APPLIED CRYPTOGRAPHY, SECOND EDITION: Protocols
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Miss in the Middle
Miss in the middle By: Gal Leonard Keret Miss in the Middle Attacks on IDEA, Khufu and Khafre • Written by: – Prof. Eli Biham. – Prof. Alex Biryukov. – Prof. Adi Shamir. Introduction • So far we used traditional differential which predict and detect statistical events of highest possible probability. Introduction • A new approach is to search for events with probability one, whose condition cannot be met together (events that never happen). Impossible Differential • Random permutation: 휎 푀0 = 푎푛푦 퐶 표푓 푠푖푧푒 푀0. • Cipher (not perfect): 퐸 푀0 = 푠표푚푒 퐶 표푓 푠푖푧푒 푀0. • Events (푚 ↛ 푐) that never happen distinguish a cipher from a random permutation. Impossible Differential • Impossible events (푚 ↛ 푐) can help performing key elimination. • All the keys that lead to impossibility are obviously wrong. • This way we can filter wrong key guesses and leaving the correct key. Enigma – for example • Some of the attacks on Enigma were based on the observation that letters can not be encrypted to themselves. 퐸푛푖푔푚푎(푀0) ≠ 푀0 In General • (푀0, 퐶1) is a pair. If 푀0 푀0 → 퐶1. • 푀 ↛ 퐶 . 0 0 Some rounds For any key • ∀ 푘푒푦| 퐶1 → 퐶0 ↛ is an impossible key. Cannot lead to 퐶0. Some rounds Find each keys Decrypt 퐶1back to 퐶0. IDEA • International Data Encryption Algorithm. • First described in 1991. • Block cipher. • Symmetric. • Key sizes: 128 bits. • Block sizes: 64 bits. ⊕ - XOR. ⊞ - Addition modulo 216 ⊙ - Multiplication modulo 216+1 Encryption security • Combination of different mathematical groups. • Creation of "incompatibility“: ∗ • 푍216+1 → 푍216 ∗ • 푍216 → 푍216+1 ∗ ∗ Remark: 푍216+1 doesn’t contain 0 like 푍216 , so in 푍216+1 0 will be converted to 216 since 0 ≡ 216(푚표푑 216). -

Miss in the Middle Attacks on IDEA and Khufu
Miss in the Middle Attacks on IDEA and Khufu Eli Biham? Alex Biryukov?? Adi Shamir??? Abstract. In a recent paper we developed a new cryptanalytic techni- que based on impossible differentials, and used it to attack the Skipjack encryption algorithm reduced from 32 to 31 rounds. In this paper we describe the application of this technique to the block ciphers IDEA and Khufu. In both cases the new attacks cover more rounds than the best currently known attacks. This demonstrates the power of the new cryptanalytic technique, shows that it is applicable to a larger class of cryptosystems, and develops new technical tools for applying it in new situations. 1 Introduction In [5,17] a new cryptanalytic technique based on impossible differentials was proposed, and its application to Skipjack [28] and DEAL [17] was described. In this paper we apply this technique to the IDEA and Khufu cryptosystems. Our new attacks are much more efficient and cover more rounds than the best previously known attacks on these ciphers. The main idea behind these new attacks is a bit counter-intuitive. Unlike tra- ditional differential and linear cryptanalysis which predict and detect statistical events of highest possible probability, our new approach is to search for events that never happen. Such impossible events are then used to distinguish the ci- pher from a random permutation, or to perform key elimination (a candidate key is obviously wrong if it leads to an impossible event). The fact that impossible events can be useful in cryptanalysis is an old idea (for example, some of the attacks on Enigma were based on the observation that letters can not be encrypted to themselves). -

Giza and the Pyramids, Veteran Hosni Mubarak
An aeroplane flies over the pyramids and Sphinx on the Giza Plateau near Cairo. ARCHAEOLOGY The wonder of the pyramids Andrew Robinson enjoys a volume rounding up research on the complex at Giza, Egypt. n Giza and the Pyramids, veteran Hosni Mubarak. After AERAGRAM 16(2), 8–14; 2015), the tomb’s Egyptologists Mark Lehner and Zahi Mubarak fell from four sides, each a little more than 230 metres Hawass cite an Arab proverb: “Man power during the long, vary by at most just 18.3 centimetres. Ifears time, but time fears the pyramids.” It’s Arab Spring that year, Lehner and Hawass reject the idea that a reminder that the great Egyptian complex Hawass resigned, amid armies of Egyptian slaves constructed the on the Giza Plateau has endured for some controversy. pyramids, as the classical Greek historian four and a half millennia — the last monu- The Giza complex Herodotus suggested. They do, however, ment standing of that classical-era must-see invites speculation embrace the concept that the innovative list, the Seven Wonders of the World. and debate. Its three administrative and social organization Lehner and Hawass have produced an pyramids are the Giza and the demanded by the enormous task of build- astonishingly comprehensive study of the tombs of pharaohs Pyramids ing the complex were key factors in creating excavations and scientific investigations Khufu, Khafre and MARK LEHNER & ZAHI Egyptian civilization. CREATIVE GEOGRAPHIC L. STANFIELD/NATL JAMES that have, over two centuries, uncovered Menkaure, also known HAWASS The authors are also in accord over a the engineering techniques, religious and as Cheops, Chephren Thames & Hudson: theory regarding the purpose of the Giza cultural significance and other aspects of and Mycerinus, 2017. -

Encryption Block Cipher
10/29/2007 Encryption Encryption Block Cipher Dr.Talal Alkharobi 2 Block Cipher A symmetric key cipher which operates on fixed-length groups of bits, termed blocks, with an unvarying transformation. When encrypting, a block cipher take n-bit block of plaintext as input, and output a corresponding n-bit block of ciphertext. The exact transformation is controlled using a secret key. Decryption is similar: the decryption algorithm takes n-bit block of ciphertext together with the secret key, and yields the original n-bit block of plaintext. Mode of operation is used to encrypt messages longer than the block size. 1 Dr.Talal Alkharobi 10/29/2007 Encryption 3 Encryption 4 Decryption 2 Dr.Talal Alkharobi 10/29/2007 Encryption 5 Block Cipher Consists of two algorithms, encryption, E, and decryption, D. Both require two inputs: n-bits block of data and key of size k bits, The output is an n-bit block. Decryption is the inverse function of encryption: D(E(B,K),K) = B For each key K, E is a permutation over the set of input blocks. n Each key K selects one permutation from the possible set of 2 !. 6 Block Cipher The block size, n, is typically 64 or 128 bits, although some ciphers have a variable block size. 64 bits was the most common length until the mid-1990s, when new designs began to switch to 128-bit. Padding scheme is used to allow plaintexts of arbitrary lengths to be encrypted. Typical key sizes (k) include 40, 56, 64, 80, 128, 192 and 256 bits. -

Foreword by Whitfield Diffie Preface About the Author Chapter 1
Applied Cryptography: Second Edition - Bruce Schneier Applied Cryptography, Second Edition: Protocols, Algorthms, and Source Code in C by Bruce Schneier Wiley Computer Publishing, John Wiley & Sons, Inc. ISBN: 0471128457 Pub Date: 01/01/96 Foreword By Whitfield Diffie Preface About the Author Chapter 1—Foundations 1.1 Terminology 1.2 Steganography 1.3 Substitution Ciphers and Transposition Ciphers 1.4 Simple XOR 1.5 One-Time Pads 1.6 Computer Algorithms 1.7 Large Numbers Part I—Cryptographic Protocols Chapter 2—Protocol Building Blocks 2.1 Introduction to Protocols 2.2 Communications Using Symmetric Cryptography 2.3 One-Way Functions 2.4 One-Way Hash Functions 2.5 Communications Using Public-Key Cryptography 2.6 Digital Signatures 2.7 Digital Signatures with Encryption 2.8 Random and Pseudo-Random-Sequence Generation Chapter 3—Basic Protocols 3.1 Key Exchange 3.2 Authentication 3.3 Authentication and Key Exchange 3.4 Formal Analysis of Authentication and Key-Exchange Protocols 3.5 Multiple-Key Public-Key Cryptography 3.6 Secret Splitting 3.7 Secret Sharing 3.8 Cryptographic Protection of Databases Chapter 4—Intermediate Protocols 4.1 Timestamping Services 4.2 Subliminal Channel 4.3 Undeniable Digital Signatures 4.4 Designated Confirmer Signatures 4.5 Proxy Signatures 4.6 Group Signatures 4.7 Fail-Stop Digital Signatures 4.8 Computing with Encrypted Data 4.9 Bit Commitment 4.10 Fair Coin Flips 4.11 Mental Poker 4.12 One-Way Accumulators 4.13 All-or-Nothing Disclosure of Secrets Page 1 of 666 Applied Cryptography: Second Edition - Bruce -
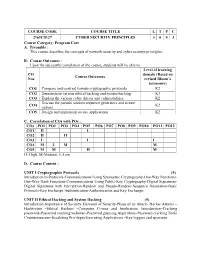
COURSE CODE COURSE TITLE L T P C 2161CS127 CYBER SECURITY PRINCIPLES 3 0 0 3 Course Category: Program Core A
COURSE CODE COURSE TITLE L T P C 2161CS127 CYBER SECURITY PRINCIPLES 3 0 0 3 Course Category: Program Core A. Preamble : This course describes the concepts of network security and cyber security principles. B. Course Outcomes : Upon the successful completion of the course, students will be able to: Level of learning CO domain (Based on Course Outcomes Nos. revised Bloom’s taxonomy) CO1 Compare and contrast various cryptographic protocols K2 CO2 Demonstrate various ethical hacking and system hacking K3 CO3 Explain the various cyber threats and vulnerabilities. K2 Discuss the pseudo random sequence generators and stream CO4 K2 ciphers CO5 Design and implement secure applications K2 C. Correlation of COs with POs : COs PO1 PO2 PO3 PO4 PO5 PO6 PO7 PO8 PO9 PO10 PO11 PO12 CO1 H L CO2 H H CO3 L L L CO4 M L M M CO5 M M H M H- High; M-Medium; L-Low D. Course Content : UNIT I Cryptographic Protocols (9) Introduction to Protocols-Communications Using Symmetric Cryptography-One-Way Functions- One-Way Hash Functions-Communications Using Public-Key Cryptography-Digital Signatures- Digital Signatures with Encryption-Random and Pseudo-Random-Sequence Generation-Basic Protocols-Key Exchange-Authentication-Authentication and Key Exchange. UNIT II Ethical Hacking and System Hacking (9) Introduction-Importance of Security-Elements of Security-Phase of an Attack- Hacker Attacks – Hacktivism –Ethical Hackers –Computer Crimes and Implication. Introduction–Cracking password–Password cracking websites–Password guessing Algorithms–Password cracking Tools Countermeasure–Escalating Privileges-Executing Applications –Key loggers and spywares. UNIT III Cyber Threats and Vulnerabilities (9) Cyber Threats-Cyber Activism-Cybercrime-Cyber Espionage-Cyber terrorism-Cyber Warfare- Cyber World Vulnerabilities-Cyber Operations-Cyber Weaponry-Society’s Critical Structures as Targets. -

Two Dozen Short Lessons in Haskell a Participatory Textbook on Functional Programming
Two Dozen Short Lessons in Haskell a participatory textbook on functional programming by Rex Page School of Computer Science University of Oklahoma Copyright © 1995, 1996, 1997 by Rex Page Permission to copy and use this document for educational or research purposes of a non-commercial nature is hereby granted, provided that this copyright notice is retained on all copies. All other rights reserved by author. Rex Page School of Computer Science University of Oklahoma 200 Felgar Street — EL114 Norman OK 73019 USA [email protected] Table of Contents 1.................................................................................................. How To Use This Book 5.................................................................................................... Hello World, Etc. 1 10..............................................................................................................Definitions 2 14...............................................................................How to Run Haskell Programs 3 17......................................... Computations on Sequences — List Comprehensions 4 21...................................................................... Function Composition and Currying 5 25.......................... Patterns of Computation — Composition, Folding, and Mapping 6 33......................................................................................................................Types 7 37........................................................ Function Types, Classes, and Polymorphism 8 42........................................... -

On Probability of Success in Linear and Differential Cryptanalysis
J. Cryptol. (2008) 21: 131–147 DOI: 10.1007/s00145-007-9013-7 On Probability of Success in Linear and Differential Cryptanalysis Ali Aydın Selçuk Department of Computer Engineering, Bilkent University, Ankara, 06800, Turkey [email protected] Communicated by Eli Biham Received 28 April 2003 and revised 7 August 2007 Online publication 14 September 2007 Abstract. Despite their widespread usage in block cipher security, linear and dif- ferential cryptanalysis still lack a robust treatment of their success probability, and the success chances of these attacks have commonly been estimated in a rather ad hoc fashion. In this paper, we present an analytical calculation of the success probability of linear and differential cryptanalytic attacks. The results apply to an extended sense of the term “success” where the correct key is found not necessarily as the highest-ranking candidate but within a set of high-ranking candidates. Experimental results show that the analysis provides accurate results in most cases, especially in linear cryptanalysis. In cases where the results are less accurate, as in certain cases of differential cryptanaly- sis, the results are useful to provide approximate estimates of the success probability and the necessary plaintext requirement. The analysis also reveals that the attacked key length in differential cryptanalysis is one of the factors that affect the success probabil- ity directly besides the signal-to-noise ratio and the available plaintext amount. Key words. Block ciphers, Linear cryptanalysis, Differential cryptanalysis, Success probability, Order statistics. 1. Introduction Differential cryptanalysis (DC) [1] and linear cryptanalysis (LC) [11,12]aretwoofthe most important techniques in block cipher cryptanalysis today. -

Cryptography
University of Indonesia Magister of Information Technology Cryptography Arrianto Mukti Wibowo University of Indonesia – University of Budi Luhur Magister of Information Technology Tujuan • Mempelajari berbagai metode dan teknik penyembunyian data menggunakan kriptografi. University of Indonesia – University of Budi Luhur Magister of Information Technology Topik • Symmetric & asymmetric cryptography, key strength, cryptosystems, public key infrastructure (PKI), one-way function, hash function, key management, cryptographic attacks University of Indonesia – University of Budi Luhur Magister of Information Technology Cryptography Issues (Schneier ‟96) • Kerahasiaan (confidentiality) dijamin dengan melakukan enkripsi (penyandian). • Keutuhan (integrity) atas data-data pembayaran dilakukan dengan fungsi hash satu arah. • Jaminan atas identitas dan keabsahan (authenticity) pihak-pihak yang melakukan transaksi dilakukan dengan menggunakan password atau sertifikat digital. Sedangkan keotentikan data transaksi dapat dilakukan dengan tanda tangan digital. • Transaksi dapat dijadikan barang bukti yang tidak bisa disangkal (non-repudiation) dengan memanfaatkan tanda tangan digital dan sertifikat digital. University of Indonesia – University of Budi Luhur Magister of Information Technology Makna Kriptografi • Krupto + Grafh = secret + writing • Cryptography: ilmu untuk membuat sebuah pesan menjadi aman University of Indonesia – University of Budi Luhur Magister of Information Technology Cryptographic algorithm & key • Cipher: fungsi matematika yang -

Analyses of Curupira Block Cipher
VIII Simpósio Brasileiro em Segurança da Informação e de Sistemas Computacionais 89 Analyses of Curupira Block Cipher Jorge Nakahara Jr 1jorge [email protected] Abstract. Curupira is a 96-bit block cipher, with keys of 96, 144 or 192 bits, and variable number of rounds, an algorithm described at SBRC 2007. This paper1 presents impossible-differential, boomerang and higher-order multiset attacks on reduced-round versions of Curupira, that were not previously considered in the security analysis by its designers. Also, we provide security analyses based solely on the block size and on the key size of the cipher, such as plaintext leakage and related-key attacks. Our analyses indicate new attacks on up to 6-round Curupira. 1. Introduction Curupira is a block cipher designed by Barreto and Simpl´ıcio and presented at SBRC 2007 [Barreto and Simpl´ıcio Jr 2007]. This cipher has a Substitution Permutation Net- work (SPN) structure, like the AES [AES 1997] and is based on the wide-trail design strategy [Daemen 1995]. In [Barreto and Simpl´ıcio Jr 2007], the designers of Curupira argued about its security under several attack settings. The best reported attack was the square or saturation attack [Daemen et al. 1997] on up to seven rounds of Curupira, with a complexity smaller than that of an exhaustive key search. In this paper, we describe impossible-differential (ID), boomerang and higher-order multiset attacks on reduced- round versions of Curupira. The motivation for the ID and boomerang attacks are the fact that these techniques exploit the cipher from both the encryption and decryption di- rections, namely, the corresponding distinguishers are based on differentials constructed from both ends of a given cipher. -

The GCHQ Protocol and Its Problems
The GCHQ Protocol and Its Problems Ross Anderson, Michael Roe Cambridge University Computer Laboratory Pembroke Street, Cambridge CB2 3QG Email: (rjal4,mrr)@cl. cam.ac .uk Abstract. The UK government is fielding an architecture for secure electronic mail based on the NSA’s Message Security Protocol, with a key escrow scheme inspired by Diffie-Hellman. Attempts have been made to have this protocol adopted by other governments and in various do- mestic applications. The declared policy goal is to entrench commercial key escrow while simultaneously creating a large enough market that software houses will support the protocol as a standard feature rather than charging extra for it. We describe this protocol and show that, like the ‘Clipper’ proposal of a few years ago, it has a number of problems. It provides the worst of both secret and public key systems, without delivering the advantages of ei- ther; it does not support nonrepudiation; a.nd there are serious problems with the replacement of compromised keys, the protection of security la- bels, and the support of complex or dynamic administrative structures. 1 Introduction Over the last two years, the British government’s crypto policy has changed completely. Whereas in 1994 the Primc Minister assured the House of Com- mons that no further restrictions on encryption were envisaged, we now find the government proposing to introduce a licensing scheme for ‘trusted third par- ties’, and licenses will only be granted to operators that escrow their customers’ confidentiality keys to the government’s satisfaction [ll,211. In March 1996, a document describing the cryptographic protocols to he used in government electronic mail systems was issued by CESG, the department of GCHQ concerned with the protection of government information; it has since been made available on the worldwide web [4]. -

Pyramids of the Giza Plateau Pyramid Complexes of Khufu, Khafre, and Menkaure
Pyramids of the Giza Plateau Pyramid Complexes of Khufu, Khafre, and Menkaure Charles Rigano AuthorHouse™ 1663 Liberty Drive Bloomington, IN 47403 www.authorhouse.com Phone: 1-800-839-8640 © 2014 Charles Rigano. All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted by any means without the written permission of the author. Published by AuthorHouse 05/14/2015 ISBN: 978-1-4969-5249-3 (sc) ISBN: 978-1-4969-5248-6 (e) Any people depicted in stock imagery provided by Thinkstock are models, and such images are being used for illustrative purposes only. Certain stock imagery © Thinkstock. Because of the dynamic nature of the Internet, any web addresses or links contained in this book may have changed since publication and may no longer be valid. The views expressed in this work are solely those of the author and do not necessarily reflect the views of the publisher, and the publisher hereby disclaims any responsibility for them. Front Cover: - Khufu’s Great Pyramid at dusk as seen from near the Sphinx. Photo by the author. Back Cover: Top - The three Giza Pyramids from close to far: Menkaure and subsidiary pyramids, Khafre, and Khufu. Photo by author. Bottom - Author Charles Rigano with Menkaure’s Pyramid in the background. Author’s photo. Contents Preface The Gizeh Plateau Area Surrounding the Giza Plateau Giza Plateau Pyramid Complexes Chapter 1: The Giza Plateau Chapter 2: Khufu’s Pyramid Exterior Chapter 3: Khufu’s Pyramid Interior Chapter 4: Khufu’s Mortuary Complex Chapter 5: Khufu’s Pyramid – Designing, Closing, and Opening Chapter 6: Khafre’s Pyramid Site Chapter 7: Khafre’s Pyramid Interior Chapter 8: Khafre’s Mortuary Complex Chapter 9: The Sphinx Complex Chapter 10: Menkaure’s Pyramid Exterior Chapter 11: Menkaure’s Pyramid Interior Chapter 12: Menkaure’s Mortuary Complex Appendix: The Tuthmosis IV Stele Between the Sphinx Paws Photo Credits Suggested Reading and References Preface I remember the moment in 1970 that my fascination for Ancient Egypt started.