Summarizing Software Artifacts: a Case Study of Bug Reports
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Install Tani Software
Install Tani Software Windows Under Windows all software comes with an installer which is an executable program. You can start it directly. If You update an installed Tani product it will uninstall the previous version automatically and replaces it with the actual one. All user configuration setting will be preserved. A reboot will be requested in these conditions: The running software can not be stopped. This may be true if an other running program uses the software. Some parts of the software can not be removed because other software holds them open. A program uses the directory holding the software. A hint: If You uninstall the software separately and try installing them again it will request a reboot always. Optionally you can ignore the reboot request. This is always at your own risk. Possibly required files can not be installed. The installed software may not work as expected. Why a reboot is required after uninstall: The uninstall program can not be deleted by itself because it runs. Windows uses random generated file names in this registry key. So the installer cannot check if the reboot will be required or is optional. The installation depending on your Windows patch level may start its internal update. This does not relay on software from Tani GmbH. If Windows will request updates it will do so. During the Windows update an internet connection is required. The installation process will need additional time until the update is finished. More information is available in the Windows Update. For special envoronments it can be necessary running the OPC server or the PLC Engine not as a Windows service. -
Debian 1 Debian
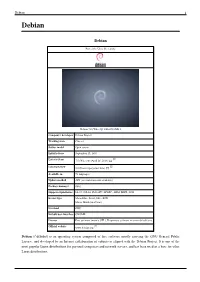
Debian 1 Debian Debian Part of the Unix-like family Debian 7.0 (Wheezy) with GNOME 3 Company / developer Debian Project Working state Current Source model Open-source Initial release September 15, 1993 [1] Latest release 7.5 (Wheezy) (April 26, 2014) [±] [2] Latest preview 8.0 (Jessie) (perpetual beta) [±] Available in 73 languages Update method APT (several front-ends available) Package manager dpkg Supported platforms IA-32, x86-64, PowerPC, SPARC, ARM, MIPS, S390 Kernel type Monolithic: Linux, kFreeBSD Micro: Hurd (unofficial) Userland GNU Default user interface GNOME License Free software (mainly GPL). Proprietary software in a non-default area. [3] Official website www.debian.org Debian (/ˈdɛbiən/) is an operating system composed of free software mostly carrying the GNU General Public License, and developed by an Internet collaboration of volunteers aligned with the Debian Project. It is one of the most popular Linux distributions for personal computers and network servers, and has been used as a base for other Linux distributions. Debian 2 Debian was announced in 1993 by Ian Murdock, and the first stable release was made in 1996. The development is carried out by a team of volunteers guided by a project leader and three foundational documents. New distributions are updated continually and the next candidate is released after a time-based freeze. As one of the earliest distributions in Linux's history, Debian was envisioned to be developed openly in the spirit of Linux and GNU. This vision drew the attention and support of the Free Software Foundation, who sponsored the project for the first part of its life. -

Active@ Livecd User Guide Copyright © 1999-2015, LSOFT TECHNOLOGIES INC
Active@ LiveCD User Guide Copyright © 1999-2015, LSOFT TECHNOLOGIES INC. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without written permission from LSOFT TECHNOLOGIES INC. LSOFT TECHNOLOGIES INC. reserves the right to revise this documentation and to make changes in content from time to time without obligation on the part of LSOFT TECHNOLOGIES INC. to provide notification of such revision or change. LSOFT TECHNOLOGIES INC. provides this documentation without warranty of any kind, either, implied or expressed, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. LSOFT may make improvements or changes in the product(s) and/or the program(s) described in this documentation at any time. All technical data and computer software is commercial in nature and developed solely at private expense. As the User, or Installer/Administrator of this software, you agree not to remove or deface any portion of any legend provided on any licensed program or documentation contained in, or delivered to you in conjunction with, this User Guide. LSOFT.NET logo is a trademark of LSOFT TECHNOLOGIES INC. Other brand and product names may be registered trademarks or trademarks of their respective holders. 2 Active@ LiveCD User Guide Contents 1 Product Overview................................................................................................................ 4 1.1 About Active@ LiveCD .................................................................................................. 4 1.2 Requirements for Using Active@ Boot Disk .................................................................... 6 1.3 Downloading and Creating Active@ LiveCD.................................................................... 6 1.4 Booting from a CD, DVD or USB Media ......................................................................... -

Linux – Das Umfassende Handbuch 1.430 Seiten, Gebunden, Mit CD, 14
Know-howWissen, wie’s für geht. Kreative. Leseprobe In dieser Leseprobe erhalten Sie einen Einstieg in die Linux-Welt und erfahren, wie Sie Audio und Video unter Linux nutzen. Dar- über hinaus lernen Sie die Kommandozentrale kennen: die Shell. Außerdem können Sie einen Blick in das vollständige Inhalts- und Stichwortverzeichnis des Buches werfen. »Was ist Linux?« »Installationsgrundlagen« »Audio und Video« »Die Shell« »Software- und Paketverwaltung« Inhaltsverzeichnis Index Der Autor Leseprobe weiterempfehlen Michael Kofler Linux – Das umfassende Handbuch 1.430 Seiten, gebunden, mit CD, 14. Auflage 2015 49,90 Euro, ISBN 978-3-8362-3775-8 www.rheinwerk-verlag.de/3855 “buch” — 2015/11/5 — 21:54 — page 25 — #19 1 Kapitel 1 Was ist Linux? Um die einleitende Frage zu beantworten, erkläre ich in diesem Kapitel zuerst einige wichtige Begriffe, die im gesamten Buch immer wieder verwendet werden: Betriebs- system, Unix, Distribution, Kernel etc. Ein knapper Überblick über die Merkmale von Linux und die verfügbaren Programme macht deutlich, wie weit die Anwendungs- möglichkeiten von Linux reichen. Es folgt ein kurzer Ausflug in die Geschichte von Linux: Sie erfahren, wie Linux entstanden ist und auf welchen Komponenten es basiert. Von zentraler Bedeutung ist dabei natürlich die General Public License (kurz GPL), die angibt, unter welchen Bedingungen Linux weitergegeben werden darf. Erst die GPL macht Linux zu einem freien System, wobei »frei« mehr heißt als einfach »kostenlos«. 1.1 Einführung Linux ist ein Unix-ähnliches Betriebssystem. Der wichtigste Unterschied gegenüber historischen Unix-Systemen besteht darin, dass Linux zusammen mit dem vollstän- digen Quellcode frei kopiert werden darf. Ein Betriebssystem ist ein Bündel von Programmen, mit denen die grundlegend- Betriebssystem sten Funktionen eines Rechners realisiert werden: die Schnittstelle zwischen Mensch und Maschine (also konkret: die Verwaltung von Tastatur, Bildschirm etc.) und die Verwaltung der Systemressourcen (CPU-Zeit, Speicher etc.). -

Install Gnome Software Center Arch
Install gnome software center arch Upstream URL: License(s): GPL2. Maintainers: Jan Steffens. Package Size: MB. Installed Size: Installed Size: MB. gnome-software will be available as a preview in It can install, remove applications on systems with PackageKit. It can install updates on Gnome software will not start / Applications & Desktop. A quick video on Gnome Software Center in Arch Linux. Gnome unstable repository. There is a component called Polkit that is used by many applications to request root permissions to do things (it can do so because it's a. GNOME Software on #archlinux with native PackageKit backend, and this is a gui for installing software, ala ubuntu software manager, but distro This is some kind of Ubuntu Software Centre, with comments and all that. Need help installing Gnome Software Center for Arch Linux? Here are some instructions: Click DOWNLOAD HERE in the menu. Download the file. Make the file. I had to install it with along with packagekit. This is what's missing to make Antergos *the* beginner-friendly Arch-based distro, or general So, it is not a bad idea for the “Gnome Software Center” to include by default. GNOME software software center graphic that we will find the default in future releases of Fedora in addition to being installed in Arch Linux Please help me to install GNOME Software on. GNOME Software Will Work On Arch Linux With PackageKit the Alpm/Pacman back-end for using this GNOME application to install and. From: Sriram Ramkrishna ; To: desktop-devel-list devel-list gnome org>; Subject: gnome- software/packagekit. -

Volume 2, Issue 02
The *Nixed Report Issue 02 Unix and Overlooked Pop Culture April 2013 Table of Contents ./ This issue's ./ column talks about getting computers on the cheap or even free in some cases. (P. 3) Unix The Computers Are Multiplying: Toshiba Satellite L305-S5921, (P. 5) A new computer has been added to the tech family at The *Nixed Report. This Toshiba notebook will allow for more in depth reviews of operating systems, such as openSUSE 12.3 Distro Journey Series: openSUSE 12.3 (P. 6) In light of the recent controversy regarding Ubuntu, the question that comes to mind is what else is out there regarding a computer's OS? In this issue, Thomas takes a look at the ins and outs of openSUSE 12.3. Overlooked Pop Culture Book Review: 1984 (P. 11) The world seems to be filled with surveillance these days. In 1949, George Orwell published a book that was so popular, it became a movie and was used by Apple in order to portray IBM as Big Brother. Thomas reviews the book that partially predicted a surveillance society inside of a police state. Staff Profile: Stephen Kelley (P. 14) Stephen is the intellectual amplifier of the official podcast. Going above and beyond, he finds extra content to supplement the topics that are discussed, which is why he is featured in this issue's Staff Profile. ./ Obtaining Tech on the Cheap or Free of Charge By Thomas Holbrook II Window shopping for computers or gadgets can be fun, yet depressing. The price tags often prevent many from being able to obtain what they truly desire. -

Cutelyst Usando Qt Na
CUTELYST USANDO QT NA WEB Daniel Nicoletti – INDRA [email protected] GET /HELLO 200 ok Daniel Nicoletti Bacharel em Ciência da Computaç ão pelo UNASP em 2007 Há mais de 10 anos desenvolvento aplicaç ões C++ com Qt e KDE frameworks. Autor de projetos como Apper, print-manager, colord-kde, packagekit-qt, aptcc, debconf-kde dentre outros que não deram muito certo :( E contribuiç ões para QtMultimedia, QtWayland, Kernel Linux, networkmanager-qt, polkit-kde, Grantlee, dentre outros que já não lembro :) POR QUE MAIS UM FRAMEWORK!? 2008 Django ganhando popularidade no mundo Python ▸ API mudava a cada release ▸ Feito em Python Ruby on Rails surfando na onda da popularidade do Twitter ▸ Lento ▸ Absurdamente simples para problemas simples, mas imposível para problemas complexos Perl Catalyst ▸ Mais rápido que ROR ▸ Simples, elegante “2013 Retomar um projeto Catalyst, parado há anos. Falta de experiencia com CPAN, Perl e técnicas de depuração de código Perl TIVE UMA IDÉIA Usar as informaç ões obtidas pelo MOC através do QtMetaObject para simular, as definiç ões de a ç ões do Catalyst Catalyst sub users :Path(“” usuarios ) :Args(0) { my ($self, $c) = @_; … } Cutelyst C_ATTR(users, :Path(“” usuarios ) :Args(0)) void users(Context *c) { … } C_ATTR macro expande para Q_CLASSINFO e Q_INVOKABLE expondo a informaç ão e o método seguinte no QMetaObject do Controller. Apesar do Catalyst ser MVC, o Cutelyst atualmente é apenas VC ▸ Model no Catalyst é a fonte de Dados, DBiX, Sql, NoSql. ▸ A informaç ão do model normalmente é manualmente colocada na stash() ▸ Em C++ precisamos conhecer as Classes para chamar os metodos, para isso podemos ter uma classe abstrata Controllers São as classes que contém a lógica da sua applicaç ão: ▸ Obter dados Sql ▸ Escolher a view a ser usada Views ▸ Verificar autenticaç ão São as classes ▸ Fazer cálculos responsaveis por formatar ▸ Chamar API exerna.. -
Linux for Hams Class #2
Linux For Hams Class #2 Orv Beach W6BI Training Chair Southern California Linux Expo Training Plan – Class #2 Some command line basics How to add third-party repositories How to install updates How install new packages (programs) An overview of KDE Plasma (the UI) Command Line Basics Copy & Paste in a GUI Copy – ctl-c; or right-click, Copy Cut – ctl- x; or right-click, Cut Paste – ctl-v; or right-click, Paste Command Line Basics Copy & Paste on the command line Two methods Windows-ish Unix method Can mix both methods – very useful! Copy & Paste - On the command line Windows-ish method : Copy – Highlight, right-click, select Copy or: ctl-Shift-c Cut – N/A Paste – right-click, select Paste or: ctl-Shift-v Copy & Paste - On the command line Unix method Copy – Highlight Cut – N/A Paste – Click cursor (left mouse click) where you want to paste Center-mouse click to paste That's it! Command Line Basics Same across almost all Linux distros ✷remember – case CoUnTs! su / su - <enter> pwd (print working dir) <password> date exit man <command> (q to quit) cd <dirpath> touch <filename> rm <filename> less <filename>(q to quit) mkdir <dirname> yum (or dnf) <command> rmdir <dirname>* <package> ssh <hostname or ip locate <filename> address> which <program> Text Editors GUI, TUI*, CLI GUI: kate (not installed by default) gedit (not installed by default) TUI: joe (not installed by default) nedit (not installed by default) CLI vi / vim Emacs *Text-based User Interface Adding Repositories (RPM Fusion) http://rpmfusion.org/ How to enable repository GUI Follow instructions on web page for both free & non-free repositories CLI Copy & paste one command from web page to console! How to Install Updates Graphical – click on the gear: Command line: yum (or dnf) update How to Install Packages Graphical – use Apper How to Install Packages Graphical – use Apper How to Install Packages Graphical – use Apper How to Install Packages Command line yum / dnf install <packagename> <second_packagename>.. -
Debian-Paketmanagement
Debian-Paketmanagement Axel Beckert und Frank Hofmann Onyx Neon Debian-Paketmanagement ii Copyright © 2012, 2013, 2014, 2015, 2016, 2017, 2018, 2019, 2020, 2021 Axel Beckert, Frank Hofmann Das Buch "Debian-Paketmanagement" von Frank Hofmann und Axel Beckert ist lizenziert unter einer Creative Commons Na- mensnennung - Weitergabe unter gleichen Bedingungen 4.0 International Lizenz. Debian-Paketmanagement iii VERSIONSGESCHICHTE NUMMER DATUM BESCHREIBUNG NAME debian/0_2021.03.01- 2021-09- 42-g5ca0d33 17T23:18:06+00:00 Debian-Paketmanagement iv Inhaltsverzeichnis I Konzepte 1 1 Willkommen im Linux-Dschungel! 2 1.1 Was ist Debian?....................................................2 1.2 Debian-Architekturen.................................................3 1.2.1 Debian-Ports-Projekt.............................................3 1.2.2 Pakete für alle Architekturen.........................................4 1.2.3 Multiarch: Mehrere Architekturen gleichzeitig auf einem System......................4 1.2.4 Bevor es Multiarch gab............................................5 1.3 Vom tar.gz zur Linux-Distribution........................................5 1.4 Debians Paketsystem.................................................5 1.5 Welche UNIX-artigen Betriebssysteme verwenden das Paketformat und das APT-Paketmanagement.......6 2 Software in Paketen organisieren 7 2.1 Was ist Paketmanagement...............................................7 2.2 Varianten und Formate für Softwarepakete......................................8 2.3 Softwarestapel und Ebenen..............................................9 -

Active@ Killdisk User Guide Copyright © 1999-2015, LSOFT TECHNOLOGIES INC
Active@ KillDisk User Guide Copyright © 1999-2015, LSOFT TECHNOLOGIES INC. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without written permission from LSOFT TECHNOLOGIES INC. LSOFT TECHNOLOGIES INC. reserves the right to revise this documentation and to make changes in content from time to time without obligation on the part of LSOFT TECHNOLOGIES INC. to provide notification of such revision or change. LSOFT TECHNOLOGIES INC. provides this documentation without warranty of any kind, either implied or expressed, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. LSOFT may make improvements or changes in the product(s) and/or the program(s) described in this documentation at any time. All technical data and computer software is commercial in nature and developed solely at private expense. As the User, or Installer/Administrator of this software, you agree not to remove or deface any portion of any legend provided on any licensed program or documentation contained in, or delivered to you in conjunction with, this User Guide. Active@ KillDisk, the Active@ KillDisk logo, KillDisk and Erasers Software are trademarks of LSOFT TECHNOLOGIES INC. The LSOFT.NET logo is a trademark of LSOFT TECHNOLOGIES INC. Other brand and product names may be registered trademarks or trademarks of their respective holders. 2 Active@ KillDisk User Guide Contents 1. Product Overview .................................................................................................................... 4 1.1 Erasing Confidential Data ................................................................................................... 4 1.2 Wiping Confidential Data from Unoccupied Disk’s Space ................................................... -

Opensuse Linux 12.1 Klaus Schmidt Systembetreuer 1
openSUSE Linux 12.1 Klaus Schmidt Systembetreuer 1. Ausgabe, 1. Aktualisierung, April 2014 LI12S I openSUSE Linux 12.1 - Systembetreuer Hinzufügen und Konfiguration von Grundlagen Hardware und Software 1 Informationen zu diesem Buch .................. 4 6 YaST bedienen .......................................... 52 1.1 Voraussetzungen und Ziele ............................ 4 1.2 Aufbau und Konventionen ............................ 4 6.1 Das YaST-Kontrollzentrum starten .............. 52 6.2 Die Online-Aktualisierung ........................... 53 6.3 Die weiteren Kategorien des YaST- Kontrollzentrums ......................................... 57 2 Linux-Grundlagen ........................................ 6 6.4 Die YaST-Kategorie für Sicherheit und 2.1 Linux und UNIX - Entstehung und Benutzer ....................................................... 61 Geschichte ....................................................... 6 6.5 Übung ........................................................... 65 2.2 Aufbau des Linux-Systems .............................. 9 2.3 Unterschiede zu Windows ............................ 13 2.4 Technische Konzepte eines UNIX-Systems ... 15 7 Bootmanager und Start von 2.5 Benutzer unter Linux .................................... 17 Systemdiensten konfigurieren ................ 66 2.6 Behindertengerechte Funktionen bzw. 7.1 Technische Hintergründe des Barrierefreiheit ............................................. 18 Bootprozesses ............................................... 66 2.7 Die geänderten SI-Maßeinheiten................ -

Tobii Dynavox I-Series Brukerhåndbok I–13 I–16 Brukerhåndbok Tobii Dynavox I-Series Versjon 1.0.1 12/2019 Med Enerett
Tobii Dynavox I-Series Brukerhåndbok I–13 I–16 Brukerhåndbok Tobii Dynavox I-Series Versjon 1.0.1 12/2019 Med enerett. Copyright © Tobii AB (publ) Ingen deler av dette dokumentet får reproduseres, lagres i en database eller deles i noen form eller på noen måte (elektronisk, ved fotokopiering, innspilling eller annet) uten skriftlig tillatelse fra utgiveren. Den angitte opphavsretten inkluderer ethvert format og alle deler av det opphavsrettslig beskyttede materialet, og in- formasjon som måtte være tillatt under nåværende gjel- dende lov eller heretter vedtatt, inkludert, men ikke begrenset til, materiale som er basert på programvare som vises på skjermen, som skjermbilder, menyer, etc.. Informasjonen i dette dokumentet tilhører Tobii Dynavox. Det er forbudt å gjengi deler av eller hele innholdet uten skriftlig forhåndstillatelse fra Tobii Dynavox. Produkter som refereres til i dette dokumentet kan være varemerker og/eller registrerte varemerker. Utgiver og for- fatter har ikke krav på disse varemerkene. Alle forholdsregler er tatt ved utarbeidelse av dette doku- mentet, og utgiver og forfatter tar ikke ansvar for feil eller mangler, eller for skader som oppstår som resultat av bruk av informasjon i dette dokumentet, eller av bruk av pro- grammer som eventuelt følger med. Utgiver og forfatter skal på ingen måte holdes ansvarlig for profittap eller an- dre kommersielle skader som oppstår eller påstås å opp- stå direkte eller indirekte på grunn av dette dokumentet. Innholdet kan endres uten varsel. Gå til nettstedet til Tobii Dynavox på www.TobiiDynavox.com for å få oppdaterte versjoner av dette dokumentet. Kontaktinformasjon: Tobii Dynavox AB Tobii Dynavox LLC Karlsrovägen 2D 2100 Wharton Street, Suite 182 53 Danderyd 400 Sverige Pittsburgh, PA 15203 USA +46 8 663 69 90 +1-800-344-1778 De følgende produktene er beskyttet av de amerikanske patentene 7,572,008, 6,659,611, 8,185,845 og 9,996,159: ● I–13 ● I–16 Du finner hvilken type Tobii Dynavox I-Series-enhet du har på etiketten på baksiden.