M. Tech Information and Cyber Security- CBCS S. No Subject Code
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Foreword by Whitfield Diffie Preface About the Author Chapter 1
Applied Cryptography: Second Edition - Bruce Schneier Applied Cryptography, Second Edition: Protocols, Algorthms, and Source Code in C by Bruce Schneier Wiley Computer Publishing, John Wiley & Sons, Inc. ISBN: 0471128457 Pub Date: 01/01/96 Foreword By Whitfield Diffie Preface About the Author Chapter 1—Foundations 1.1 Terminology 1.2 Steganography 1.3 Substitution Ciphers and Transposition Ciphers 1.4 Simple XOR 1.5 One-Time Pads 1.6 Computer Algorithms 1.7 Large Numbers Part I—Cryptographic Protocols Chapter 2—Protocol Building Blocks 2.1 Introduction to Protocols 2.2 Communications Using Symmetric Cryptography 2.3 One-Way Functions 2.4 One-Way Hash Functions 2.5 Communications Using Public-Key Cryptography 2.6 Digital Signatures 2.7 Digital Signatures with Encryption 2.8 Random and Pseudo-Random-Sequence Generation Chapter 3—Basic Protocols 3.1 Key Exchange 3.2 Authentication 3.3 Authentication and Key Exchange 3.4 Formal Analysis of Authentication and Key-Exchange Protocols 3.5 Multiple-Key Public-Key Cryptography 3.6 Secret Splitting 3.7 Secret Sharing 3.8 Cryptographic Protection of Databases Chapter 4—Intermediate Protocols 4.1 Timestamping Services 4.2 Subliminal Channel 4.3 Undeniable Digital Signatures 4.4 Designated Confirmer Signatures 4.5 Proxy Signatures 4.6 Group Signatures 4.7 Fail-Stop Digital Signatures 4.8 Computing with Encrypted Data 4.9 Bit Commitment 4.10 Fair Coin Flips 4.11 Mental Poker 4.12 One-Way Accumulators 4.13 All-or-Nothing Disclosure of Secrets Page 1 of 666 Applied Cryptography: Second Edition - Bruce -
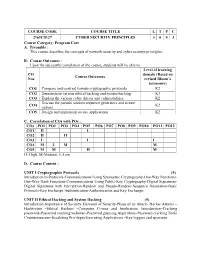
COURSE CODE COURSE TITLE L T P C 2161CS127 CYBER SECURITY PRINCIPLES 3 0 0 3 Course Category: Program Core A
COURSE CODE COURSE TITLE L T P C 2161CS127 CYBER SECURITY PRINCIPLES 3 0 0 3 Course Category: Program Core A. Preamble : This course describes the concepts of network security and cyber security principles. B. Course Outcomes : Upon the successful completion of the course, students will be able to: Level of learning CO domain (Based on Course Outcomes Nos. revised Bloom’s taxonomy) CO1 Compare and contrast various cryptographic protocols K2 CO2 Demonstrate various ethical hacking and system hacking K3 CO3 Explain the various cyber threats and vulnerabilities. K2 Discuss the pseudo random sequence generators and stream CO4 K2 ciphers CO5 Design and implement secure applications K2 C. Correlation of COs with POs : COs PO1 PO2 PO3 PO4 PO5 PO6 PO7 PO8 PO9 PO10 PO11 PO12 CO1 H L CO2 H H CO3 L L L CO4 M L M M CO5 M M H M H- High; M-Medium; L-Low D. Course Content : UNIT I Cryptographic Protocols (9) Introduction to Protocols-Communications Using Symmetric Cryptography-One-Way Functions- One-Way Hash Functions-Communications Using Public-Key Cryptography-Digital Signatures- Digital Signatures with Encryption-Random and Pseudo-Random-Sequence Generation-Basic Protocols-Key Exchange-Authentication-Authentication and Key Exchange. UNIT II Ethical Hacking and System Hacking (9) Introduction-Importance of Security-Elements of Security-Phase of an Attack- Hacker Attacks – Hacktivism –Ethical Hackers –Computer Crimes and Implication. Introduction–Cracking password–Password cracking websites–Password guessing Algorithms–Password cracking Tools Countermeasure–Escalating Privileges-Executing Applications –Key loggers and spywares. UNIT III Cyber Threats and Vulnerabilities (9) Cyber Threats-Cyber Activism-Cybercrime-Cyber Espionage-Cyber terrorism-Cyber Warfare- Cyber World Vulnerabilities-Cyber Operations-Cyber Weaponry-Society’s Critical Structures as Targets. -

Two Dozen Short Lessons in Haskell a Participatory Textbook on Functional Programming
Two Dozen Short Lessons in Haskell a participatory textbook on functional programming by Rex Page School of Computer Science University of Oklahoma Copyright © 1995, 1996, 1997 by Rex Page Permission to copy and use this document for educational or research purposes of a non-commercial nature is hereby granted, provided that this copyright notice is retained on all copies. All other rights reserved by author. Rex Page School of Computer Science University of Oklahoma 200 Felgar Street — EL114 Norman OK 73019 USA [email protected] Table of Contents 1.................................................................................................. How To Use This Book 5.................................................................................................... Hello World, Etc. 1 10..............................................................................................................Definitions 2 14...............................................................................How to Run Haskell Programs 3 17......................................... Computations on Sequences — List Comprehensions 4 21...................................................................... Function Composition and Currying 5 25.......................... Patterns of Computation — Composition, Folding, and Mapping 6 33......................................................................................................................Types 7 37........................................................ Function Types, Classes, and Polymorphism 8 42........................................... -

Cryptography
University of Indonesia Magister of Information Technology Cryptography Arrianto Mukti Wibowo University of Indonesia – University of Budi Luhur Magister of Information Technology Tujuan • Mempelajari berbagai metode dan teknik penyembunyian data menggunakan kriptografi. University of Indonesia – University of Budi Luhur Magister of Information Technology Topik • Symmetric & asymmetric cryptography, key strength, cryptosystems, public key infrastructure (PKI), one-way function, hash function, key management, cryptographic attacks University of Indonesia – University of Budi Luhur Magister of Information Technology Cryptography Issues (Schneier ‟96) • Kerahasiaan (confidentiality) dijamin dengan melakukan enkripsi (penyandian). • Keutuhan (integrity) atas data-data pembayaran dilakukan dengan fungsi hash satu arah. • Jaminan atas identitas dan keabsahan (authenticity) pihak-pihak yang melakukan transaksi dilakukan dengan menggunakan password atau sertifikat digital. Sedangkan keotentikan data transaksi dapat dilakukan dengan tanda tangan digital. • Transaksi dapat dijadikan barang bukti yang tidak bisa disangkal (non-repudiation) dengan memanfaatkan tanda tangan digital dan sertifikat digital. University of Indonesia – University of Budi Luhur Magister of Information Technology Makna Kriptografi • Krupto + Grafh = secret + writing • Cryptography: ilmu untuk membuat sebuah pesan menjadi aman University of Indonesia – University of Budi Luhur Magister of Information Technology Cryptographic algorithm & key • Cipher: fungsi matematika yang -

The GCHQ Protocol and Its Problems
The GCHQ Protocol and Its Problems Ross Anderson, Michael Roe Cambridge University Computer Laboratory Pembroke Street, Cambridge CB2 3QG Email: (rjal4,mrr)@cl. cam.ac .uk Abstract. The UK government is fielding an architecture for secure electronic mail based on the NSA’s Message Security Protocol, with a key escrow scheme inspired by Diffie-Hellman. Attempts have been made to have this protocol adopted by other governments and in various do- mestic applications. The declared policy goal is to entrench commercial key escrow while simultaneously creating a large enough market that software houses will support the protocol as a standard feature rather than charging extra for it. We describe this protocol and show that, like the ‘Clipper’ proposal of a few years ago, it has a number of problems. It provides the worst of both secret and public key systems, without delivering the advantages of ei- ther; it does not support nonrepudiation; a.nd there are serious problems with the replacement of compromised keys, the protection of security la- bels, and the support of complex or dynamic administrative structures. 1 Introduction Over the last two years, the British government’s crypto policy has changed completely. Whereas in 1994 the Primc Minister assured the House of Com- mons that no further restrictions on encryption were envisaged, we now find the government proposing to introduce a licensing scheme for ‘trusted third par- ties’, and licenses will only be granted to operators that escrow their customers’ confidentiality keys to the government’s satisfaction [ll,211. In March 1996, a document describing the cryptographic protocols to he used in government electronic mail systems was issued by CESG, the department of GCHQ concerned with the protection of government information; it has since been made available on the worldwide web [4]. -

Confidentiality Framework
T/3522TL/2778/9 4 February 1997 CESG INFOSEC MEMORANDUM NO. 14 AN HMG PUBLIC KEY INFRASTRUCTURE TO SUPPORT CONFIDENTIALITY Issue 1.0 CESG ELECTRONIC INFORMATION SYSTEMS SECURITY MEMORANDUM NO. 14 AN HMG PUBLIC KEY INFRASTRUCTURE TO SUPPORT CONFIDENTIALITY Issue 1.0 February 1997 © Crown Copyright 1997 Communications-Electronics Security Group CESG Infosec Memorandum No. 14 FOREWORD This Memorandum is issued by the Communications-Electronics Security Group (CESG) of Government Communications Headquarters as part of its responsibility to advise HMG on Electronic Information Systems Security (Infosec). It suggests an architecture for a public key infrastructure (PKI) to support confidentiality between communicating systems. The Memorandum will eventually form part of a suite of documents which collectively provide advice on the implementation of a PKI, and the use of the services enabled by such an infrastructure (e.g. electronic mail). The architecture as described in this document is an initial attempt at defining a PKI, and CESG will take into account any comments on its feasibility. This Memorandum is intended for use by HMG, its contractors and suppliers. General correspondence in connection with this document, including requests for additional copies, should be addressed to: Communications-Electronics Security Group (X13) Government Communications Headquarters PO Box 144 Cheltenham GL52 5UE United Kingdom Technical correspondence in connection with this document should be sent to T27 at the above address. page ii Issue 1.0 February -
APPLIED CRYPTOGRAPHY, SECOND EDITION: Protocols, Algorithms, and Source Code in C:Table of Contents
To access the contents, click the chapter and section titles. Applied Cryptography, Second Edition: Protocols, Algorthms, and Source Code in C (cloth) (Publisher: John Wiley & Sons, Inc.) Author(s): Bruce Schneier ISBN: 0471128457 Publication Date: 01/01/96 Brief Full Advanced Search Search Tips Search this book: Foreword by Whitfield Diffie Preface About the Author Chapter 1—Foundations 1.1 Terminology 1.2 Steganography 1.3 Substitution Ciphers and Transposition Ciphers 1.4 Simple XOR 1.5 One-Time Pads 1.6 Computer Algorithms 1.7 Large Numbers Part I—Cryptographic Protocols Chapter 2—Protocol Building Blocks 2.1 Introduction to Protocols 2.2 Communications Using Symmetric Cryptography 2.3 One-Way Functions 2.4 One-Way Hash Functions 2.5 Communications Using Public-Key Cryptography 2.6 Digital Signatures 2.7 Digital Signatures with Encryption 2.8 Random and Pseudo-Random-Sequence Generation Chapter 3—Basic Protocols 3.1 Key Exchange 3.2 Authentication 3.3 Authentication and Key Exchange 3.4 Formal Analysis of Authentication and Key-Exchange Protocols 3.5 Multiple-Key Public-Key Cryptography 3.6 Secret Splitting 3.7 Secret Sharing 3.8 Cryptographic Protection of Databases Chapter 4—Intermediate Protocols 4.1 Timestamping Services 4.2 Subliminal Channel 4.3 Undeniable Digital Signatures 4.4 Designated Confirmer Signatures 4.5 Proxy Signatures 4.6 Group Signatures 4.7 Fail-Stop Digital Signatures 4.8 Computing with Encrypted Data 4.9 Bit Commitment 4.10 Fair Coin Flips 4.11 Mental Poker 4.12 One-Way Accumulators 4.13 All-or-Nothing Disclosure -
Applied Cryptography, Second Edition
To access the contents, click the chapter and section titles. Applied Cryptography, Second Edition: Protocols, Algorthms, and Source Code in C (cloth) (Publisher: John Wiley & Sons, Inc.) Author(s): Bruce Schneier ISBN: 0471128457 Publication Date: 01/01/96 Brief Full Advanced Search Search Tips Search this book: Foreword by Whitfield Diffie Preface About the Author Chapter 1—Foundations 1.1 Terminology 1.2 Steganography 1.3 Substitution Ciphers and Transposition Ciphers 1.4 Simple XOR 1.5 One-Time Pads 1.6 Computer Algorithms 1.7 Large Numbers Part I—Cryptographic Protocols Chapter 2—Protocol Building Blocks 2.1 Introduction to Protocols 2.2 Communications Using Symmetric Cryptography 2.3 One-Way Functions 2.4 One-Way Hash Functions 2.5 Communications Using Public-Key Cryptography 2.6 Digital Signatures 2.7 Digital Signatures with Encryption 2.8 Random and Pseudo-Random-Sequence Generation Chapter 3—Basic Protocols 3.1 Key Exchange 3.2 Authentication 3.3 Authentication and Key Exchange 3.4 Formal Analysis of Authentication and Key-Exchange Protocols 3.5 Multiple-Key Public-Key Cryptography 3.6 Secret Splitting 3.7 Secret Sharing 3.8 Cryptographic Protection of Databases Chapter 4—Intermediate Protocols 4.1 Timestamping Services 4.2 Subliminal Channel 4.3 Undeniable Digital Signatures 4.4 Designated Confirmer Signatures 4.5 Proxy Signatures 4.6 Group Signatures 4.7 Fail-Stop Digital Signatures 4.8 Computing with Encrypted Data 4.9 Bit Commitment 4.10 Fair Coin Flips 4.11 Mental Poker 4.12 One-Way Accumulators 4.13 All-or-Nothing Disclosure -
APPLIED CRYPTOGRAPHY, SECOND EDITION: Protocols
To access the contents, click the chapter and section titles. Applied Cryptography, Second Edition: Protocols, Algorthms, and Source Code in C (cloth) (Publisher: John Wiley & Sons, Inc.) Author(s): Bruce Schneier ISBN: 0471128457 Publication Date: 01/01/96 Brief Full Advanced Search Search Tips Search this book: Foreword by Whitfield Diffie Preface About the Author Chapter 1—Foundations 1.1 Terminology 1.2 Steganography 1.3 Substitution Ciphers and Transposition Ciphers 1.4 Simple XOR 1.5 One-Time Pads 1.6 Computer Algorithms 1.7 Large Numbers Part I—Cryptographic Protocols Chapter 2—Protocol Building Blocks 2.1 Introduction to Protocols 2.2 Communications Using Symmetric Cryptography 2.3 One-Way Functions 2.4 One-Way Hash Functions 2.5 Communications Using Public-Key Cryptography 2.6 Digital Signatures 2.7 Digital Signatures with Encryption 2.8 Random and Pseudo-Random-Sequence Generation Chapter 3—Basic Protocols 3.1 Key Exchange 3.2 Authentication 3.3 Authentication and Key Exchange 3.4 Formal Analysis of Authentication and Key-Exchange Protocols 3.5 Multiple-Key Public-Key Cryptography 3.6 Secret Splitting 3.7 Secret Sharing 3.8 Cryptographic Protection of Databases Chapter 4—Intermediate Protocols 4.1 Timestamping Services 4.2 Subliminal Channel 4.3 Undeniable Digital Signatures 4.4 Designated Confirmer Signatures 4.5 Proxy Signatures 4.6 Group Signatures 4.7 Fail-Stop Digital Signatures 4.8 Computing with Encrypted Data 4.9 Bit Commitment 4.10 Fair Coin Flips 4.11 Mental Poker 4.12 One-Way Accumulators 4.13 All-or-Nothing Disclosure -

Security Engineering 0011 0010 1010 1101 0001 0100 1011 Lesson 10 Combining Block Ciphers; Pseudo-Random- Sequence Generators and Stream Ciphers
Security Engineering 0011 0010 1010 1101 0001 0100 1011 Lesson 10 Combining Block Ciphers; Pseudo-Random- Sequence Generators and Stream Ciphers, Spring 2010 Dr. Marenglen Biba Combining Block Ciphers Combining Block Ciphers Double Encryption Triple Encryption Doubling the Block Length Other Multiple Encryption Schemes CDMF Key Shortening 0011 0010 1010 1101 0001 0100 1011 Whitening Cascading Multiple Block Algorithms Combining Multiple Block Algorithms Combining block algorithms • There are many ways to combine block algorithms to get new algorithms. • The idea behind these schemes is to try to increase security without going through the trouble of designing a new algorithm. 0011 0010• DES 1010 has1101 been 0001 0100a secure 1011 algorithm However, the key is too short. • Wouldn’t it be nice to use DES as a building block for another algorithm with a longer key? • We’d have the best of both worlds: the assurance of almost four decades of cryptanalysis plus a long key. Multiple encryption • Multiple encryption is one combination technique: using an algorithm to encrypt the same plaintext block multiple times with multiple keys. • Cascading is like multiple encryption, but uses different algorithms. • Encrypting a plaintext block twice with the same key, 0011 0010whether 1010 1101 with 0001 the 0100 same 1011 algorithm or a different one, is not smart. – For the same algorithm, it does not affect the complexity of a brute-force search. • If you are going to use any of the following techniques, make sure the multiple keys are different and independent. Double Encryption • A naìve way of improving the security of a block algorithm is to encrypt a block twice with two different keys. -

The GCHQ Protocol and Its Problems
The GCHQ Protocol and its Problems Ross Anderson, Michael Roe Cambridge University Computer Laboratory Pembroke Street, Cambridge CB2 3QG Email: (rja14,mrr)@cl.cam.ac.uk Abstract. The UK government is fielding an architecture for secure electronic mail based on the NSA’s Message Security Protocol, with a key escrow scheme inspired by Diffie-Hellman. Attempts have been made to have this protocol adopted by other governments and in various do- mestic applications. The declared policy goal is to entrench commercial key escrow while simultaneously creating a large enough market that software houses will support the protocol as a standard feature rather than charging extra for it. We describe this protocol and show that, like the ‘Clipper’ proposal of a few years ago, it has a number of problems. It provides the worst of both secret and public key systems, without delivering the advantages of ei- ther; it does not support nonrepudiation; and there are serious problems with the replacement of compromised keys, the protection of security la- bels, and the support of complex or dynamic administrative structures. 1 Introduction Over the last two years, the British government’s crypto policy has changed completely. Whereas in 1994 the Prime Minister assured the House of Com- mons that no further restrictions on encryption were envisaged, we now find the government proposing to introduce a licensing scheme for ‘trusted third par- ties’, and licenses will only be granted to operators that escrow their customers’ confidentiality keys to the government’s satisfaction [11, ?]. In March 1996, a document describing the cryptographic protocols to be used in government electronic mail systems was issued by CESG, the department of GCHQ concerned with the protection of government information; it has since been made available on the worldwide web [4]. -
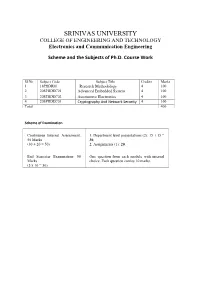
SRINIVAS UNIVERSITY COLLEGE of ENGINEERING and TECHNOLOGY Electronics and Communication Engineering
SRINIVAS UNIVERSITY COLLEGE OF ENGINEERING AND TECHNOLOGY Electronics and Communication Engineering Scheme and the Subjects of Ph.D. Course Work Sl.No Subject Code Subject Title Credits Marks 1 18PHDRM Research Methodology 4 100 2 20SPHDEC01 Advanced Embedded System 4 100 3 20SPHDEC02 Automotive Electronics 4 100 4 20SPHDEC03 Cryptography And Network Security 4 100 Total 400 Scheme of Examination Continuous Internal Assessment: 1. Department level presentations (2): 15 + 15 = 50 Marks 30, (30 + 20 = 50) 2. Assignments (1): 20. End Semester Examination: 50 One question from each module with internal Marks choice. Each question carries 10 marks. (5 x 10 = 50) ADVANCED EMBEDDED SYSTEM 20SPHDEC01 Module -1 Embedded System: Embedded vs General computing system, classification, application and purpose of ES. Core of an Embedded System, Memory, Sensors, Actuators, LED, Optocoupler, Communication Interface, Reset circuits, RTC, WDT, Characteristics and Quality Attributes of Embedded Systems (Selected Topics from Ch -1, 2, 3 of Text 1). Module -2 Hardware Software Co-Design, embedded firmware design approaches, computational models, embedded firmware development languages, Integration and testing of Embedded Hardware and firmware, Components in embedded system development environment (IDE), Files generated during compilation, simulators, emulators and debugging (Selected Topics From Ch-7, 9, 12, 13 of Text 1). Module -3 ARM-32 bit Microcontroller: Thumb-2 technology and applications of ARM, Architecture of ARM Cortex M3, Various Units in the architecture, General Purpose Registers, Special Registers, exceptions, interrupts, stack operation, reset sequence (Ch 1, 2, 3 of Text 2). Module -4 Instruction Sets: Assembly basics, Instruction list and description, useful instructions, Memory Systems, Memory maps, Cortex M3 implementation overview, pipeline and bus interface (Ch-4, 5, 6 of Text 2).