Tivoli Workload Scheduler for Z/OS: Customization and Tuning
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

AMPERSAND an International Journal of General and Applied Linguistics
AMPERSAND An International Journal of General and Applied Linguistics AUTHOR INFORMATION PACK TABLE OF CONTENTS XXX . • Description p.1 • Abstracting and Indexing p.2 • Editorial Board p.2 • Guide for Authors p.4 ISSN: 2215-0390 DESCRIPTION . Serving the breadth of the general and applied linguistics communities, Ampersand offers a highly- visible, open-access home for authors. An international, peer-reviewed journal, Ampersand welcomes submissions in applied and historical linguistics, phonetics, phonology, pragmatics, semantics, sociolinguistics and syntax. Ampersand provides authors with an open-access venue to disseminate a wide range of linguistic research in an equally wide range of formats, prioritizing rapid peer review and publication so that researchers can share their work in its most current and innovative form. In response to the global thrust toward open source, open data and open access in science, Ampersand offers the opportunity for authors to make their research freely available to everyone, opening their work to a wider audience and increased readership. Ampersand caters to a comprehensive audience, ranging from language researchers, linguists, teachers, educationalists, practitioners to those with a general interest in language and linguistics. The journal aims to encourage the free exchange of information between researchers by being a forum for the constructive discussion and debate of issues in both theoretical and applied research. The journal welcomes all types of submission format: traditional 'full' research articles, short communications, opinion pieces, book reviews, case studies and literature reviews. Ampersand also offers the opportunity to publish special issues or sections to reflect current interest and research in topical or developing areas. The journal fully supports authors wanting to present their research in an innovative fashion through the use of modern multimedia in the award-winning 'article of the future' format on ScienceDirect?. -
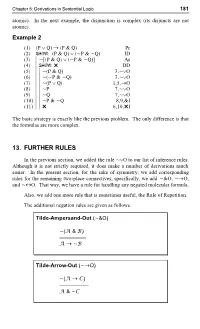
Tilde-Arrow-Out (~→O)
Chapter 5: Derivations in Sentential Logic 181 atomic). In the next example, the disjunction is complex (its disjuncts are not atomic). Example 2 (1) (P ´ Q) → (P & Q) Pr (2) •: (P & Q) ∨ (~P & ~Q) ID (3) |~[(P & Q) ∨ (~P & ~Q)] As (4) |•: ¸ DD (5) ||~(P & Q) 3,~∨O (6) ||~(~P & ~Q) 3,~∨O (7) ||~(P ∨ Q) 1,5,→O (8) ||~P 7,~∨O (9) ||~Q 7,~∨O (10) ||~P & ~Q 8,9,&I (11) ||¸ 6,10,¸I The basic strategy is exactly like the previous problem. The only difference is that the formulas are more complex. 13. FURTHER RULES In the previous section, we added the rule ~∨O to our list of inference rules. Although it is not strictly required, it does make a number of derivations much easier. In the present section, for the sake of symmetry, we add corresponding rules for the remaining two-place connectives; specifically, we add ~&O, ~→O, and ~↔O. That way, we have a rule for handling any negated molecular formula. Also, we add one more rule that is sometimes useful, the Rule of Repetition. The additional negation rules are given as follows. Tilde-Ampersand-Out (~&O) ~(d & e) ––––––––– d → ~e Tilde-Arrow-Out (~→O) ~(d → f) –––––––––– d & ~f 182 Hardegree, Symbolic Logic Tilde-Double-Arrow-Out (~±O) ~(d ± e) –––––––––– ~d ± e The reader is urged to verify that these are all valid argument forms of sentential logic. There are other valid forms that could serve equally well as the rules in question. The choice is to a certain arbitrary. The advantage of the particular choice becomes more apparent in a later chapter on predicate logic. -

Introducing Sentential Logic (SL) Part I – Syntax
Introducing Sentential Logic (SL) Part I – Syntax 1. As Aristotle noted long ago, some entailments in natural language seem to hold by dint of their “logical” form. Consider, for instance, the example of Aristotle’s being a logician above, as opposed to the “material” entailment considering the relative locations of Las Vegas and Pittsburgh. Such logical entailment provides the basic motivation for formal logic. So-called “formal” or “symbolic” logic is meant in part to provide a (perhaps idealized) model of this phenomenon. In formal logic, we develop an artificial but highly regimented language, with an eye perhaps of understanding natural language devices as approximating various operations within that formal language. 2. We’ll begin with a formal language that is commonly called either Sentential Logic (SL) or, more high- falutinly, “the propositional calculus.” You’re probably already quite familiar with it from an earlier logic course. SL is composed of Roman capital letters (and subscripted capital letters), various operators (or functors), and left and right parentheses. The standard operators for SL include the tilde (~), the ampersand (&), the wedge (v), and the arrow (→). Other operators, such as the double arrow, the stroke and the dagger, can easily be added as the need arises. The Syntax of S.L 3. A syntax for a language specifies how to construct meaningful expressions within that language. For purely formal languages such as SL, we can understand such expressions as well-formed formulas (wffs). The syntax of SL is recursive. That means that we start with basic (or atomic) wffs, and then specify how to build up more complex wffs from them. -

List of Approved Special Characters
List of Approved Special Characters The following list represents the Graduate Division's approved character list for display of dissertation titles in the Hooding Booklet. Please note these characters will not display when your dissertation is published on ProQuest's site. To insert a special character, simply hold the ALT key on your keyboard and enter in the corresponding code. This is only for entering in a special character for your title or your name. The abstract section has different requirements. See abstract for more details. Special Character Alt+ Description 0032 Space ! 0033 Exclamation mark '" 0034 Double quotes (or speech marks) # 0035 Number $ 0036 Dollar % 0037 Procenttecken & 0038 Ampersand '' 0039 Single quote ( 0040 Open parenthesis (or open bracket) ) 0041 Close parenthesis (or close bracket) * 0042 Asterisk + 0043 Plus , 0044 Comma ‐ 0045 Hyphen . 0046 Period, dot or full stop / 0047 Slash or divide 0 0048 Zero 1 0049 One 2 0050 Two 3 0051 Three 4 0052 Four 5 0053 Five 6 0054 Six 7 0055 Seven 8 0056 Eight 9 0057 Nine : 0058 Colon ; 0059 Semicolon < 0060 Less than (or open angled bracket) = 0061 Equals > 0062 Greater than (or close angled bracket) ? 0063 Question mark @ 0064 At symbol A 0065 Uppercase A B 0066 Uppercase B C 0067 Uppercase C D 0068 Uppercase D E 0069 Uppercase E List of Approved Special Characters F 0070 Uppercase F G 0071 Uppercase G H 0072 Uppercase H I 0073 Uppercase I J 0074 Uppercase J K 0075 Uppercase K L 0076 Uppercase L M 0077 Uppercase M N 0078 Uppercase N O 0079 Uppercase O P 0080 Uppercase -
Form 1094-C Schema to Form Crosswalk
Element Form 1094-C XML Schema Elements Form Line Required eFile Type eFile Type Definition minOccurs maxOccurs Description Form1094CUpstreamDetailType Number or Optional SubmissionId N/A SubmissionIdType string 1 1 Required A sequential number (non-negative integer) that uniquely identifies each maxLength value="10" submission within a transmission - every Form 1094-C requires a SubmissionId. pattern value="[1-9][0-9]*" SubmissionId should start at 1 and increment by 1 sequentially for each Form 1094- C in the transmission. OriginalUniqueSubmissionId N/A UniqueSubmissionIdType string 0 1 Optional Global type for the Original Unique Submission Identifier. pattern value="[^\s].[^\s]{1,80}\|[1-9]{1}[0- The UniqueSubmission Identifier for 1094-C is as follows: 9]{0,15}"/> ReceiptId|SubmissionId TestScenarioId N/A TestScenarioIdType string 0 1 Optional The TestScenarioId is only applicable to transmissions submitted to AATS and pattern ([1-9]|[1-9][0-9])C{0,1}-([0-9]|[1-9][0- identifies which test scenario the Form 1094-C represents. 9]) TaxYr N/A YearType string 1 1 Required IRS TaxYr is the tax year for which the data on the Form 1094-C is being submitted. pattern value="[1-9][0-9]{3}"/ Base type for a year in the format of YYYY. CorrectedInd N/A DigitBooleanType string 1 1 Required CorrectedInd indicates if the record is an original (0) or a correction (1) to a record enumerations: that the IRS has already received, processed, and accepted. "0" or" 1" CorrectedSubmissionInfoGrp N/A CorrectedSubmissionInfoGrpType complexType 0 1 Optional CorrectedSubmissionInfoGrp contains Information to identify the submission being corrected. CorrectedUniqueSubmissionId N/A UniqueSubmissionIdType string 1 1 Required CorrectedUniqueSubmissionId is the unique submission identifier of the pattern value="[^\s].[^\s]{1,80}\|[1-9]{1}[0- submission being corrected. -
Form 1094-C Form to Schema Crosswalk
Element Form 1094-C XML Schema Elements Form Line Required eFile Type eFile Type Definition minOccurs maxOccurs Description Form1094CUpstreamDetailType Number or Optional* SubmissionId N/A SubmissionIdType string 1 1 Required A sequential number (non-negative integer) that uniquely identifies each maxLength value="10" submission within a transmission - every Form 1094-C requires a SubmissionId. pattern value="[1-9][0-9]*" SubmissionId should start at 1 and increment by 1 sequentially for each Form 1094- C in the transmission. OriginalUniqueSubmissionId N/A UniqueSubmissionIdType string 0 1 Optional Global type for the Original Unique Submission Identifier. pattern value="[^\s].[^\s]{1,80}\|[1-9]{1}[0- The UniqueSubmission Identifier for 1094-C is as follows: 9]{0,15}"/> ReceiptId|SubmissionId TestScenarioId N/A TestScenarioIdType string 0 1 Optional The TestScenarioId is only applicable to transmissions submitted to AATS and pattern ([1-9]|[1-9][0-9])C{0,1}-([0-9]|[1- identifies which test scenario the Form 1094-C represents. 9][0-9]) TaxYr N/A YearType string 1 1 Required IRS TaxYr is the tax year for which the data on the Form 1094-C is being submitted. pattern value="[1-9][0-9]{3}"/ Base type for a year in the format of YYYY. CorrectedInd N/A DigitBooleanType string 1 1 Required CorrectedInd indicates if the submission is an original (0) or a correction (1) to a enumerations: submission that the IRS has already received, processed, and accepted. "0" or" 1" CorrectedSubmissionInfoGrp N/A CorrectedSubmissionInfoGrpType complexType 0 1 Optional CorrectedSubmissionInfoGrp contains Information to identify the submission being corrected. CorrectedUniqueSubmissionId N/A UniqueSubmissionIdType string 1 1 Required CorrectedUniqueSubmissionId is the unique submission identifier of the pattern value="[^\s].[^\s]{1,80}\|[1-9]{1}[0- submission being corrected. -

APA Style for Citing References
APA Style for Citing References APA style requires two elements for citing outside sources: brief parenthetical citations in the text of a paper, and a detailed References list at the end. Together, these elements allow your reader to know and to access the sources you used. For the system to function, all sources cited in the text must appear in the References list, and all sources listed in the References list must be cited in the text. For more information, go to library.uml.edu (if needed, access via "Off Campus Users Login), select <Create a Bibliography>, scroll down to the "Websites" section and select <American Psychological Association formats>, then <Create an APA reference list>. Citations in Text APA style calls for at least two pieces of information to be included whenever citing the source of information presented in the text of a paper. The author’s surname, followed by a comma and the work’s date of publication, must always appear, and these items must match the corresponding entry in the references list (same surnames, same order, same year). A third possible piece of information, the page number (or for unpaged websites, the paragraph number), must be used for any direct quotation. For articles with multiple authors, use all authors’ surnames, in correct order, separated by commas, with ampersand (&) before the last surname. The use of ‘et al.’ (literally, “and others”) is permitted only when there are 7 or more authors, or whenever the citation, with all authors’ names, has already been used once in the paper. If the author is an organization, use the organization's full name, in normal word order. -

Logo & Trademark Use Guidelines
Logo & Trademark Use Guidelines • The Stellar Industries, Inc. logos, as well as any other trademark names and designs used by or for the above mentioned must be reproduced from the authorized reproductions or files and cannot be redrawn, re-proportioned, separated, cut apart or modified in any way. • The size and spacing in the logo may not be changed. • The logo may be reduced or enlarged proportionately (follow aspect ratio listed with each logo). • The main Stellar logo aspect ratio is 2.38:1. Definition: Aspect ratio is the ratio between the width of the picture and the height of the picture. The Stellar logo is to be proportioned at 2.38” wide to every 1” high. • Alterations, squeezing, and/or stretching in any direction of any of the logos is not permitted. • Colors of the logo – Deviations from these colors are not allowed with out prior written approval from the Stellar Marketing/Communications Department. Stellar Colors: Pantone Matching System: CMYK Process Colors: Web safe colors allowed: Red: 1805 Red: C=17, M=98, Y=100, K=7 Red: #c12726 Blue: 287 Blue: C=100, M=69, Y=0, K=11.5 Blue: #003366 Gray: C=, M=5, Y=5, K=25 Gray: #CCCCCC Gray: Cool Gray 7 • Thread colors must match the above mentioned Pantone or Process Colors. Deviations from these colors are not allowed with out prior written approval from the Stellar Marketing/Communications Department. Stitch count is approxi- mately 3,400. • Thread may be all the same color of the item (embossed look) as long as entire logo is one color. -

Rule 1. to Avoid Confusion, Use Commas to Separate Words And
BASIC RULES OF GRAMMAR A paragraph is a unit of thought that develops an idea. A traditional paragraph contains a topic sentence that states the idea to be developed, plus additional sentences that develop the idea stated by the topic sentence. In U.S. formal academic English, paragraphs have three principal parts. These three parts are the topic sentence, body sentences, and the concluding sentence. (http://lrs.ed.uiuc.edu/students/fwalters/para.html) Comma Rule To avoid confusion, use commas to separate words and word groups 1. with a series of three or more. Example: My $10 million estate is to be split among my husband, daughter, son, and nephew. Omitting the comma after son would indicate that the son and nephew would have to split one-third of the estate. Rule Use a comma to separate two adjectives when the word and can be 2. inserted between them. Examples: He is a strong, healthy man. We stayed at an expensive summer resort. You would not say expensive and summer resort, so no comma. Rule Use a comma when an -ly adjective is used with other adjectives. 3. NOTE: To test whether an -ly word is an adjective, see if it can be used alone with the noun. If it can, use the comma. Examples: Felix was a lonely, young boy. I get headaches in brightly lit rooms. Brightly is not an adjective because it cannot be used alone with rooms; therefore, no comma is used between brightly and lit. 1 Rule Use commas before or surrounding the name or title of a person 4. -

Publication 28 Contents
Contents 1 Introduction. 1 11 Background . 1 111 Purpose . 1 112 Scope . 1 113 Additional Benefits . 1 12 Overview . 2 121 Address and List Maintenance . 2 122 List Correction. 2 123 Updates. 2 124 Address Output . 3 125 Deliverability . 3 13 Address Information Systems Products and Services . 3 2 Postal Addressing Standards . 5 21 General . 5 211 Standardized Delivery Address Line and Last Line. 5 212 Format . 5 213 Secondary Address Unit Designators . 6 214 Attention Line . 7 215 Dual Addresses . 7 22 Last Line of the Address. 8 221 City Names . 8 222 Punctuation . 8 223 Spelling of City Names . 8 224 Format . 9 225 Military Addresses. 9 226 Preprinted Delivery Point Barcodes . 9 23 Delivery Address Line . 10 231 Components . 10 232 Street Name . 10 233 Directionals . 11 234 Suffixes . 13 235 Numeric Street Names . 13 236 Corner Addresses . 14 237 Highways. 14 238 Military Addresses. 14 239 Department of State Addresses . 15 June 2020 i Postal Addressing Standards 24 Rural Route Addresses. 15 241 Format . 15 242 Leading Zero . 16 243 Hyphens . 16 244 Designations RFD and RD . 16 245 Additional Designations . 16 246 ZIP+4. 16 25 Highway Contract Route Addresses . 17 251 Format . 17 252 Leading Zero . 17 253 Hyphens . 17 254 Star Route Designations . 17 255 Additional Designations . 18 256 ZIP+4. 18 26 General Delivery Addresses . 18 261 Format . 18 262 ZIP Code or ZIP+4 . 18 27 United States Postal Service Addresses . 19 271 Format . 19 272 ZIP Code or ZIP+4 . 19 28 Post Office Box Addresses. 19 281 Format . 19 282 Leading Zero . -

2019 Other Federal Agencies Annual Charges
ACTUAL FEDERAL ENERGY REGULATORY COMMISSION OFFICE OF THE CHIEF FINANCIAL OFFICER ASSESSMENT TABLE FOR OTHER FEDERAL AGENCIES CHARGES FISCAL YEAR 2019 Prorated Annual Annual Individual Project Annual Project Licensee Capacity Generated Pumped Charge Type Charge (KW) (MWH) (MWH) Factor PRIVATE LICENSEES Other Federal Agency Cost $3,789,728 Maximum Charge $122,427 Total Charge for Projects above Maximum Charge (3 Projects) $367,281 Total Other Federal Agency Cost less Charges for Projects above Maximum $3,422,447 Total Charge Factor 43,229,646 Total Individual Charge Factors (ICFs) for Projects above Maximum 6,058,766 Total Charge Factor less Total ICFs for Projects above Maximum 37,170,880 Unit Charge Factor 0.092073 00013 GREEN ISLAND AND POWER AUTHORITY A 6,000 40,272 0 10,531 $970 00018 IDAHO POWER COMPANY A 42,217 154,296 0 59,575 $5,485 00020 PACIFICORP A 77,450 138,824 0 93,068 $8,569 00067 SOUTHERN CALIFORNIA EDISON CO. C 373,350 773,614 27,643 458,309 $42,198 00077 PACIFIC GAS & ELECTRIC COMPANY A 9,959 16,862 0 11,856 $1,092 00082 ALABAMA POWER COMPANY A 170,000 589,256 0 236,291 $21,756 00096 PACIFIC GAS & ELECTRIC COMPANY A 162,720 589,736 0 229,065 $21,091 00120 SOUTHERN CALIFORNIA EDISON CO. A 165,376 863,078 0 262,472 $24,167 00137 PACIFIC GAS & ELECTRIC COMPANY A 206,004 888,195 0 305,926 $28,168 00175 PACIFIC GAS & ELECTRIC COMPANY A 130,500 677,680 0 206,739 $19,035 00178 PACIFIC GAS & ELECTRIC COMPANY A 11,475 0 0 11,475 $1,057 00233 PACIFIC GAS & ELECTRIC COMPANY A 312,330 1,597,445 0 492,043 $45,304 00271 ENTERGY ARKANSAS, INC A 65,300 257,085 0 94,222 $8,675 00287 MIDWEST HYDRO, LLC A 3,680 22,983 0 6,266 $577 00289 LOUISVILLE GAS & ELECTRIC COMPANY A 100,656 192,579 0 122,321 $11,262 00298 SOUTHERN CALIFORNIA EDISON CO. -

Supplement to Chapter 20 Another Form of Demorgan's Rule
Supplement to Chapter 20 Another Form of DeMorgan’s Rule: The DeMorgan Algorithm DeMorgan’s rule (“DM”) allows us to replace a sentence of the form ~(P & Q) with the corresponding sentence ~ P v ~ Q, and vice versa, that is, it allows us to replace a sentence of the form ~ P v ~ Q with the corresponding sentence ~(P & Q). Of course, DeMorgan’s rule also allows us to replace a sentence of the form ~ (P v Q) with the corresponding sentence ~ P & ~Q, and vice versa. Notice that DM “drives” the tildes inside, that is, in these cases, it shifts the tilde from the outside of the brackets onto the inside letters. At the same time, the wedge changes to the ampersand or the ampersand changes to the wedge, of course. An algorithm is a very precise, step-by-step procedure for carrying out a specific task. The purpose of this supplement is to present a little three-step algorithm that captures the essential logic of the DeMorgan rule. Using this algorithm, you will be able to make every replacement you would make using the original DeMorgan rule, plus many more. I like to add this algorithm to our proof system, and thus count any use of it as an application of the DM rule. Here is the “DeMorgan Algorithm.” DeMorgan Algorithm If a formula, or a subformula within a formula, contains an ampersand, or wedge, as its main connective, you may: 1. Change the ampersand to a wedge, or the wedge to an ampersand, as the case may be.