Windows Powershell Best Practices Windows Powershell Best Practices
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

KDE 2.0 Development, Which Is Directly Supported
23 8911 CH18 10/16/00 1:44 PM Page 401 The KDevelop IDE: The CHAPTER Integrated Development Environment for KDE by Ralf Nolden 18 IN THIS CHAPTER • General Issues 402 • Creating KDE 2.0 Applications 409 • Getting Started with the KDE 2.0 API 413 • The Classbrowser and Your Project 416 • The File Viewers—The Windows to Your Project Files 419 • The KDevelop Debugger 421 • KDevelop 2.0—A Preview 425 23 8911 CH18 10/16/00 1:44 PM Page 402 Developer Tools and Support 402 PART IV Although developing applications under UNIX systems can be a lot of fun, until now the pro- grammer was lacking a comfortable environment that takes away the usual standard activities that have to be done over and over in the process of programming. The KDevelop IDE closes this gap and makes it a joy to work within a complete, integrated development environment, combining the use of the GNU standard development tools such as the g++ compiler and the gdb debugger with the advantages of a GUI-based environment that automates all standard actions and allows the developer to concentrate on the work of writing software instead of managing command-line tools. It also offers direct and quick access to source files and docu- mentation. KDevelop primarily aims to provide the best means to rapidly set up and write KDE software; it also supports extended features such as GUI designing and translation in con- junction with other tools available especially for KDE development. The KDevelop IDE itself is published under the GNU Public License (GPL), like KDE, and is therefore publicly avail- able at no cost—including its source code—and it may be used both for free and for commer- cial development. -

Desktop Migration and Administration Guide
Red Hat Enterprise Linux 7 Desktop Migration and Administration Guide GNOME 3 desktop migration planning, deployment, configuration, and administration in RHEL 7 Last Updated: 2021-05-05 Red Hat Enterprise Linux 7 Desktop Migration and Administration Guide GNOME 3 desktop migration planning, deployment, configuration, and administration in RHEL 7 Marie Doleželová Red Hat Customer Content Services [email protected] Petr Kovář Red Hat Customer Content Services [email protected] Jana Heves Red Hat Customer Content Services Legal Notice Copyright © 2018 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. -

1 Table of Contents List of Figures
Table of Contents List of Figures ..................................................................................................................... 4 List of Tables ...................................................................................................................... 5 Chapter 1: Introduction....................................................................................................... 6 1.1 Introduction....................................................................................................................6 1.2 Problem Statement .......................................................................................................12 1.3 Thesis Objective...........................................................................................................12 1.4 Thesis Organization.....................................................................................................14 Chapter 2: Intrusion Detection.......................................................................................... 15 2.1 Introduction..................................................................................................................15 2.2 What is an IDS .............................................................................................................15 2.2.1 The Basic Concepts of Intrusion Detection......................................................16 2.2.2 A Generic Intrusion-Detection System.............................................................17 2.2.3 Characteristics of -

NTFS • Windows Reinstallation – Bypass ACL • Administrators Privilege – Bypass Ownership
Windows Encrypting File System Motivation • Laptops are very integrated in enterprises… • Stolen/lost computers loaded with confidential/business data • Data Privacy Issues • Offline Access – Bypass NTFS • Windows reinstallation – Bypass ACL • Administrators privilege – Bypass Ownership www.winitor.com 01 March 2010 Windows Encrypting File System Mechanism • Principle • A random - unique - symmetric key encrypts the data • An asymmetric key encrypts the symmetric key used to encrypt the data • Combination of two algorithms • Use their strengths • Minimize their weaknesses • Results • Increased performance • Increased security Asymetric Symetric Data www.winitor.com 01 March 2010 Windows Encrypting File System Characteristics • Confortable • Applying encryption is just a matter of assigning a file attribute www.winitor.com 01 March 2010 Windows Encrypting File System Characteristics • Transparent • Integrated into the operating system • Transparent to (valid) users/applications Application Win32 Crypto Engine NTFS EFS &.[ßl}d.,*.c§4 $5%2=h#<.. www.winitor.com 01 March 2010 Windows Encrypting File System Characteristics • Flexible • Supported at different scopes • File, Directory, Drive (Vista?) • Files can be shared between any number of users • Files can be stored anywhere • local, remote, WebDav • Files can be offline • Secure • Encryption and Decryption occur in kernel mode • Keys are never paged • Usage of standardized cryptography services www.winitor.com 01 March 2010 Windows Encrypting File System Availibility • At the GUI, the availibility -

Attachment D to Adm. Memo No. 004 INSTRUCTIONS FOR
Attachment D to Adm. Memo No. 004 INSTRUCTIONS FOR FORMATTING A DISKETTE Formatting is the preparation of diskettes for storage of information. There are several different versions of the format command that can be used. The version that you use depends upon the type of diskette and the type of disk drive in which the diskette is being formatted. In order for us to be able to read the Tuition Grant diskettes you send, the diskettes should be properly formatted. Below is a table that identifies the more commonly used diskette types and disk drive specifications. The correct version of the format command will appear in the row for your diskette type and drive type. The format command uses the parameter “d:” to indicate the disk drive designation. For example, your 5 ¼ drive may be the “A:” drive. Instead of typing “FORMAT D:”, replace the drive designation with “A:” and type “FORMAT A:”. To verify that the disks were formatted correctly, perform the CHKDSK command on the newly formatted diskette. The format for the CHKDSK command is “CHKDSK d:”. When the command returns the disk information, compare it to the information in the fourth column of the table that corresponds to your diskette type and disk drive.. If the “total disk space” numbers are the same, the diskette is formatted correctly. DISK TYPE DRIVE TYPE FORMAT COMMAND SPACE INFO. 5 ¼” DSDD DSDD FORMAT d: 362,496 bytes total disk space 5 ¼” DSDD HD FORMAT d: /T:40 /N:9 362,496 bytes total disk space 5 ¼” HD DSDD Cannot be formatted 5 ¼” HD HD FORMAT d: 1,213,952 bytes total disk space 3 ½” DSDD DSDD FORMAT d: 730,112 bytes total disk space 3 ½” DSDD HD FORMAT d: /T:80 /N:9 730,112 bytes total disk space 3 ½” HD DSDD Cannot be formatted 3 ½” HD HD FORMAT d: 1,457,664 bytes total disk space 3 ½” DSHD FORMAT d: 1,457,664 bytes total disk space. -

Blackbaud CRM Security Guide
Security Guide 11/10/2014 Blackbaud Direct Marketing 4.0 Security UK ©2014 Blackbaud, Inc. This publication, or any part thereof, may not be reproduced or transmitted in any form or by any means, electronic, or mechanical, including photocopying, recording, storage in an information retrieval system, or oth- erwise, without the prior written permission of Blackbaud, Inc. The information in this manual has been carefully checked and is believed to be accurate. Blackbaud, Inc., assumes no responsibility for any inaccuracies, errors, or omissions in this manual. In no event will Blackbaud, Inc., be liable for direct, indirect, special, incidental, or consequential damages resulting from any defect or omission in this manual, even if advised of the possibility of damages. In the interest of continuing product development, Blackbaud, Inc., reserves the right to make improvements in this manual and the products it describes at any time, without notice or obligation. All Blackbaud product names appearing herein are trademarks or registered trademarks of Blackbaud, Inc. All other products and company names mentioned herein are trademarks of their respective holder. Security-2014 Contents CONTENTS I SECURITY 1 Fundamentals of Security 1 APPLICATION USERS 3 Search for Users 3 Application User Records 4 Add an Application User 4 Edit Users 5 Delete Users 6 Grant/Revoke Users Administrator Rights 6 Run the Program as a Selected User 6 Organisational Unit Record 7 Application Users Page 8 Manage System Roles of an Application User 8 Add System Roles -

Powershell Scripting Language Course Proposal for Tallinn University of Technology
TALLINN UNIVERSITY OF TECHNOLOGY School of Information Technologies Riivo Kiljak 178071IABM POWERSHELL SCRIPTING LANGUAGE COURSE PROPOSAL FOR TALLINN UNIVERSITY OF TECHNOLOGY Master’s thesis Supervisor: Siim Vene MSc Tallinn 2019 TALLINNA TEHNIKAULIKOOL¨ Infotehnoloogia teaduskond Riivo Kiljak 178071IABM POWERSHELLI SKRIPTIMISKEELE KURSUSE ETTEPANEK TALLINNA TEHNIKAULIKOOLILE¨ Magistrito¨o¨ Juhendaja: Siim Vene MSc Tallinn 2019 Author’s Declaration of Originality I hereby certify that I am the sole author of this thesis. All the used materials, references to the literature and the work of others have been referred to. This thesis has not been presented for examination anywhere else. Author: Riivo Kiljak 07.05.2019 3 Abstract In the thesis, a recommendation is made to establish a new course at TalTech. The course is intended to teach the PowerShell scripting language to students, most importantly in the IT Systems Administration programme. Course material is proposed in the form of lecture slides, home assignments and knowledge tests. All three of which are available in the appendices of the paper. Design science is used to pass iterations of improving the content prior the the paper publishing. Academic literature is analysed to determine the included and excluded topics and the teaching methodology. More- over, input is acquired from scrutinising public information on Microsoft’s official PowerShell courses and interviewing subject matter experts who use PowerShell at local companies. The course material is provided written in LATEX which means that it can be conveniently modified, version controlled and distributed in the PDF format. Although the proposed course is seen as an online course hosted on Moodle, argumentation is made suggesting a combination with classroom seminars is likely to result in better learning outcomes at the cost of scalability. -

Dynamics NAV2013 Large Scale Hosting on Windows Azure
Microsoft Dynamics NAV Large scale hosting on 2013 R2 Windows Azure Whitepaper April 2014 Contents Introduction 4 Assumptions 4 Who is the audience of this whitepaper? 4 Windows Azure components that are needed to deploy a scalable Microsoft Dynamics NAV 2013 R2 with high availability 6 What is Windows Azure? 6 The Windows Azure SLA 6 The Windows Azure Cloud Service 6 Port-forwarding endpoints 6 Load-balancing endpoints 7 Availability sets 8 Scale 8 How to deploy Microsoft Dynamics NAV 2013 R2 for multitenancy 9 Deployment scripts on the product media 9 Certificates and SSL 9 URLs 10 Load Balancing Microsoft Dynamics NAV 11 Adding/Removing Tenants 15 Adding/Removing Microsoft Dynamics NAV servers 15 ClickOnce deployment of the Microsoft Dynamics NAV Windows client 16 Application code considerations 17 Upgrade 18 Backup 19 Monitoring 19 How to deploy SQL Server with high availability and what is supported by Microsoft Dynamics NAV 2013 R2 21 SQL Server Always-On Availability Groups 21 SQL Server Always-On Failover Clusters 21 SQL Server Database Mirror 21 SQL Azure 21 NAV Service Sample Scripts 22 Main scripts 22 Helper scripts 22 Helper DLL 22 Definitions 23 The scripts 27 Helper scripts 29 Scripts deployed to Microsoft Dynamics NAV Server 29 Folder structure on the provisioning machine 30 Folder structure on the server 30 How to get started 31 2 Large scale hosting on Windows Azure Whitepaper 3 Large scale hosting on Windows Azure Whitepaper Introduction This whitepaper describes in detail how to deploy Microsoft Dynamics NAV 2013 R2 on Windows Azure so you can serve a very large number of customers with high availability. -

F.A.Q. Series ROM-DOS TM
21520 30th Drive SE #110 Bothell, WA 98021 USA Tel: (425) 951-8086 Fax: (425) 951-8095 [email protected] [email protected] www.datalight.com TM ROM-DOS F.A.Q. Series Question: Assuming they don't want FAT32, Long Filename support, or Sockets, why should my customer upgrade to the newest ROM-DOS? Answer: Since our first FAT32 and LFN release 4.00.1091, there have been several improvements to the core ROM- DOS kernel. This core code is used primarily for our DOS 6.22 compatible compilations, and then extended in the case of a FAT32 or Long Filename build. The 4.00.1091 release is also a new code base and there will be no further upgrades to the previous DOS 6.22 code. In order to obtain new features, fixes, and support a customer must upgrade to release 4.00.1091 or greater. Along with the performance enhancements for both size and speed, several corrections have been made to the ROM-DOS kernel. These include stack and memory issues, disk access issues, and compatibility with the former market leader in DOS. Most of the ROM-DOS utilities have also been improved for size and speed, along with bug fixes. The major changes happened with the XCOPY, HIMEM, MSCDEX, CHKDSK, FDISK and FORMAT utilities. In the realm of international support, the Euro was added to the keyboard and display driver code. ROM- DOS and PC-DOS 2000 are the only non-GUI operating systems to support the Euro. Finally, new ROM-DOS utilities have been added. -
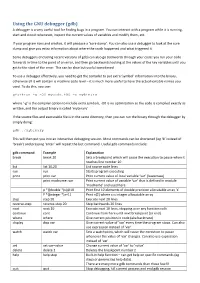
Using the GNU Debugger (Gdb) a Debugger Is a Very Useful Tool for Finding Bugs in a Program
Using the GNU debugger (gdb) A debugger is a very useful tool for finding bugs in a program. You can interact with a program while it is running, start and stop it whenever, inspect the current values of variables and modify them, etc. If your program runs and crashes, it will produce a ‘core dump’. You can also use a debugger to look at the core dump and give you extra information about where the crash happened and what triggered it. Some debuggers (including recent versions of gdb) can also go backwards through your code: you run your code forwards in time to the point of an error, and then go backwards looking at the values of the key variables until you get to the start of the error. This can be slow but useful sometimes! To use a debugger effectively, you need to get the compiler to put extra ‘symbol’ information into the binary, otherwise all it will contain is machine code level – it is much more useful to have the actual variable names you used. To do this, you use: gfortran –g –O0 mycode.f90 –o mybinary where ‘-g’ is the compiler option to include extra symbols, -O0 is no optimization so the code is compiled exactly as written, and the output binary is called ’mybinary’. If the source files and executable file is in the same directory, then you can run the binary through the debugger by simply doing: gdb ./mybinary This will then put you into an interactive debugging session. Most commands can be shortened (eg ‘b’ instead of ‘break’) and pressing ‘enter’ will repeat the last command. -

Active @ UNDELETE Users Guide | TOC | 2
Active @ UNDELETE Users Guide | TOC | 2 Contents Legal Statement..................................................................................................4 Active@ UNDELETE Overview............................................................................. 5 Getting Started with Active@ UNDELETE........................................................... 6 Active@ UNDELETE Views And Windows......................................................................................6 Recovery Explorer View.................................................................................................... 7 Logical Drive Scan Result View.......................................................................................... 7 Physical Device Scan View................................................................................................ 8 Search Results View........................................................................................................10 Application Log...............................................................................................................11 Welcome View................................................................................................................11 Using Active@ UNDELETE Overview................................................................. 13 Recover deleted Files and Folders.............................................................................................. 14 Scan a Volume (Logical Drive) for deleted files..................................................................15 -

CONESTOGA CABINET ASSEMBLY INFORMATION What Is Included with Your Cabinets: What Is Not Included with Your Cabinets
CONESTOGA CABINET ASSEMBLY INFORMATION We suggest you view the 4 minute assembly demonstration video on our web site to see how easily our high end custom cabinets are assembled. Before continuing, it is important to realize that Conestoga’s RTA cabinet is targeted at cabinet shops who would rather use this system than build their own custom cabinets from scratch. On one hand, this indicates that it’s a VERY high quality cabinet. On the other hand, it means Conestoga has made some assumptions that its user has certain level of cabinet making skills and knowledge which most homeowners may not possess. As a result, we feel the assembly instructions Conestoga details in their guide are incomplete. Therefore, we have compiled the following assembly information from our years of assembly experience with this product. Remember, as opposed to other Conestoga Re-sellers or sales agents, we actually use the product every day. So, if you have a question that is not answered here, just give us a call and we can talk you through it, send you images from our shop floor, diagrams or even helpful hardware items to assist you. If it gets frustrating, take some time away and give us a call or shoot us an email. Rest assured, we’ll get you through it! What is Included with Your Cabinets: Everything necessary to build the cabinet box. Drawer glides and necessary hardware/screws. Hinges and necessary hardware/screws. Doors, drawer fronts and drawer boxes. What is not included with Your Cabinets: Screws required to mount drawer fronts to the drawer boxes (we use self tapping wood screws 1-1/4” long, available at local home centers or hardware stores.