The GCHQ Protocol and Its Problems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

University Microfilms International 300 North Zeeb Road Ann Arbor, Michigan 48106 USA St
ISOLATION AND COMMUNITY: THE THEME AND FORM OF WILLIAM MORRIS' POETRY AND PROSE Item Type text; Dissertation-Reproduction (electronic) Authors Balch, Dennis Robert, 1949- Publisher The University of Arizona. Rights Copyright © is held by the author. Digital access to this material is made possible by the University Libraries, University of Arizona. Further transmission, reproduction or presentation (such as public display or performance) of protected items is prohibited except with permission of the author. Download date 09/10/2021 07:25:50 Link to Item http://hdl.handle.net/10150/289550 INFORMATION TO USERS This material was produced from a microfilm copy of the original document. While the most advanced technological means to photograph and reproduce this document have been used, the quality is heavily dependent upon the quality of the original submitted. The following explanation of techniques is provided to help you understand markings or patterns which may appear on this reproduction. 1.The sign or "target" for pages apparently lacking from the document photographed is "Missing Page(s)". If it was possible to obtain the missing page(s) or section, they are spliced into the film along with adjacent pages. This may have necessitated cutting thru an image and duplicating adjacent pages to insure you complete continuity. 2. When an image on the film is obliterated with a large round black mark, it is an indication that the photographer suspected that the copy may have moved during exposure and thus cause a blurred image. You will find a good image of the page in the adjacent frame. 3. When a map, drawing or chart, etc., was part of the material being photographed the photographer followed a definite method in "sectioning" the material. -

The World's Show, 1851, Or, the Adventures of Mr. and Mrs
I < ' ' 6 i-o / Digitized by the Internet Archive in 2017 with funding from Getty Research Institute https://archive.org/details/worldsshow1851or00mayh ^0 mt (S’SS.m : on -n ft mrnfrTTTK^LLuj *t^P^YfTYfTTfM TTTTTjif 111 Hli)HOR, IthfAdvInturesvi V AND M TS SANDBOYS AND FAMILY,, ;0 CAME UP TO TOENJOY THEMSEEVEiS. AND TO SEE THE GREAT BY HENMYMA¥H E.W/MEDI GEORCECrUBCS MANIC. LONDON: GEORGE NEWBOLD, 303 & 304, STRAND, Vv.C. — LIST OF ILLUSTRATIONS DESIGNED AND ETCHED BY GEORGE CRUIKSHANK. ALL THE WORLD GOING TO THE GREAT EXHIBITION Frontispiece LOOKING FOR LODGINGS 54 LONDON CRAMMED AND MANCHESTER DESERTED 2 PLATES . 59 THE OPERA BOXES DURING THE TIME OF THE GREAT EXHIBI- TION 117 THE OPENING OF THE GREAT BEE-HIVE 136 THE FIRST SHILLING DAY 153 SOME OF THE DROLLERIES OF THE GREAT EXHIBITION ... 160 ODDS AND ENDS, IN, OUT, AND ABOUT THE GREAT EXHIBITION . 162 DISPERSION OF THE WORKS OF ALL NATIONS 238 ludia Proof impressions of the above Ten Plates may be had, all printed on paper of uniform size (23^ by 17^ inches), quite perfect, and free from folds, price 15s. per set. ENGRAVINGS. THE CHEAPEST HOUSE FOR ENGRAVINGS OF EVERY DESCRIPTION is GEORGE NEWBOLD’S, 303 & 304, STRAND, LONDON, W.C. (back of st. mart’s chukch.) A Clearance Sale Catalogue, 54 Svo pp., Post Free on receipt of Four Stamps. ; ; 1851 : OB, THE ADVENTURES OF MR. AND MRS. CURSTY SANDBOYS. CHAPTER I. ‘ 1 Come, Nicliol, and gi’e us thy cracks, I seed te gang down to the smiddy, I’ve fodder’d the naigs and—the nowt, And wanted to see thee ’at did e. -

Encryption Block Cipher
10/29/2007 Encryption Encryption Block Cipher Dr.Talal Alkharobi 2 Block Cipher A symmetric key cipher which operates on fixed-length groups of bits, termed blocks, with an unvarying transformation. When encrypting, a block cipher take n-bit block of plaintext as input, and output a corresponding n-bit block of ciphertext. The exact transformation is controlled using a secret key. Decryption is similar: the decryption algorithm takes n-bit block of ciphertext together with the secret key, and yields the original n-bit block of plaintext. Mode of operation is used to encrypt messages longer than the block size. 1 Dr.Talal Alkharobi 10/29/2007 Encryption 3 Encryption 4 Decryption 2 Dr.Talal Alkharobi 10/29/2007 Encryption 5 Block Cipher Consists of two algorithms, encryption, E, and decryption, D. Both require two inputs: n-bits block of data and key of size k bits, The output is an n-bit block. Decryption is the inverse function of encryption: D(E(B,K),K) = B For each key K, E is a permutation over the set of input blocks. n Each key K selects one permutation from the possible set of 2 !. 6 Block Cipher The block size, n, is typically 64 or 128 bits, although some ciphers have a variable block size. 64 bits was the most common length until the mid-1990s, when new designs began to switch to 128-bit. Padding scheme is used to allow plaintexts of arbitrary lengths to be encrypted. Typical key sizes (k) include 40, 56, 64, 80, 128, 192 and 256 bits. -

Autumn 99 President: Eric Mitchell
Auiunui vy DARK PEAK NEWS Autumn 99 President: Eric Mitchell Chairman Cub Captain 3 News Dave Holmes Vacant 615 Loxley Road Loxley 5 Coining Events Sheffield S6 6RR Tel. (0114) 2344186 8 More News Secretary Treasurer Paul Sanderson Jeff Harrison 19 Findon Street 118 Lydgate Lane Hillsborough Crookes 9 Letters Sheffield Sheffield S6 4FG S10 5FP Tel. (0114) 2206353 Tel. (0114) 2687114 11 Features - Warts winter 98/99 Clothing & Equipment Membership - Training weekend Richard Hakes Tim Tett - Getting the Horns 454A Loxley Road 68 Roebuck Road - Thoughts on Access Loxley Sheffield S6 2XA Sheffield S6 6RS Tel.(0114) 2667922 Tel. (0114) 2339912 18 Going the Distance - Central Fells in a day Cross Country - Bob Graham 99 Pete Dyke 13 Falkland Road Sheffield Sll 7PL 21 Reports and Results Tel. (0114) 266280 41 Fell Off Editor Mike Pedley 43 In Press Frost Hole Farm - Inside the New Map Cragg Vale Hebden Bridge HX7 5RU 43 In Gear Tel. (01422) 886195 email: [email protected] .co. uk 44 The-bit-at-the-end 2 Autumn 99 Club Hut Condemmed Plans to renovate the club hut were stopped in their tracks when serious structural problems were discovered during a close inspection of the building. The findings suggested the hut could collapse at any time and left club officials with no option other than declare a return to the car park changing at the Sportsman on a Wednesday night. Roy Small and Hugh Cotton's appeal for funds has been put on hold whilst discussion are held into possibilities for a replacement. The hut was moved following the closure of the nearby prisoner of war camp in 1945 and is possibly the last remaining building from the site. -

Foreword by Whitfield Diffie Preface About the Author Chapter 1
Applied Cryptography: Second Edition - Bruce Schneier Applied Cryptography, Second Edition: Protocols, Algorthms, and Source Code in C by Bruce Schneier Wiley Computer Publishing, John Wiley & Sons, Inc. ISBN: 0471128457 Pub Date: 01/01/96 Foreword By Whitfield Diffie Preface About the Author Chapter 1—Foundations 1.1 Terminology 1.2 Steganography 1.3 Substitution Ciphers and Transposition Ciphers 1.4 Simple XOR 1.5 One-Time Pads 1.6 Computer Algorithms 1.7 Large Numbers Part I—Cryptographic Protocols Chapter 2—Protocol Building Blocks 2.1 Introduction to Protocols 2.2 Communications Using Symmetric Cryptography 2.3 One-Way Functions 2.4 One-Way Hash Functions 2.5 Communications Using Public-Key Cryptography 2.6 Digital Signatures 2.7 Digital Signatures with Encryption 2.8 Random and Pseudo-Random-Sequence Generation Chapter 3—Basic Protocols 3.1 Key Exchange 3.2 Authentication 3.3 Authentication and Key Exchange 3.4 Formal Analysis of Authentication and Key-Exchange Protocols 3.5 Multiple-Key Public-Key Cryptography 3.6 Secret Splitting 3.7 Secret Sharing 3.8 Cryptographic Protection of Databases Chapter 4—Intermediate Protocols 4.1 Timestamping Services 4.2 Subliminal Channel 4.3 Undeniable Digital Signatures 4.4 Designated Confirmer Signatures 4.5 Proxy Signatures 4.6 Group Signatures 4.7 Fail-Stop Digital Signatures 4.8 Computing with Encrypted Data 4.9 Bit Commitment 4.10 Fair Coin Flips 4.11 Mental Poker 4.12 One-Way Accumulators 4.13 All-or-Nothing Disclosure of Secrets Page 1 of 666 Applied Cryptography: Second Edition - Bruce -
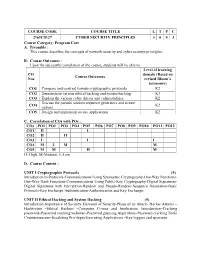
COURSE CODE COURSE TITLE L T P C 2161CS127 CYBER SECURITY PRINCIPLES 3 0 0 3 Course Category: Program Core A
COURSE CODE COURSE TITLE L T P C 2161CS127 CYBER SECURITY PRINCIPLES 3 0 0 3 Course Category: Program Core A. Preamble : This course describes the concepts of network security and cyber security principles. B. Course Outcomes : Upon the successful completion of the course, students will be able to: Level of learning CO domain (Based on Course Outcomes Nos. revised Bloom’s taxonomy) CO1 Compare and contrast various cryptographic protocols K2 CO2 Demonstrate various ethical hacking and system hacking K3 CO3 Explain the various cyber threats and vulnerabilities. K2 Discuss the pseudo random sequence generators and stream CO4 K2 ciphers CO5 Design and implement secure applications K2 C. Correlation of COs with POs : COs PO1 PO2 PO3 PO4 PO5 PO6 PO7 PO8 PO9 PO10 PO11 PO12 CO1 H L CO2 H H CO3 L L L CO4 M L M M CO5 M M H M H- High; M-Medium; L-Low D. Course Content : UNIT I Cryptographic Protocols (9) Introduction to Protocols-Communications Using Symmetric Cryptography-One-Way Functions- One-Way Hash Functions-Communications Using Public-Key Cryptography-Digital Signatures- Digital Signatures with Encryption-Random and Pseudo-Random-Sequence Generation-Basic Protocols-Key Exchange-Authentication-Authentication and Key Exchange. UNIT II Ethical Hacking and System Hacking (9) Introduction-Importance of Security-Elements of Security-Phase of an Attack- Hacker Attacks – Hacktivism –Ethical Hackers –Computer Crimes and Implication. Introduction–Cracking password–Password cracking websites–Password guessing Algorithms–Password cracking Tools Countermeasure–Escalating Privileges-Executing Applications –Key loggers and spywares. UNIT III Cyber Threats and Vulnerabilities (9) Cyber Threats-Cyber Activism-Cybercrime-Cyber Espionage-Cyber terrorism-Cyber Warfare- Cyber World Vulnerabilities-Cyber Operations-Cyber Weaponry-Society’s Critical Structures as Targets. -

Two Dozen Short Lessons in Haskell a Participatory Textbook on Functional Programming
Two Dozen Short Lessons in Haskell a participatory textbook on functional programming by Rex Page School of Computer Science University of Oklahoma Copyright © 1995, 1996, 1997 by Rex Page Permission to copy and use this document for educational or research purposes of a non-commercial nature is hereby granted, provided that this copyright notice is retained on all copies. All other rights reserved by author. Rex Page School of Computer Science University of Oklahoma 200 Felgar Street — EL114 Norman OK 73019 USA [email protected] Table of Contents 1.................................................................................................. How To Use This Book 5.................................................................................................... Hello World, Etc. 1 10..............................................................................................................Definitions 2 14...............................................................................How to Run Haskell Programs 3 17......................................... Computations on Sequences — List Comprehensions 4 21...................................................................... Function Composition and Currying 5 25.......................... Patterns of Computation — Composition, Folding, and Mapping 6 33......................................................................................................................Types 7 37........................................................ Function Types, Classes, and Polymorphism 8 42........................................... -

Cryptography
University of Indonesia Magister of Information Technology Cryptography Arrianto Mukti Wibowo University of Indonesia – University of Budi Luhur Magister of Information Technology Tujuan • Mempelajari berbagai metode dan teknik penyembunyian data menggunakan kriptografi. University of Indonesia – University of Budi Luhur Magister of Information Technology Topik • Symmetric & asymmetric cryptography, key strength, cryptosystems, public key infrastructure (PKI), one-way function, hash function, key management, cryptographic attacks University of Indonesia – University of Budi Luhur Magister of Information Technology Cryptography Issues (Schneier ‟96) • Kerahasiaan (confidentiality) dijamin dengan melakukan enkripsi (penyandian). • Keutuhan (integrity) atas data-data pembayaran dilakukan dengan fungsi hash satu arah. • Jaminan atas identitas dan keabsahan (authenticity) pihak-pihak yang melakukan transaksi dilakukan dengan menggunakan password atau sertifikat digital. Sedangkan keotentikan data transaksi dapat dilakukan dengan tanda tangan digital. • Transaksi dapat dijadikan barang bukti yang tidak bisa disangkal (non-repudiation) dengan memanfaatkan tanda tangan digital dan sertifikat digital. University of Indonesia – University of Budi Luhur Magister of Information Technology Makna Kriptografi • Krupto + Grafh = secret + writing • Cryptography: ilmu untuk membuat sebuah pesan menjadi aman University of Indonesia – University of Budi Luhur Magister of Information Technology Cryptographic algorithm & key • Cipher: fungsi matematika yang -

DIRECTORY of INFOSEC ASSURED PRODUCTS 2001 CESG DIRECTORY 14/5/01 3:48 Pm Page 2
CESG DIRECTORY 14/5/01 3:48 pm Page 1 DIRECTORY OF INFOSEC ASSURED PRODUCTS 2001 CESG DIRECTORY 14/5/01 3:48 pm Page 2 CONTENTS INTRODUCTION Page 3-4 IACS Introduction to CESG Infosec Assurance and Certification Services Page 5-8 CLEF Contact Details Page 9 International Certification Body Contact Details Page 9 CC and ITSEC Certified Products • Smart Cards Page 10 • PC Access Control Page 11-13 • Operating Systems Page 14-18 • Networking Page 19-24 • Firewalls Page 24-31 • Communications Page 32-37 • Databases Page 38-43 • Miscellaneous Page 43-44 PROTECTION PROFILES Introduction to Protection Profiles Page 45 List of Protection Profiles products Page 46-49 CAPS Introduction to CESG Approved Products Scheme Page 51-52 CAPS products • Data Encryption Page 53-55 • Communications Security Page 55-57 • Access Control Page 58-61 • Miscellaneous Page 62 TEMPEST Introduction to Tempest Page 63 List of Tempest approved products Page 64-66 Company names and addresses Page 67-68 INDEX Page 69-70 2 CESG DIRECTORY 14/5/01 3:48 pm Page 3 INTRODUCTION This ‘Directory of Infosec Assured Products’ is a new publication that replaces the former UKSP-06. It has been produced as a top-level guide for both product developers, vendors and end-users, and gives details of the means by which security products are approved or certified, an overview of the products’ features, and the context in which they should be used. The Directory will be updated on an annual basis. However, as new products are regularly being approved and certified, these will be reflected on CESG’s websites, accessible via www.cesg.gov.uk, as and when they become available. -

Confidentiality Framework
T/3522TL/2778/9 4 February 1997 CESG INFOSEC MEMORANDUM NO. 14 AN HMG PUBLIC KEY INFRASTRUCTURE TO SUPPORT CONFIDENTIALITY Issue 1.0 CESG ELECTRONIC INFORMATION SYSTEMS SECURITY MEMORANDUM NO. 14 AN HMG PUBLIC KEY INFRASTRUCTURE TO SUPPORT CONFIDENTIALITY Issue 1.0 February 1997 © Crown Copyright 1997 Communications-Electronics Security Group CESG Infosec Memorandum No. 14 FOREWORD This Memorandum is issued by the Communications-Electronics Security Group (CESG) of Government Communications Headquarters as part of its responsibility to advise HMG on Electronic Information Systems Security (Infosec). It suggests an architecture for a public key infrastructure (PKI) to support confidentiality between communicating systems. The Memorandum will eventually form part of a suite of documents which collectively provide advice on the implementation of a PKI, and the use of the services enabled by such an infrastructure (e.g. electronic mail). The architecture as described in this document is an initial attempt at defining a PKI, and CESG will take into account any comments on its feasibility. This Memorandum is intended for use by HMG, its contractors and suppliers. General correspondence in connection with this document, including requests for additional copies, should be addressed to: Communications-Electronics Security Group (X13) Government Communications Headquarters PO Box 144 Cheltenham GL52 5UE United Kingdom Technical correspondence in connection with this document should be sent to T27 at the above address. page ii Issue 1.0 February -

An Historic Haskell Day!
An Historic Sunday, August 2, 2015 Haskell Day! SUNDAY, AUGUST 2, 2015 732-747-8060 $ TDN Home Page Click Here FEATURE PRESENTATION • GI WILLIAM HILL HASKELL INV. >TEXAS= HOLDS >EM IN JIM DANDY Saturday=s GII Jim Dandy S. at Saratoga was the loser--numerically speaking, anyways--in the confluence of sophomore stakes events carded for this always busy weekend of racing. With Tekton (Bernardini) having scratched in favor of Friday=s Curlin S. and with Upstart (Flatter) and >TDN Rising Star= Competitive Edge (Super Saver) traveling the NJ Turnpike for Sunday=s GI Haskell Invitational S., just four horses faced the starter in the main local prep for the GI Travers S. Aug. 29, but the race did not lack for excitement, as PHAROAH IMPOSING, BUT NO >SHORE= THING GI Breeders= Cup Juvenile hero Texas Red (Afleet Alex) Zayat Stable=s American Pharoah (Pioneerof the Nile) outfooted odds-on Frosted (Tapit) by a measured half- already cemented his name in history when he became length. Cont. p9 only the 12th horse to win the Triple Crown, but the bay looks to add to his legacy Sunday in the GI William >LEGA= EAGLE Hill Haskell Invitational Probably below her best last time when second in S. at Monmouth Park, a The Curragh=s G1 Pretty Polly S., Michael Tabor=s AWin and You=re In@ G1 1000 Guineas heroine Legatissimo (Ire) (Danehill qualifier for the GI Dancer {Ire}) bounced back to her formidable best at Breeders= Cup Classic. Goodwood on Saturday when storming to success in This will be the Bob the G1 Qatar Nassau S. -

Expertise As an Object: an Ontological Study of Cryptology Research in the United Kingdom from 1970 to 2000
UNIVERSITY OF SURREY Expertise as an Object: An Ontological Study of Cryptology Research in the United Kingdom from 1970 to 2000 by Richard Fletcher Submitted for the degree of Doctor of Philosophy Faculty of Arts and Human Sciences Department of Sociology Supervisors: Dr Christine Hine and Dr Nicola Green ©Richard Fletcher Words: 95,698 Declaration of Authorship This thesis and the work to which it refers are the results of my own efforts. Any ideas, data, images or text resulting from the work of others (whether published or unpublished) are fully identified as such within the work and attributed to their originator in the text, bibliography or in footnotes. This thesis has not been submitted in whole or in part for any other academic degree or professional qualification. I agree that the University has the right to submit my work to the plagiarism detection service TurnitinUK for originality checks. Whether or not drafts have been so-assessed, the University reserves the right to require an electronic version of the final document (as submitted) for assessment as above. Signature: Date: i \Quis custodiet ipsos custodes?" Juvenal (Satire VI, lines 347-8) Abstract Recent research carried out under the `third wave of science studies' has produced robust categories of expertise, and has developed normative ideas about how it should be used during controversies over technological decision-making. Though separate in the literature, third wave ideas about contributory expertise appear to be compatible with the recent `turn to ontology'. Both sets of ideas focus on what it is that practices are able to produce, and consider the results of those practices to be real.