Monitoring Windows with Powershell
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
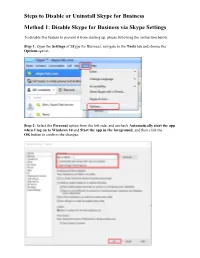
Steps to Disable Or Uninstall Skype for Business Method 1: Disable Skype for Business Via Skype Settings
Steps to Disable or Uninstall Skype for Business Method 1: Disable Skype for Business via Skype Settings To disable this feature to prevent it from starting up, please following the instruction below. Step 1: Open the Settings of Skype for Business, navigate to the Tools tab and choose the Options option. Step 2: Select the Personal option from the left side, and uncheck Automatically start the app when I log on to Windows 10 and Start the app in the foreground, and then click the OK button to confirm the changes. Step 3: Click the Settings button again on the Skype for Business interface and choose File then Exit. After the three steps, you have successfully disabled Skype for Business from your PC and you will no longer see it although it is still on your computer. Method 2: Uninstall Skype for Business via Control Panel This method requires you to clear all your profile cache for the Skype for Business account and then uninstall it from Windows 10 via Control Panel. Here is the detailed tutorial on uninstalling Skype for Business. Step 1: Open your Skype for business and then sign out of this application. Step 2: In the Sign in interface, please click the Delete my sign-in info option. Note: This step will clear all your profile cache for the Skype for Business account and will disable the auto sign-in when the application opens. Step 3: Close Skype for Business. Step 4: You should uninstall Skype for Business like any other software on your computer. Click on the Windows button in the bottom left of your screen and type Control Panel. -

Illustrated Tutorial: Creating a Bootable USB Flash Drive for Windows XP
Illustrated tutorial: Creating a bootable Version 1.0 February 15, 2007 USB flash drive for Windows XP By Greg Shultz The ability to boot Windows XP from a USB Flash Drive (UFD) offers endless possibilities. For example, you might make an easy-to-use troubleshooting tool for booting and analyzing seemingly dead PCs. Or you could transport your favorite applications back and forth from home to work without having to install them on both PCs. However, before you can create a bootable UFD, you must clear a few hurdles. You saw that one coming didn’t you? The first hurdle is having a PC in which the BIOS will allow you to configure the USB port to act as a bootable device. The second hurdle is having a UFD that that will work as a bootable device and that’s large enough and fast enough to boot an operating system such as Windows XP. The third hurdle is finding a way to condense and install Windows XP on a UFD. If you have a PC that was manufactured in the last several years, chances are that its BIOS will allow you to configure the USB port to act as a bootable device. If you have a good qual- ity UFD that’s at least 512 KB and that was manufactured in the last couple of years, you’ve probably cleared the second hurdle. And once you’ve cleared those first two hur- dles, the third one is a piece of cake. All you have to do is download and run some free soft- ware to create the bootable UFD. -

An Adaptive Policy Based Framework for Network Management
Department of Computing Imperial College London University of London An Adaptive Policy Based Framework for Network Management Leonidas A. Lymberopoulos A thesis submitted in partial fulfilment of the requirements for the degree of Doctor of Philosophy in the Faculty of Engineering of the University of London, and for the Diploma of the Imperial College London London, October 2004 Στους γονείς µου, Αντρέα και Γεωργία To my parents, Andreas and Georgia Abstract Policy-based management has emerged as a promising solution for the management of large-scale and heterogeneous networks. This approach has been adopted in several network management areas, such as in the areas of Quality of Service (QoS) and security management. However, although policy-based management has been the subject of considerable research, proposed solutions are often restricted to static condition-action rules where conditions determine when actions should be performed on the managed entities. The static policy configurations require manual intervention to cater for configuration changes and to enable policy deployment. However, changes in the system such as QoS violations, network failures or denial of service attacks in a secured network may require adaptation of existing policies to new circumstances. Thus, policies themselves need to be managed and adapted. Policies define management strategies for network devices, access control systems or internet services. However, little work has been done on validating whether the policies will lead to a feasible implementation for the specific environment to which they apply. Validation requires checking that the policy is consistent with the functional or resource constraints within the target environment. For example, one can check whether the policies assume functionality or specific operations, which do not exist in target devices, or bandwidth in excess of the capacity of data links. -
Opening Skype on Windows 10
Skype Opening Skype on Windows 10 ................... 1 Making a Video Call ..................................... 3 Checking Your Audio & Video .................... 2 Accepting a Video Call .................................4 Using Skype ................................................. 3 Installing Skype ........................................... 5 Finding Someone ........................................ 3 Opening Skype on Windows 10 1. On a Windows 10 computer, in the lower left corner click the Windows icon. 2. Type in “Skype” and as soon as you see “Skype” click on that selection, and enter your Skype username and password if prompted. If you do not already have a Skype account, you can easily create one—they are free. You can even create a Microsoft account just for Skype at https://outlook.live.com/owa Checking Your Audio & Video 1. Open Skype. 2. In the left pane, in the top right corner, click on the ellipse (…). 3. Your Settings open. 4. In the left pane, select Audio & Video. 5. In the Camera section your live picture should appear. If it does not, see if there is an option above your picture, and try selecting a different web camera. 6. Scroll down until you see the Audio section. Test your microphone and speakers and adjust the volume as needed. 7. Close the dialog box by clicking the X in the top left corner. Using Skype Once you open Skype, you will select someone to call from the left pane. You have some important options there: Search, Chats, Contacts The first couple times you use Skype you may need to search for your friends and family. You can search by name or email address associated with their Skype account. -

Administrative Guide for Windows 10 and Windows Server Fall Creators Update (1709)
Operational and Administrative Guidance Microsoft Windows 10 and Windows Server Common Criteria Evaluation for Microsoft Windows 10 and Windows Server Version 1903 (May 2019 Update) General Purpose Operating System Protection Profile © 2019 Microsoft. All rights reserved. Microsoft Windows 10 GP OS Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. No association with any real company, organization, product, person or event is intended or should be inferred. -

Microsoft Windows 10 Update Hello, Microsoft Has Begun
Subject Line: Microsoft Windows 10 Update Hello, Microsoft has begun pushing a warning message to Windows 10 computers that a critical security update must be performed. Several clients have informed us that they are seeing the warning message. It will appear as a generic blue screen after your computer has been powered up, and it states that after April 10, 2018 Microsoft will no longer support your version of Windows 10 until the critical security update has been performed. Please note if your UAN computer has not been recently connected to the internet, you would not have received this message. UAN has confirmed that the warning message is a genuine message from Microsoft, and UAN strongly encourages all clients to perform this critical security update as soon as possible. Please note: ‐ This update is a Microsoft requirement and UAN cannot stop or delay its roll out. To perform the critical security updated select the ‘Download update’ button located within the warning message. ‐ This update is very large, for those clients that have metered internet usage at their home may want to perform the update at a different location with unmetered high speed internet, perhaps at another family member’s home. ‐ Several UAN staff members have performed the critical security update on their home computers, and the process took more than an hour to complete. To check that your computer has been updated or to force the update at a time that is convenient to you, go to the windows Start button and click on Settings (the icon that looks like a gear above the Start button) > Update and Security > Windows Update > Check for Updates and then follow the instructions on the screen. -

Microsoft Service Pack & Security Bulletin Support
Microsoft Service Pack & Security Bulletin Support ReadMe Revision History Date Revised Changes Made March 23, 2020 March 2020 Microsoft Security Update Contents What’s New? . 1 Microsoft Security Bulletins . 2 Current Microsoft Security Bulletin Status . 2 Enabling Windows Updates on Avid Systems . 6 Using a Microsoft WSUS Server for distributing Windows Updates. 7 Historical List of Microsoft Security Bulletin Exceptions . 7 What’s New? For March security bulletins, see “Current Microsoft Security Bulletin Status” on page 2. The section on “Notification Regarding the January 2020 Windows Updates” on page 3 has been updated to include information on MediaCentral Asset Management and MediaCentral Newsroom Management. See also http://avid.force.com/pkb/articles/en_US/Troubleshooting/en239659. Microsoft Security Bulletins Microsoft Security Bulletins Install Windows Security Patches and Service Packs. To download patches, run Windows Update. By default Avid supports all Windows Service Packs and security patches (sometimes referred to as “hot fixes”) which apply to the environments in which Avid products are deployed. We refer to them as Windows Updates in this document. Customers can schedule the download and installation of Windows Updates whenever they are available and make sense in their production environment. Avid tests the updates within several days of their availability. However, customers do not have to wait for the testing to be complete before installing the updates. Our current testing methodology is to utilize Windows Update on a representative sample of Avid products upon notification of new Security Bulletin availability by Microsoft. These systems are updated and observed while under test. Once the test period has completed (approx. -

© Iquila Ltd 2018-2019 - 1
Rev-1 Joining a Client PC to a Domain Controller using iQuila Server Setup 1. Install the iQuila client software on your windows domain controller server (please note if you have more than one domain controller, you must install the iQuila client software on each domain controller in your network.) 2. Assign a static IP address to the iQuila virtual network adaptor. (Please see Help Document for using Static IP addresses) 3. Go to Control Panel then select view network status and tasks, select change adaptor settings, right click on the iQuila network adaptor (VPN – VPN Client) and client properties. 4. Select Internet protocol version v (TCP/IPv4) and click properties. Select use the following IP address and enter an IP address in your given range, i.e. 192.168.30.9. Enter your given subnet mask i.e. 255.255.255.0 Leave the default gateway setting blank Under the DNS section select use the preferred DNS server address and enter the same address as you entered for the IP address 192.168.30.9 Click ok to save IP address and click on the exit the adaptor properties window. © iQuila Ltd 2018-2019 - www.iquila.com 1 Client Setup 1. Install the iQuila client software on the client computers that you would like to join to the domain and ensure they have registered with the iQuila Cloud server. 2. You now need to set the DNS server address on the iQuila virtual adaptor or contact iQuila support and request the change of DNS address in your Virtual DHCP Server settings. -

Microsoft DNS
1 a. Domain Name Service (DNS) encompassing Microsoft DNS From Wikipedia, the free encyclopedia Jump to: navigation, search Microsoft DNS is the name given to the implementation of domain name system services provided in Microsoft Windows operating systems. Contents [hide] 1 Overview 2 DNS lookup client o 2.1 The effects of running the DNS Client service o 2.2 Differences from other systems 3 Dynamic DNS Update client 4 DNS server o 4.1 Common issues 5 See also 6 References 7 External links [edit] Overview The Domain Name System support in Microsoft Windows NT, and thus its derivatives Windows 2000, Windows XP, and Windows Server 2003, comprises two clients and a server. Every Microsoft Windows machine has a DNS lookup client, to perform ordinary DNS lookups. Some machines have a Dynamic DNS client, to perform Dynamic DNS Update transactions, registering the machines' names and IP addresses. Some machines run a DNS server, to publish DNS data, to service DNS lookup requests from DNS lookup clients, and to service DNS update requests from DNS update clients. The server software is only supplied with the server versions of Windows. [edit] DNS lookup client Applications perform DNS lookups with the aid of a DLL. They call library functions in the DLL, which in turn handle all communications with DNS servers (over UDP or TCP) and return the final results of the lookup back to the applications. 2 Microsoft's DNS client also has optional support for local caching, in the form of a DNS Client service (also known as DNSCACHE). Before they attempt to directly communicate with DNS servers, the library routines first attempt to make a local IPC connection to the DNS Client service on the machine. -

Microsoft Windows Server 2016 on Hp Z2 Mini G4, Z240, Z440, Z640, and Z840 Workstations
TECHNICAL WHITE PAPER CONTENTS & NAVIGATION 1 Before you begin 2 Things you need before you begin Support plan 2-5 Operating system installation process 6 Summary Appendix A: Additional HP support URLs INSTALLING MICROSOFT WINDOWS SERVER 2016 ON HP Z2 MINI G4, Z240, Z440, Z640, AND Z840 WORKSTATIONS BEFORE YOU BEGIN Before starting this process, note the following: • It is very important to be aware of the Microsoft Windows operating system licensing requirements. Contact your Microsoft licensing representative for the proper licensing requirements. • The Web URLs listed in this document are for additional reference. URLs are subject to change or termination. HP makes no attempt to assure that these URLs are current. • By providing this document, HP is not liable for providing any additional consulting services. Contact your HP Sales Representative or Channel Partner to arrange for additional HP Consulting Services. • This document is not meant to be comprehensive in supporting all the possible configurations of the HP Z G4, HP Zx40, and HP Z2 Mini G4 Workstations. Instead, it provides sufficient information to enable key hardware devices. Warning You should always back up all important data (such as personal files, photos, videos, documents, applications, software) before beginning the converter process to avoid any possibility of losing your data. See https://support.hp.com/us-en/document/c03270359 for more information. Following the installation steps outlined in this document will erase your hard drive. If your hard drive already contains information you need to retain, be sure to make a backup copy to a separate location before 1. proceeding with the installation. -

Platform Support Matrix for SAP Business
Platform Support Matrix PUBLIC SAP Business One Document Version: 1.28 – 2021-05-07 SAP Business One Platform Support Matrix Release 9.0 and higher Typographic Conventions Type Style Description Example Words or characters quoted from the screen. These include field names, screen titles, pushbuttons labels, menu names, menu paths, and menu options. Textual cross-references to other documents. Example Emphasized words or expressions. EXAMPLE Technical names of system objects. These include report names, program names, transaction codes, table names, and key concepts of a programming language when they are surrounded by body text, for example, SELECT and INCLUDE. Example Output on the screen. This includes file and directory names and their paths, messages, names of variables and parameters, source text, and names of installation, upgrade and database tools. Example Exact user entry. These are words or characters that you enter in the system exactly as they appear in the documentation. <Example> Variable user entry. Angle brackets indicate that you replace these words and characters with appropriate entries to make entries in the system. EXAMPLE Keys on the keyboard, for example, F2 or ENTER. PUBLIC © 2021 SAP SE or an SAP affiliate company. All SAP Business One Platform Support Matrix 2 rights reserved. Typographic Conventions Document History Version Date Change 1.0 2014-02-12 Release Version 1.01 2014-05-08 SAP Note 1787431 link added on XL Reporter platform support restrictions 1.02 2014-07-08 SAP Business One 9.1 added to the overview -

Contents About the Author
Auditing Microsoft Domain Environment Contents About the Author.........................................................................................................................2 About The Microsoft Domain Environments:............................................................................3 About Auditing:...........................................................................................................................4 Gaining First User:......................................................................................................................5 Enumerating AD Users and Groups With Gained User:.............................................................8 Checking Common Vulnerabilities:..........................................................................................12 Gaining First Shell:...................................................................................................................13 Migrating Into A Process:.........................................................................................................15 Pass The Hash:..........................................................................................................................17 Dump Everything From Domain Controller:............................................................................18 Auditing Microsoft Domain Environment 1 Auditing Microsoft Domain Environment About the Author Engin Demirbilek, Computer Engineering Student Penetration Tester in Turkey at SiberAsist Cyber Security Consultancy.