A Data Compression Algorithm Based on Adaptive Huffman Code for Wireless Sensor Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Program Book(EN)
TRANSPORTATION IN CHINA 2025: CONNECTING THE WORLD 中国交通 2025:联通世界 Transportation in China 2025: Connecting the World 1 CONTENTS The 19th COTA International Conference of Transportation Professionals Transportation in China 2025: Connecting the World Welcome Remarks ······································ 4 Organization Council ································· 8 Organizers ······················································ 13 Sponsors ·························································· 17 Instructions for Presenters ························ 19 Instructions for Session Chairs ················ 19 Program at a Glance ··································· 20 Program ··························································· 22 Poster Sessions ············································· 56 General Information ··································· 86 Conference Speakers & Organizers ······· 95 Pre- and Post-CICTP2019 Events ············ 196 • Welcome Remarks It is our great pleasure to welcome you all to the 19th COTA International Conference Welcome of Transportation Professionals (CICTP 2019) in Nanjing, China. The CICTP2019 is jointly Remarks organized by Chinese Overseas Transportation Association (COTA), Southeast University, and Jiaotong International Cooperation Service Center of Ministry of Transport. The CICTP annual conference series was established by COTA back in 2001 and in the past two decades benefited from support from the American Society of Civil Engineers (ASCE), Transportation Research Board (TRB), and many other -
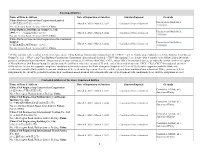
Sanctioned Entities Name of Firm & Address Date
Sanctioned Entities Name of Firm & Address Date of Imposition of Sanction Sanction Imposed Grounds China Railway Construction Corporation Limited Procurement Guidelines, (中国铁建股份有限公司)*38 March 4, 2020 - March 3, 2022 Conditional Non-debarment 1.16(a)(ii) No. 40, Fuxing Road, Beijing 100855, China China Railway 23rd Bureau Group Co., Ltd. Procurement Guidelines, (中铁二十三局集团有限公司)*38 March 4, 2020 - March 3, 2022 Conditional Non-debarment 1.16(a)(ii) No. 40, Fuxing Road, Beijing 100855, China China Railway Construction Corporation (International) Limited Procurement Guidelines, March 4, 2020 - March 3, 2022 Conditional Non-debarment (中国铁建国际集团有限公司)*38 1.16(a)(ii) No. 40, Fuxing Road, Beijing 100855, China *38 This sanction is the result of a Settlement Agreement. China Railway Construction Corporation Ltd. (“CRCC”) and its wholly-owned subsidiaries, China Railway 23rd Bureau Group Co., Ltd. (“CR23”) and China Railway Construction Corporation (International) Limited (“CRCC International”), are debarred for 9 months, to be followed by a 24- month period of conditional non-debarment. This period of sanction extends to all affiliates that CRCC, CR23, and/or CRCC International directly or indirectly control, with the exception of China Railway 20th Bureau Group Co. and its controlled affiliates, which are exempted. If, at the end of the period of sanction, CRCC, CR23, CRCC International, and their affiliates have (a) met the corporate compliance conditions to the satisfaction of the Bank’s Integrity Compliance Officer (ICO); (b) fully cooperated with the Bank; and (c) otherwise complied fully with the terms and conditions of the Settlement Agreement, then they will be released from conditional non-debarment. If they do not meet these obligations by the end of the period of sanction, their conditional non-debarment will automatically convert to debarment with conditional release until the obligations are met. -

002170196E1c16a28b910f.Pdf
6 THURSDAY, APRIL 23, 2015 DOCUMENT CHINA DAILY 7 JUSTICE INTERPOL LAUNCHES GLOBAL DRAGNET FOR 100 CHINESE FUGITIVES It’s called Operation Sky Net. Amid the nation’s intensifying antigraft campaign, arrest warrants were issued by Interpol China for former State employees and others suspected of a wide range of corrupt practices. China Daily was authorized by the Chinese justice authorities to publish the information below. Language spoken: Liu Xu Charges: Place of birth: Anhui property and goods Language spoken: Zeng Ziheng He Jian Qiu Gengmin Wang Qingwei Wang Linjuan Chinese, English Sex: Male Embezzlement Language spoken: of another party by Chinese Sex: Male Sex: Male Sex: Male Sex: Male Sex: Female Charges: Date of birth: Chinese, English fraud Charges: Date of birth: Date of birth: Date of birth: Date of birth: Date of birth: Accepting bribes 07/02/1984 Charges: Embezzlement Embezzlement 15/07/1971 14/11/1965 15/05/1962 03/01/1972 17/07/1980 Place of birth: Beijing Place of birth: Henan Language spoken: Place of birth: Place of birth: Place of birth: Language spoken: Language spoken: Chinese Zhejiang Jinan, Shandong Jilin Chinese, English Chinese Charges: Graft Language spoken: Language spoken: Language spoken: Charges: Corruption Charges: Chinese Chinese, English Chinese Embezzlement Charges: Contract Charges: Commits Charges: fraud, and flight of fraud by means of a Misappropriation of Yang Xiuzhu 25/11/1945 Place of birth: Chinese Zhang Liping capital contribution Chu Shilin letter of credit Dai Xuemin public funds Sex: Female -

Christian Women and the Making of a Modern Chinese Family: an Exploration of Nü Duo 女鐸, 1912–1951
Christian Women and the Making of a Modern Chinese Family: an Exploration of Nü duo 女鐸, 1912–1951 Zhou Yun A thesis submitted for the degree of Doctor of Philosophy of The Australian National University February 2019 © Copyright by Zhou Yun 2019 All Rights Reserved Except where otherwise acknowledged, this thesis is my own original work. Acknowledgements I would like to express my deep gratitude to my supervisor Dr. Benjamin Penny for his valuable suggestions and constant patience throughout my five years at The Australian National University (ANU). His invitation to study for a Doctorate at Australian Centre on China in the World (CIW) not only made this project possible but also kindled my academic pursuit of the history of Christianity. Coming from a research background of contemporary Christian movements among diaspora Chinese, I realise that an appreciation of the present cannot be fully achieved without a thorough study of the past. I was very grateful to be given the opportunity to research the Republican era and in particular the development of Christianity among Chinese women. I wish to thank my two co-advisers—Dr. Wei Shuge and Dr. Zhu Yujie—for their time and guidance. Shuge’s advice has been especially helpful in the development of my thesis. Her honest critiques and insightful suggestions demonstrated how to conduct conscientious scholarship. I would also like to extend my thanks to friends and colleagues who helped me with my research in various ways. Special thanks to Dr. Caroline Stevenson for her great proof reading skills and Dr. Paul Farrelly for his time in checking the revised parts of my thesis. -

Hong Kong SAR
China Data Supplement November 2006 J People’s Republic of China J Hong Kong SAR J Macau SAR J Taiwan ISSN 0943-7533 China aktuell Data Supplement – PRC, Hong Kong SAR, Macau SAR, Taiwan 1 Contents The Main National Leadership of the PRC 2 LIU Jen-Kai The Main Provincial Leadership of the PRC 30 LIU Jen-Kai Data on Changes in PRC Main Leadership 37 LIU Jen-Kai PRC Agreements with Foreign Countries 47 LIU Jen-Kai PRC Laws and Regulations 50 LIU Jen-Kai Hong Kong SAR 54 Political, Social and Economic Data LIU Jen-Kai Macau SAR 61 Political, Social and Economic Data LIU Jen-Kai Taiwan 65 Political, Social and Economic Data LIU Jen-Kai ISSN 0943-7533 All information given here is derived from generally accessible sources. Publisher/Distributor: GIGA Institute of Asian Affairs Rothenbaumchaussee 32 20148 Hamburg Germany Phone: +49 (0 40) 42 88 74-0 Fax: +49 (040) 4107945 2 November 2006 The Main National Leadership of the PRC LIU Jen-Kai Abbreviations and Explanatory Notes CCP CC Chinese Communist Party Central Committee CCa Central Committee, alternate member CCm Central Committee, member CCSm Central Committee Secretariat, member PBa Politburo, alternate member PBm Politburo, member Cdr. Commander Chp. Chairperson CPPCC Chinese People’s Political Consultative Conference CYL Communist Youth League Dep. P.C. Deputy Political Commissar Dir. Director exec. executive f female Gen.Man. General Manager Gen.Sec. General Secretary Hon.Chp. Honorary Chairperson H.V.-Chp. Honorary Vice-Chairperson MPC Municipal People’s Congress NPC National People’s Congress PCC Political Consultative Conference PLA People’s Liberation Army Pol.Com. -

Xi Jinping's War on Corruption
University of Mississippi eGrove Honors College (Sally McDonnell Barksdale Honors Theses Honors College) 2015 The Chinese Inquisition: Xi Jinping's War on Corruption Harriet E. Fisher University of Mississippi. Sally McDonnell Barksdale Honors College Follow this and additional works at: https://egrove.olemiss.edu/hon_thesis Part of the Political Science Commons Recommended Citation Fisher, Harriet E., "The Chinese Inquisition: Xi Jinping's War on Corruption" (2015). Honors Theses. 375. https://egrove.olemiss.edu/hon_thesis/375 This Undergraduate Thesis is brought to you for free and open access by the Honors College (Sally McDonnell Barksdale Honors College) at eGrove. It has been accepted for inclusion in Honors Theses by an authorized administrator of eGrove. For more information, please contact [email protected]. The Chinese Inquisition: Xi Jinping’s War on Corruption By Harriet E. Fisher A thesis presented in partial fulfillment of the requirements for completion Of the Bachelor of Arts degree in International Studies at the Croft Institute for International Studies and the Sally McDonnell Barksdale Honors College The University of Mississippi University, Mississippi May 2015 Approved by: ______________________________ Advisor: Dr. Gang Guo ______________________________ Reader: Dr. Kees Gispen ______________________________ Reader: Dr. Peter K. Frost i © 2015 Harriet E. Fisher ALL RIGHTS RESERVED ii For Mom and Pop, who taught me to learn, and Helen, who taught me to teach. iii Acknowledgements I am indebted to a great many people for the completion of this thesis. First, I would like to thank my advisor, Dr. Gang Guo, for all his guidance during the thesis- writing process. His expertise in China and its endemic political corruption were invaluable, and without him, I would not have had a topic, much less been able to complete a thesis. -

China and Weapons of Mass Destruction: Implications for the United States
China and Weapons of Mass Destruction: Implications for the United States China and Weapons of Mass Destruction: Implications for the United States 5 November 1999 This conference was sponsored by the National Intelligence Council and Federal Research Division. The views expressed in this report are those of individuals and do not represent official US intelligence or policy positions. The NIC routinely sponsors such unclassified conferences with outside experts to gain knowledge and insight to sharpen the level of debate on critical issues. Introduction | Schedule | Papers | Appendix I | Appendix II | Appendix III | Appendix IV Introduction This conference document includes papers produced by distinguished experts on China's weapons-of-mass-destruction (WMD) programs. The seven papers were complemented by commentaries and general discussions among the 40 specialists at the proceedings. The main topics of discussion included: ● The development of China's nuclear forces. ● China's development of chemical and biological weapons. ● China's involvement in the proliferation of WMD. ● China's development of missile delivery systems. ● The implications of these developments for the United States. Interest in China's WMD stems in part from its international agreements and obligations. China is a party to the International Atomic Energy Agency (IAEA), the Treaty on the Non-Proliferation of Nuclear Weapons (NPT), the Zangger Committee, and the Chemical Weapons Convention (CWC) and has signed but not ratified the Comprehensive Nuclear Test Ban Treaty (CTBT). China is not a member of the Australia Group, the Wassenaar Arrangement, the Nuclear Suppliers Group, or the Missile Technology Control Regime (MTCR), although it has agreed to abide by the latter (which is not an international agreement and lacks legal authority). -

Risk of 2019 Novel Coronavirus Importations Throughout China Prior to the Wuhan Quarantine
medRxiv preprint doi: https://doi.org/10.1101/2020.01.28.20019299; this version posted February 3, 2020. The copyright holder for this preprint (which was not certified by peer review) is the author/funder, who has granted medRxiv a license to display the preprint in perpetuity. It is made available under a CC-BY-NC-ND 4.0 International license . Title: Risk of 2019 novel coronavirus importations throughout China prior to the Wuhan quarantine 1,+ 2,+ 2 3 4 Authors: Zhanwei Du , Lin Wang , Simon Cauchemez , Xiaoke Xu , Xianwen Wang , 5 1,6* Benjamin J. Cowling , and Lauren Ancel Meyers Affiliations: 1. The University of Texas at Austin, Austin, Texas 78712, The United States of America 2. Institut Pasteur, 28 rue du Dr Roux, Paris 75015, France 3. Dalian Minzu University, Dalian 116600, China. 4. Dalian University of Technology, Dalian 116024, China 5. The University of Hong Kong, Sassoon Rd 7, Hong Kong SAR, China 6. Santa Fe Institute, Santa Fe, New Mexico, The United States of America Corresponding author: Lauren Ancel Meyers Corresponding author email: [email protected] + These first authors contributed equally to this article Abstract On January 23, 2020, China quarantined Wuhan to contain an emerging coronavirus (2019-nCoV). Here, we estimate the probability of 2019-nCoV importations from Wuhan to 369 cities throughout China before the quarantine. The expected risk exceeds 50% in 128 [95% CI 75 186] cities, including five large cities with no reported cases by January 26th. NOTE: This preprint reports new research that has not been certified by peer review and should not be used to guide clinical practice. -

The Romance of the Three Kingdoms Podcast. This Is Episode 78. Hey
Welcome to the Romance of the Three Kingdoms Podcast. This is episode 78. Hey, guess what? We just passed the midway point of the novel, and guess what? We still don’t have three kingdoms in this Romance of the THREE Kingdoms. But stay with me, because we’re about to take a big step toward that this week. So last time, we left Liu Bei in a bit of a dicey situation. His plot with Zhang Song to take over the Riverlands leaked out, and Zhang Song lost his head because of it. Not only that, Liu Zhang was at long last on to his dear kinsman’s true intentions and ordered his men to strengthen defenses at all the key points. While this was going on, Liu Bei was putting into action his own plan, which called for pretending that he was leaving the Riverlands. His first stop was going to be Fucheng (2,2), and he sent word on ahead to the two generals defending Fu (2) River Pass that he would like to bid them goodbye before he left. The two officers, Yang (2) Huai (2) and Gao (1) Pei (4), had long been suspicious of Liu Bei, and they decided that this would be the perfect opportunity to assassinate him. So they each stashed a dagger under their clothes and took 200 men with them to go see Liu Bei. Meanwhile, as Liu Bei was approaching the Fu (2) River, his military strategist Pang Tong advised him, “If Yang Huai and Gao Pei come to meet us without hesitation, we must be on guard. -

Empty Cloud, the Autobiography of the Chinese Zen Master Xu
EMPTY CLOUD The Autobiography of the Chinese Zen Master XU YUN TRANSLATED BY CHARLES LUK Revised and Edited by Richard Hunn The Timeless Mind . Undated picture of Xu-yun. Empty Cloud 2 CONTENTS Contents .......................................................................................... 3 Acknowledgements ......................................................................... 4 Introduction .................................................................................... 5 CHAPTER ONE: Early Years ............................................................ 20 CHAPTER TWO: Pilgrimage to Mount Wu-Tai .............................. 35 CHAPTER THREE: The Journey West ............................................. 51 CHAPTER FOUR: Enlightenment and Atonement ......................... 63 CHAPTER FIVE: Interrupted Seclusion .......................................... 75 CHAPTER SIX: Taking the Tripitaka to Ji Zu Shan .......................... 94 CHAPTER SEVEN: Family News ................................................... 113 CHAPTER EIGHT: The Peacemaker .............................................. 122 CHAPTER NINE: The Jade Buddha ............................................... 130 CHAPTER TEN: Abbot At Yun-Xi and Gu-Shan............................. 146 CHAPTER ELEVEN: Nan-Hua Monastery ..................................... 161 CHAPTER TWELVE: Yun-Men Monastery .................................... 180 CHAPTER THIRTEEN: Two Discourses ......................................... 197 CHAPTER FOURTEEN: At the Yo Fo & Zhen Ru Monasteries -

Asia Focus #3
PROGRAMME ASIE QUELLE COMPOSITION DU POLITBURO ET DU COMITÉ CENTRAL CHINOIS APRÈS 2017 ? Par Alex PAYETTE STAGIAIRE POSTDOCTORAL CRSH UNIVERSITÉ DE MONTREAL OCTOBRE 2016 Septembre 2016 ASIA FOCUS #3 l’IRIS ASIA FOCUS #3 - PROGRAMME ASIE / Octobre 2016 lors que 2016 se termine et que la campagne anticorruption agressivement menée par la tristement célèbre « jiwei » [纪委] a pris fin, il ne reste que A quelques mois pour finaliser la sélection interne des cadres qui seront appelés à être élus en novembre au Politburo ainsi qu’au Comité central. Cela dit, depuis la fin de 2015, nous avons pu remarquer un certain durcissement, voire même un « repli » de la part de Xi, tant dans son attitude face au pouvoir (p. ex. retour aux idiomes/symboles maoïstes, méfiance ouverte de l’Occident, attitude de plus en plus inflexible en matière de structures internationales, etc.), que dans son attitude envers certains patriarches du Parti, notamment Jiang Zemin (président de la République populaire entre 1993 et 2003) et Hu Jintao (président de 2003 à 2013), ainsi qu’envers les autres forces en présence sur la scène politique chinoise (par exemple la Ligue des jeunesses communistes [共青团]1, la « faction du pétrole » [石油帮]2, la bande Shanghai [ 上海帮], la bande du Jiangxi [江派], etc.). Ce dernier a également resserré son emprise non seulement sur Beijing – par le biais de son proche collaborateur Wang Xiaohong [王 小洪]3-, mais bien aussi sur le pays en entier. Tandis que le temps d’« abattre les tigres » [打虎] et que les déraillements de la jiwei sont encore perceptibles, en particulier dans la province du Hebei4, fort est de constater que l’impact n’est pas celui escompté, sauf dans les cas de Su Shulin [苏树林]5 et Jiang Jiemin [蒋洁敏]6, et qu’il ne sera pas vraiment possible d’évaluer les dégâts de cette campagne avant la formation du Comité central de 2022. -

Chinese Public Diplomacy: the Rise of the Confucius Institute / Falk Hartig
Chinese Public Diplomacy This book presents the first comprehensive analysis of Confucius Institutes (CIs), situating them as a tool of public diplomacy in the broader context of China’s foreign affairs. The study establishes the concept of public diplomacy as the theoretical framework for analysing CIs. By applying this frame to in- depth case studies of CIs in Europe and Oceania, it provides in-depth knowledge of the structure and organisation of CIs, their activities and audiences, as well as problems, chal- lenges and potentials. In addition to examining CIs as the most prominent and most controversial tool of China’s charm offensive, this book also explains what the structural configuration of these Institutes can tell us about China’s under- standing of and approaches towards public diplomacy. The study demonstrates that, in contrast to their international counterparts, CIs are normally organised as joint ventures between international and Chinese partners in the field of educa- tion or cultural exchange. From this unique setting a more fundamental observa- tion can be made, namely China’s willingness to engage and cooperate with foreigners in the context of public diplomacy. Overall, the author argues that by utilising the current global fascination with Chinese language and culture, the Chinese government has found interested and willing international partners to co- finance the CIs and thus partially fund China’s international charm offensive. This book will be of much interest to students of public diplomacy, Chinese politics, foreign policy and international relations in general. Falk Hartig is a post-doctoral researcher at Goethe University, Frankfurt, Germany, and has a PhD in Media & Communication from Queensland Univer- sity of Technology, Australia.