The NTFS File System
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Active@ Boot Disk User Guide Copyright © 2008, LSOFT TECHNOLOGIES INC
Active@ Boot Disk User Guide Copyright © 2008, LSOFT TECHNOLOGIES INC. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without written permission from LSOFT TECHNOLOGIES INC. LSOFT TECHNOLOGIES INC. reserves the right to revise this documentation and to make changes in content from time to time without obligation on the part of LSOFT TECHNOLOGIES INC. to provide notification of such revision or change. LSOFT TECHNOLOGIES INC. provides this documentation without warranty of any kind, either implied or expressed, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. LSOFT may make improvements or changes in the product(s) and/or the program(s) described in this documentation at any time. All technical data and computer software is commercial in nature and developed solely at private expense. As the User, or Installer/Administrator of this software, you agree not to remove or deface any portion of any legend provided on any licensed program or documentation contained in, or delivered to you in conjunction with, this User Guide. LSOFT.NET logo is a trademark of LSOFT TECHNOLOGIES INC. Other brand and product names may be registered trademarks or trademarks of their respective holders. 2 Active@ Boot Disk User Guide Contents 1.0 Product Overview .......................................................................................................... -

Keyboard Shortcuts for Windows Computers
AbilityNet Factsheet – May 2019 Keyboard Shortcuts for Windows computers This factsheet highlights some of the actions you can carry out quickly on your computer by using key combinations rather than using the mouse to navigate menus and options. These key combinations are referred to as shortcuts as they are often a much quicker way of carrying out tasks. They can also be particularly useful for repetitive actions. AbilityNet Factsheet: Keyboard Shortcuts Page 1 of 12 www.abilitynet.org.uk/factsheets May 2019 Contents 1. What are shortcuts ............................................................................................. 3 A note on Apple (Mac) computers ........................................................................... 3 Conventions ............................................................................................................. 3 Navigating Within Windows Using the Keyboard ..................................................... 4 Reference Chart ...................................................................................................... 7 Autocorrect as a shortcut ......................................................................................... 9 2. How can AbilityNet help? ................................................................................. 10 Free advice and home visits .................................................................................. 10 My Computer My Way ........................................................................................... 10 Workplace -

Mac Keyboard Shortcuts Cut, Copy, Paste, and Other Common Shortcuts
Mac keyboard shortcuts By pressing a combination of keys, you can do things that normally need a mouse, trackpad, or other input device. To use a keyboard shortcut, hold down one or more modifier keys while pressing the last key of the shortcut. For example, to use the shortcut Command-C (copy), hold down Command, press C, then release both keys. Mac menus and keyboards often use symbols for certain keys, including the modifier keys: Command ⌘ Option ⌥ Caps Lock ⇪ Shift ⇧ Control ⌃ Fn If you're using a keyboard made for Windows PCs, use the Alt key instead of Option, and the Windows logo key instead of Command. Some Mac keyboards and shortcuts use special keys in the top row, which include icons for volume, display brightness, and other functions. Press the icon key to perform that function, or combine it with the Fn key to use it as an F1, F2, F3, or other standard function key. To learn more shortcuts, check the menus of the app you're using. Every app can have its own shortcuts, and shortcuts that work in one app may not work in another. Cut, copy, paste, and other common shortcuts Shortcut Description Command-X Cut: Remove the selected item and copy it to the Clipboard. Command-C Copy the selected item to the Clipboard. This also works for files in the Finder. Command-V Paste the contents of the Clipboard into the current document or app. This also works for files in the Finder. Command-Z Undo the previous command. You can then press Command-Shift-Z to Redo, reversing the undo command. -

MULTIPLE ACCUDRAW SHORTCUT FILES by Seth M
MULTIPLE ACCUDRAW SHORTCUT FILES By Seth M. Cohen, ProSoft NET Is your MicroStation desktop cluttered with toolframes & toolbars? Are you sacrificing precious desktop real estate because “YOU GOTTA HAVE THAT ICON”? If so, then creating multiple AccuDraw key-in shortcuts will let you reclaim your desktop! What is AccuDraw? According to the MicroStation/J help, “AccuDraw is a drafting aid that evaluates such parameters as your current pointer location, the previously entered data point, the last coordinate directive, the current tool's needs, and any directive you have entered via either keyboard shortcuts or AccuDraw options. AccuDraw then generates the appropriate precision coordinates and applies them to the active tool”. The topic that we will be discussing is AccuDraw shortcuts. ACCUDRAW SHORTCUTS The functionality of AccuDraw shortcuts is to run MicroStation key-in commands. This is accomplished by the user creating a shortcut to a desired key-in by associating two alphanumeric characters to that key-in. Here is an example of how to create an AccuDraw shortcut, and how they can make drafting more efficient, and increase your MicroStation desktop. Wouldn’t it be nice if…….you could turn off the display of, let’s say, 150 reference files without having to: 1) Open the Reference File Dialog box 2) Select all the reference files 3) Click the display toggle on the Reference File Dialog to off 4) Click the Update All icon to refresh the view Well with AccuDraw, you could set two shortcuts to toggle all the reference files on and off. Here’s how: First, we will define two shortcuts that will act like switches. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -
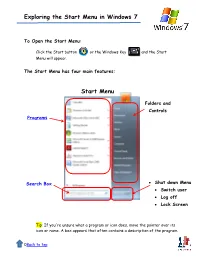
Exploring the Start Menu in Windows 7
Exploring the Start Menu in Windows 7 To Open the Start Menu: Click the Start button or the Windows Key and the Start Menu will appear. The Start Menu has four main features: Start Menu Folders and Controls Programs Shut down Menu Search Box Switch user Log off Lock Screen Tip: If you're unsure what a program or icon does, move the pointer over its icon or name. A box appears that often contains a description of the program. 0Back to top Exploring the Start Menu in Windows 7 Programs (Left Pane of the Start Menu) The programs list includes recently used programs and “Pinned” programs. Click once on a program icon to open it Jump List: If an entry has a black menu arrow, clicking on it will show a “Jump List” of recently opened and Pinned documents. Documents can be opened directly from this list. Jump List Left Click on “All Programs” to show a list of available programs and folders. Organize and move icons by left clicking, then dragging to the desired location. 0Back to top Exploring the Start Menu in Windows 7 Adding or Removing a Program on the Start Menu or Taskbar: Adding or “Pinning” a program on the Start Menu or Taskbar: 1. Find the program icon in the Start Menu, All Programs or Taskbar 2. Right click on the program icon 3. Select “Pin to Taskbar” and/or “Pin to Start Menu” 4. The icon will now be Pinned (stuck) to the selected area. 5. Icons can also be added to the Taskbar from the Start Menu by clicking on the icon in the Start Menu and dragging it to the Taskbar. -

Your Performance Task Summary Explanation
Lab Report: 11.2.5 Manage Files Your Performance Your Score: 0 of 3 (0%) Pass Status: Not Passed Elapsed Time: 6 seconds Required Score: 100% Task Summary Actions you were required to perform: In Compress the D:\Graphics folderHide Details Set the Compressed attribute Apply the changes to all folders and files In Hide the D:\Finances folder In Set Read-only on filesHide Details Set read-only on 2017report.xlsx Set read-only on 2018report.xlsx Do not set read-only for the 2019report.xlsx file Explanation In this lab, your task is to complete the following: Compress the D:\Graphics folder and all of its contents. Hide the D:\Finances folder. Make the following files Read-only: D:\Finances\2017report.xlsx D:\Finances\2018report.xlsx Complete this lab as follows: 1. Compress a folder as follows: a. From the taskbar, open File Explorer. b. Maximize the window for easier viewing. c. In the left pane, expand This PC. d. Select Data (D:). e. Right-click Graphics and select Properties. f. On the General tab, select Advanced. g. Select Compress contents to save disk space. h. Click OK. i. Click OK. j. Make sure Apply changes to this folder, subfolders and files is selected. k. Click OK. 2. Hide a folder as follows: a. Right-click Finances and select Properties. b. Select Hidden. c. Click OK. 3. Set files to Read-only as follows: a. Double-click Finances to view its contents. b. Right-click 2017report.xlsx and select Properties. c. Select Read-only. d. Click OK. e. -

File Permissions Do Not Restrict Root
Filesystem Security 1 General Principles • Files and folders are managed • A file handle provides an by the operating system opaque identifier for a • Applications, including shells, file/folder access files through an API • File operations • Access control entry (ACE) – Open file: returns file handle – Allow/deny a certain type of – Read/write/execute file access to a file/folder by – Close file: invalidates file user/group handle • Access control list (ACL) • Hierarchical file organization – Collection of ACEs for a – Tree (Windows) file/folder – DAG (Linux) 2 Discretionary Access Control (DAC) • Users can protect what they own – The owner may grant access to others – The owner may define the type of access (read/write/execute) given to others • DAC is the standard model used in operating systems • Mandatory Access Control (MAC) – Alternative model not covered in this lecture – Multiple levels of security for users and documents – Read down and write up principles 3 Closed vs. Open Policy Closed policy Open Policy – Also called “default secure” • Deny Tom read access to “foo” • Give Tom read access to “foo” • Deny Bob r/w access to “bar” • Give Bob r/w access to “bar • Tom: I would like to read “foo” • Tom: I would like to read “foo” – Access denied – Access allowed • Tom: I would like to read “bar” • Tom: I would like to read “bar” – Access allowed – Access denied 4 Closed Policy with Negative Authorizations and Deny Priority • Give Tom r/w access to “bar” • Deny Tom write access to “bar” • Tom: I would like to read “bar” – Access -

Windows NT® 4 for Dummies® File:///P|/VSCAN/TOSCAN/MT/NT4DUM/NT4.HTM
Table of contents Windows NT® 4 For Dummies® file:///P|/VSCAN/TOSCAN/MT/NT4DUM/NT4.HTM Table of Contents Windows NT® 4 For Dummies® Introduction About This Book How to Use This Book And What about You? How This Book Is Organized Part I: Introducing Windows NT (Bare-Bones Stuff) Part II: Making Windows NT Do Something Part III: Using Windows NT Applications Part IV: Been There, Done That: Quick References for Moving to Windows NT Part V: Getting Help Part VI: The Part of Tens Icons Used in This Book Where to Go from Here Part I: Intro to Windows NT (Bare Bones Stuff) Chapter 1: What Is Windows NT? What Is This "Windows" Stuff, Anyway? What Does Windows NT 4 Do? Why Should I Bother Using Windows NT? Will I Like Windows NT 4 Better than Windows NT 3.51? What's the Difference between Windows NT Workstation and Windows NT Server? Bracing Yourself for Windows NT 4 Chapter 2: Boring Information, Bothersome Computer Parts The Computer Microprocessor Floppy Disks, Compact Discs (CDs), and Disk Drives Floppy disk flipping What disk drives does Windows NT like? What does "write-protected" mean? Driving with compact discs The Mouse and That Double-Click Stuff Cards and Monitors Keyboards Groups of keys More key principles Print Screen: the one fun, weird code key Modems Printers Networks Sound Cards (Disgusting Bioactive Noises) Parts Required by Windows NT Chapter 3: Windows NT Stuff Everybody Thinks You Already Know Backing Up Your Work Clicking 1 of 9 07/14/99 08:29:14 Table of contents Windows NT® 4 For Dummies® file:///P|/VSCAN/TOSCAN/MT/NT4DUM/NT4.HTM -

The Control Panel and Settings in Windows 10 Most Programs and Apps Have Settings Specific to That Program
GGCS Introduction to Windows 10 Part 3: The Control Panel and Settings in Windows 10 Most programs and apps have settings specific to that program. For example, in a word processor such as Microsoft Word there are settings for margins, fonts, tabs, etc. If you have another word processor, it can have different settings for margins, fonts, etc. These specific settings only affect one program. The settings in the Control Panel and in Settings are more general and affect the whole computer and peripherals such as the mouse, keyboard, monitor and printers. For example, if you switch the right and left buttons on the mouse in the Control Panel or in Settings, they are switched for everything you click on. If you change the resolution of the monitor, it is changed for the desktop, menus, Word, Internet Explorer and Edge, etc. How to display the Control Panel 1. Right-click the Windows Start button or press the Windows key on the keyboard + X. 2. Click “Control Panel” on the popup menu as shown in the first screen capture. In Windows 10, many of the settings that once were in the Control Panel have moved to Settings. However, there are often links in Settings that take you back to the Control Panel and many other settings that still only exist in the Control Panel. Settings versus Control Panel is an evolving part of Windows design that started with Windows 8. It is not clear at this time whether the Control Panel will eventually go away or whether it will simply be used less frequently by most users. -

Students,Faculty & Staff Guide for Windows 7
iM Students,Faculty & Staff Guide for Windows 7 Prepared by Information Technology Division Lehman College, CUNY March 22, 2014 This document was originally prepared by Dickinson College. It was modified and adapted for use at Lehman College with the permission of Dickinson College. Introduction to Windows 7 Table of Contents Windows 7 Taskbar ...................................................................................................................................... 2 Show Desktop ............................................................................................................................................... 2 Start Menu..................................................................................................................................................... 3 Pin ................................................................................................................................................................. 4 Jump Lists ..................................................................................................................................................... 4 Snap .............................................................................................................................................................. 5 Windows Search ........................................................................................................................................... 6 Library (the new My Documents area & more) ........................................................................................... -

How to Open Control Panel in Windows 10 Way 1: Open It in the Start Menu
Course Name : O Level(B4-Ist sem.) Subject : ITT&NB Topic : Control Panel Date : 27-03-20 Control Panel The Control Panel is a component of Microsoft Windows that provides the ability to view and change system settings. It consists of a set of applets that include adding or removing hardware and software, controlling user accounts, changing accessibility options, and accessing networking settings. How to open Control Panel in Windows 10 Way 1: Open it in the Start Menu. Click the bottom-left Start button to open the Start Menu, type control panel in the search box and select Control Panel in the results. Way 2: Access Control Panel from the Quick Access Menu. Press Windows+X or right-tap the lower-left corner to open the Quick Access Menu, and then choose Control Panel in it. Way 3: Go to Control Panel through the Settings Panel. Open the Settings Panel by Windows+I, and tap Control Panel on it. Way 4: Open Control Panel in the File Explorer. Click the File Explorer icon on the taskbar, select Desktop and double-tap Control Panel. Way 5: Open the program via Run. Press Windows+R to open the Run dialog, enter control panel in the empty box and click OK. Changing System Date and Time Step 1: Click the bottom-right clock icon on the taskbar, and select Date and time settings. Or we can right click the clock icon, click Adjust data /time. Step 2: As the Date and time Windows opens, we can turn off Set time automatically. Step 3: In the Date and Time Settings window, respectively change date and time, and then tap OK to confirm the changes.