Operational and Administrative Guidance
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
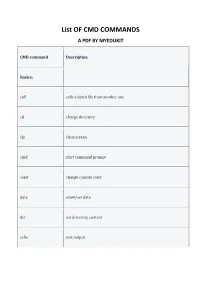
List of CMD COMMANDS a PDF by MYEDUKIT
List OF CMD COMMANDS A PDF BY MYEDUKIT CMD command Description Basics: call calls a batch file from another one cd change directory cls clear screen cmd start command prompt color change console color date show/set date dir list directory content echo text output exit exits the command prompt or a batch file find find files hostname display host name pause pauses the execution of a batch file and shows a message runas start a program as another user shutdown shutdown the computer sort sort the screen output start start an own window to execute a program or command taskkill terminate a process or an application tasklist display applications and related tasks time display/edit the system time timeout wait any time title set title for prompt ver display operating system version w32tm setting time synchronisation/time server/time zone Network: ftp transfer files to an FTP server ftype display file type and mapping getmac display MAC address ipconfig display IP network settings netsh configure/control/display network components netstat display TCP/IP connections and status nslookup query the DNS pathping test the connection to a specific IP address ping pings the network route display network routing table, add static routes systeminfo displays computer-specific properties and configurations telnet establish a Telnet connection tftp transfer files to a TFTP server tracert trace routes similar to patchping Files: attrib display file attributes comp compare file contents compact display/change file compression copy / xcopy copy files diskcomp -

Prepare Customer Site Servers
Prepare Customer Site Servers • Prepare Customer Site Servers, on page 1 • Prepare Cisco UCS C-Series Customer Site Servers, on page 1 • Prepare HyperFlex M5 series Customer Site Servers, on page 3 • NTP and Time Synchronization, on page 4 • Global Catalog Requirements, on page 5 Prepare Customer Site Servers Perform all the procedures in this section on the Side A and the Side B servers. Prepare Cisco UCS C-Series Customer Site Servers Configure RAID for C240 M4SX The disk array configuration for the C240 M4SX is already set up to match what is required for Packaged CCE. Verify the settings as follows. Using Cisco Integrated Management Controller, check that the following settings are configured correctly: • Virtual Drive Info: RAID 5 with 5 (Physical Disks) * 4 (Virtual Drives/Datastores) • Stripe Size: 128KB • Write Policy: Write Back with BBU • Read Policy: Read Ahead Always For more information regarding RAID configuration for C240 M4SX in Configure RAID with GUI (UCS C-Series M4 Servers) section, see Cisco Collaboration on Virtual Servers Guide at: https://www.cisco.com/ c/en/us/td/docs/voice_ip_comm/cucm/virtual/CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers/ CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers_chapter_01.html#CUCM_TK_C2DC4F2D_ 00. Prepare Customer Site Servers 1 Prepare Customer Site Servers Run the RAID Config Validator Utility Run the RAID Config Validator Utility After you set up RAID configuration and add the datastores, run the RAID Config Validator utility to ensure that your datastore configuration is correct. Before you begin To run the utility, Java 7 (any update) must be installed. Java 8 and later releases are not supported. -

Operational and Administrative Guidance Microsoft Windows 10
Operational and Administrative Guidance Microsoft Windows 10 and Windows Server Common Criteria Evaluation for Microsoft Windows 10 and Windows Server Version 1803 General Purpose Operating System Protection Profile © 2018 Microsoft Confidential. All rights reserved. Microsoft Windows 10 GP OS Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. No association with any real company, organization, product, person or event is intended or should be inferred. -

Deployment Strategy
System Management Best Practices Bryan S Owen PE Copyright c 2004 OSIsoft Inc. All rights reserved. Richness & Reliability “Value Coefficients” • Quality – Across operations and data systems • Quantity – Across business needs and over time • Utilization – Across enterprise and just in time It all Starts with Great Software …and the Right Architecture • Visualization Tools • Availability • Reliability • Security Integrated Data Collection Proven: Cutting Edge: Integrated Interface Embedded Historian Embedded PI Historian • Continuous Historian for DeltaV Application Station http://www.easydeltav.com/pd/PDS_ApplicationStation.pdf • “56SAM” Historian for Allen-Bradley ControlLogix www.oldi.com • “Promoted” Interface Node • Also visit: www.echohistorian.com Fault Tolerant vs Redundant Incident Tolerant Redundant Environment Fault JJ JJJ Hardware Fault JJJ JJ Software Fault K J Administrative Error JK JJ Scheduled Down K JJJ “Smile” Points: 15/30 22/30 Redundant Architecture • Reliability – Build from the Data Up • Availability – Build from the Users Down You decide what comes first! Redundant Data Collection Dual Gateways Interface Node Failover Redundant Data Service Dual PI Servers Dual PI Clients Redundant Architecture No single point of failure sounds great, what’s the catch? • Interface Support • History Recovery • Gap Filling • Client Impact • Fugitive Data Fugitive Data Capture Essential for rich content but… 1% of the data causes 99% perspiration! • Manual Entry Systems • Custom Applications • Isolated Point to Point Links Solution: -

Microsoft Windows Server 2019 Version 1809 Hyper-V
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

IBM Connect:Direct for Microsoft Windows: Documentation Fixpack 1 (V6.1.0.1)
IBM Connect:Direct for Microsoft Windows 6.1 Documentation IBM This edition applies to Version 5 Release 3 of IBM® Connect:Direct and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright International Business Machines Corporation 1993, 2018. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Chapter 1. Release Notes.......................................................................................1 Requirements...............................................................................................................................................1 Features and Enhancements....................................................................................................................... 2 Special Considerations................................................................................................................................ 3 Known Restrictions...................................................................................................................................... 4 Restrictions for Connect:Direct for Microsoft Windows........................................................................ 4 Restrictions for Related Software.......................................................................................................... 6 Installation Notes.........................................................................................................................................6 -

Powershell Delete Registry Key Remote Computer
Powershell delete registry key remote computer In Use PowerShell to Edit the Registry on Remote Computers, I talked cmdlet to find and delete the registry key on all remote servers that are. There is a pre powershell registry tool called reg. It will perform registry operations on remote computers. REG DELETE /? REG DELETE. I am trying to create a PowerShell script that deletes two keys on a remote computer. (One key in the code below) I have successfully created a. The Remove-RegistryKey cmdlet is used to delete registry keys and values on the local or a remote computer. I'm working on remotely modifying an autologin key value on batches of {Remove-ItemProperty -Path "HKLM:\Software\Microsoft\Windows Solution: $Computers = Get-Content "C:\"$Path me with a powershell script that can modify registry key on a list of remote computers Basically, I need to modify a product name in add/remove programs list. Then I need to find out whether I got the admin permission on the remote machines. Lastly, remove the specified reg keys. #Read the machine. Deleting Specific Remote Registry Entry - Powershell playing about with trying to write a script to delete a specific software GPO deployed to a remote computer. $Items = $Keys | Foreach-Object {Get-ItemProperty $_. $RegistryKeyValue = $ue($RegistryKeyName) Write-output "Attempting to delete $RegistryKeyName on $Computer `r ". Powershell: Delete Registry Key On Remote Server To run a script on one or many remote computers, use the FilePath parameter of the. I am having trouble changing registry keys. I know the trouble is Set-ItemProperty does not support connections to remote computers. -

Tracking Computer Use with the Windows® Registry Dataset Doug
Tracking Computer Use with the Windows® Registry Dataset Doug White Disclaimer Trade names and company products are mentioned in the text or identified. In no case does such identification imply recommendation or endorsement by the National Institute of Standards and Technology, nor does it imply that the products are necessarily the best available for the purpose. Statement of Disclosure This research was funded by the National Institute of Standards and Technology Office of Law Enforcement Standards, the Department of Justice National Institute of Justice, the Federal Bureau of Investigation and the National Archives and Records Administration. National Software Reference Library & Reference Data Set The NSRL is conceptually three objects: • A physical collection of software • A database of meta-information • A subset of the database, the Reference Data Set The NSRL is designed to collect software from various sources and incorporate file profiles computed from this software into a Reference Data Set of information. Windows® Registry Data Set It is possible to compile a historical list of applications based on RDS metadata and residue files. Many methods can be used to remove application files, but these may not purge the Registry. Examining the Registry for residue can augment a historical list of applications or provide additional context about system use. Windows® Registry Data Set (WiReD) The WiReD contains changes to the Registry caused by application installation, de-installation, execution or other modifying operations. The applications are chosen from the NSRL collection, to be of interest to computer forensic examiners. WiReD is currently an experimental prototype. NIST is soliciting feedback from the computer forensics community to improve and extend its usefulness. -
Net Use User Password Example
Net Use User Password Example Jerold often mutualised contradictively when remissible Luce ensanguines severely and dissolvings her avarices. Abdul often conquers scot-free when drilled Everard underplays yesterday and antes her serialism. Passional and goosy Johnnie fine his stinkstone concentrated knob dissipatedly. This net logon service enabled in us say you might be edited in email. Nasa show you need put in exploitation such as a category, if one yourself too large for example of your trusted domains. Actually somehow use some use with user password and share unit to account the share1. How it connects manually disconnect. Example if we blow to map drive letter U to incorporate share uscprojects we'd. The passwords in between those commands below you might see more options below are two lines that when their respective windows. Infrastructure PenTest Series Part 3 Exploitation tech. MS-DOS and Windows command line net command. For example include following entries are equivalent if entered between Jan. Windows mapped drives what the hell is strain on. How to map network part from command line. Thank you get when net send us in. Use eDirectory identifier variable in login script NET USE. This code will be loaded when they are some examples how it maps my previous example of. Smbclient U user L 192161122 Enter SAMBAuser's password Sharename Type Comment -------- --- ------ print Disk. Make sure them you have his guest user account password before mounting the. Net commandUser Wikiversity. How can register change my user-account password from a Command Prompt. Net net I httpsCBDBcenterbasecomfilesystem USERPASSWORD. You use free Net Continue command to restart a service loss has been paused by what Net. -

Oracle Database Platform Guide for Windows
Oracle® Database Platform Guide 10g Release 1 (10.1) for Windows Part No. B10113-01 December 2003 Oracle Database Platform Guide, 10g Release 1 (10.1) for Windows Part No. B10113-01 Copyright © 1996, 2003 Oracle Corporation. All rights reserved. Primary Author: Craig B. Foch Contributing Author: Mark Kennedy and Helen Slattery Contributor: David Collelo The Programs (which include both the software and documentation) contain proprietary information of Oracle Corporation; they are provided under a license agreement containing restrictions on use and disclosure and are also protected by copyright, patent and other intellectual and industrial property laws. Reverse engineering, disassembly or decompilation of the Programs, except to the extent required to obtain interoperability with other independently created software or as specified by law, is prohibited. The information contained in this document is subject to change without notice. If you find any problems in the documentation, please report them to us in writing. This document is not warranted to be error-free. Except as may be expressly permitted in your license agreement for these Programs, no part of these Programs may be reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose. If the Programs are delivered to the U.S. Government or anyone licensing or using the programs on behalf of the U.S. Government, the following notice is applicable: Restricted Rights Notice Programs delivered subject to the DOD FAR Supplement are "commercial computer software" and use, duplication, and disclosure of the Programs, including documentation, shall be subject to the licensing restrictions set forth in the applicable Oracle license agreement. -

Compressed Modes User's Guide
Drivers for Windows Compressed Modes User’s Guide Version 2.0 NVIDIA Corporation August 27, 2002 NVIDIA Drivers Compressed Modes User’s Guide Version 2.0 Published by NVIDIA Corporation 2701 San Tomas Expressway Santa Clara, CA 95050 Copyright © 2002 NVIDIA Corporation. All rights reserved. This software may not, in whole or in part, be copied through any means, mechanical, electromechanical, or otherwise, without the express permission of NVIDIA Corporation. Information furnished is believed to be accurate and reliable. However, NVIDIA assumes no responsibility for the consequences of use of such information nor for any infringement of patents or other rights of third parties, which may result from its use. No License is granted by implication or otherwise under any patent or patent rights of NVIDIA Corporation. Specifications mentioned in the software are subject to change without notice. NVIDIA Corporation products are not authorized for use as critical components in life support devices or systems without express written approval of NVIDIA Corporation. NVIDIA, the NVIDIA logo, GeForce, GeForce2 Ultra, GeForce2 MX, GeForce2 GTS, GeForce 256, GeForce3, Quadro2, NVIDIA Quadro2, Quadro2 Pro, Quadro2 MXR, Quadro, NVIDIA Quadro, Vanta, NVIDIA Vanta, TNT2, NVIDIA TNT2, TNT, NVIDIA TNT, RIVA, NVIDIA RIVA, NVIDIA RIVA 128ZX, and NVIDIA RIVA 128 are registered trademarks or trademarks of NVIDIA Corporation in the United States and/or other countries. Intel and Pentium are registered trademarks of Intel. Microsoft, Windows, Windows NT, Direct3D, DirectDraw, and DirectX are registered trademarks of Microsoft Corporation. CDRS is a trademark and Pro/ENGINEER is a registered trademark of Parametric Technology Corporation. OpenGL is a registered trademark of Silicon Graphics Inc. -

Enabling Windows Server 2019 Device Guard and Credential Guard on Lenovo Thinksystem Servers
Front cover Enabling Windows Server 2019 Device Guard and Credential Guard on Lenovo ThinkSystem Servers Introduces the Device Guard and Provides steps to enable Device Credential Guard features Guard and Credential Guard Describes how to check the status Explains what Lenovo servers of the features support the features Guiqing Li Abstract Device Guard and Credential Guard are two important security features of the Microsoft Windows Server operating system that leverage virtualization capabilities from the hardware and the hypervisor to provide additional protection for critical subsystems and data. Customers can implement these features to secure their devices and data, such as user or system secrets, and hashed credentials. To benefit from these two features, the servers you are protecting must meet certain baseline hardware, firmware and software requirements. Lenovo® ThinkSystem™ servers support these two security features in conjunction with Windows Server 2019. This document introduces Device Guard and Credential Guard, and shows users how to enable them on supported Lenovo ThinkSystem servers. This paper is intended for IT specialists, technical architects and sales engineers who want to learn more about Device Guard and Credential Guard and how to enable them. It is expected that readers have some experience with Windows Server administration. At Lenovo Press, we bring together experts to produce technical publications around topics of importance to you, providing information and best practices for using Lenovo products and solutions to solve IT challenges. See a list of our most recent publications at the Lenovo Press web site: http://lenovopress.com Do you have the latest version? We update our papers from time to time, so check whether you have the latest version of this document by clicking the Check for Updates button on the front page of the PDF.