programi pisani za jednu ISA arhitekturu mogu sa što manje napora izvršavati na računalima koja imaju drugačiju ISA arhitekturu. Problem je u tome što različite ISA arhitekture mogu imati dosta različite memorijske modele. ABSTRACT ARM ISA processors are no longer used "only" for mobile phones and tablets, but also for server computers (even supercomputers) and laptops / desktops. Apple has also switched from Intel to ARM on Macintosh computers. The big challenge in that transition was - how to enable program code written for Intel's ISA architecture to run on an M1 processor that has an ARM architecture. In general, the desire is that programs written for one ISA architecture can be executed with as little effort as possible on computers that have a different ISA architecture. The problem is that different ISA architectures can have quite different memory models. 1. UVOD Procesori ARM ISA arhitekture ne koriste se više "samo" za mobitele i tablete, nego i za serverska računala (pa i superračunala), te laptop/desktop računala. Koriste se i u industriji, u proizvodnim procesima, a i kao ugradbeni čipovi u ostale proizvode, npr. za ugradnju u IOT uređaje i u vozila (posebno autonomna vozila). -

Operational and Administrative Guidance
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

Installation and Upgrade General Checklist Report
VeritasTM Services and Operations Readiness Tools Installation and Upgrade Checklist Report for InfoScale Storage 7.3.1, Solaris 11, SPARC Index Back to top Important Notes Components for InfoScale System requirements Product features Product documentation Patches for InfoScale Storage and Platform Platform configuration Host bus adapter (HBA) parameters and switch parameters Operations Manager Array Support Libraries (ASLs) Additional tasks to consider Important Notes Back to top Note: You have not selected the latest product version. Consider installing or upgrading to the latest version; otherwise, you may encounter issues that have already been fixed. To run a new report for the latest product version, select it from the Veritas product drop-down list. Array Support Libraries (ASLs) When installing Veritas products, please be aware that ASLs updates are not included in the patches update bundle. Please go to the Array Support Libraries (ASLs) to get the latest updates for your disk arrays. Components for InfoScale Back to top The InfoScale product you selected contains the following component(s). Dynamic Multi-Pathing Storage Foundation Storage Foundation Cluster File System Get more introduction of Veritas InfoScale. System requirements Back to top Required CPU number and memory: Required number of CPUs Required memory SF or SFHA N/A 2GB SFCFS or SFCFSHA 2 2GB 1 of 11 VeritasTM Services and Operations Readiness Tools Required disk space: Partitions Minimum space required Maximum space required Recommended space /opt 99 MB 1051 MB 134 MB /root 1 MB 30 MB 1 MB /usr 3 MB 237 MB 3 MB /var 1 MB 1 MB 1 MB Supported architectures: SPARC M5 series [1] SPARC M6 series [1] SPARC M7 series [1][2] SPARC S7 series [1] SPARC T3 series [1] SPARC T4 series [1] SPARC T5 series [1] SPARC T7 series [1][2] SPARC T8 series [1][2] SPARC64 X+ series [1] SPARC64 XII series [1] SPARC64-V series SPARC64-VI series SPARC64-VII/VII+ series SPARC64-X series [1] UltraSPARC II series UltraSPARC III series UltraSPARC IV series UltraSPARC T1 series [1] UltraSPARC T2/T2+ series [1] 1. -

Fujitsu's Vision for High Performance Computing
FujitsuFujitsu’’ss VisionVision forfor HighHigh PerformancePerformance ComputingComputing October 26, 2004 Yuji Oinaga Fujitsu Ltd. 1 CONTENTSCONTENTS HPC Policy and Concept Current HPC Platform HPC2500 IA-Cluster Major HPC customers Road Map Toward Peta-Scale Computing 2 FUJITSUFUJITSU HPCHPC PolicyPolicy ~ Developing & Providing Top Level Supercomputer ~ - High Computational Power - High Speed Interconnect - Reliability/Availability - Leading Edge Semiconductor Technology - Highly Reliable, HPC Featured Operating System & Middleware - Sophisticated Compilers and Development Tools 3 HistoryHistory ofof HPCHPC PlatformPlatform PRIMEPOWER HPC2500 VPP5000 Vector Parallel VPP300/700 IA32/IPF Cluster PRIMEPOWER VPP500 2000 Vector VP2000 AP3000 VP Series AP1000 F230-75APU Scalar 1980 1985 1990 1995 2000 2005 4 ConceptConcept ofof FujitsuFujitsu HPCHPC ProvideProvide thethe best/fastestbest/fastest platformplatform forfor eacheach applications.applications. -Scalar SMP : PRIMEPOWER, New Linux SMP -IA Cluster : PRIMERGY Cluster ProvideProvide thethe highhigh speedspeed interconnect.interconnect. -Crossbar : High Speed Optical Interconnect -Multi-Stage : Infiniband ProvideProvide HighHigh Operability/UsabilityOperability/Usability -Enhancement of Operability/Usability : Extended Partitioning, Dynamic Reconfiguration -Cluster Middleware : Total Cluster Control System ( Parallelnavi ) Shared Rapid File System ( SRFS ) 5 FujitsuFujitsu’’ss CurrentCurrent HPCHPC PlatformPlatform ~ Fujitsu is a leading edge company in HPC field ~ SPARC/Solaris -

Computer Architectures an Overview
Computer Architectures An Overview PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sat, 25 Feb 2012 22:35:32 UTC Contents Articles Microarchitecture 1 x86 7 PowerPC 23 IBM POWER 33 MIPS architecture 39 SPARC 57 ARM architecture 65 DEC Alpha 80 AlphaStation 92 AlphaServer 95 Very long instruction word 103 Instruction-level parallelism 107 Explicitly parallel instruction computing 108 References Article Sources and Contributors 111 Image Sources, Licenses and Contributors 113 Article Licenses License 114 Microarchitecture 1 Microarchitecture In computer engineering, microarchitecture (sometimes abbreviated to µarch or uarch), also called computer organization, is the way a given instruction set architecture (ISA) is implemented on a processor. A given ISA may be implemented with different microarchitectures.[1] Implementations might vary due to different goals of a given design or due to shifts in technology.[2] Computer architecture is the combination of microarchitecture and instruction set design. Relation to instruction set architecture The ISA is roughly the same as the programming model of a processor as seen by an assembly language programmer or compiler writer. The ISA includes the execution model, processor registers, address and data formats among other things. The Intel Core microarchitecture microarchitecture includes the constituent parts of the processor and how these interconnect and interoperate to implement the ISA. The microarchitecture of a machine is usually represented as (more or less detailed) diagrams that describe the interconnections of the various microarchitectural elements of the machine, which may be everything from single gates and registers, to complete arithmetic logic units (ALU)s and even larger elements. -

Microprocessor
MICROPROCESSOR www.MPRonline.com THE REPORTINSIDER’S GUIDE TO MICROPROCESSOR HARDWARE FUJITSU’S SPARC64 V IS REAL DEAL Fujitsu’s design differs from HAL’s version; faster than US III By Kevin Krewell {10/21/02-01} At Microprocessor Forum 2002, Fujitsu stepped forward to carry the banner for the fastest SPARC processor, surpassing Sun’s fastest UltraSPARC III on clock frequency and SPEC performance. In fact, at 1.35GHz, the Fujitsu processor has the highest clock frequency of any 64-bit server processor now in production. This by a Fujitsu acquisition, HAL Computer. At Micro- clock-speed advantage—plus large on-chip processor Forum 1999, Mike Shebanow, then vice caches; a fast system-crossbar switch; and a four- president and CTO of the HAL Computer Divi- issue, out-of-order core—translates into good sion of Fujitsu, proposed a complex and very wide SPEC benchmark performance for Fujitsu’s superscalar version of the SPARC64 V processor, SPARC64 V processor. The SPARC64 V is an evo- with an instruction trace cache, superspeculation, lutionary step in Fujitsu’s SPARC processor line and split L2 cache (see MPR 11/15/99-01,“Hal instead of the more-radical approach proposed three Makes Sparcs Fly”). Mike’s innovative chip never made years ago by HAL Computer at Microprocessor Forum it to market, but the trace-cache idea became a mainstream 1999. This latest version of Fujitsu’s SPARC processor fam- processor feature, shipping in Intel’s Pentium 4 microarchi- ily, revealed by Fujitsu’s director of Development Depart- tecture. The Pentium 4 also paralleled another of Mike’s ment (Processor Development Division) Aiichiro Inoue, is based on an enhanced version of the previous SPARC64 GP processor core, with larger caches and advanced semicon- L1I$ Decode & FP (16) L1D$ L2$ 128KB I-buffer Issue (4) SP (10) 128KB 2MB ductor process technology. -

EMC® Data Domain® Operating System 5.7 Administration Guide
EMC® Data Domain® Operating System Version 5.7 Administration Guide 302-002-091 REV. 02 Copyright © 2010-2016 EMC Corporation. All rights reserved. Published in the USA. Published March, 2016 EMC believes the information in this publication is accurate as of its publication date. The information is subject to change without notice. The information in this publication is provided as is. EMC Corporation makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose. Use, copying, and distribution of any EMC software described in this publication requires an applicable software license. EMC², EMC, and the EMC logo are registered trademarks or trademarks of EMC Corporation in the United States and other countries. All other trademarks used herein are the property of their respective owners. For the most up-to-date regulatory document for your product line, go to EMC Online Support (https://support.emc.com). EMC Corporation Hopkinton, Massachusetts 01748-9103 1-508-435-1000 In North America 1-866-464-7381 www.EMC.com 2 EMC Data Domain Operating System 5.7 Administration Guide CONTENTS Preface 13 Chapter 1 EMC Data Domain System Features and Integration 17 Revision history.............................................................................................18 EMC Data Domain system overview............................................................... 19 EMC Data Domain system features............................................................... -

Guía Sobre Tiflotecnología Y Tecnología De Apoyo Para Uso
Guía sobre Tiflotecnología y Tecnología de Apoyo para uso educativo (Última actualización: febrero 2016) Guía sobre Tiflotecnología y Tecnología de Apoyo para uso educativo ÍNDICE INTRODUCCIÓN ..................................................................................................................................... 6 CONOCIMIENTOS BÁSICOS .................................................................................................................. 11 DEFINICIONES.................................................................................................................................... 11 HARDWARE ....................................................................................................................................... 14 SOFTWARE ........................................................................................................................................ 18 OTROS DISPOSITIVOS ........................................................................................................................ 19 SISTEMA OPERATIVO (VERSIONES) WINDOWS, OS X, IOS, ANDROID, WINDOWS MOBILE, LINUX ........ 22 WINDOWS ......................................................................................................................................... 23 OS X ................................................................................................................................................... 25 LINUX ...............................................................................................................................................