Applied Cryptography, Second Edition
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

David Wong Snefru
SHA-3 vs the world David Wong Snefru MD4 Snefru MD4 Snefru MD4 MD5 Merkle–Damgård SHA-1 SHA-2 Snefru MD4 MD5 Merkle–Damgård SHA-1 SHA-2 Snefru MD4 MD5 Merkle–Damgård SHA-1 SHA-2 Snefru MD4 MD5 Merkle–Damgård SHA-1 SHA-2 Keccak BLAKE, Grøstl, JH, Skein Outline 1.SHA-3 2.derived functions 3.derived protocols f permutation-based cryptography AES is a permutation input AES output AES is a permutation 0 input 0 0 0 0 0 0 0 key 0 AES 0 0 0 0 0 0 output 0 Sponge Construction f Sponge Construction 0 0 0 1 0 0 0 1 f 0 1 0 0 0 0 0 1 Sponge Construction 0 0 0 1 r 0 0 0 1 f 0 1 0 0 c 0 0 0 1 Sponge Construction 0 0 0 1 r 0 0 0 1 f r c 0 1 0 0 0 0 0 0 c 0 0 0 0 0 1 0 0 key 0 AES 0 0 0 0 0 0 0 Sponge Construction message 0 1 0 1 0 ⊕ 1 0 0 f 0 0 0 0 0 1 0 0 Sponge Construction message 0 0 0 ⊕ ⊕ 0 f 0 0 0 0 Sponge Construction message 0 0 0 ⊕ ⊕ 0 f f 0 0 0 0 Sponge Construction message 0 0 0 ⊕ ⊕ ⊕ 0 f f 0 0 0 0 Sponge Construction message 0 0 0 ⊕ ⊕ ⊕ 0 f f f 0 0 0 0 Sponge Construction message 0 0 0 ⊕ ⊕ ⊕ 0 f f f 0 0 0 0 absorbing Sponge Construction message output 0 0 0 ⊕ ⊕ ⊕ 0 f f f 0 0 0 0 absorbing Sponge Construction message output 0 0 0 ⊕ ⊕ ⊕ 0 f f f f 0 0 0 0 absorbing Sponge Construction message output 0 0 0 ⊕ ⊕ ⊕ 0 f f f f 0 0 0 0 absorbing Sponge Construction message output 0 0 0 ⊕ ⊕ ⊕ 0 f f f f f 0 0 0 0 absorbing Sponge Construction message output 0 0 0 ⊕ ⊕ ⊕ 0 f f f f f 0 0 0 0 absorbing squeezing Keccak Guido Bertoni, Joan Daemen, Michaël Peeters and Gilles Van Assche 2007 SHA-3 competition 2012 2007 SHA-3 competition 2012 SHA-3 standard -

NISTIR 7620 Status Report on the First Round of the SHA-3
NISTIR 7620 Status Report on the First Round of the SHA-3 Cryptographic Hash Algorithm Competition Andrew Regenscheid Ray Perlner Shu-jen Chang John Kelsey Mridul Nandi Souradyuti Paul NISTIR 7620 Status Report on the First Round of the SHA-3 Cryptographic Hash Algorithm Competition Andrew Regenscheid Ray Perlner Shu-jen Chang John Kelsey Mridul Nandi Souradyuti Paul Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 September 2009 U.S. Department of Commerce Gary Locke, Secretary National Institute of Standards and Technology Patrick D. Gallagher, Deputy Director NISTIR 7620: Status Report on the First Round of the SHA-3 Cryptographic Hash Algorithm Competition Abstract The National Institute of Standards and Technology is in the process of selecting a new cryptographic hash algorithm through a public competition. The new hash algorithm will be referred to as “SHA-3” and will complement the SHA-2 hash algorithms currently specified in FIPS 180-3, Secure Hash Standard. In October, 2008, 64 candidate algorithms were submitted to NIST for consideration. Among these, 51 met the minimum acceptance criteria and were accepted as First-Round Candidates on Dec. 10, 2008, marking the beginning of the First Round of the SHA-3 cryptographic hash algorithm competition. This report describes the evaluation criteria and selection process, based on public feedback and internal review of the first-round candidates, and summarizes the 14 candidate algorithms announced on July 24, 2009 for moving forward to the second round of the competition. The 14 Second-Round Candidates are BLAKE, BLUE MIDNIGHT WISH, CubeHash, ECHO, Fugue, Grøstl, Hamsi, JH, Keccak, Luffa, Shabal, SHAvite-3, SIMD, and Skein. -

Data Intensive Dynamic Scheduling Model and Algorithm for Cloud Computing Security Md
1796 JOURNAL OF COMPUTERS, VOL. 9, NO. 8, AUGUST 2014 Data Intensive Dynamic Scheduling Model and Algorithm for Cloud Computing Security Md. Rafiqul Islam1,2 1Computer Science Department, American International University Bangladesh, Dhaka, Bangladesh 2Computer Science and Engineering Discipline, Khulna University, Khulna, Bangladesh Email: [email protected] Mansura Habiba Computer Science Department, American International University Bangladesh, Dhaka, Bangladesh Email: [email protected] Abstract—As cloud is growing immensely, different point cloud computing has gained widespread acceptance. types of data are getting more and more dynamic in However, without appropriate security and privacy terms of security. Ensuring high level of security for solutions designed for clouds, cloud computing becomes all data in storages is highly expensive and time a huge failure [2, 3]. Amazon provides a centralized consuming. Unsecured services on data are also cloud computing consisting simple storage services (S3) becoming vulnerable for malicious threats and data and elastic compute cloud (EC2). Google App Engine is leakage. The main reason for this is that, the also an example of cloud computing. While these traditional scheduling algorithms for executing internet-based online services do provide huge amounts different services on data stored in cloud usually of storage space and customizable computing resources. sacrifice security privilege in order to achieve It is eliminating the responsibility of local machines for deadline. To provide adequate security without storing and maintenance of data. Considering various sacrificing cost and deadline for real time data- kinds of data for each user stored in the cloud and the intensive cloud system, security aware scheduling demand of long term continuous assurance of their data algorithm has become an effective and important safety, security is one of the prime concerns for the feature. -

Ensuring Audit Log Accountability Through Hash Based Techniques
International Journal of Future Computer and Communication, Vol. 1, No. 4, December 2012 Ensuring Audit Log Accountability through Hash Based Techniques Rashmita Jena, M. Aparna, Chinmaya Sahu, Rajeev Ranjan, and Rajesh Atmakuri trying to meet his sales requirements for a fiscal year. He Abstract—Audit logs are now considered good practice and a might attempt to change the transaction dates to make it standard approach for business systems. The integrity of the appear that they had transpired within the previous fiscal year auditing records themselves is critical. By simply storing all the when, in reality, they had not. Consider a school database interactions in a separate audit log does not guarantee the where a student who receives a “F” in one of his subjects, in integrity of the log. Data tampering can be done through unauthorized access and in some cases through authorized users. which he needs at least a “B”, could be highly tempted to try Results of such action can be unpleasant for business and their to dishonestly change his grade to a “B” in the database. This clients. Therefore, a demand for audit log security is needed would be an example of a student who would have to hack more than ever. This paper describes a mechanism based on into the system, unless of course the student somehow had cryptographic hash functions and trusted timestamping that access to the database containing the grade. prevents an outsider or inside intruder from silently corrupting The above discussed examples provide just a few of the the audit log. In addition it is shown that the proposed mechanism can be realized in database systems with little reasons why someone might want to tamper with a database. -

Digital Stamp and Signature Guide
Division of Land Use Regulation Digital Stamp and Signature Guide Instructions for E‐Submission Digital Signatures Version 1 06/05/2020 File: lur_052 Table of Contents Section 1: State Board of Professional Engineers and Land Surveyors Rules 1.1: 13:40-8.1A DIGITAL SIGNATURES AND SEALS…………………………………………………...1 Section 2: Overview……………………………………………………………………………………………………2 Section 3 Glossary of Terms…………………………………………………………………………………………2 Section 4: How Authentication Works……………………………………………………………………………..2 Section 5: Digital Signing and Sealing Plans-Example 1.………………….…………………………………..4 5.1: Bluebeam REVU Digital Signature and Seal Setup………………………………………………..4 5.2: Bluebeam Signature and Seal – Demonstration………………………………………………...…7 Section 6 Digital Signing and Sealing Plans-Example 2.…………………………………………..…………10 6.1: Adobe Signature and Seal Setup……………………………………………………….…………...10 6.2: Adobe Signature and Seal – Demonstration……………………………………………………....15 Digital Signature and Seal Guide Division of Land Use Regulation The NJ Board of Professional Engineers (PE) and Land Surveyors adopted rules for digital signatures and seals in November of 2015. Any electronic plans submitted to the Division of Land Use Regulation, where a signed and sealed plan is required, shall comply with the NJ Administrative Code governing the State Board of Professional Engineers and Land Surveyors. As a point of reference, below is the section of PE rules applicable to digital signatures and seals: N.J.A.C. 13:40-8.1A DIGITAL SIGNATURES AND SEALS a) A digital signature and seal shall carry the same weight, authority, and effect as a handwritten signature and impression-type seal when the following criteria are met: 1) The digital signing and sealing process satisfies the requirements of the Digital Signature Standard (DSS) established by the National Institute of Standards and Technology, FIPS PUB 186-4, Digital Signature Algorithm Validation System, (2014), which is hereby incorporated by reference, as amended and supplemented. -

Virtualpatent - Enabling the Traceability of Ideas Shared Online Using Decentralized Trusted Timestamping
Bibliographic Details BibTeX, EndNote… Related Work Authors’ Details VirtualPatent - Enabling the Traceability of Ideas Shared Online using Decentralized Trusted Timestamping Corinna Breitinger Bela Gipp Department of Computer and Department of Computer and Information Science Information Science University of Konstanz University of Konstanz [email protected] [email protected] Abstract Online discussion and sharing platforms have enabled ideas to be disseminated more quickly than ever before. However, there are many good reasons why individuals hesitate to share their ideas online. In academia, for instance, researchers may not want their contribution to be made public until after it has been published to ensure that they are appropriately credited for their work. As a consequence, novel ideas or creative work tend to only be shared within a small circle of trusted peers instead of with wider audiences online. This status quo prevents other experts on a specific topic from contributing to the discussion. In this paper, we present a proof-of-concept implementation of an online discussion and sharing platform that addresses this problem. The web- based application, coined VirtualPatent, automatically timestamps each post a user shares by creating a distributed timestamp on the blockchain of the cryptocurrency Bitcoin – a method for trusted-timestamp creation that we published in a previous paper. Unlike platform-managed timestamps, timestamps stored on the blockchain are persistent and cannot be tampered with. The system thus enables the author of a posting made online to retrospectively prove the exact time that the specific contribution was first put forth in a tamperproof manner – similar to a published paper, but with the simplicity of writing a post on a social media website. -

Performance Analysis of Cryptographic Hash Functions Suitable for Use in Blockchain
I. J. Computer Network and Information Security, 2021, 2, 1-15 Published Online April 2021 in MECS (http://www.mecs-press.org/) DOI: 10.5815/ijcnis.2021.02.01 Performance Analysis of Cryptographic Hash Functions Suitable for Use in Blockchain Alexandr Kuznetsov1 , Inna Oleshko2, Vladyslav Tymchenko3, Konstantin Lisitsky4, Mariia Rodinko5 and Andrii Kolhatin6 1,3,4,5,6 V. N. Karazin Kharkiv National University, Svobody sq., 4, Kharkiv, 61022, Ukraine E-mail: [email protected], [email protected], [email protected], [email protected], [email protected] 2 Kharkiv National University of Radio Electronics, Nauky Ave. 14, Kharkiv, 61166, Ukraine E-mail: [email protected] Received: 30 June 2020; Accepted: 21 October 2020; Published: 08 April 2021 Abstract: A blockchain, or in other words a chain of transaction blocks, is a distributed database that maintains an ordered chain of blocks that reliably connect the information contained in them. Copies of chain blocks are usually stored on multiple computers and synchronized in accordance with the rules of building a chain of blocks, which provides secure and change-resistant storage of information. To build linked lists of blocks hashing is used. Hashing is a special cryptographic primitive that provides one-way, resistance to collisions and search for prototypes computation of hash value (hash or message digest). In this paper a comparative analysis of the performance of hashing algorithms that can be used in modern decentralized blockchain networks are conducted. Specifically, the hash performance on different desktop systems, the number of cycles per byte (Cycles/byte), the amount of hashed message per second (MB/s) and the hash rate (KHash/s) are investigated. -

Some Attacks on Merkle-Damgård Hashes
Overview Some Attacks on Merkle-Damg˚ardHashes John Kelsey, NIST and KU Leuven May 8, 2018 m m m m ||10*L 0 1 2 3 iv F h F h F h F h 0 1 2 final Introduction 1 / 63 Overview I Cryptographic Hash Functions I Thinking About Collisions I Merkle-Damg˚ardhashing I Joux Multicollisions[2004] I Long-Message Second Preimage Attacks[1999,2004] I Herding and the Nostradamus Attack[2005] Introduction 2 / 63 Why Talk About These Results? I These are very visual results{looking at the diagram often explains the idea. I The results are pretty accessible. I Help you think about what's going on inside hashing constructions. Introduction 3 / 63 Part I: Preliminaries/Review I Hash function basics I Thinking about collisions I Merkle-Damg˚ardhash functions Introduction 4 / 63 Cryptographic Hash Functions I Today, they're the workhorse of crypto. I Originally: Needed for digital signatures I You can't sign 100 MB message{need to sign something short. I \Message fingerprint" or \message digest" I Need a way to condense long message to short string. I We need a stand-in for the original message. I Take a long, variable-length message... I ...and map it to a short string (say, 128, 256, or 512 bits). Cryptographic Hash Functions 5 / 63 Properties What do we need from a hash function? I Collision resistance I Preimage resistance I Second preimage resistance I Many other properties may be important for other applications Note: cryptographic hash functions are designed to behave randomly. Cryptographic Hash Functions 6 / 63 Collision Resistance The core property we need. -

Block Cipher Based Hashed Functions
ANALYSIS OF THREE BLOCK CIPHER BASED HASH FUNCTIONS: WHIRLPOOL, GRØSTL AND GRINDAHL A THESIS SUBMITTED TO THE GRADUATE SCHOOL OF APPLIED MATHEMATICS OF MIDDLE EAST TECHNICAL UNIVERSITY BY RITA ISMAILOVA IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF DOCTOR OF PHYLOSOPHY IN CRYPTOGRAPHY SEPTEMBER 2012 Approval of the thesis: ANALYSIS OF THREE BLOCK CIPHER BASED HASH FUNCTIONS: WHIRLPOOL, GRØSTL AND GRINDAHL submitted by RITA ISMAILOVA in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Department of Cryptography, Middle East Technical University by, Prof. Dr. Bülent Karasözen ____________ Director, Graduate School of Applied Mathematics Prof. Dr. Ferruh Özbudak ____________ Head of Department, Cryptography Assoc. Prof. Dr. Melek Diker Yücel ____________ Supervisor, Department of Electrical and Electronics Engineering Examining Committee Members: Prof. Dr. Ersan Akyıldız ____________ Department of Mathematics, METU Assoc. Prof. Dr. Melek Diker Yücel ____________ Department of Electrical and Electronics Engineering, METU Assoc. Prof. Dr. Ali Doğanaksoy ____________ Department of Mathematics, METU Assist. Prof. Dr. Zülfükar Saygı ____________ Department of Mathematics, TOBB ETU Dr. Hamdi Murat Yıldırım ____________ Department of Computer Technology and Information Systems, Bilkent University Date: ____________ I hereby declare that all information in this document has been obtained and presented in accordance with academic rules and ethical conduct. I also declare that, as required by these rules and conduct, I have fully cited and referenced all material and results that are not original to this work. Name, Last Name: RITA ISMAILOVA Signature : iii ABSTRACT ANALYSIS OF THREE BLOCK CIPHER BASED HASH FUNCTIONS: WHIRLPOOL, GRØSTL AND GRINDAHL Ismailova, Rita Ph.D., Department of Cryptography Supervisor : Assoc. -

Foreword by Whitfield Diffie Preface About the Author Chapter 1
Applied Cryptography: Second Edition - Bruce Schneier Applied Cryptography, Second Edition: Protocols, Algorthms, and Source Code in C by Bruce Schneier Wiley Computer Publishing, John Wiley & Sons, Inc. ISBN: 0471128457 Pub Date: 01/01/96 Foreword By Whitfield Diffie Preface About the Author Chapter 1—Foundations 1.1 Terminology 1.2 Steganography 1.3 Substitution Ciphers and Transposition Ciphers 1.4 Simple XOR 1.5 One-Time Pads 1.6 Computer Algorithms 1.7 Large Numbers Part I—Cryptographic Protocols Chapter 2—Protocol Building Blocks 2.1 Introduction to Protocols 2.2 Communications Using Symmetric Cryptography 2.3 One-Way Functions 2.4 One-Way Hash Functions 2.5 Communications Using Public-Key Cryptography 2.6 Digital Signatures 2.7 Digital Signatures with Encryption 2.8 Random and Pseudo-Random-Sequence Generation Chapter 3—Basic Protocols 3.1 Key Exchange 3.2 Authentication 3.3 Authentication and Key Exchange 3.4 Formal Analysis of Authentication and Key-Exchange Protocols 3.5 Multiple-Key Public-Key Cryptography 3.6 Secret Splitting 3.7 Secret Sharing 3.8 Cryptographic Protection of Databases Chapter 4—Intermediate Protocols 4.1 Timestamping Services 4.2 Subliminal Channel 4.3 Undeniable Digital Signatures 4.4 Designated Confirmer Signatures 4.5 Proxy Signatures 4.6 Group Signatures 4.7 Fail-Stop Digital Signatures 4.8 Computing with Encrypted Data 4.9 Bit Commitment 4.10 Fair Coin Flips 4.11 Mental Poker 4.12 One-Way Accumulators 4.13 All-or-Nothing Disclosure of Secrets Page 1 of 666 Applied Cryptography: Second Edition - Bruce -
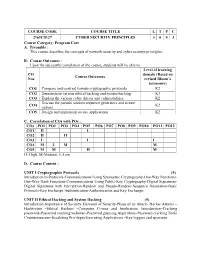
COURSE CODE COURSE TITLE L T P C 2161CS127 CYBER SECURITY PRINCIPLES 3 0 0 3 Course Category: Program Core A
COURSE CODE COURSE TITLE L T P C 2161CS127 CYBER SECURITY PRINCIPLES 3 0 0 3 Course Category: Program Core A. Preamble : This course describes the concepts of network security and cyber security principles. B. Course Outcomes : Upon the successful completion of the course, students will be able to: Level of learning CO domain (Based on Course Outcomes Nos. revised Bloom’s taxonomy) CO1 Compare and contrast various cryptographic protocols K2 CO2 Demonstrate various ethical hacking and system hacking K3 CO3 Explain the various cyber threats and vulnerabilities. K2 Discuss the pseudo random sequence generators and stream CO4 K2 ciphers CO5 Design and implement secure applications K2 C. Correlation of COs with POs : COs PO1 PO2 PO3 PO4 PO5 PO6 PO7 PO8 PO9 PO10 PO11 PO12 CO1 H L CO2 H H CO3 L L L CO4 M L M M CO5 M M H M H- High; M-Medium; L-Low D. Course Content : UNIT I Cryptographic Protocols (9) Introduction to Protocols-Communications Using Symmetric Cryptography-One-Way Functions- One-Way Hash Functions-Communications Using Public-Key Cryptography-Digital Signatures- Digital Signatures with Encryption-Random and Pseudo-Random-Sequence Generation-Basic Protocols-Key Exchange-Authentication-Authentication and Key Exchange. UNIT II Ethical Hacking and System Hacking (9) Introduction-Importance of Security-Elements of Security-Phase of an Attack- Hacker Attacks – Hacktivism –Ethical Hackers –Computer Crimes and Implication. Introduction–Cracking password–Password cracking websites–Password guessing Algorithms–Password cracking Tools Countermeasure–Escalating Privileges-Executing Applications –Key loggers and spywares. UNIT III Cyber Threats and Vulnerabilities (9) Cyber Threats-Cyber Activism-Cybercrime-Cyber Espionage-Cyber terrorism-Cyber Warfare- Cyber World Vulnerabilities-Cyber Operations-Cyber Weaponry-Society’s Critical Structures as Targets. -

On Probabilities of Hash Value Matches
Printer - please drop in Elsevier (tree) logo Computers 8 Security Vol. 17, No.2, pp. 171- 174, 1998 0 1998 Elsevier Science Limited All rights reserved. Printed in Great Britain 0167-4048/98 $19.00 On Probabilities of Hash Value Matches Mohammad Peyraviana, Allen Roginskya, Ajay Kshemkalyanib alBM Corporation, Research Triangle Park, NC 27709, USA bECECS Detlartment. University of Cincinnati, Cincinnati, OH 45221, USAL ’ ‘ _ Hash functions are used in authentication and cryptography, as hash function is said to be collision resistant if it is hard well as for the efficient storage and retrieval of data using hashed to find two input strings that map to the same hash keys. Hash functions are susceptible to undesirable collisions. To design or choose an appropriate hash function for an application, value.The problem of constructing fast hash functions it is essential to estimate the probabilities with which these colli- that also have low collision rates is studied in [S]. Key- sions can occur. In this paper we consider two problems: one of to-address transformation techniques for file access evaluating the probability of no collision at all and one of finding and their performance have been studied in [8]. Given a bound for the probability of a collision with a particular hash k, the number of hashed values that have been used in value. The quality of these estimates under various values of the parameters is also discussed. a hashing scheme in which input strings are mapped to random values, the expected number of locations Keywords: hash functions, security, cryptography, indexing, databases that must be looked at until an empty hashed value is found is formulated in [lo].