Linux PHRASEBOOK
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Usask Open Textbook Authoring Guide – Ver.1.0
USask Open Textbook Authoring Guide – Ver.1.0 USask Open Textbook Authoring Guide – Ver.1.0 A Guide to Authoring & Adapting Open Textbooks at the University of Saskatchewan Distance Education Unit (DEU), University of Saskatchewan Jordan Epp, M.Ed., Kristine Dreaver-Charles, M.Sc.Ed., Jeanette McKee, M.Ed. Open Press DEU, Usask Saskatoon Copyright:2016 by Distance Education Unit, University of Saskatchewan. This book is an adaptation based on the B.C. Open Textbook Authoring Guide created by BCcampus and licensed with a CC-BY 4.0 license. Changes to the BCcampus Authoring Guide for this University of Saskatchewan adaptation included: Changing the references from BCcampus Open Project to be more relevant to the University of Saskatchewan’s open textbook development. Creation of a new title page and book title. Changing information about Support Services to be University of Saskatchewan specific. Performing a general text edit throughout the guide, added image captions, and updated most images to remove the BCcampus branding. Updating Pressbook platform nomenclature to be consistent with the current version of Pressbooks. Unless otherwise noted, this book is released under a Creative Commons Attribution (CC-BY) 4.0 Unported license. Under the terms of the CC-BY license you can freely share, copy or redistribute the material in any medium or format, or adapt the material by remixing, transforming or modifying this material providing you attribute the Distance Education Unit, University of Saskatchewan and BCcampus. Attribution means you must give appropriate credit to the Distance Education Unit, University of Saskatchewan and BCcampus as the original creator, note the CC-BY license this document has been released under, and indicate if you have made any changes to the content. -

Tuto Documentation Release 0.1.0
Tuto Documentation Release 0.1.0 DevOps people 2020-05-09 09H16 CONTENTS 1 Documentation news 3 1.1 Documentation news 2020........................................3 1.1.1 New features of sphinx.ext.autodoc (typing) in sphinx 2.4.0 (2020-02-09)..........3 1.1.2 Hypermodern Python Chapter 5: Documentation (2020-01-29) by https://twitter.com/cjolowicz/..................................3 1.2 Documentation news 2018........................................4 1.2.1 Pratical sphinx (2018-05-12, pycon2018)...........................4 1.2.2 Markdown Descriptions on PyPI (2018-03-16)........................4 1.2.3 Bringing interactive examples to MDN.............................5 1.3 Documentation news 2017........................................5 1.3.1 Autodoc-style extraction into Sphinx for your JS project...................5 1.4 Documentation news 2016........................................5 1.4.1 La documentation linux utilise sphinx.............................5 2 Documentation Advices 7 2.1 You are what you document (Monday, May 5, 2014)..........................8 2.2 Rédaction technique...........................................8 2.2.1 Libérez vos informations de leurs silos.............................8 2.2.2 Intégrer la documentation aux processus de développement..................8 2.3 13 Things People Hate about Your Open Source Docs.........................9 2.4 Beautiful docs.............................................. 10 2.5 Designing Great API Docs (11 Jan 2012)................................ 10 2.6 Docness................................................. -

Markdown Markup Languages What Is Markdown? Symbol
Markdown What is Markdown? ● Markdown is a lightweight markup language with plain text formatting syntax. Péter Jeszenszky – See: https://en.wikipedia.org/wiki/Markdown Faculty of Informatics, University of Debrecen [email protected] Last modified: October 4, 2019 3 Markup Languages Symbol ● Markup languages are computer languages for annotating ● Dustin Curtis. The Markdown Mark. text. https://dcurt.is/the-markdown-mark – They allow the association of metadata with parts of text in a https://github.com/dcurtis/markdown-mark clearly distinguishable way. ● Examples: – TeX, LaTeX https://www.latex-project.org/ – Markdown https://daringfireball.net/projects/markdown/ – troff (man pages) https://www.gnu.org/software/groff/ – XML https://www.w3.org/XML/ – Wikitext https://en.wikipedia.org/wiki/Help:Wikitext 2 4 Characteristics Usage (2) ● An easy-to-read and easy-to-write plain text ● Collaboration platforms and tools: format that. – GitHub https://github.com/ ● Can be converted to various output formats ● See: Writing on GitHub (e.g., HTML). https://help.github.com/en/categories/writing-on-github – Trello https://trello.com/ ● Specifically targeted at non-technical users. ● See: How To Format Your Text in Trello ● The syntax is mostly inspired by the format of https://help.trello.com/article/821-using-markdown-in-trell o plain text email. 5 7 Usage (1) Usage (3) ● Markdown is widely used on the web for ● Blogging platforms and content management entering text. systems: – ● The main application areas include: Ghost https://ghost.org/ -

Mysql and Linux/Unix Abstract
MySQL and Linux/Unix Abstract This is the MySQL Linux extract from the MySQL 5.6 Reference Manual. For legal information, see the Legal Notices. For help with using MySQL, please visit the MySQL Forums, where you can discuss your issues with other MySQL users. Document generated on: 2021-09-23 (revision: 70881) Table of Contents Preface and Legal Notices ............................................................................................................ v 1 Installing MySQL on Unix/Linux Using Generic Binaries ............................................................... 1 2 Installing MySQL on Linux ......................................................................................................... 5 2.1 Installing MySQL on Linux Using the MySQL Yum Repository ........................................... 6 2.2 Replacing a Third-Party Distribution of MySQL Using the MySQL Yum Repository .............. 9 2.3 Installing MySQL on Linux Using the MySQL APT Repository ......................................... 11 2.4 Installing MySQL on Linux Using the MySQL SLES Repository ....................................... 11 2.5 Installing MySQL on Linux Using RPM Packages from Oracle ......................................... 12 2.6 Installing MySQL on Linux Using Debian Packages from Oracle ...................................... 15 2.7 Installing MySQL on Linux from the Native Software Repositories .................................... 16 2.8 Deploying MySQL on Linux with Docker ....................................................................... -

The R Journal Volume 4/2, December 2012
The Journal Volume 4/2, December 2012 A peer-reviewed, open-access publication of the R Foundation for Statistical Computing Contents Editorial . .3 Contributed Research Articles What’s in a Name? . .5 It’s Not What You Draw, It’s What You Don’t Draw . 13 Debugging grid Graphics . 19 frailtyHL: A Package for Fitting Frailty Models with H-likelihood . 28 influence.ME: Tools for Detecting Influential Data in Mixed Effects Models . 38 The crs Package: Nonparametric Regression Splines for Continuous and Categorical Predic- tors.................................................... 48 Rfit: Rank-based Estimation for Linear Models . 57 Graphical Markov Models with Mixed Graphs in R . 65 Programmer’s Niche The State of Naming Conventions in R . 74 News and Notes Changes in R . 76 Changes on CRAN . 80 News from the Bioconductor Project . 101 R Foundation News . 102 2 The Journal is a peer-reviewed publication of the R Foun- dation for Statistical Computing. Communications regarding this pub- lication should be addressed to the editors. All articles are licensed un- der the Creative Commons Attribution 3.0 Unported license (CC BY 3.0, http://creativecommons.org/licenses/by/3.0/). Prospective authors will find detailed and up-to-date submission in- structions on the Journal’s homepage. Editor-in-Chief: Martyn Plummer Editorial Board: Heather Turner, Hadley Wickham, and Deepayan Sarkar Editor Help Desk: Uwe Ligges Editor Book Reviews: G. Jay Kerns Department of Mathematics and Statistics Youngstown State University Youngstown, Ohio 44555-0002 USA [email protected] R Journal Homepage: http://journal.r-project.org/ Email of editors and editorial board: [email protected] The R Journal is indexed/abstracted by EBSCO, DOAJ, Thomson Reuters. -

Red Hat Developer Toolset 9 User Guide
Red Hat Developer Toolset 9 User Guide Installing and Using Red Hat Developer Toolset Last Updated: 2020-08-07 Red Hat Developer Toolset 9 User Guide Installing and Using Red Hat Developer Toolset Zuzana Zoubková Red Hat Customer Content Services Olga Tikhomirova Red Hat Customer Content Services [email protected] Supriya Takkhi Red Hat Customer Content Services Jaromír Hradílek Red Hat Customer Content Services Matt Newsome Red Hat Software Engineering Robert Krátký Red Hat Customer Content Services Vladimír Slávik Red Hat Customer Content Services Legal Notice Copyright © 2020 Red Hat, Inc. The text of and illustrations in this document are licensed by Red Hat under a Creative Commons Attribution–Share Alike 3.0 Unported license ("CC-BY-SA"). An explanation of CC-BY-SA is available at http://creativecommons.org/licenses/by-sa/3.0/ . In accordance with CC-BY-SA, if you distribute this document or an adaptation of it, you must provide the URL for the original version. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. -

Chapter 7 Package Management
Chapter 7 Package Management CERTIFICATION OBJECTIVES 7.01 The Red Hat Package Manager ✓ Two-Minute Drill 7.02 More RPM Commands Q&A Self Test 7.03 Dependencies and the yum Command 7.04 More Package Management Tools fter installation is complete, systems are secured, filesystems are configured, and other initial setup tasks are completed, you still have work to do. Almost certainly before your system is in the state you desire, you will be required to install or remove packages. To make sure the right updates are installed, you need to know how to get a system working with ARed Hat Subscription Management (RHSM) or the repository associated with a rebuild distribution. To accomplish these tasks, you need to understand how to use the rpm and yum commands in detail. Although these are “just” two commands, they are rich in detail. Entire books have been dedicated to the rpm command, such as the Red Hat RPM Guide by Eric 344 Chapter 7 Package Management Foster-Johnson. For many, that degree of in-depth knowledge of the rpm command is no longer necessary, given the capabilities of the yum command and the additional package management tools provided in RHEL 7. CERTIFICATION OBJECTIVE 7.01 The Red Hat Package Manager One of the major duties of a system administrator is software management. New applications are installed. Services are updated. Kernels are patched. Without the right tools, it can be difficult to figure out what software is on a system, what is the latest update, and what applications depend on other software. -

Install Tani Software
Install Tani Software Windows Under Windows all software comes with an installer which is an executable program. You can start it directly. If You update an installed Tani product it will uninstall the previous version automatically and replaces it with the actual one. All user configuration setting will be preserved. A reboot will be requested in these conditions: The running software can not be stopped. This may be true if an other running program uses the software. Some parts of the software can not be removed because other software holds them open. A program uses the directory holding the software. A hint: If You uninstall the software separately and try installing them again it will request a reboot always. Optionally you can ignore the reboot request. This is always at your own risk. Possibly required files can not be installed. The installed software may not work as expected. Why a reboot is required after uninstall: The uninstall program can not be deleted by itself because it runs. Windows uses random generated file names in this registry key. So the installer cannot check if the reboot will be required or is optional. The installation depending on your Windows patch level may start its internal update. This does not relay on software from Tani GmbH. If Windows will request updates it will do so. During the Windows update an internet connection is required. The installation process will need additional time until the update is finished. More information is available in the Windows Update. For special envoronments it can be necessary running the OPC server or the PLC Engine not as a Windows service. -

Automatic Dependency Management for Scientific Applications on Clusters
Automatic Dependency Management for Scientific Applications on Clusters Ben Tovar, Nicholas Hazekamp, Nathaniel Kremer-Herman, and Douglas Thain btovar,nhazekam,nkremerh,dthain @nd.edu { } Department of Computer Science and Engineering University of Notre Dame Abstract—Software installation remains a challenge in scien- are unprivileged, and multiple incompatible versions may need tific computing. End users require custom software stacks that to exist simultaneously. are not provided through commodity channels. The resulting To address this problem, we present VC3-Builder, a user- effort needed to install software delays research in the first place, and creates friction for moving applications to new resources level system for managing software dependencies across mul- and new users. Ideally, end-users should be able to manage their tiple clusters. VC3-Builder shares some elements of design own software stacks without requiring administrator privileges. with recent systems such as Nix [8] and Spack [10], but it To that end, we describe VC3-Builder, a tool for deploying is more suited for rapid deployment by exploiting pre-existing software environments automatically on clusters. Its primary software where available and using the resources of the cluster application comes in cloud and opportunistic computing, where deployment must be performed in batch as a side effect of job itself to perform parallel and distributed builds. execution. VC3-Builder uses workflow technologies as a means We demonstrate VC3-Builder by several case studies of of exploiting cluster resources for building in a portable way. We complex applications that present a challenge for users to build demonstrate the use of VC3-Builder on three applications with and deploy manually: the MAKER bioinformatics pipeline, the complex dependencies: MAKER, Octave, and CVMFS, building CVMFS distributed filesystem, and the Octave mathematics and running on three different cluster facilities in sequential, parallel, and distributed modes. -

Tecnologías Libres Para La Traducción Y Su Evaluación
FACULTAD DE CIENCIAS HUMANAS Y SOCIALES DEPARTAMENTO DE TRADUCCIÓN Y COMUNICACIÓN Tecnologías libres para la traducción y su evaluación Presentado por: Silvia Andrea Flórez Giraldo Dirigido por: Dra. Amparo Alcina Caudet Universitat Jaume I Castellón de la Plana, diciembre de 2012 AGRADECIMIENTOS Quiero agradecer muy especialmente a la Dra. Amparo Alcina, directora de esta tesis, en primer lugar por haberme acogido en el máster Tecnoloc y el grupo de investigación TecnoLeTTra y por haberme animado luego a continuar con mi investigación como proyecto de doctorado. Sus sugerencias y comentarios fueron fundamentales para el desarrollo de esta tesis. Agradezco también al Dr. Grabriel Quiroz, quien como profesor durante mi último año en la Licenciatura en Traducción en la Universidad de Antioquia (Medellín, Colombia) despertó mi interés por la informática aplicada a la traducción. De igual manera, agradezco a mis estudiantes de Traducción Asistida por Computador en la misma universidad por interesarse en el software libre y por motivarme a buscar herramientas alternativas que pudiéramos utilizar en clase sin tener que depender de versiones de demostración ni recurrir a la piratería. A mi colega Pedro, que comparte conmigo el interés por la informática aplicada a la traducción y por el software libre, le agradezco la oportunidad de llevar la teoría a la práctica profesional durante todos estos años. Quisiera agradecer a Esperanza, Anna, Verónica y Ewelina, compañeras de aventuras en la UJI, por haber sido mi grupo de apoyo y estar siempre ahí para escucharme en los momentos más difíciles. Mis más sinceros agradecimientos también a María por ser esa voz de aliento y cordura que necesitaba escuchar para seguir adelante y llegar a feliz término con este proyecto. -

Ubuntu Server Guide Basic Installation Preparing to Install
Ubuntu Server Guide Welcome to the Ubuntu Server Guide! This site includes information on using Ubuntu Server for the latest LTS release, Ubuntu 20.04 LTS (Focal Fossa). For an offline version as well as versions for previous releases see below. Improving the Documentation If you find any errors or have suggestions for improvements to pages, please use the link at thebottomof each topic titled: “Help improve this document in the forum.” This link will take you to the Server Discourse forum for the specific page you are viewing. There you can share your comments or let us know aboutbugs with any page. PDFs and Previous Releases Below are links to the previous Ubuntu Server release server guides as well as an offline copy of the current version of this site: Ubuntu 20.04 LTS (Focal Fossa): PDF Ubuntu 18.04 LTS (Bionic Beaver): Web and PDF Ubuntu 16.04 LTS (Xenial Xerus): Web and PDF Support There are a couple of different ways that the Ubuntu Server edition is supported: commercial support and community support. The main commercial support (and development funding) is available from Canonical, Ltd. They supply reasonably- priced support contracts on a per desktop or per-server basis. For more information see the Ubuntu Advantage page. Community support is also provided by dedicated individuals and companies that wish to make Ubuntu the best distribution possible. Support is provided through multiple mailing lists, IRC channels, forums, blogs, wikis, etc. The large amount of information available can be overwhelming, but a good search engine query can usually provide an answer to your questions. -
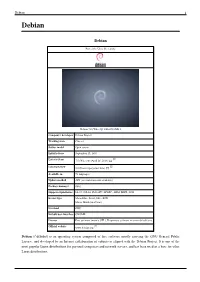
Debian 1 Debian
Debian 1 Debian Debian Part of the Unix-like family Debian 7.0 (Wheezy) with GNOME 3 Company / developer Debian Project Working state Current Source model Open-source Initial release September 15, 1993 [1] Latest release 7.5 (Wheezy) (April 26, 2014) [±] [2] Latest preview 8.0 (Jessie) (perpetual beta) [±] Available in 73 languages Update method APT (several front-ends available) Package manager dpkg Supported platforms IA-32, x86-64, PowerPC, SPARC, ARM, MIPS, S390 Kernel type Monolithic: Linux, kFreeBSD Micro: Hurd (unofficial) Userland GNU Default user interface GNOME License Free software (mainly GPL). Proprietary software in a non-default area. [3] Official website www.debian.org Debian (/ˈdɛbiən/) is an operating system composed of free software mostly carrying the GNU General Public License, and developed by an Internet collaboration of volunteers aligned with the Debian Project. It is one of the most popular Linux distributions for personal computers and network servers, and has been used as a base for other Linux distributions. Debian 2 Debian was announced in 1993 by Ian Murdock, and the first stable release was made in 1996. The development is carried out by a team of volunteers guided by a project leader and three foundational documents. New distributions are updated continually and the next candidate is released after a time-based freeze. As one of the earliest distributions in Linux's history, Debian was envisioned to be developed openly in the spirit of Linux and GNU. This vision drew the attention and support of the Free Software Foundation, who sponsored the project for the first part of its life.