Microsoft Service Pack & Security Bulletin Support
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Microsoft Windows 10 Update Hello, Microsoft Has Begun
Subject Line: Microsoft Windows 10 Update Hello, Microsoft has begun pushing a warning message to Windows 10 computers that a critical security update must be performed. Several clients have informed us that they are seeing the warning message. It will appear as a generic blue screen after your computer has been powered up, and it states that after April 10, 2018 Microsoft will no longer support your version of Windows 10 until the critical security update has been performed. Please note if your UAN computer has not been recently connected to the internet, you would not have received this message. UAN has confirmed that the warning message is a genuine message from Microsoft, and UAN strongly encourages all clients to perform this critical security update as soon as possible. Please note: ‐ This update is a Microsoft requirement and UAN cannot stop or delay its roll out. To perform the critical security updated select the ‘Download update’ button located within the warning message. ‐ This update is very large, for those clients that have metered internet usage at their home may want to perform the update at a different location with unmetered high speed internet, perhaps at another family member’s home. ‐ Several UAN staff members have performed the critical security update on their home computers, and the process took more than an hour to complete. To check that your computer has been updated or to force the update at a time that is convenient to you, go to the windows Start button and click on Settings (the icon that looks like a gear above the Start button) > Update and Security > Windows Update > Check for Updates and then follow the instructions on the screen. -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -
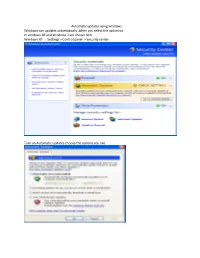
Automatic Updates Using Windows Windows Can Updates Automatically ,When You Select the Option On
Automatic updates using windows Windows can updates automatically ,when you select the option on. In windows XP and Windows 7 are shown here Windows XP : Settings > Control panel > Security center Turn on Automatic updates choose the options you like. In windows 7: Control panel > System and security So how can do all users let updates on system. By default, Windows only allows users with administrator user accounts to install updates. To allow all users to install updates, follow these steps: Click to open Windows Update. In the left pane, click Change settings. Do one of the following: To allow standard users to install updates, select the Allow all users to install updates on this computer check box. To prevent standard users from installing updates, clear the Allow all users to install updates on this computer check box. If you use automatic updating for Important or Recommended updates, those updates are installed regardless of whether the current user is an administrator or not. Different types of updates Updates are classified as Important, Recommended, Optional, and Featured. Important updates offer significant benefits, such as improved security, privacy, and reliability. They should be installed as they become available, and can be installed automatically with Windows Update. Recommended updates address non-critical problems or help enhance your computing experience. While these updates do not address fundamental issues with your computer or Windows software, they can offer meaningful improvements. These can be installed automatically. Optional updates can include updates, drivers, or new software from Microsoft to enhance your computing experience. You can only install these manually. -

Microsoft Windows Server 2019 Version 1809 Hyper-V
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

Migrating Active Directory to Windows Server 2012 R2
Windows Server 2012 R2 Migrating Active Directory to Windows Server 2012 R2 Hands-on lab In this lab, you will complete a migration of a Windows Server 2008 R2 domain environment to Windows Server 2012 R2 with no downtime to clients. All roles currently held including FSMO, DHCP and DNS will be transferred to enable the Windows Server 2008 R2 domain controller to be retired. Produced by HynesITe, Inc. Version 1.0 12/15/2013 This document supports a preliminary release of a software product that may be changed substantially prior to final commercial release. This document is provided for informational purposes only and Microsoft makes no warranties, either express or implied, in this document. Information in this document, including URL and other Internet Web site references, is subject to change without notice. The entire risk of the use or the results from the use of this document remains with the user. Unless otherwise noted, the companies, organizations, products, domain names, e-mail addresses, logos, people, places, and events depicted in examples herein are fictitious. No association with any real company, organization, product, domain name, e-mail address, logo, person, place, or event is intended or should be inferred. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form or by any means (electronic, mechanical, photocopying, recording, or otherwise), or for any purpose, without the express written permission of Microsoft Corporation. -

The Control Panel and Settings in Windows 10 Most Programs and Apps Have Settings Specific to That Program
GGCS Introduction to Windows 10 Part 3: The Control Panel and Settings in Windows 10 Most programs and apps have settings specific to that program. For example, in a word processor such as Microsoft Word there are settings for margins, fonts, tabs, etc. If you have another word processor, it can have different settings for margins, fonts, etc. These specific settings only affect one program. The settings in the Control Panel and in Settings are more general and affect the whole computer and peripherals such as the mouse, keyboard, monitor and printers. For example, if you switch the right and left buttons on the mouse in the Control Panel or in Settings, they are switched for everything you click on. If you change the resolution of the monitor, it is changed for the desktop, menus, Word, Internet Explorer and Edge, etc. How to display the Control Panel 1. Right-click the Windows Start button or press the Windows key on the keyboard + X. 2. Click “Control Panel” on the popup menu as shown in the first screen capture. In Windows 10, many of the settings that once were in the Control Panel have moved to Settings. However, there are often links in Settings that take you back to the Control Panel and many other settings that still only exist in the Control Panel. Settings versus Control Panel is an evolving part of Windows design that started with Windows 8. It is not clear at this time whether the Control Panel will eventually go away or whether it will simply be used less frequently by most users. -

Security Policy for FIPS 140-2 Validation
BitLocker Windows Resume Security Policy for FIPS 140‐2 Validation BitLocker® Windows Resume (winresume) in Microsoft Windows 8.1 Enterprise Windows Server 2012 R2 Windows Storage Server 2012 R2 Surface Pro 3 Surface Pro 2 Surface Pro Windows Embedded 8.1 Industry Enterprise StorSimple 8000 Series DOCUMENT INFORMATION Version Number 2.0 Updated On April 22, 2015 © 2015 Microsoft. All Rights Reserved Page 1 of 19 This Security Policy is non‐proprietary and may be reproduced only in its original entirety (without revision). BitLocker Windows Resume The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. -

Security Update Notification
6605 19 ½ Mile Road Sterling Heights, MI 48314-1408 USA Tel: +1-586-254-0020 | Fax: +1-586-254-0053 [email protected] | www.sisconet.com Security Update Notification Microsoft Common Controls ActiveX Control (MSCOMCTL.OCX) Vulnerability 12 December 2012 (Links Updated 21 April 2016) NOTE: This Security Update Notification supersedes the version previously posted by SISCO dated 7 August 2012. An additional vulnerability was found by Microsoft requiring a new update. If you did not apply the update described in the 7 August 2012 notice you only need to apply the update described here. If you did apply the update described in the 7 August 2012 notice you will also need to apply the update from this notice. Microsoft Security Bulletin MS12‐060 disclosed a Critical Vulnerability in the Windows Common Controls that could allow remote code execution http://technet.microsoft.com/en‐us/security/bulletin/ms12‐060 . This ActiveX control is bundled with the Visual Basic 6 redistributable run‐time package that SISCO includes with our products. There is a security patch available from Microsoft for this vulnerability that many systems will receive under normal Windows update processes. HOWEVER, unless your computer has a Microsoft product installed (i.e. Office, SQL Server, BizTalk, etc.) that is checked during the Microsoft Windows Update process you will not receive an update. Microsoft’s Windows Update process will not detect the presence of this vulnerable control if you have not installed one or more of these other Microsoft products. The presence of the VB6 redistributable run‐time package that SISCO installs will not be detected by the Windows Update process if you do not have these other Microsoft products installed. -

Using Powershell Script to Manage the Windows 10 Update Policy
Using PowerShell Script to Manage the Windows 10 Update Policy Introduction The main objective of this article is to provide step-by-step instructions on how to use PowerShell script to set and modify the Windows update policy using a Windows bundle. The Windows 10 update settings can be easily re-configured using this bundle. This document includes the following information: • Prerequisites • Creating the Bundle • Deploying the Bundle • Logging Results Prerequisites Prior to deploying the bundle, you need be aware of the following: • The Windows bundle can be deployed only on Windows 10 devices. • Using the bundle, you can modify the update settings for Windows 10 devices. However, if the same setting is controlled by a group policy, the latter will prevail. • Prior to deploying the bundle, you must enable script execution by running the following command: Set-ExecutionPolicy <Unrestricted / AllSigned / RemoteSigned>). By default, the value set as Restricted. Creating the Bundle To create the Windows bundle: 1. In ZENworks Control Center, create a Windows bundle and add the modifyWindowsUpdateConfiguration.ps1, the settings.xml and the Setupconfig.ini files. For the Setupconfig.ini file, ensure that you specify the Destination Directory as %systemdrive%\Users\Default\AppData\Local\Microsoft\Windows\WSUS\ For information on how to create Windows bundles, see https://www.novell.com/documentation/zenworks-2017-update- 1/zen_cm_software_distribution/data/ba480hx.html 2. In the Bundles page, click the bundle that was created in the previous step and click Actions > Launch. 3. Click the Run Script Action link and in the Edit Action – Script dialog, specify the Action Name, Script File Name, Script Parameters and Path to Script Engine. -

Microsoft Windows Server 2012 R2
MICROSOFT WINDOWS SERVER 2012 R2 APPLICATION-FOCUSED SERVICES TOP 3 BENEFITS Windows Server 2012 R2 enables you to build and deploy applications in your data center that utilize higher-level, ❒4 Comprehensive Cloud Platform cloud-based application services and APIs that are ❒4 Cost Savings and Increased Efficiencies compatible with service provider clouds and Windows Azure. This functionality provides improved application ❒4 Support for a Modern Work Style portability between on-premises, public and partner- hosted clouds, increasing the flexibility and elasticity of your IT services. OPTIMIZE YOUR CLOUD BUSINESS Windows Server 2012 R2 also provides frameworks, With the world of IT changing rapidly, traditional services and tools to increase scalability and elasticity approaches to solving infrastructure problems are for multitenant-aware applications and websites. inadequate. The Microsoft vision for this new era of IT is to provide one consistent platform for infrastructure, apps, and data: the Cloud OS. The Cloud OS spans customer data centers, service provider data centers and the Microsoft PEOPLE WHO GET IT public cloud. At the heart of the solution is Windows Server 2012 R2. With Windows Server 2012 R2, you gain Along with your dedicated account manager, an enterprise-grade platform to cost-effectively optimize CDW has Microsoft trained and certified your business with a cloud. experts who can help find the right data center technologies for you, including: SIMPLE AND COST-EFFECTIVE DESIGN Windows Server 2012 R2 enables you to blend your Professional Services: on-premises solutions with the cloud without having • 500 engineers and project managers, to reengineer infrastructure, systems management or including 90+ Microsoft engineers applications. -

Monitoring Windows with Powershell
Monitoring Windows Systems with PowerShell SL1 version 8.14.0 Table of Contents Introduction 4 Monitoring Windows Devices in the ScienceLogic Platform 5 What is SNMP? 5 What is PowerShell? 5 PowerPacks 6 Configuring Windows Systems for Monitoring with SNMP 7 Configuring SNMP for Windows Server 2016 and Windows Server 2012 8 Configuring Ping Responses 8 Installing the SNMP Service 9 Configuring the SNMP Service 14 Configuring the Firewall to Allow SNMP Requests 19 Configuring Device Classes for Windows Server 2016 and Windows 10 19 Manually Align the Device Class 20 Edit the Registry Key 20 Configuring SNMP for Windows Server 2008 21 Configuring Ping Responses 21 Installing the SNMP Service 22 Configuring the SNMP Service 25 Configuring the Firewall to Allow SNMP Requests 30 Configuring Windows Servers for Monitoring with PowerShell 31 Prerequisites 32 Configuring PowerShell 32 Step 1: Configuring the User Account for the ScienceLogic Platform 33 Option 1: Creating an Active Directory Account with Administrator Access 33 Option 2: Creating a Local User Account with Administrator Access 34 Option 3: Creating a Non-Administrator User Account 34 Optional: Configuring the User Account for Remote PowerShell Access to Microsoft Exchange Server 36 Optional: Configuring the User Account for Remote PowerShell Access to Hyper-V Servers 36 Creating a User Group and Adding a User in Active Directory 36 Setting the Session Configuration Parameters and Group Permissions 37 Creating a PowerShell Credential 38 Optional: Configuring the User Account for -

Vmware Horizon 7 7.13 Setting up Published Desktops and Applications in Horizon Console
Setting Up Published Desktops and Applications in Horizon Console OCT 2020 VMware Horizon 7 7.13 Setting Up Published Desktops and Applications in Horizon Console You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com © Copyright 2018-2020 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 2 Contents 1 Setting Up Published Desktops and Applications in Horizon Console 6 2 Introduction to Published Desktops and Applications 7 Farms, RDS Hosts, and Published Desktops and Applications 7 Advantages of Published Desktop Pools 8 Advantages of Application Pools 8 3 Setting Up Remote Desktop Services Hosts 10 Remote Desktop Services Hosts 10 Prepare Windows Server Operating Systems for Remote Desktop Services (RDS) Host Use 12 Install Remote Desktop Services on Windows Server 2008 R2 14 Install Remote Desktop Services on Windows Server 2012, 2012 R2, 2016, or 2019 15 Install Desktop Experience on Windows Server 2008 R2 16 Install Desktop Experience on Windows Server 2012, 2012 R2, 2016, or 2019 16 Restrict Users to a Single Session 17 Install Horizon Agent on a Remote Desktop Services Host 18 Horizon Agent Custom Setup Options for an RDS Host 19 Modify Installed Components with the Horizon Agent Installer 22 Silent Installation Properties for Horizon Agent 23 Printing From a Remote Application Launched Inside a Nested Session 28 Enable Time Zone Redirection for Published Desktop and Application