Voip Skype (Ebay)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Akamai Accelerated Network Program FAQ Akamai Accelerated Network Program Frequently Asked Questions
Akamai Accelerated Network Program FAQ Akamai Accelerated Network Program Frequently Asked Questions Thank you for your interest in the Akamai Accelerated Network What security is there on your boxes? Program. To ensure that you have all your preliminary questions Akamai zealously guards the integrity of our servers. Of course, answered, please review this document. Your Akamai representative we cannot list the steps taken to secure the boxes, but we do have is also available to add more detail or answer additional over 6,000 servers installed in ISPs all over the world, and not one questions that may not be covered. It’s not too late to Accelerate has ever been remotely compromised. Standard security measures Your Network. are taken, such as disabling telnet access, using SSH, turning off daemons not used in production, etc. Server Installation Do you servers work behind a firewall? What do my engineers have to do during the installation? The servers are serving content just as the origin servers – Yahoo!, We ask our partners to simply install the hardware (rack mounted CNN, ESPN, Apple, etc. – would be. The origin servers are not computers and ethernet switches), connect them with the cables behind your firewall, and our servers work best if they are not provided, and finally to assign each computer an IP address and behind your firewall. default gateway. After installation what maintenance and support is Network required? Can we put servers from other content distributors in our The partner is not required to perform any regular maintenance network as well? on Akamai’s equipment. -

The Ambulance the Squad Car & the Internet.Pdf
The Ambulance, the Squad Car, & the Internet The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Susan P. Crawford, The Ambulance, the Squad Car, & the Internet, 21 Berkeley Tech. L.J. 873 (2006). Published Version http://scholarship.law.berkeley.edu/btlj/vol21/iss2/5/ Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:12956284 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA Berkeley Technology Law Journal Volume 21 | Issue 2 Article 5 March 2006 The Ambulance, the Squad Car, & the Internet Susan P. Crawford Follow this and additional works at: http://scholarship.law.berkeley.edu/btlj Recommended Citation Susan P. Crawford, The Ambulance, the Squad Car, & the Internet, 21 Berkeley Tech. L.J. 873 (2006). Available at: http://scholarship.law.berkeley.edu/btlj/vol21/iss2/5 This Article is brought to you for free and open access by the Law Journals and Related Materials at Berkeley Law Scholarship Repository. It has been accepted for inclusion in Berkeley Technology Law Journal by an authorized administrator of Berkeley Law Scholarship Repository. For more information, please contact [email protected]. THE AMBULANCE, THE SQUAD CAR, & THE INTERNET By Susan P. Crawfordt TABLE OF CONTENTS I. IN T R OD U C T IO N ............................................................................................ 874 II. THE MARKET CONTEXT ........................................................................... 877 III. FCC INTERNET SOCIAL POLICIES ...................................................... -

The Internet As Emerging Critical Infrastructure: What Needs to Be Measured?
the Internet as emerging critical infrastructure: what needs to be measured? cooperative association for internet data analysis 30 november 2005 presented to lsn jet @ nsf (http://www.nitrd.gov/subcommittee/lsn/jet/) [email protected] outline of talk what is critical infrastructure top problems of Internet historical context (incongruity) what have we learned and how can we apply it? [ case study: scalability (separate talk) ] what we (all) can do to help critical infrastructure what is it? how does it get that way? what are common characteristics? is the Internet one? or will it be soon? what are the implications for public and private sectors? underlying goals: innovation, economic strength, democracy, freedom, health, science, arts, society. it really is about living in a better world... top Internet problems 16 operational internet problems • security • authentication • spam • scalable configuration management • robust scalability of routing system • compromise of e2e principle • dumb network • measurement • patch management • “normal accidents” • growth trends in traffic and user expectations • time management and prioritization of tasks • stewardship vs governance • intellectual property and digital rights • interdomain qos/emergency services • inter-provider vendor/business coordination persistently unsolved problems for 10+ years (see presentations at www.caida.org ) top Internet problems why we’re not making progress • top unsolved problems in internet operations and engineering are rooted in economics, ownership, and trust (EOT). • -

Telecom in the Time of Crash
INCIDENTAL PAPER Telecom in the Time of Crash Kas Kalba November 2002 Program on Information Resources Policy Center for Information Policy Research Harvard University The Program on Information Resources Policy is jointly sponsored by Harvard University and the Center for Information Policy Research. Chairman Managing Director Anthony G. Oettinger John C. B. LeGates Kas Kalba is President of Kalba International, Inc., a management consulting and research firm. He is writing a book on the telecom crash, from which this paper is derived, and has been a longstanding participant in PIRP activities. Copyright © 2002 by Kas Kalba. Not to be reproduced in any form without written consent from Kas Kalba, Kalba International. Inc., 23 Sandy Pond Road, Lincoln, 01773, USA. +1 (781) 259-9589. E-mail: [email protected] URL: http://www.kalbainternational.com ISBN 1-879716-85-2 I-02-2 November 2002 PROGRAM ON INFORMATION RESOURCES POLICY Harvard University Center for Information Policy Research Affiliates AT&T Corp. Nippon Telegraph & Telephone Corp Australian Telecommunications Users (Japan) Group PDS Consulting BellSouth Corp. PetaData Holdings, Inc. The Boeing Company Samara Associates Booz Allen Hamilton Skadden, Arps, Slate, Meagher & Flom Center for Excellence in Education LLP Commission of the European Sonexis Communities Strategy Assistance Services Critical Path TOR LLC CyraCom International United States Government: Ellacoya Networks, Inc. Department of Commerce Hanaro Telecom Corp. (Korea) National Telecommunications and Hearst Newspapers Information Administration Hitachi Research Institute (Japan) Department of Defense IBM Corp. National Defense University Korea Telecom Department of Health and Human Lee Enterprises, Inc. Services Lexis–Nexis National Library of Medicine John and Mary R. -

Flooding Attacks by Exploiting Persistent Forwarding Loops
Flooding Attacks by Exploiting Persistent Forwarding Loops Jianhong Xia, Lixin Gao and Teng Fei University of Massachusetts, Amherst MA 01003, USA Email: {jxia, lgao, tfei}@ecs.umass.edu Introduction • Routing determines forwarding paths X A Y C B Why Persistent Forwarding Loop Occurs --- Example on Neglecting Pull-up Route • Announces 18.0.0.0/16 to the Internet • Router A has default route pointing to B Internet • Router A uses 18.0.0.0/24 only BB 18.0.0.0/16 ute ult ro AA defa • Any traffic to 18.0.0.0/24 18.0.1.0~18.0.255.255 will enter a forwarding ` loop between A and B ` ` Risk of Persistent Forwarding Loops • Flooding Attacks to legitimate hosts X Traffic to X Imperiled Ra Rb Rc Addresses Traffic to Y Y Shadowed Addresses • How many shadowed addresses in the Internet? • How many imperiled addresses in the Internet? Measurement Design •Design – Balancing granularity and overhead – Samples 2 addresses in each /24 IP block • Addresses space collection – Addresses covered by RouteView table – De-aggregate prefixes to /24 prefixes • Fine-grained prefixes • Data traces – Traceroute to 5.5 million fine-grained prefixes – Measurement lasts for 3 weeks in Sep. 2005 Shadowed vs. Imperiled Addresses • Shadowed addresses/prefixes – 135,973 shadowed prefixes – 2.47% of routable addresses – Located in 5341 ASes • Imperiled addresses/prefixes – 42,887 imperiled prefixes – 0.78% of routable addresses – Located in 2117 ASes Validating Persistent Forwarding Loops • Validation from various locations – From Asia, Europe, West and East coast of US -
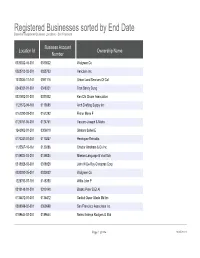
Registered Businesses Sorted by End Date Based on Registered Business Locations - San Francisco
Registered Businesses sorted by End Date Based on Registered Business Locations - San Francisco Business Account Location Id Ownership Name Number 0030032-46-001 0030032 Walgreen Co 0028703-02-001 0028703 Vericlaim Inc 1012834-11-141 0091116 Urban Land Services Of Cal 0348331-01-001 0348331 Tran Sandy Dung 0331802-01-001 0331802 Ken Chi Chuan Association 1121572-09-161 0113585 Arch Drafting Supply Inc 0161292-03-001 0161292 Fisher Marie F 0124761-06-001 0124761 Vaccaro Joseph & Maria 1243902-01-201 0306019 Shatara Suheil E 0170247-01-001 0170247 Henriquez Reinaldo 1125567-10-161 0130286 Chador Abraham & Co Inc 0189884-03-001 0189884 Mission Language & Vocl Sch 0318928-03-001 0318928 John W De Roy Chiroprac Corp 0030032-35-001 0030032 Walgreen Co 1228793-07-191 0148350 Willis John P 0310148-01-001 0310148 Blasko Peter B Et Al 0135472-01-001 0135472 Saddul Oscar Allado Md Inc 0369698-02-001 0369698 San Francisco Associates Inc 0189644-02-001 0189644 Neirro Erainya Rodgers G Etal Page 1 of 984 10/05/2021 Registered Businesses sorted by End Date Based on Registered Business Locations - San Francisco DBA Name Street Address City State Source Zipcode Walgreens #15567 845 Market St San Francisco CA 94103 Vericlaim Inc 500 Sansome St Ste 614 San Francisco CA 94111 Urban Land Services Of Cal 1170 Sacramento St 5d San Francisco CA 94108 Elizabeth Hair Studio 672 Geary St San Francisco CA 94102 Ken Chi Chuan Association 3626 Taraval St Apt 3 San Francisco CA 94116 Arch Drafting Supply Inc 10 Carolina St San Francisco CA 94103 Marie Fisher Interior -

Legislators of Cyberspace: an Analysis of the Role Of
SHAPING CODE Jay P. Kesan* & Rajiv C. Shah** I. INTRODUCTION ............................................................................................................................ 4 II. THE CASE STUDIES: THE DEVELOPMENT OF CODE WITHIN INSTITUTIONS.............................. 13 A. World Wide Web......................................................................................................... 14 1. Libwww............................................................................................................ 14 2. NCSA Mosaic .................................................................................................. 16 B. Cookies ........................................................................................................................ 21 1. Netscape’s Cookies .......................................................................................... 21 2. The IETF’s Standard for Cookies .................................................................... 24 C. Platform for Internet Content Selection....................................................................... 28 D. Apache......................................................................................................................... 34 III. LEGISLATIVE BODIES: SOCIETAL INSTITUTIONS THAT DEVELOP CODE ................................. 37 A. Universities.................................................................................................................. 38 B. Firms........................................................................................................................... -

Akamai 2019 State of the Internet / Security Phishing
Akamai Security Research: Cybercriminals Using Enterprise-Based Strategies For Phishing Kit Development And Deployment Oct 30, 2019 09:49 CET Akamai 2019 State of the Internet / Security Phishing Akamai Security Research: Cybercriminals Using Enterprise- Based Strategies For Phishing Kit Development And Deployment Malicious Actors Developing Custom Tools and Processes to Target and Leverage the World’s Largest Tech Brands and Victimize Their Users Cambridge, MA -- October 30, 2019 -- Akamai Technologies, Inc. (NASDAQ: AKAM) today published the Akamai 2019 State of the Internet / Security Phishing: Baiting the Hook report. The research findings indicate that cybercriminals are using enterprise-based development and deployment strategies, such as phishing as a service (PaaS), to leverage some of the world’s largest tech brands, with 42.63% of domains observed targeting Microsoft, PayPal, DHL, and Dropbox. The report details that phishing is no longer just an email-based threat, but has expanded to include social media and mobile devices, creating a wide- reaching problem that touches all industries. This evolving method continues to morph into different techniques, one of which being business email compromise (BEC) attacks. According to the FBI, BEC attacks resulted in worldwide losses of more than $12 billionbetween October 2013 and May 2018. “Phishing is a long-term problem that we expect will have adversaries continuously going after consumers and businesses alike until personalized awareness training programs and layered defense techniques are put in place,” said Martin McKeay, Editorial Director of the State of the Internet/Security report for Akamai. The report shows that cybercriminals are targeting top global brands and their users across various industries through highly-organized and sophisticated phishing kit operations. -

Esports – Who Are the Big Players and the Likely
Esports – Who are the big players and the likely winners Millennial driven esports continues to grow rapidly. The number of esports enthusiasts worldwide was estimated to be ~165 million in 2018, and for total global viewers, the forecast is ~453 million in 2019. Esports global revenue is forecast to pass US$1b in 2019 and by 2022 the global eSports market revenue is forecast to reach US$1.79 billion growing at a CAGR of 22.3%. The big players in esports Activision Blizzard Inc. (NASDAQ: ATVI) Activision Blizzard owns the popular Overwatch League as well as World of Warcraft, StarCraft, Diablo, and Hearthstone. In 2018 Activision Blizzard signed a multiyear deal with Walt Disney to broadcast the Overwatch League. As of March 2018, it was the largest game company in the Americas and Europe in terms of revenue and market capitalization. Activision Blizzard has several business units: Activision Publishing, Blizzard Entertainment, King, Major League Gaming,and Activision Blizzard Studios. Alphabet Inc. (NASDAQ: GOOGL) Alphabet (Google) has a new cloud gaming platform called Stadia. It operates games hosted on remote servers and then streams video content to connected devices, including smartphones, tablets, computers and TVs. Other competitors in the streaming space include Amazon (Twitch), Facebook, Twitter, Microsoft, Tencent, and Alibaba. Amazon (NASDAQ: AMZN) Amazon’s Twitch leads the online USA streaming market. Amazon acquired Twitch for nearly $1 billion in 2014. Twitch is only a very small percentage of Amazon’s massive revenue. Electronic Arts Inc. (NASDAQ: EA) Electronic Arts is an American video game company headquartered in California. It is the second-largest gaming company in the Americas and Europe by revenue and market capitalization. -

2015 Valuation Handbook – Guide to Cost of Capital and Data Published Therein in Connection with Their Internal Business Operations
Market Results Through #DBDLADQ 2014 201 Valuation Handbook Guide to Cost of Capital Industry Risk Premia Company List Cover image: Duff & Phelps Cover design: Tim Harms Copyright © 2015 by John Wiley & Sons, Inc. All rights reserved. Published by John Wiley & Sons, Inc., Hoboken, New Jersey. Published simultaneously in Canada. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning, or otherwise, except as permitted under Section 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, Inc., 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600, or on the Web at www.copyright.com. Requests to the Publisher for permission should be addressed to the Permissions Department, John Wiley & Sons, Inc., 111 River Street, Hoboken, NJ 07030, (201) 748-6011, fax (201) 748- 6008, or online at http://www.wiley.com/go/permissions. The forgoing does not preclude End-users from using the 2015 Valuation Handbook – Guide to Cost of Capital and data published therein in connection with their internal business operations. Limit of Liability/Disclaimer of Warranty: While the publisher and author have used their best efforts in preparing this book, they make no representations or warranties with respect to the accuracy or completeness of the contents of this book and specifically disclaim any implied warranties of merchantability or fitness for a particular purpose. -

Brief for Plaintiff-Appellant Akamai Technologies, Inc
I]1111IIIIIIIIIIIIIJllJIfllIIIJJIIIttIHJillIJllllIJlllIlJJJFIIflMMIIJillIlJJIIIJ USFC2009-1372-10 {466256B 1-3FB1-4D3A-A6D4-9850D2 B04CA5 } {117249}{54-110705:110649}{062011} APPELLANT'S BRIEF 2009-1372,-1380,-1416,-1417 IN THE UNITED STATES COURT OF APPEALS FOR THE FEDERAL CIRCUIT AKAMAI TECHNOLOGIES, INC., Plaintiff-Appellant, and THE MASSACHUSETTS INSTITUTE OF TECHNOLOGY, Plaintiff-Appellant, V° LIMELIGHT NETWORKS, INC., Defendant-Cross Appellant. App_l's_from"_" __ the United States District Court for the District of Massachusetts in case nos. 06-CV-11109 and 06-CV-11585, Judge Rya W. Zobel. PRINCIPAL BRIEF FOR PLAINTIFF-APPELLANT AKAMAI TECHNOLOGIES, INC. ON REHEARING EN BANC Of Counsel: DONALD R. DUNNER KARA F. STOLL ROBERT S, FRANK, JR, FINNEGAN, HENDERSON, FARABOW, CHOATE, HALL&STEWARTLLP GARRETT & DUNNER, LLP Two lntem_ionalPlace 901 New York Avenue, NW Boston, MA02110 Washington, DC 20001-4413 (202) 408-4000 Attorney for Plaintiff-Appellant The Massachusetts Institute of Technology JENNIFER S. SWAN F1NNEGAN, HENDERSON, FARABOW, GARRETr & DUNNER, LLP 3300 Hillview Avenue Palo Alto, CA 94304-1203 (650) 849-6676 Attorneys for Plaintiff-Appellant June 20, 2011 Akamai Technologies, Inc. CERTIFICATE OF INTEREST Counsel for Akamai Technologies, Inc. certifies the following: 1. The full name of every party or amicus represented by Counsel is: Akamai Technologies, Inc. 2. The name of the real party in interest represented by me is: None ° All parent corporations and any publicly held companies that own 10 percent or more of the stock of the party represented by me are: None o The names of all law finns and the partners or associates that appeared for the party or amicus now represented by me in the trial court or agency or are expected to appear in this Court are: Donald R. -

The Great Telecom Meltdown for a Listing of Recent Titles in the Artech House Telecommunications Library, Turn to the Back of This Book
The Great Telecom Meltdown For a listing of recent titles in the Artech House Telecommunications Library, turn to the back of this book. The Great Telecom Meltdown Fred R. Goldstein a r techhouse. com Library of Congress Cataloging-in-Publication Data A catalog record for this book is available from the U.S. Library of Congress. British Library Cataloguing in Publication Data Goldstein, Fred R. The great telecom meltdown.—(Artech House telecommunications Library) 1. Telecommunication—History 2. Telecommunciation—Technological innovations— History 3. Telecommunication—Finance—History I. Title 384’.09 ISBN 1-58053-939-4 Cover design by Leslie Genser © 2005 ARTECH HOUSE, INC. 685 Canton Street Norwood, MA 02062 All rights reserved. Printed and bound in the United States of America. No part of this book may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage and retrieval system, without permission in writing from the publisher. All terms mentioned in this book that are known to be trademarks or service marks have been appropriately capitalized. Artech House cannot attest to the accuracy of this information. Use of a term in this book should not be regarded as affecting the validity of any trademark or service mark. International Standard Book Number: 1-58053-939-4 10987654321 Contents ix Hybrid Fiber-Coax (HFC) Gave Cable Providers an Advantage on “Triple Play” 122 RBOCs Took the Threat Seriously 123 Hybrid Fiber-Coax Is Developed 123 Cable Modems