Windows 10 Command Line Cheat Sheet
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Bulk Data Migration Using Robocopy
Bulk Data Migration Using Robocopy Created by: Nasuni Support Last update: 6/14/2011 Contents Overview...................................................................................................................................................................... 2 Using Robocopy to copy data to the Nasuni Filer....................................................................................... 2 2011 © Nasuni Corporation. All Rights Reserved Resizing the Cache and Snapshots Disks in Nasuni Filer v2.7 Robocopy and the Nasuni Filer cache ............................................................................................................. 2 Conclusion ................................................................................................................................................................... 3 Overview The information in this document applies to Nasuni Filer 2.x versions. It explains how to use Robocopy, a Microsoft Windows tool, to migrate data from a Windows file server to the Nasuni Filer. Robocopy has been bundled with Windows operating systems since Vista and Server 2008. Using Robocopy to copy data to the Nasuni Filer Robocopy is a Windows command line tool. To migrate data to the Nasuni Filer using Robocopy follow the steps below. 1. Identify the data set you want to migrate to the Nasuni Filer 2. Create/locate a share on the Nasuni Filer to write your data set to 3. Run cmd.exe 4. Run the command below from the source server’s command line. robocopy (path to source data) (path to Filer share) -
List of CMD COMMANDS a PDF by MYEDUKIT
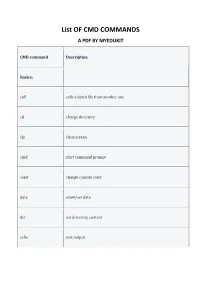
List OF CMD COMMANDS A PDF BY MYEDUKIT CMD command Description Basics: call calls a batch file from another one cd change directory cls clear screen cmd start command prompt color change console color date show/set date dir list directory content echo text output exit exits the command prompt or a batch file find find files hostname display host name pause pauses the execution of a batch file and shows a message runas start a program as another user shutdown shutdown the computer sort sort the screen output start start an own window to execute a program or command taskkill terminate a process or an application tasklist display applications and related tasks time display/edit the system time timeout wait any time title set title for prompt ver display operating system version w32tm setting time synchronisation/time server/time zone Network: ftp transfer files to an FTP server ftype display file type and mapping getmac display MAC address ipconfig display IP network settings netsh configure/control/display network components netstat display TCP/IP connections and status nslookup query the DNS pathping test the connection to a specific IP address ping pings the network route display network routing table, add static routes systeminfo displays computer-specific properties and configurations telnet establish a Telnet connection tftp transfer files to a TFTP server tracert trace routes similar to patchping Files: attrib display file attributes comp compare file contents compact display/change file compression copy / xcopy copy files diskcomp -

Prepare Customer Site Servers
Prepare Customer Site Servers • Prepare Customer Site Servers, on page 1 • Prepare Cisco UCS C-Series Customer Site Servers, on page 1 • Prepare HyperFlex M5 series Customer Site Servers, on page 3 • NTP and Time Synchronization, on page 4 • Global Catalog Requirements, on page 5 Prepare Customer Site Servers Perform all the procedures in this section on the Side A and the Side B servers. Prepare Cisco UCS C-Series Customer Site Servers Configure RAID for C240 M4SX The disk array configuration for the C240 M4SX is already set up to match what is required for Packaged CCE. Verify the settings as follows. Using Cisco Integrated Management Controller, check that the following settings are configured correctly: • Virtual Drive Info: RAID 5 with 5 (Physical Disks) * 4 (Virtual Drives/Datastores) • Stripe Size: 128KB • Write Policy: Write Back with BBU • Read Policy: Read Ahead Always For more information regarding RAID configuration for C240 M4SX in Configure RAID with GUI (UCS C-Series M4 Servers) section, see Cisco Collaboration on Virtual Servers Guide at: https://www.cisco.com/ c/en/us/td/docs/voice_ip_comm/cucm/virtual/CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers/ CHCS_BK_C7C7ED05_00_cisco-collaboration-on-virtual-servers_chapter_01.html#CUCM_TK_C2DC4F2D_ 00. Prepare Customer Site Servers 1 Prepare Customer Site Servers Run the RAID Config Validator Utility Run the RAID Config Validator Utility After you set up RAID configuration and add the datastores, run the RAID Config Validator utility to ensure that your datastore configuration is correct. Before you begin To run the utility, Java 7 (any update) must be installed. Java 8 and later releases are not supported. -

Deployment Strategy
System Management Best Practices Bryan S Owen PE Copyright c 2004 OSIsoft Inc. All rights reserved. Richness & Reliability “Value Coefficients” • Quality – Across operations and data systems • Quantity – Across business needs and over time • Utilization – Across enterprise and just in time It all Starts with Great Software …and the Right Architecture • Visualization Tools • Availability • Reliability • Security Integrated Data Collection Proven: Cutting Edge: Integrated Interface Embedded Historian Embedded PI Historian • Continuous Historian for DeltaV Application Station http://www.easydeltav.com/pd/PDS_ApplicationStation.pdf • “56SAM” Historian for Allen-Bradley ControlLogix www.oldi.com • “Promoted” Interface Node • Also visit: www.echohistorian.com Fault Tolerant vs Redundant Incident Tolerant Redundant Environment Fault JJ JJJ Hardware Fault JJJ JJ Software Fault K J Administrative Error JK JJ Scheduled Down K JJJ “Smile” Points: 15/30 22/30 Redundant Architecture • Reliability – Build from the Data Up • Availability – Build from the Users Down You decide what comes first! Redundant Data Collection Dual Gateways Interface Node Failover Redundant Data Service Dual PI Servers Dual PI Clients Redundant Architecture No single point of failure sounds great, what’s the catch? • Interface Support • History Recovery • Gap Filling • Client Impact • Fugitive Data Fugitive Data Capture Essential for rich content but… 1% of the data causes 99% perspiration! • Manual Entry Systems • Custom Applications • Isolated Point to Point Links Solution: -

Preparation of Papers in Two-Column Format
Protecting Media Production Companies against Ransomware Rob Gonsalves Avid Technology, Inc. Burlington Massachusetts [email protected] Abstract - Ransomware, a type of malicious software designed to block access to digital assets until a sum of money is paid, represents a growing threat for media production companies, as digital media assets are a valued target for hackers. To protect their media assets and mitigate the risk of these types of attacks, companies can implement a set of security policies, procedures and systems. Deploying and operating Disaster Recovery (DR) systems with specific safeguards against ransomware will help companies retrieve valuable files without having to pay FIGURE 1 - INITIAL RANSOMWARE ATTACK cyber-criminals. This paper will discuss the growing threat of ransomware to media companies and cover the key The initial attack often comes when a user inadvertently concepts for understanding and building security and DR downloads and installs malware from a website. After systems with specific safeguards against ransomware. installation, the ransomware quietly searches for and Using these techniques, critical business functions can encrypts files. Its goal is to stay below the radar until it can continue in the event of an attack. find and encrypt all of the files that could be of value to the user. By the time the company is presented with the RANSOMWARE malware’s message with the ransom demand, the damage has already been done [2]. Ransomware is a form of malware that encrypts data files and holds these files for ransom. After the initial infection, the malware begins encrypting files on local drives, shared storage, and potentially other computers on the network. -

Microsoft Windows Server 2019 Version 1809 Hyper-V
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

Operational and Administrative Guidance
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

When Powerful SAS Meets Powershell
PharmaSUG 2018 - Paper QT-06 ® TM When Powerful SAS Meets PowerShell Shunbing Zhao, Merck & Co., Inc., Rahway, NJ, USA Jeff Xia, Merck & Co., Inc., Rahway, NJ, USA Chao Su, Merck & Co., Inc., Rahway, NJ, USA ABSTRACT PowerShell is an MS Windows-based command shell for direct interaction with an operating system and its task automation. When combining the powerful SAS programming language and PowerShell commands/scripts, we can greatly improve our efficiency and accuracy by removing many trivial manual steps in our daily routine work as SAS programmers. This paper presents five applications we developed for process automation. 1) Automatically convert RTF files in a folder into PDF files, all files or a selection of them. Installation of Adobe Acrobat printer is not a requirement. 2) Search the specific text of interest in all files in a folder, the file format could be RTF or SAS Source code. It is very handy in situations like meeting urgent FDA requests when there is a need to search required information quickly. 3) Systematically back up all existing files including the ones in subfolders. 4) Update the attributes of a selection of files with ease, i.e., change all SAS code and their corresponding output including RTF tables and SAS log in a production environment to read only after database lock. 5) Remove hidden temporary files in a folder. It can clean up and limit confusion while delivering the whole output folder. Lastly, the SAS macros presented in this paper could be used as a starting point to develop many similar applications for process automation in analysis and reporting activities. -

How to Perform File System Backup and Restore with Netwrix File Server Change Reporter Technical Article
HOW TO PERFORM FILE SYSTEM BACKUP AND RESTORE WITH NETWRIX FILE SERVER CHANGE REPORTER TECHNICAL ARTICLE Product Version: 3.3 April/2012 Copyright © 2012 NetWrix Corporation. All Rights Reserved. NetWrix File Server Change Reporter Technical Article Legal Notice The information in this publication is furnished for information use only, and does not constitute a commitment from NetWrix Corporation of any features or functions discussed. NetWrix Corporation assumes no responsibility or liability for the accuracy of the information presented, which is subject to change without notice. NetWrix is a registered trademark of NetWrix Corporation. The NetWrix logo and all other NetWrix product or service names and slogans are registered trademarks or trademarks of NetWrix Corporation. Active Directory is a trademark of Microsoft Corporation. All other trademarks and registered trademarks are property of their respective owners. Disclaimers This document may contain information regarding the use and installation of non-NetWrix products. Please note that this information is provided as a courtesy to assist you. While NetWrix tries to ensure that this information accurately reflects the information provided by the supplier, please refer to the materials provided with any non-NetWrix product and contact the supplier for confirmation. NetWrix Corporation assumes no responsibility or liability for incorrect or incomplete information provided about non-NetWrix products. © 2012 NetWrix Corporation. All rights reserved. www.netwrix.com Copyright © 2012 NetWrix Corporation. All Rights Reserved Page 2 of 11 Suggestions or comments about this document? www.netwrix.com/feedback NetWrix File Server Change Reporter Technical Article Table of Contents 1. INTRODUCTION ................................................................................ 4 1.1. Overview .............................................................................. 4 1.2. -

Windows Tool Reference
AppendixChapter A1 Windows Tool Reference Windows Management Tools This appendix lists sets of Windows management, maintenance, configuration, and monitor- ing tools that you may not be familiar with. Some are not automatically installed by Windows Setup but instead are hidden away in obscure folders on your Windows Setup DVD or CD- ROM. Others must be downloaded or purchased from Microsoft. They can be a great help in using, updating, and managing Windows. We’ll discuss the following tool kits: ■ Standard Tools—Our pick of handy programs installed by Windows Setup that we think are unappreciated and not well-enough known. ■ Support Tools—A set of useful command-line and GUI programs that can be installed from your Windows Setup DVD or CD-ROM. ■ Value-Added Tools—Several more sets of utilities hidden away on the Windows Setup CD-ROM. ■ Windows Ultimate Extras and PowerToys for XP—Accessories that can be downloaded for free from microsoft.com. The PowerToys include TweakUI, a program that lets you make adjustments to more Windows settings than you knew existed. ■ Resource Kits—A set of books published by Microsoft for some versions of Windows that includes a CD-ROM containing hundreds of utility programs. What you may not have known is that in some cases you can download the Resource Kit program toolkits with- out purchasing the books. ■ Subsystem for UNIX-Based Applications (SUA)—A package of network services and command-line tools that provide a nearly complete UNIX environment. It can be installed only on Windows Vista Ultimate and Enterprise, and Windows Server 2003. -

EMC® Data Domain® Operating System 5.7 Administration Guide
EMC® Data Domain® Operating System Version 5.7 Administration Guide 302-002-091 REV. 02 Copyright © 2010-2016 EMC Corporation. All rights reserved. Published in the USA. Published March, 2016 EMC believes the information in this publication is accurate as of its publication date. The information is subject to change without notice. The information in this publication is provided as is. EMC Corporation makes no representations or warranties of any kind with respect to the information in this publication, and specifically disclaims implied warranties of merchantability or fitness for a particular purpose. Use, copying, and distribution of any EMC software described in this publication requires an applicable software license. EMC², EMC, and the EMC logo are registered trademarks or trademarks of EMC Corporation in the United States and other countries. All other trademarks used herein are the property of their respective owners. For the most up-to-date regulatory document for your product line, go to EMC Online Support (https://support.emc.com). EMC Corporation Hopkinton, Massachusetts 01748-9103 1-508-435-1000 In North America 1-866-464-7381 www.EMC.com 2 EMC Data Domain Operating System 5.7 Administration Guide CONTENTS Preface 13 Chapter 1 EMC Data Domain System Features and Integration 17 Revision history.............................................................................................18 EMC Data Domain system overview............................................................... 19 EMC Data Domain system features............................................................... -

Rsview SE V4.0 CPR7+ Distributed System Design Considerations (Rev
RSView SE V4.0 CPR7+ Distributed System Design Considerations (Rev. 4, Sep. 2007) This page left intentionally blank. RSView SE V4.0 (CPR7+) Distributed System Design Considerations Rev. 4, September, 2007, page 2 of 46 Table of Contents Introduction............................................................................................................................................................7 Prerequisite reading before application development........................................................................................7 Revision History ....................................................................................................................................................7 RSView SE Component Terminology...................................................................................................................8 FactoryTalk Directory™....................................................................................................................................8 RSView Studio ..................................................................................................................................................8 RSView SE Server.............................................................................................................................................8 Data Server.........................................................................................................................................................8 RSView SE Client..............................................................................................................................................8