Group Policy 10/21/2014
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
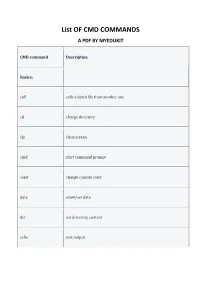
List of CMD COMMANDS a PDF by MYEDUKIT
List OF CMD COMMANDS A PDF BY MYEDUKIT CMD command Description Basics: call calls a batch file from another one cd change directory cls clear screen cmd start command prompt color change console color date show/set date dir list directory content echo text output exit exits the command prompt or a batch file find find files hostname display host name pause pauses the execution of a batch file and shows a message runas start a program as another user shutdown shutdown the computer sort sort the screen output start start an own window to execute a program or command taskkill terminate a process or an application tasklist display applications and related tasks time display/edit the system time timeout wait any time title set title for prompt ver display operating system version w32tm setting time synchronisation/time server/time zone Network: ftp transfer files to an FTP server ftype display file type and mapping getmac display MAC address ipconfig display IP network settings netsh configure/control/display network components netstat display TCP/IP connections and status nslookup query the DNS pathping test the connection to a specific IP address ping pings the network route display network routing table, add static routes systeminfo displays computer-specific properties and configurations telnet establish a Telnet connection tftp transfer files to a TFTP server tracert trace routes similar to patchping Files: attrib display file attributes comp compare file contents compact display/change file compression copy / xcopy copy files diskcomp -

Prepare Customer Site Servers
Prepare Customer Site Servers • Prepare Customer Site Servers, on page 1 • Prepare Cisco UCS C-Series Customer Site Servers, on page 1 • Prepare HyperFlex M5 series Customer Site Servers, on page 3 • NTP and Time Synchronization, on page 4 • Global Catalog Requirements, on page 5 Prepare Customer Site Servers Perform all the procedures in this section on the Side A and the Side B servers. Prepare Cisco UCS C-Series Customer Site Servers Configure RAID for C240 M4SX The disk array configuration for the C240 M4SX is already set up to match what is required for Packaged CCE. Verify the settings as follows. Using Cisco Integrated Management Controller, check that the following settings are configured correctly: • Virtual Drive Info: RAID 5 with 5 (Physical Disks) * 4 (Virtual Drives/Datastores) • Stripe Size: 128KB • Write Policy: Write Back with BBU • Read Policy: Read Ahead Always For more information regarding RAID configuration for C240 M4SX in Configure RAID with GUI (UCS C-Series M4 Servers) section, see Cisco Collaboration on Virtual Servers Guide at: https://www.cisco.com/ c/en/us/td/docs/voice_ip_comm/cucm/virtual/CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers/ CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers_chapter_01.html#CUCM_TK_C2DC4F2D_ 00. Prepare Customer Site Servers 1 Prepare Customer Site Servers Run the RAID Config Validator Utility Run the RAID Config Validator Utility After you set up RAID configuration and add the datastores, run the RAID Config Validator utility to ensure that your datastore configuration is correct. Before you begin To run the utility, Java 7 (any update) must be installed. Java 8 and later releases are not supported. -

Deployment Strategy
System Management Best Practices Bryan S Owen PE Copyright c 2004 OSIsoft Inc. All rights reserved. Richness & Reliability “Value Coefficients” • Quality – Across operations and data systems • Quantity – Across business needs and over time • Utilization – Across enterprise and just in time It all Starts with Great Software …and the Right Architecture • Visualization Tools • Availability • Reliability • Security Integrated Data Collection Proven: Cutting Edge: Integrated Interface Embedded Historian Embedded PI Historian • Continuous Historian for DeltaV Application Station http://www.easydeltav.com/pd/PDS_ApplicationStation.pdf • “56SAM” Historian for Allen-Bradley ControlLogix www.oldi.com • “Promoted” Interface Node • Also visit: www.echohistorian.com Fault Tolerant vs Redundant Incident Tolerant Redundant Environment Fault JJ JJJ Hardware Fault JJJ JJ Software Fault K J Administrative Error JK JJ Scheduled Down K JJJ “Smile” Points: 15/30 22/30 Redundant Architecture • Reliability – Build from the Data Up • Availability – Build from the Users Down You decide what comes first! Redundant Data Collection Dual Gateways Interface Node Failover Redundant Data Service Dual PI Servers Dual PI Clients Redundant Architecture No single point of failure sounds great, what’s the catch? • Interface Support • History Recovery • Gap Filling • Client Impact • Fugitive Data Fugitive Data Capture Essential for rich content but… 1% of the data causes 99% perspiration! • Manual Entry Systems • Custom Applications • Isolated Point to Point Links Solution: -

Microsoft Windows Server 2019 Version 1809 Hyper-V
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

Operational and Administrative Guidance
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

EMC® Data Domain® Operating System 5.7 Administration Guide
EMC® Data Domain® Operating System Version 5.7 Administration Guide 302-002-091 REV. 02 Copyright © 2010-2016 EMC Corporation. All rights reserved. Published in the USA. Published March, 2016 EMC believes the information in this publication is accurate as of its publication date. The information is subject to change without notice. The information in this publication is provided as is. EMC Corporation makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose. Use, copying, and distribution of any EMC software described in this publication requires an applicable software license. EMC², EMC, and the EMC logo are registered trademarks or trademarks of EMC Corporation in the United States and other countries. All other trademarks used herein are the property of their respective owners. For the most up-to-date regulatory document for your product line, go to EMC Online Support (https://support.emc.com). EMC Corporation Hopkinton, Massachusetts 01748-9103 1-508-435-1000 In North America 1-866-464-7381 www.EMC.com 2 EMC Data Domain Operating System 5.7 Administration Guide CONTENTS Preface 13 Chapter 1 EMC Data Domain System Features and Integration 17 Revision history.............................................................................................18 EMC Data Domain system overview............................................................... 19 EMC Data Domain system features............................................................... -

Rsview SE V4.0 CPR7+ Distributed System Design Considerations (Rev
RSView SE V4.0 CPR7+ Distributed System Design Considerations (Rev. 4, Sep. 2007) This page left intentionally blank. RSView SE V4.0 (CPR7+) Distributed System Design Considerations Rev. 4, September, 2007, page 2 of 46 Table of Contents Introduction............................................................................................................................................................7 Prerequisite reading before application development........................................................................................7 Revision History ....................................................................................................................................................7 RSView SE Component Terminology...................................................................................................................8 FactoryTalk Directory™....................................................................................................................................8 RSView Studio ..................................................................................................................................................8 RSView SE Server.............................................................................................................................................8 Data Server.........................................................................................................................................................8 RSView SE Client..............................................................................................................................................8 -

Windows Domain and Workgroup Planning Guide
EXPERION PKS RELEASE 516 Windows Domain and Workgroup Planning Guide EPDOC-X250-en-516A August 2020 Disclaimer This document contains Honeywell proprietary information. Information contained herein is to be used solely for the purpose submitted, and no part of this document or its contents shall be reproduced, published, or disclosed to a third party without the express permission of Honeywell International Sàrl. While this information is presented in good faith and believed to be accurate, Honeywell disclaims the implied warranties of merchantability and fitness for a purpose and makes no express warranties except as may be stated in its written agreement with and for its customer. In no event is Honeywell liable to anyone for any direct, special, or consequential damages. The information and specifications in this document are subject to change without notice. Copyright 2020 - Honeywell International Sàrl - 2 - Contents 3 Chapter 1 - About this document 7 1.1 Revision History 7 1.2 Intended audience 7 1.3 Prerequisite skills 7 1.4 Related documents 7 Chapter 2 - Planning a Windows domain/workgroup 9 2.1 Overview of Windows domain 9 2.2 Overview of a Windows workgroup 10 2.3 Overview of a domain controller 10 2.4 Overview of a Read-only Domain Controller 11 2.5 Overview of a peer domain controller 11 2.5.1 Multiple domain controllers in a domain 12 2.6 Overview of Active Directory and its components 13 2.6.1 Overview of Forests 13 2.6.2 Overview of domain trees 14 2.6.3 Overview of Organizational Units 15 2.6.4 Using a single domain with -

Advantech AE Technical Share Document
Advantech AE Technical Share Document Date 2018/07/23 SR# 1-3508328831 Category □FAQ ■SOP Related OS N/A Abstract How to setup Windows OS as SNTP server of WISE-4000 series? Keyword WISE, SNTP, private network, Windows. Related WISE-4010LAN, WISE-4050LAN, WISE-4060LAN, WISE-4012, Product WISE-4012E, WISE-4050, WISE-4051, WISE-4060, WISE-4220-S231 Problem Description: If WISE is not going to use public Network, is it possible to use Windows as SNTP server? This document is showing how to set up Windows as SNTP server of WISE module. Brief Solution - Step by Step: Step 1. Time server setting . Run Windows command. “regedit” 1 Step 2. To use local CMOS time clock . Locate registry entry: – HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\Config\Announce Flags – Change the value from 10 to 5 . (it means to use local CMOS time clock, KB314054) Checking NTP client setup is correct “w32tm /query /source” Step 3. Enable NTP server . Locate registry entry: – HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\W32Time\TimeProviders\Nt pServer – Enabled = 1. 2 Step 4. Run the Windows Time service . Run Windows command as administrator. “net stop w32time” . “net start w32time” Step 5. Run the NTP server . Checking on NTP server – use command “w32tm /query /configuration” to view if not show “NtpClient <Local>” . Checking on NTP client – use command “w32tm /resync” and “w32tm /query /source” to show if successful 3 Step 6. Setup SNTP function on WISE . Primary SNTP server: the IP of the NTP server, which is the Windows NTP server setup in step 1-5. SNTP time polling interval (sec.): counted from the time WISE plugged line power. -

Virtualizing Microsoft Skype for Business Server on Vmware Vsphere®
Virtualizing Microsoft Skype for Business Server on VMware vSphere® Skype for Business 2015 / vSphere 6.0 BEST PRACTICES GUIDE Virtualizing Microsoft Skype for Business Server on VMware vSphere Table of Contents 1. Introduction ........................................................................................................................................... 4 1.1 Purpose ........................................................................................................................................ 4 1.2 Target Audience .......................................................................................................................... 4 1.3 Scope ........................................................................................................................................... 5 1.4 External References .................................................................................................................... 5 2. ESXi Host Best Practices for Skype for Business Server 2015 ........................................................... 6 2.1 CPU Configuration Guidelines ..................................................................................................... 6 2.1.1 Physical and Virtual CPUs ...................................................................................................... 6 2.1.2 Skype for Business Server 2015 Capacity Sizing Guidelines ................................................. 6 2.1.3 VMware vSphere Virtual Symmetric Multiprocessing ............................................................ -

A-Z List of Windows CMD Commands — Also Included CMD Commands Commands PDF PDF
A-Z List Of Windows CMD Commands — Also Included CMD Com... https://techlog360.com/all-windows-cmd-commands/?preview_id=43... A-Z List Of Windows CMD Commands — Also Included CMD Commands Commands PDF PDF Sabarinath CMD Commands Function A addusers Used to add and list users in a CSV file admodcmd Used for bulk modifying contents in an active directory Address Resolution Protocol is used to map IP address to arp the hardware address assoc Used to change associations for file extensions associat One step file association at Run a command at a specific time atmadm Display connection info of the ATM adapter attrib Used to change file attributes B bcdboot Used to create and repair a system partition bcdedit Used to manage boot configuration data Used to manage the Background Intelligent Transfer bitsadmin Service bootcfg Used to edit boot configuration in Windows break Enable/Disable break capability (CTRL+C) in CMD C cacls Used to change permissions of files call Used one batch program to call another certreq Used to request a certificate from a certification authority certutil Manage Certification Authority files and services cd Used to change folder (directory) or go to a specific one change Used to change terminal services chcp Displays the number of active console code page chdir Same as cd command chkdsk Used to check and repair issues in the disk chkntfs Used to check the NTFS file system choice Accept user input (via keyboard) to a batch file cipher Used to encrypt/decrypt files and folder cleanmgr Used clean temp files and recycle -

Windows Server 2016 Time Sync Accuracy Addendum
Addendum to the White paper on Windows Time Sync Accuracy Contents Summary ....................................................................................................................................................... 2 Measuring Time Sync Accuracy..................................................................................................................... 3 Measurement Tools .................................................................................................................................. 3 Popcorn Filter ............................................................................................................................................ 5 Notes Server vs Client Terminology and Version information.................................................................. 6 Server 2016 Forest Test Topology ............................................................................................................ 6 Server2012R2 Forest Test Topology ......................................................................................................... 7 Methodology for AD Time Sync Accuracy Measurements ....................................................................... 8 Methodology for Simple NTP accuracy measurements ........................................................................... 9 Comparison between Server 2012R2 and Server 2016 ................................................................................ 9 Forest with a VMIC Root Time Source ...................................................................................................