Microsoft Windows Server 2019 Version 1809 Hyper-V
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lab Report: 7.1.6 Configure Windows Defender
Lab Report: 7.1.6 Configure Windows Defender Your Performance Your Score: 0 of 6 (0%) Pass Status: Not Passed Elapsed Time: 12 seconds Required Score: 100% Task Summary Perform a full scan once per week Hide Details Perform the scan on Saturday Perform the scan at midnight (12:00 am) Perform a full system scan Check for updates before scanning Configure default actions to take Hide Details Remove severe alert items Remove high alert items Remove medium alert items Allow low alert items Apply recommended actions to items detected during a scan Configure advanced options Hide Details Scan email Scan removable drives Display items from all users of this computer Perform a quick scan Explanation In this lab, your task is to configure Windows Defender as follows: Automatic scanning setting: Frequency: Saturday Approximate time: 12:00 am Type: Full scan (A quick scan checks the areas of the computer that spyware is likely to affect, and a full scan checks all files and programs on the computer) Check for updated definitions before scanning: Enabled Default actions settings: Severe alert items: Remove High alert items: Remove Medium alert items: Remove Low alert items: Allow Apply recommended actions: Enabled Advanced settings: Scan email: Enabled Scan removable drives: Enabled Administrator settings: Display items from all users of this computer: Enabled Complete this lab as follows: 1. Right-click Start > Control Panel. 2. In the top right corner under View by, select Small icons from the drop-down list. 3. Select Windows Defender. 4. Select Tools. 5. Under Settings, select Options. 6. Make sure Automatically scan my computer (recommended) is selected to allow Windows Defender to scan the computer automatically. -

Mitigating Service Account Credential Theft on Windows
Mitigating Service Account Credential Theft on Windows Reducing the risk of automated authentication against untrusted endpoints Version 1.0.0 Last Updated: 2014-09-16 Mitigating Service Account Credential Theft on Windows Disclaimer This document is for informational purposes only. The authors make no warranties, express, implied, or statutory as to the information in the document. This document is provided "as-is". Information and views expressed in this document, including URLs and other Internet website references, may change without notice. You bear the risk of using it. This document is provided under the Creative Commons Attribution 4.0 International (CC BY 4.0) license. The names of actual companies and products mentioned herein may be the trademarks of their respective owners. Authors HD Moore Joe Bialek Ashwath Murthy Rapid7 Microsoft Palo Alto Networks Contents Executive Summary ................................................................................................................................................................ 1 Introduction ............................................................................................................................................................................ 2 Attacks .................................................................................................................................................................................... 2 Kerberos ............................................................................................................................................................................. -

Microsoft Windows 10 Update Hello, Microsoft Has Begun
Subject Line: Microsoft Windows 10 Update Hello, Microsoft has begun pushing a warning message to Windows 10 computers that a critical security update must be performed. Several clients have informed us that they are seeing the warning message. It will appear as a generic blue screen after your computer has been powered up, and it states that after April 10, 2018 Microsoft will no longer support your version of Windows 10 until the critical security update has been performed. Please note if your UAN computer has not been recently connected to the internet, you would not have received this message. UAN has confirmed that the warning message is a genuine message from Microsoft, and UAN strongly encourages all clients to perform this critical security update as soon as possible. Please note: ‐ This update is a Microsoft requirement and UAN cannot stop or delay its roll out. To perform the critical security updated select the ‘Download update’ button located within the warning message. ‐ This update is very large, for those clients that have metered internet usage at their home may want to perform the update at a different location with unmetered high speed internet, perhaps at another family member’s home. ‐ Several UAN staff members have performed the critical security update on their home computers, and the process took more than an hour to complete. To check that your computer has been updated or to force the update at a time that is convenient to you, go to the windows Start button and click on Settings (the icon that looks like a gear above the Start button) > Update and Security > Windows Update > Check for Updates and then follow the instructions on the screen. -

Windows Server Security Best Practices
Windows Server Security – Best Practices v.3.0.5 Windows Server Security Best Practices Revised – February 7, 2020 Version 2.0.0 ______________________________________________________________________________________ Page 1 of 10 Windows Server Security – Best Practices v.3.0.5 Initial Document Created by: 2009 Windows Server Security Best Practices Committee Document Creation Date: August 21, 2009 Revision Revised by: 2019 Windows Server Security Best Practices Committee Revision Date: February 7, 2020 Version Number: 2.0.0 Acknowledgments The final release document is a collaborative work between the following committee members: Freddie Lewis Khushbu Desai Theodore McDonald Tanya Sootes Usage The ever-changing nature of information technology prevents this document from being entirely inclusive but should serve as a general guideline. This document is not intended to supersede or replace policy. Please feel free to query the Windows Server Team ([email protected]) or the Systems Administrator Group ([email protected]) for additional guidance. ______________________________________________________________________________________ Page 2 of 10 Windows Server Security – Best Practices v.3.0.5 Table of Contents Initial Document 2 Revision 2 Acknowledgments 2 Usage 2 1. Security Best Practices 5 1.1. User Environment 5 1.1.1. Server Account Control 5 1.1.2. Administrator and Equivalents 5 1.1.3. Delegating Control 5 1.1.4. Password Policy 5 1.2. File and Print Serving 5 1.2.1. Folder and NTFS Permissions 5 1.2.2. Print Management 6 1.3. Remote Access 6 1.3.1. Remote Desktop 6 1.3.2. Off-Campus Access 6 1.4. OS Configuration and Maintenance 6 1.4.1. -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -

Microsoft Service Pack & Security Bulletin Support
Microsoft Service Pack & Security Bulletin Support ReadMe Revision History Date Revised Changes Made March 23, 2020 March 2020 Microsoft Security Update Contents What’s New? . 1 Microsoft Security Bulletins . 2 Current Microsoft Security Bulletin Status . 2 Enabling Windows Updates on Avid Systems . 6 Using a Microsoft WSUS Server for distributing Windows Updates. 7 Historical List of Microsoft Security Bulletin Exceptions . 7 What’s New? For March security bulletins, see “Current Microsoft Security Bulletin Status” on page 2. The section on “Notification Regarding the January 2020 Windows Updates” on page 3 has been updated to include information on MediaCentral Asset Management and MediaCentral Newsroom Management. See also http://avid.force.com/pkb/articles/en_US/Troubleshooting/en239659. Microsoft Security Bulletins Microsoft Security Bulletins Install Windows Security Patches and Service Packs. To download patches, run Windows Update. By default Avid supports all Windows Service Packs and security patches (sometimes referred to as “hot fixes”) which apply to the environments in which Avid products are deployed. We refer to them as Windows Updates in this document. Customers can schedule the download and installation of Windows Updates whenever they are available and make sense in their production environment. Avid tests the updates within several days of their availability. However, customers do not have to wait for the testing to be complete before installing the updates. Our current testing methodology is to utilize Windows Update on a representative sample of Avid products upon notification of new Security Bulletin availability by Microsoft. These systems are updated and observed while under test. Once the test period has completed (approx. -
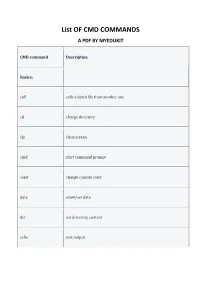
List of CMD COMMANDS a PDF by MYEDUKIT
List OF CMD COMMANDS A PDF BY MYEDUKIT CMD command Description Basics: call calls a batch file from another one cd change directory cls clear screen cmd start command prompt color change console color date show/set date dir list directory content echo text output exit exits the command prompt or a batch file find find files hostname display host name pause pauses the execution of a batch file and shows a message runas start a program as another user shutdown shutdown the computer sort sort the screen output start start an own window to execute a program or command taskkill terminate a process or an application tasklist display applications and related tasks time display/edit the system time timeout wait any time title set title for prompt ver display operating system version w32tm setting time synchronisation/time server/time zone Network: ftp transfer files to an FTP server ftype display file type and mapping getmac display MAC address ipconfig display IP network settings netsh configure/control/display network components netstat display TCP/IP connections and status nslookup query the DNS pathping test the connection to a specific IP address ping pings the network route display network routing table, add static routes systeminfo displays computer-specific properties and configurations telnet establish a Telnet connection tftp transfer files to a TFTP server tracert trace routes similar to patchping Files: attrib display file attributes comp compare file contents compact display/change file compression copy / xcopy copy files diskcomp -

Prepare Customer Site Servers
Prepare Customer Site Servers • Prepare Customer Site Servers, on page 1 • Prepare Cisco UCS C-Series Customer Site Servers, on page 1 • Prepare HyperFlex M5 series Customer Site Servers, on page 3 • NTP and Time Synchronization, on page 4 • Global Catalog Requirements, on page 5 Prepare Customer Site Servers Perform all the procedures in this section on the Side A and the Side B servers. Prepare Cisco UCS C-Series Customer Site Servers Configure RAID for C240 M4SX The disk array configuration for the C240 M4SX is already set up to match what is required for Packaged CCE. Verify the settings as follows. Using Cisco Integrated Management Controller, check that the following settings are configured correctly: • Virtual Drive Info: RAID 5 with 5 (Physical Disks) * 4 (Virtual Drives/Datastores) • Stripe Size: 128KB • Write Policy: Write Back with BBU • Read Policy: Read Ahead Always For more information regarding RAID configuration for C240 M4SX in Configure RAID with GUI (UCS C-Series M4 Servers) section, see Cisco Collaboration on Virtual Servers Guide at: https://www.cisco.com/ c/en/us/td/docs/voice_ip_comm/cucm/virtual/CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers/ CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers_chapter_01.html#CUCM_TK_C2DC4F2D_ 00. Prepare Customer Site Servers 1 Prepare Customer Site Servers Run the RAID Config Validator Utility Run the RAID Config Validator Utility After you set up RAID configuration and add the datastores, run the RAID Config Validator utility to ensure that your datastore configuration is correct. Before you begin To run the utility, Java 7 (any update) must be installed. Java 8 and later releases are not supported. -

Operational and Administrative Guidance Microsoft Windows 10
Operational and Administrative Guidance Microsoft Windows 10 and Windows Server Common Criteria Evaluation for Microsoft Windows 10 and Windows Server Version 1803 General Purpose Operating System Protection Profile © 2018 Microsoft Confidential. All rights reserved. Microsoft Windows 10 GP OS Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. No association with any real company, organization, product, person or event is intended or should be inferred. -

Deployment Strategy
System Management Best Practices Bryan S Owen PE Copyright c 2004 OSIsoft Inc. All rights reserved. Richness & Reliability “Value Coefficients” • Quality – Across operations and data systems • Quantity – Across business needs and over time • Utilization – Across enterprise and just in time It all Starts with Great Software …and the Right Architecture • Visualization Tools • Availability • Reliability • Security Integrated Data Collection Proven: Cutting Edge: Integrated Interface Embedded Historian Embedded PI Historian • Continuous Historian for DeltaV Application Station http://www.easydeltav.com/pd/PDS_ApplicationStation.pdf • “56SAM” Historian for Allen-Bradley ControlLogix www.oldi.com • “Promoted” Interface Node • Also visit: www.echohistorian.com Fault Tolerant vs Redundant Incident Tolerant Redundant Environment Fault JJ JJJ Hardware Fault JJJ JJ Software Fault K J Administrative Error JK JJ Scheduled Down K JJJ “Smile” Points: 15/30 22/30 Redundant Architecture • Reliability – Build from the Data Up • Availability – Build from the Users Down You decide what comes first! Redundant Data Collection Dual Gateways Interface Node Failover Redundant Data Service Dual PI Servers Dual PI Clients Redundant Architecture No single point of failure sounds great, what’s the catch? • Interface Support • History Recovery • Gap Filling • Client Impact • Fugitive Data Fugitive Data Capture Essential for rich content but… 1% of the data causes 99% perspiration! • Manual Entry Systems • Custom Applications • Isolated Point to Point Links Solution: -

IBM Connect:Direct for Microsoft Windows: Documentation Fixpack 1 (V6.1.0.1)
IBM Connect:Direct for Microsoft Windows 6.1 Documentation IBM This edition applies to Version 5 Release 3 of IBM® Connect:Direct and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright International Business Machines Corporation 1993, 2018. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Chapter 1. Release Notes.......................................................................................1 Requirements...............................................................................................................................................1 Features and Enhancements....................................................................................................................... 2 Special Considerations................................................................................................................................ 3 Known Restrictions...................................................................................................................................... 4 Restrictions for Connect:Direct for Microsoft Windows........................................................................ 4 Restrictions for Related Software.......................................................................................................... 6 Installation Notes.........................................................................................................................................6 -

Operational and Administrative Guidance
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious.