Red Hat Enterprise Virtualization Sizing Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Red Hat Jboss Developer Studio
RED HAT JBOSS DEVELOPER STUDIO DATASHEET BENEFITS EVERYTHING YOU NEED TO DEVELOP, TEST, AND DEPLOY RICH WEB, MOBILE WEB, AND ENTERPRISE APPLICATIONS AND SOA SERVICES. • Provides a pre-assembled ® ® development environment, Red Hat JBoss Developer Studio provides superior support for your entire development life including both tooling and cycle in a single tool. It is a certified Eclipse-based integrated development environment (IDE) for runtime components developing, testing, and deploying rich web applications, mobile web applications, transactional enterprise applications, and SOA-based integration applications and services. • Enables development of applications for deployment JBoss Developer Studio includes a broad set of tooling capabilities and support for multiple pro- on-premise or in the cloud gramming models and frameworks, including Java™ Enterprise Edition 6, RichFaces, JavaServer ® through its seamless inte- Faces (JSF), Enterprise JavaBeans (EJB), Java Persistence API (JPA), and Hibernate , JAX-RS gration with both OpenShift with RESTEasy, Contexts Dependency Injection (CDI), HTML5, and many other popular technolo- Enterprise by Red Hat and gies. It is fully tested and certified to ensure that all its plug-ins, runtime components, and their OpenShift Online by Red Hat dependencies are compatible with each other. • Certified updates so you JBoss Developer Studio provides developer choice in supporting multiple Java virtual machines don’t have to worry about (JVMs), productivity with Maven, and testing with Arquillian. It also includes all needed depen- updating parts that may dencies and third-party plugins. These pre-configured tools save time and offer significant value, not work with the rest of improving productivity and reducing deployment times. the environment Developers can have confidence that their development environment is stable, upgradeable, • Tested and certified to deployable, and supportable. -

5.7 Release Notes
Red Hat Enterprise Linux 5 5.7 Release Notes Release Notes for Red Hat Enterprise Linux 5.7 Red Hat Inc. Red Hat Enterprise Linux 5 5.7 Release Notes Release Notes for Red Hat Enterprise Linux 5.7 Legal Notice Copyright © 2011 Red Hat, Inc. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat Software Collections is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. The OpenStack ® Word Mark and OpenStack logo are either registered trademarks/service marks or trademarks/service marks of the OpenStack Foundation, in the United States and other countries and are used with the OpenStack Foundation's permission. -

Vmware Vsphere the Leader in Virtualized Infrastructure and Your First Step to Application Modernization
DATASHEET VMware vSphere The leader in virtualized infrastructure and your first step to application modernization AT A GLANCE Why VMware vSphere®? VMware vSphere® is the industry vSphere 7 is the biggest release of vSphere in over a decade. With the latest release, VMware W leading compute virtualization platform. E ® vSphereN vSp withher eVMware 7 wit hTanzu Tan™z enablesu millions of IT administrators across the globe to get started with Kubernetes workloads within an hour1. vSphere 7 has been rearchitected with Modernize the 70 million+ workloads running on vSphere native Kubernetes for application modernization. Developers can’t afford infrastructure that slows them down – I P A businesses rely on developers to rapidly s e Run tim e S e rvice s Infra stru cture S e rvice s t develop and deploy applications to e n Developer r Tanzu Kubernetes Grid Network Storage accelerate digital transformation. On the e vCenter b Service Service Service Server u other hand, IT teams are challenged to K deliver modern infrastructure that Intrinsic Security & Lifecycle Management supports modern container-based application development, including the IT Admin Compute Networking Storage services and tools to build new applications. Deliver Developer- Align Dev Ops and Simplify cloud FIGURE 1: VMware revSpheready infra withstru cTanzuture 2 IT Teams operations Using vSphere 7, customers and ® partners can now deliver a developer- vSphere 7 has beenConfid erearchitectedntial │ ©2020 VMware, Inc. with native Kubernetes to enable IT Admins to use vCenter Server11 ready infrastructure, scale without to operate Kubernetes clusters through namespaces. VMware vSphere with Tanzu allows IT Admins to operate with their existing skillset and deliver a self-service access to infrastructure for the Dev compromise and simplify operations. -
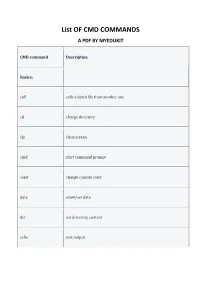
List of CMD COMMANDS a PDF by MYEDUKIT
List OF CMD COMMANDS A PDF BY MYEDUKIT CMD command Description Basics: call calls a batch file from another one cd change directory cls clear screen cmd start command prompt color change console color date show/set date dir list directory content echo text output exit exits the command prompt or a batch file find find files hostname display host name pause pauses the execution of a batch file and shows a message runas start a program as another user shutdown shutdown the computer sort sort the screen output start start an own window to execute a program or command taskkill terminate a process or an application tasklist display applications and related tasks time display/edit the system time timeout wait any time title set title for prompt ver display operating system version w32tm setting time synchronisation/time server/time zone Network: ftp transfer files to an FTP server ftype display file type and mapping getmac display MAC address ipconfig display IP network settings netsh configure/control/display network components netstat display TCP/IP connections and status nslookup query the DNS pathping test the connection to a specific IP address ping pings the network route display network routing table, add static routes systeminfo displays computer-specific properties and configurations telnet establish a Telnet connection tftp transfer files to a TFTP server tracert trace routes similar to patchping Files: attrib display file attributes comp compare file contents compact display/change file compression copy / xcopy copy files diskcomp -

Add-Ons for Red Hat Enterprise Linux
DATASHEET ADD-ONS FOR RED HAT ENTERPRISE LINUX WORKLOAD AND MISSION-CRITICAL PLATFORM ENHANCEMENTS In conjunction with Red Hat® Enterprise Linux®, Red Hat offers a portfolio of Add-Ons to extend the features of your Red Hat Enterprise Linux subscription. Add-Ons to Red Hat Enterprise Linux tailor your application environment to suit your particular computing requirements. With increased flexibility and choice, customers can deploy what they need, when they need it. ADD-ON OPTIONS FOR AVAILABILITY MANAGEMENT High Availability Add-On Red Hat’s High Availability Add-On provides on-demand failover services between nodes within a cluster, making applications highly available. The High Availability Add-On supports up to 16 nodes and may be configured for most applications that use customizable agents, as well as for virtual guests. The High Availability Add-On also includes failover support for off-the-shelf applications like Apache, MySQL, and PostgreSQL. When using the High Availability Add-On, a highly available service can fail over from one node to another with no apparent interruption to cluster clients. The High Availability Add-On also ensures data integrity when one cluster node takes over control of a service from another clus- ter node. It achieves this by promptly evicting nodes from the cluster that are deemed to be faulty using a method called “fencing” that prevents data corruption. www.redhat.com DATASHEET ADD-ONS For RED Hat ENterprise LINUX 6 Resilient Storage Add-On Red Hat’s Resilient Storage Add-On enables a shared storage or clustered file system to access the same storage device over a network. -

Prepare Customer Site Servers
Prepare Customer Site Servers • Prepare Customer Site Servers, on page 1 • Prepare Cisco UCS C-Series Customer Site Servers, on page 1 • Prepare HyperFlex M5 series Customer Site Servers, on page 3 • NTP and Time Synchronization, on page 4 • Global Catalog Requirements, on page 5 Prepare Customer Site Servers Perform all the procedures in this section on the Side A and the Side B servers. Prepare Cisco UCS C-Series Customer Site Servers Configure RAID for C240 M4SX The disk array configuration for the C240 M4SX is already set up to match what is required for Packaged CCE. Verify the settings as follows. Using Cisco Integrated Management Controller, check that the following settings are configured correctly: • Virtual Drive Info: RAID 5 with 5 (Physical Disks) * 4 (Virtual Drives/Datastores) • Stripe Size: 128KB • Write Policy: Write Back with BBU • Read Policy: Read Ahead Always For more information regarding RAID configuration for C240 M4SX in Configure RAID with GUI (UCS C-Series M4 Servers) section, see Cisco Collaboration on Virtual Servers Guide at: https://www.cisco.com/ c/en/us/td/docs/voice_ip_comm/cucm/virtual/CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers/ CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers_chapter_01.html#CUCM_TK_C2DC4F2D_ 00. Prepare Customer Site Servers 1 Prepare Customer Site Servers Run the RAID Config Validator Utility Run the RAID Config Validator Utility After you set up RAID configuration and add the datastores, run the RAID Config Validator utility to ensure that your datastore configuration is correct. Before you begin To run the utility, Java 7 (any update) must be installed. Java 8 and later releases are not supported. -

Survey on Virtualization with Xen Hypervisor
International Journal of Engineering Research & Technology (IJERT) ISSN: 2278-0181 Vol. 1 Issue 8, October - 2012 Survey On Virtualization With Xen Hypervisor Mr.Tejas P.Bhatt*1, Asst.Prof.Pinal.J.Patel#2 * C.S.E. Department, Government College of Engineering, Gandhinagar Gujarat Technology University, Gujarat, India. # C.S.E. Department, Government College of Engineering, Gandhinagar Gujarat Technology University, Gujarat, India Abstract In the cloud computing, there is one virtual machine that need them. For this reason, cloud computing has also can created and put it out on the physical machine with been described as "on-demand computing." The Internet providing the ideas using the hypervisors. So the is utilized as a vehicle but it is not the cloud. Google, Amazon, eBay, etc utilize cloud technologies to provide virtualization technology has limit security capabilities in services via the Internet. The cloud technologies are an order to secure wide area environment such as the cloud. operating technology built on a vast number of computers While consolidating physical to virtual machines using that provide a service [1]. Google as a best example of Xen hypervisor, we want to be able to deploy and manage cloud computing. What happens when you type and virtual machines in the same way we manage and deploy search something on Google? Have you ever thought physical machines. For operators and support people about this? Does your PC go through all that information, there should be no difference between virtual and sorts it out for you and display all the relevant results? IJERTNo, it doesn’t. Otherwise, you would wait much longer physical installations Therefore, the development of a for a simple results page to display. -

Deployment Strategy
System Management Best Practices Bryan S Owen PE Copyright c 2004 OSIsoft Inc. All rights reserved. Richness & Reliability “Value Coefficients” • Quality – Across operations and data systems • Quantity – Across business needs and over time • Utilization – Across enterprise and just in time It all Starts with Great Software …and the Right Architecture • Visualization Tools • Availability • Reliability • Security Integrated Data Collection Proven: Cutting Edge: Integrated Interface Embedded Historian Embedded PI Historian • Continuous Historian for DeltaV Application Station http://www.easydeltav.com/pd/PDS_ApplicationStation.pdf • “56SAM” Historian for Allen-Bradley ControlLogix www.oldi.com • “Promoted” Interface Node • Also visit: www.echohistorian.com Fault Tolerant vs Redundant Incident Tolerant Redundant Environment Fault JJ JJJ Hardware Fault JJJ JJ Software Fault K J Administrative Error JK JJ Scheduled Down K JJJ “Smile” Points: 15/30 22/30 Redundant Architecture • Reliability – Build from the Data Up • Availability – Build from the Users Down You decide what comes first! Redundant Data Collection Dual Gateways Interface Node Failover Redundant Data Service Dual PI Servers Dual PI Clients Redundant Architecture No single point of failure sounds great, what’s the catch? • Interface Support • History Recovery • Gap Filling • Client Impact • Fugitive Data Fugitive Data Capture Essential for rich content but… 1% of the data causes 99% perspiration! • Manual Entry Systems • Custom Applications • Isolated Point to Point Links Solution: -

Integrating Openshift Enterprise with Identity Management (Idm) in Red Hat Enterprise Linux
Integrating OpenShift Enterprise with Identity Management (IdM) in Red Hat Enterprise Linux OpenShift Enterprise 2.2 IdM in Red Hat Enterprise Linux 7 Windows Server 2012 - Active Directory Integration Mark Heslin Principal Systems Engineer Version 1.1 January 2015 1801 Varsity Drive™ Raleigh NC 27606-2072 USA Phone: +1 919 754 3700 Phone: 888 733 4281 Fax: +1 919 754 3701 PO Box 13588 Research Triangle Park NC 27709 USA Linux is a registered trademark of Linus Torvalds. Red Hat, Red Hat Enterprise Linux and the Red Hat "Shadowman" logo are registered trademarks of Red Hat, Inc. in the United States and other countries. Microsoft and Windows are U.S. registered trademarks of Microsoft Corporation. UNIX is a registered trademark of The Open Group. Intel, the Intel logo and Xeon are registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries. All other trademarks referenced herein are the property of their respective owners. © 2014 by Red Hat, Inc. This material may be distributed only subject to the terms and conditions set forth in the Open Publication License, V1.0 or later (the latest version is presently available at http://www.opencontent.org/openpub/). The information contained herein is subject to change without notice. Red Hat, Inc. shall not be liable for technical or editorial errors or omissions contained herein. Distribution of modified versions of this document is prohibited without the explicit permission of Red Hat Inc. Distribution of this work or derivative of this work in any standard (paper) book form for commercial purposes is prohibited unless prior permission is obtained from Red Hat Inc. -

Microsoft Windows Server 2019 Version 1809 Hyper-V
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

Vcenter Server and Host Management
vCenter Server and Host Management 02 APR 2020 Modified on 13 AUG 2020 VMware vSphere 7.0 VMware ESXi 7.0 vCenter Server 7.0 vCenter Server and Host Management You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com © Copyright 2009-2020 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 2 Contents About VMware vCenter Server and Host Management 9 Updated Information 10 1 vSphere Concepts and Features 11 Virtualization Basics 11 Physical Topology of vSphere Data Center 12 vSphere Software Components 13 Client Interfaces for vSphere 16 vSphere Managed Inventory Objects 16 Optional vCenter Server Components 18 vCenter Server Plug-Ins 19 2 Using the vSphere Client 21 Log In to vCenter Server by Using the vSphere Client 22 Use the vSphere Client Navigator 23 Manage Client Plug-Ins 23 Monitor Client Plugins 24 Install the VMware Enhanced Authentication Plug-in 24 Refresh Data 25 Searching the Inventory 25 Perform a Quick Search 26 Save, Run, Rename, and Delete a Search 26 Sort the vSphere Client Inventory 27 Drag Objects 28 Export Lists 28 Attach File to Service Request 29 Keyboard Shortcuts 29 Inventory Keyboard Shortcuts 29 Provide Feedback with the vSphere Client 30 Start, Stop, and Restart Services 30 3 Using Enhanced Linked Mode 32 4 Configuring Hosts in vCenter Server 33 Host Configuration 33 Configure the Boot Device on an ESXi Host 33 Configure Agent VM Settings 34 VMware, Inc. 3 vCenter -

Operational and Administrative Guidance
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious.