Windows Domain and Workgroup Planning Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Introduction to Linear Bialgebra
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by University of New Mexico University of New Mexico UNM Digital Repository Mathematics and Statistics Faculty and Staff Publications Academic Department Resources 2005 INTRODUCTION TO LINEAR BIALGEBRA Florentin Smarandache University of New Mexico, [email protected] W.B. Vasantha Kandasamy K. Ilanthenral Follow this and additional works at: https://digitalrepository.unm.edu/math_fsp Part of the Algebra Commons, Analysis Commons, Discrete Mathematics and Combinatorics Commons, and the Other Mathematics Commons Recommended Citation Smarandache, Florentin; W.B. Vasantha Kandasamy; and K. Ilanthenral. "INTRODUCTION TO LINEAR BIALGEBRA." (2005). https://digitalrepository.unm.edu/math_fsp/232 This Book is brought to you for free and open access by the Academic Department Resources at UNM Digital Repository. It has been accepted for inclusion in Mathematics and Statistics Faculty and Staff Publications by an authorized administrator of UNM Digital Repository. For more information, please contact [email protected], [email protected], [email protected]. INTRODUCTION TO LINEAR BIALGEBRA W. B. Vasantha Kandasamy Department of Mathematics Indian Institute of Technology, Madras Chennai – 600036, India e-mail: [email protected] web: http://mat.iitm.ac.in/~wbv Florentin Smarandache Department of Mathematics University of New Mexico Gallup, NM 87301, USA e-mail: [email protected] K. Ilanthenral Editor, Maths Tiger, Quarterly Journal Flat No.11, Mayura Park, 16, Kazhikundram Main Road, Tharamani, Chennai – 600 113, India e-mail: [email protected] HEXIS Phoenix, Arizona 2005 1 This book can be ordered in a paper bound reprint from: Books on Demand ProQuest Information & Learning (University of Microfilm International) 300 N. -

On Free Quasigroups and Quasigroup Representations Stefanie Grace Wang Iowa State University
Iowa State University Capstones, Theses and Graduate Theses and Dissertations Dissertations 2017 On free quasigroups and quasigroup representations Stefanie Grace Wang Iowa State University Follow this and additional works at: https://lib.dr.iastate.edu/etd Part of the Mathematics Commons Recommended Citation Wang, Stefanie Grace, "On free quasigroups and quasigroup representations" (2017). Graduate Theses and Dissertations. 16298. https://lib.dr.iastate.edu/etd/16298 This Dissertation is brought to you for free and open access by the Iowa State University Capstones, Theses and Dissertations at Iowa State University Digital Repository. It has been accepted for inclusion in Graduate Theses and Dissertations by an authorized administrator of Iowa State University Digital Repository. For more information, please contact [email protected]. On free quasigroups and quasigroup representations by Stefanie Grace Wang A dissertation submitted to the graduate faculty in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY Major: Mathematics Program of Study Committee: Jonathan D.H. Smith, Major Professor Jonas Hartwig Justin Peters Yiu Tung Poon Paul Sacks The student author and the program of study committee are solely responsible for the content of this dissertation. The Graduate College will ensure this dissertation is globally accessible and will not permit alterations after a degree is conferred. Iowa State University Ames, Iowa 2017 Copyright c Stefanie Grace Wang, 2017. All rights reserved. ii DEDICATION I would like to dedicate this dissertation to the Integral Liberal Arts Program. The Program changed my life, and I am forever grateful. It is as Aristotle said, \All men by nature desire to know." And Montaigne was certainly correct as well when he said, \There is a plague on Man: his opinion that he knows something." iii TABLE OF CONTENTS LIST OF TABLES . -

Windows Shell Action Command Library
Windows Shell Action Command Library A Guide to the BigFix® Action Shell Commands BigFix, Inc. Emeryville, CA Last Modified: May 27, 2003 Compatible with BigFix Enterprise Suite (BES) version 3.0 and BigFix Consumer Client version 1.7 ii © 1998–2003 BigFix, Inc. All rights reserved. BigFix®, Fixlet® and "Fix it before it fails"® are registered trademarks of BigFix, Inc. i- prevention, Powered by BigFix, Relevance Engine, and related BigFix logos are trademarks of BigFix, Inc. All other product names, trade names, trademarks, and logos used in this documentation are the property of their respective owners. BigFix’s use of any other company’s trademarks, trade names, product names and logos or images of the same does not necessarily constitute: (1) an endorsement by such company of BigFix and its products, and (2) an endorsement of the company or its products by BigFix. No part of this documentation may be reproduced, transmitted, or otherwise distributed in any form or by any means (electronic or otherwise) without the prior written consent of BigFix, Inc. You may not use this documentation for any purpose except in connection with your use or evaluation of BigFix software and any other use, including for reverse engineering such software or creating compatible software, is prohibited. If the license to the software which this documentation accompanies is terminated, you must immediately return this documentation to BigFix, Inc. and destroy all copies you may have. All inquiries regarding the foregoing should be addressed to: BigFix, Inc. 5915 Hollis Street Emeryville, CA 94608-2017 Copyright © 2003 by BigFix, Inc. -

Administrative Guide for Windows 10 and Windows Server Fall Creators Update (1709)
Operational and Administrative Guidance Microsoft Windows 10 and Windows Server Common Criteria Evaluation for Microsoft Windows 10 and Windows Server Version 1903 (May 2019 Update) General Purpose Operating System Protection Profile © 2019 Microsoft. All rights reserved. Microsoft Windows 10 GP OS Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. No association with any real company, organization, product, person or event is intended or should be inferred. -

The NTFS File System
The NTFS File System OVERVIEW: This lab is part of a series of lab exercises intended to support courseware for Forensics training. The development of this document is funded by the Department of Labor (DOL) Trade Adjustment Assistance Community College and Career Training (TAACCCT) Grant No. TC-22525-11-60-A-48. In this lab, students will enumerate hosts on the network using various tools. This lab includes the following tasks: 1 – Examining the NTFS File System 2 – Using a HEX Editor to explore an NTFS Partition 3 – Verifying and viewing the image details 4 – Analyzing an NTFS Partition With Autopsy Key TermDescription The acronym NTFS stands for New Technology File System. The NTFS File System was originally introduced with the Windows NT. NTFS is a journaling file system which means it keeps a log of changes being written to the disk. If a computer is shutdown improperly, it will have a better NTFS chance of recovery if it has a journaling file system. Files and folder access can be restricted with the security feature of NTFS. Starting with Windows 2000, Microsoft included the Encrypted File System, or EFS, as an NTFS feature. EFS allows users to encrypt files to protect against unauthorized access. A Feature of the NTFS File system that allows you to encrypt files and folders. The feature EFS became available on the NTFS File system starting with Windows 2000, and is still available today on Windows 10 and Server 2016. An Alternate Data Stream, or ADS, is a feature of the NTFS file system that allowed compatibility ADS with older versions of the Mac OS. -

Tokenvator Release 3 Written by Alexander Polce Leary | July 22, 2021 Tokenvator Release 3 Is a Long Overdue Update That Includes a Major Overhaul to the Tool
Tokenvator Release 3 written by Alexander Polce Leary | July 22, 2021 Tokenvator Release 3 is a long overdue update that includes a major overhaul to the tool. From the user interface, it will be mostly familiar with some command line tweaks. Under the surface, large portions of the code base have been reworked, and parts of the base have had some updates. In this series, we will go over some of the changes and new features added. Teaser Alert: Adding Privileges & Creating Tokens Improvements First and foremost, the user interface. Historically, every action had a series of positional arguments that were clunky and generally difficult to remember. They were also not very flexible, and as the commands started to have more, and additional optional arguments, they became completely unwieldy. These have been replaced with flags that will auto complete. For instance, to list and enable privileges: This also works in the non-interactive mode (though it won’t tab complete – sorry, it’s Windows): Additionally, the scroll back function was improved and numerous bugs were resolved. For instance, now when you press up you will always go to the last command issued. A printable command history has also been added if you want to copy and paste instead or keep a log of your actions. The info functionality was improved again, removing many bugs and adding additional information, such as impersonation contexts: (Tokens) > whoami [*] Operating as NT AUTHORITY\SYSTEM (Tokens) > info [*] Primary Token [+] User: S-1-5-21-258464558-1780981397-2849438727-1001 -

Oracle® Database Administrator's Reference
Oracle® Database Administrator's Reference 18c for Microsoft Windows E83889-01 August 2018 Oracle Database Administrator's Reference, 18c for Microsoft Windows E83889-01 Copyright © 1996, 2018, Oracle and/or its affiliates. All rights reserved. Primary Authors: Tanaya Bhattacharjee, Sunil Surabhi, Mark Bauer Contributing Authors: Lance Ashdown Contributors: Alexander Key, Sivaselvam Narayanasamy, Ricky Chen, David Collelo, David Friedman, Prakash Jashnani, Sue K. Lee, Rich Long, Satish Panchumarthy, Ravi Thammaiah, Michael Verheij This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency- specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. -
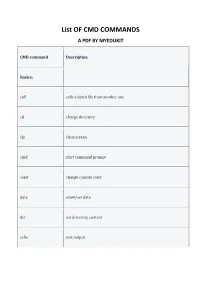
List of CMD COMMANDS a PDF by MYEDUKIT
List OF CMD COMMANDS A PDF BY MYEDUKIT CMD command Description Basics: call calls a batch file from another one cd change directory cls clear screen cmd start command prompt color change console color date show/set date dir list directory content echo text output exit exits the command prompt or a batch file find find files hostname display host name pause pauses the execution of a batch file and shows a message runas start a program as another user shutdown shutdown the computer sort sort the screen output start start an own window to execute a program or command taskkill terminate a process or an application tasklist display applications and related tasks time display/edit the system time timeout wait any time title set title for prompt ver display operating system version w32tm setting time synchronisation/time server/time zone Network: ftp transfer files to an FTP server ftype display file type and mapping getmac display MAC address ipconfig display IP network settings netsh configure/control/display network components netstat display TCP/IP connections and status nslookup query the DNS pathping test the connection to a specific IP address ping pings the network route display network routing table, add static routes systeminfo displays computer-specific properties and configurations telnet establish a Telnet connection tftp transfer files to a TFTP server tracert trace routes similar to patchping Files: attrib display file attributes comp compare file contents compact display/change file compression copy / xcopy copy files diskcomp -

© Iquila Ltd 2018-2019 - 1
Rev-1 Joining a Client PC to a Domain Controller using iQuila Server Setup 1. Install the iQuila client software on your windows domain controller server (please note if you have more than one domain controller, you must install the iQuila client software on each domain controller in your network.) 2. Assign a static IP address to the iQuila virtual network adaptor. (Please see Help Document for using Static IP addresses) 3. Go to Control Panel then select view network status and tasks, select change adaptor settings, right click on the iQuila network adaptor (VPN – VPN Client) and client properties. 4. Select Internet protocol version v (TCP/IPv4) and click properties. Select use the following IP address and enter an IP address in your given range, i.e. 192.168.30.9. Enter your given subnet mask i.e. 255.255.255.0 Leave the default gateway setting blank Under the DNS section select use the preferred DNS server address and enter the same address as you entered for the IP address 192.168.30.9 Click ok to save IP address and click on the exit the adaptor properties window. © iQuila Ltd 2018-2019 - www.iquila.com 1 Client Setup 1. Install the iQuila client software on the client computers that you would like to join to the domain and ensure they have registered with the iQuila Cloud server. 2. You now need to set the DNS server address on the iQuila virtual adaptor or contact iQuila support and request the change of DNS address in your Virtual DHCP Server settings. -

Prepare Customer Site Servers
Prepare Customer Site Servers • Prepare Customer Site Servers, on page 1 • Prepare Cisco UCS C-Series Customer Site Servers, on page 1 • Prepare HyperFlex M5 series Customer Site Servers, on page 3 • NTP and Time Synchronization, on page 4 • Global Catalog Requirements, on page 5 Prepare Customer Site Servers Perform all the procedures in this section on the Side A and the Side B servers. Prepare Cisco UCS C-Series Customer Site Servers Configure RAID for C240 M4SX The disk array configuration for the C240 M4SX is already set up to match what is required for Packaged CCE. Verify the settings as follows. Using Cisco Integrated Management Controller, check that the following settings are configured correctly: • Virtual Drive Info: RAID 5 with 5 (Physical Disks) * 4 (Virtual Drives/Datastores) • Stripe Size: 128KB • Write Policy: Write Back with BBU • Read Policy: Read Ahead Always For more information regarding RAID configuration for C240 M4SX in Configure RAID with GUI (UCS C-Series M4 Servers) section, see Cisco Collaboration on Virtual Servers Guide at: https://www.cisco.com/ c/en/us/td/docs/voice_ip_comm/cucm/virtual/CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers/ CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers_chapter_01.html#CUCM_TK_C2DC4F2D_ 00. Prepare Customer Site Servers 1 Prepare Customer Site Servers Run the RAID Config Validator Utility Run the RAID Config Validator Utility After you set up RAID configuration and add the datastores, run the RAID Config Validator utility to ensure that your datastore configuration is correct. Before you begin To run the utility, Java 7 (any update) must be installed. Java 8 and later releases are not supported. -
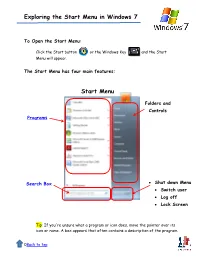
Exploring the Start Menu in Windows 7
Exploring the Start Menu in Windows 7 To Open the Start Menu: Click the Start button or the Windows Key and the Start Menu will appear. The Start Menu has four main features: Start Menu Folders and Controls Programs Shut down Menu Search Box Switch user Log off Lock Screen Tip: If you're unsure what a program or icon does, move the pointer over its icon or name. A box appears that often contains a description of the program. 0Back to top Exploring the Start Menu in Windows 7 Programs (Left Pane of the Start Menu) The programs list includes recently used programs and “Pinned” programs. Click once on a program icon to open it Jump List: If an entry has a black menu arrow, clicking on it will show a “Jump List” of recently opened and Pinned documents. Documents can be opened directly from this list. Jump List Left Click on “All Programs” to show a list of available programs and folders. Organize and move icons by left clicking, then dragging to the desired location. 0Back to top Exploring the Start Menu in Windows 7 Adding or Removing a Program on the Start Menu or Taskbar: Adding or “Pinning” a program on the Start Menu or Taskbar: 1. Find the program icon in the Start Menu, All Programs or Taskbar 2. Right click on the program icon 3. Select “Pin to Taskbar” and/or “Pin to Start Menu” 4. The icon will now be Pinned (stuck) to the selected area. 5. Icons can also be added to the Taskbar from the Start Menu by clicking on the icon in the Start Menu and dragging it to the Taskbar. -
![Arxiv:2011.04704V2 [Cs.LO] 22 Mar 2021 Eain,Bttre Te Opttoal Neetn Oessuc Models Interesting Well](https://docslib.b-cdn.net/cover/8213/arxiv-2011-04704v2-cs-lo-22-mar-2021-eain-bttre-te-opttoal-neetn-oessuc-models-interesting-well-348213.webp)
Arxiv:2011.04704V2 [Cs.LO] 22 Mar 2021 Eain,Bttre Te Opttoal Neetn Oessuc Models Interesting Well
Domain Semirings United Uli Fahrenberg1, Christian Johansen2, Georg Struth3, and Krzysztof Ziemia´nski4 1Ecole´ Polytechnique, Palaiseau, France 2 University of Oslo, Norway 3University of Sheffield, UK 4University of Warsaw, Poland Abstract Domain operations on semirings have been axiomatised in two different ways: by a map from an additively idempotent semiring into a boolean subalgebra of the semiring bounded by the additive and multiplicative unit of the semiring, or by an endofunction on a semiring that induces a distributive lattice bounded by the two units as its image. This note presents classes of semirings where these approaches coincide. Keywords: semirings, quantales, domain operations 1 Introduction Domain semirings and Kleene algebras with domain [DMS06, DS11] yield particularly simple program ver- ification formalisms in the style of dynamic logics, algebras of predicate transformers or boolean algebras with operators (which are all related). There are two kinds of axiomatisation. Both are inspired by properties of the domain operation on binary relations, but target other computationally interesting models such as program traces or paths on digraphs as well. The initial two-sorted axiomatisation [DMS06] models the domain operation as a map d : S → B from an additively idempotent semiring (S, +, ·, 0, 1) into a boolean subalgebra B of S bounded by 0 and 1. This seems natural as domain elements form powerset algebras in the target models mentioned. Yet the domain algebra B cannot be chosen freely: B must be the maximal boolean subalgebra of S bounded by 0 and 1 and equal to the set Sd of fixpoints of d in S. The alternative, one-sorted axiomatisation [DS11] therefore models d as an endofunction on a semiring S that induces a suitable domain algebra on Sd—yet generally only a bounded distributive lattice.