A Novel Approach to Local Multimedia Sharing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
31295004054614.Pdf (10.42Mb)
TOWARD PIN m^ SIECI£ EMANCIPATION: THE DEVELOPMENT OF INDEPENDENCE IN THOMAS HARDY'S WESSEX WOMEN by MARTHA LUAN CARTER BRUN30N, B.S., M.A. A DISSSr.TATION IN ENGLISH Submitted to the Graduate Faculty of Texas Technoloc:ical College in Partial Fulfillment of the Requirements for the Degree of DOCTOR OP PHILOSOPHY Approved AC 90) ACKN j^yLL-roM;- NTS I am deeply Indebted to Dr. Roger L, Brooks for aerving as director of this disserfefitloa and for his con- atant assistance end encouragement over T;he past several yearStt I am also grateful to the other members of my com-» mittee^ Dr» J« T, HcCullen and rr# Jacqueline Collins, for their generous aid anri interest. ii TABL:^ OF CONTENTS Page ACKHOWLED(H^<NTS •«.... ii TVT ONE INTFiODUCTION •.. 1 ?^nT -TWO HAPDY»S WOMEN RiilACT TO SJCIAL CO?^V..IiTIul^S Chapter I Conventional Reaction in uhe Early ^.lovels ••••••••••15 Chapter II Rebels Hevolt. Others Conio/m: The HldfUe Ifovels • • 1^.6 Chapter III A Finer Dividing Line for Con ventions: The Mayor of Caster- bridge and The Woodlanders • . • 35 Chapter IV The New Compounds: teas of the D<Jrbervilles, Jude the oFscurej and The Well-Beloved • • • . • 11? PART TiAih^:: CO'ICLUSION ••••••• •...••• 1U9 BIBLIOG APrlY • • 159 iii PART ONE INTPODUCTI.N Critics, even though they do not consistently inter pret his oharaoterizations, consider among the foremost of Thomas Hardy*s achievements his characterization of women* One does not have to go beyond major critical studies, how ever, to find ample comment on the women as well as to estab lish the -

Nyon Driftsanvisning Online-Version Sv Bruksanvisning I Original
Nyon Driftsanvisning Online-version sv Bruksanvisning i original 1 270 020 Wsv (2017.07) T / 68 2 Innehållsförteckning Säkerhetsanvisningar . 5 Allmänna säkerhetsanvisningar . 5 Säkerhetsanvisningar för eBikes . 6 Säkerhetsanvisningar i samband med navigeringen . 8 Hjärtliga gratulationer . 9 Uppdateringar . 9 De första stegen . 10 Manöversystemet ”Nyon” . 12 Premiumfunktioner . 13 Smartphone-kompatibilitet . 14 Manövrering . 15 Huvudmeny . 16 Driftstart . 17 Förutsättningar . 17 In-/urkoppling av elcykelsystemet . 17 Sätta in och ta ut cykeldatorn . 18 Sätta/stänga av cykeldatorn . 18 Energiförsörjning av externa enheter via USB-kontaktdonet . 19 Idrifttagning av cykeldatorn . 19 Inloggning i cykeldatorn . 20 Anslut hjärtfrekvensbältet till Nyon . 21 1 270 020 Wsv | (19.7.17) Bosch eBike Systems 3 Drift . 22 Visningar och inställningar av cykeldatorn . 22 Driftsläge ”Dashboard” . 22 Driftsläge ”Ride” . 24 Driftsläge ”Karta & navigation” . 26 Driftsläge ”Fitness” . 30 Driftsläge ”Inställningar” . 32 Statusvisningar . 34 Cykeldatorns energiförsörjning . 35 Återställa Nyon . 35 Indikering av batteriets laddningstillstånd . 36 Inställning av assistansgrad . 37 In-/urkoppling av ledhjälp . 39 Tända/släcka cykelbelysning . 39 eShift (tillval) . 40 Visningar och inställningar av Smartphone-applikationen ”Bosch eBike Connect” . 41 Aktivering av applikationen ”Bosch eBike Connect” . 42 Registrering via Smartphone och Bluetooth®-koppling . 43 Huvudmeny till ”Bosch eBike Connect” . 44 Menypunkt ”Dashboard” . 45 Menypunkt ”Aktiviteter” . 46 Menypunkt ”Karta” . 47 Menypunkt ”Butik” . 48 Menypunkt ”Inställningar” . 49 Överföring av kartorna till Nyon . 51 Menypunkt ”Hjälp” . 52 Bosch eBike Systems 1 270 020 Wsv | (19.7.17) 4 Visningar och inställningar på online-portalen . 53 Online-registrering . 53 Huvudmeny online-portal . 54 Menypunkt ”Scrivboard” . 54 Menypunkt ”Ruttplanering” . 55 Importera GPX-track . 56 Menypunkt ”Aktiviteter” . 57 Menypunkt ”eBike System” . 58 Menypunkt ”Hjälp” . 58 Menypunkten ”Profil” . -

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

What Can Apple TV™ Teach Us About Digital Signage?
What can Apple TV™ teach us about Digital Signage? Mark Hemphill | @ScreenScape July 2016 Executive Summary As a savvy communicator, you could be increasing revenue by building dynamic media channels into every one of your business locations via digital signage, yet something is holding you back. The cost and complexity associated with such technology is still too high for the average business owner to tackle. Or is it? Some of the traditional vendors in the digital signage industry make the task of connecting and controlling a few screens out to be a momentous challenge, a task for high paid experts. On the other hand, a new class of technologies has arrived in the home entertainment world that strips the exercise down to basics. And it’s surging in popularity. Apple TV™, and other similar streaming Internet devices, have managed to successfully eliminate the need for complicated hardware and complex installation processes to allow average non-technical homeowners to bring the Internet to their television screens. This trend in consumer entertainment offers insights we can adapt to the commercial world, lessons for digital signage vendors and their customers, which lead towards to simpler, more cost-effective, more user-friendly, and more scalable solutions. This article explores some of the following lessons in detail: • Simple appliances outperform PCs and Macs as digital media players • Sourcing and mounting a TV is not the critical challenge • In order to scale, digital signage networks must be designed for average non-technical users to operate • Creating an epic viewing experience isn’t as important as enabling a large and diverse network • Simplicity and cost-effectiveness go hand in hand By making it easier to connect and control screens, tomorrow’s digital signage solutions will help more businesses to reap the benefits of place-based media. -
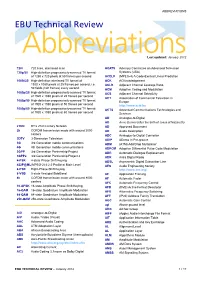
ABBREVIATIONS EBU Technical Review
ABBREVIATIONS EBU Technical Review AbbreviationsLast updated: January 2012 720i 720 lines, interlaced scan ACATS Advisory Committee on Advanced Television 720p/50 High-definition progressively-scanned TV format Systems (USA) of 1280 x 720 pixels at 50 frames per second ACELP (MPEG-4) A Code-Excited Linear Prediction 1080i/25 High-definition interlaced TV format of ACK ACKnowledgement 1920 x 1080 pixels at 25 frames per second, i.e. ACLR Adjacent Channel Leakage Ratio 50 fields (half frames) every second ACM Adaptive Coding and Modulation 1080p/25 High-definition progressively-scanned TV format ACS Adjacent Channel Selectivity of 1920 x 1080 pixels at 25 frames per second ACT Association of Commercial Television in 1080p/50 High-definition progressively-scanned TV format Europe of 1920 x 1080 pixels at 50 frames per second http://www.acte.be 1080p/60 High-definition progressively-scanned TV format ACTS Advanced Communications Technologies and of 1920 x 1080 pixels at 60 frames per second Services AD Analogue-to-Digital AD Anno Domini (after the birth of Jesus of Nazareth) 21CN BT’s 21st Century Network AD Approved Document 2k COFDM transmission mode with around 2000 AD Audio Description carriers ADC Analogue-to-Digital Converter 3DTV 3-Dimension Television ADIP ADress In Pre-groove 3G 3rd Generation mobile communications ADM (ATM) Add/Drop Multiplexer 4G 4th Generation mobile communications ADPCM Adaptive Differential Pulse Code Modulation 3GPP 3rd Generation Partnership Project ADR Automatic Dialogue Replacement 3GPP2 3rd Generation Partnership -

Enable Mobile Ecosystem on Intel Platforms
Mobility Ecosystem business models and ecosystem in change Oliver Buschmann October 22, 2013 Intel confidential — Do Not Forward Key ecosystem & business model changes Android rising Verticali- Device zation & composition UX race China low- ‘Subsidizers’ cost emerging Intel confidential History of Smartphone ecosystem disruption Symbian iOS Blackberry Palm Android Windows Disruption Disruption Wave 2 Disruption Wave 1 Low Cost Wave 3? Integration Modular 3 Intel confidential Ecosytems verticalize with different Business Monetization Data & Transaction Revenue Advertizing Adv / ~$44B Search: Ads, Web Svc: Transaction $3 B $3 B Apps & Revenue SW & Content: $12B Media, eCom. Services ~$20 B Apps : $ND Revenue Apps : Applicat.: ~$1B $27 B OS OS $30 B Consoles, Device Devices Devices SP, Tb, Wb: Tablets Hardware $145 B $104B $5B $13 B Si & Mfg Si Revenue $14 B Revenue Legend: Observed/Company reported Supposition Core monetization area 4 Intel confidential The race for best User Experience Leadership capable today Solution in market, not currently leadershipNo solution in market or limited 2013 UX Ecosystem Landscape traction/capability Capability Intel Apple Google Microsoft Samsung Qualcomm Personal Nuance Genie Siri Google Now N/A – Bing S-Voice Platform focus Assistant Intel PA Notifications Wallet Nuance Bing HW accel Speech / NLU Siri / Nuance Google Voice S-Voice / Nuance HW accel, LPAL Tell Me LPAL Personal Personal Assistant Location Intel LBS, Chipset Maps Maps Maps CSR / Android iZat Context CSP, Sensor Hub Siri Google Now Context -

Technology Ties: Getting Real After Microsoft
i c a r u s Winter/Spring 2005 Technology Ties: Getting Real after Microsoft The D.C. Circuit’s 2001 decision in United States v. Microsoft opened the door for high-tech monopolists to tie products Scott Sher together if they can demonstrate that the procompetitive Wilson Sonsini Goodrich & Rosati justification for their practice outweighs the competitive harm. Reston, VA Although not yet endorsed by the Supreme Court, the [email protected] Microsoft decision poses a significant threat to stand-alone application providers selling products in dominant operating environments where the operating systems (“OS”) provider also sells competitive stand-alone applications. In the recently-filed private lawsuit—Real Networks v. Microsoft1— Real Networks included in its complaint tying allegations against Microsoft, a dominant OS provider, claiming that the defendant tied the sale of its OS to the purchase of (allegedly less desirable) applications for its operating system. The fate of lawsuits such as Real is almost assuredly contingent upon whether courts follow the Microsoft holding and resulting legal standard or adhere to a more traditional tying analysis, which requires per se condemnation of such practices. These cases and the development of the law of technology ties are likely to have a profound effect on the development of future operating systems and the long-term viability of many independent application providers who offer products that function in such OS’s. With dominant OS providers like Microsoft reaching further into the application world— through the development and/or acquisition of applications that function on their dominant OS environments—OS providers increasingly are becoming competitors to independent application providers, while at the same time providing the industry-standard OS on which these applications run. -

Review: a Digital Video Player to Support Music Practice and Learning Emond, Bruno; Vinson, Norman; Singer, Janice; Barfurth, M
NRC Publications Archive Archives des publications du CNRC ReView: a digital video player to support music practice and learning Emond, Bruno; Vinson, Norman; Singer, Janice; Barfurth, M. A.; Brooks, Martin This publication could be one of several versions: author’s original, accepted manuscript or the publisher’s version. / La version de cette publication peut être l’une des suivantes : la version prépublication de l’auteur, la version acceptée du manuscrit ou la version de l’éditeur. Publisher’s version / Version de l'éditeur: Journal of Technology in Music Learning, 4, 1, 2007 NRC Publications Record / Notice d'Archives des publications de CNRC: https://nrc-publications.canada.ca/eng/view/object/?id=2573dfda-4fa0-4a7f-b8e0-4014b537e486 https://publications-cnrc.canada.ca/fra/voir/objet/?id=2573dfda-4fa0-4a7f-b8e0-4014b537e486 Access and use of this website and the material on it are subject to the Terms and Conditions set forth at https://nrc-publications.canada.ca/eng/copyright READ THESE TERMS AND CONDITIONS CAREFULLY BEFORE USING THIS WEBSITE. L’accès à ce site Web et l’utilisation de son contenu sont assujettis aux conditions présentées dans le site https://publications-cnrc.canada.ca/fra/droits LISEZ CES CONDITIONS ATTENTIVEMENT AVANT D’UTILISER CE SITE WEB. Questions? Contact the NRC Publications Archive team at [email protected]. If you wish to email the authors directly, please see the first page of the publication for their contact information. Vous avez des questions? Nous pouvons vous aider. Pour communiquer directement avec un auteur, consultez la première page de la revue dans laquelle son article a été publié afin de trouver ses coordonnées. -

Jejening BULLETM Guarantees Advertlaera Aorangl , , 2IU.: ....Sept
HWIHIIIHIIIIIIIIIIIUIHmilllllHOllWWI, ' yv?f: !Paily WOMEN READ THE ADS AND BUY THE GOODS STEAMER TABLE, The local merchant needt a From Ban Francisco! 1 paper that reachea the Mongolia . f. .'. j.SodL 1 ' ..... greateat number of H Ventura i. Sept. (J, people In their For 8n Francisco: ' hornet. Manchuria Sept. 8 i f3f THE .' Alameda..: ...Sept 20 P- - St EVENING BULLETIN g Korea t Sept. 22 fills the evening field and From Vancouver: JEjENING BULLETM guarantees advertlaera Aorangl , , 2IU.: ....Sept. both quantity and qual- For Vancouver: ity of circulation. " " " " Mlowera Sept. 20, THE BULLETIN IS HONOLULU'S HOME PAPER fSD O'CLOCK EDITION mmmmmms Voi XII No. 3169 HONOLULU. TERRITORY OjP HAWAII. MONDAY, SEPTEMBER i, 1905 Pbiob 6 Cknts. Some Straight Talk LABOR PEACE TOMORROW While tl i Outing At Pearl Harbor Waiting For Quorum I BASEBALITODAY Y IS MI a Calls Crowd To m FINAL SHOTS ARE Peninsula AIIWA CENTRAL COMMITTEE'S UNOFFICIAL IDEAS D. A. CS AND ELKS IIS TERRITORY OFFICERS REST, FOR CHAMPIONSHIP The Republican Territorial Central (Lane "To smooth things over." -- "COUNTY SERVANTS TOIL Committee met at Republican head- Clarke "To go to I, hear" he has a jGood Property Will Soon FIRED AT FRONT now " quarters Saturday evening to hoar o WEATHER REPORTED FINE AT lane, Interrupting "Ko doubt the GOOD WEATHER PROMISED FOR PARK KAM3 AND MAILES report of on revi- Be Opened For the reports back on tho mainland were DASEQALL, GAME9 AND EX- PLAY FIR8T FOR TAIL- - of Less sion party rules. than halt a stretched a bit; tho reporters must CURSIONDANCING AT ENDERS. -

UNIVERSIDAD AUTÓNOMA DE CIUDAD JUÁREZ Instituto De Ingeniería Y Tecnología Departamento De Ingeniería Eléctrica Y Computación
UNIVERSIDAD AUTÓNOMA DE CIUDAD JUÁREZ Instituto de Ingeniería y Tecnología Departamento de Ingeniería Eléctrica y Computación GRABADOR DE VIDEO DIGITAL UTILIZANDO UN CLUSTER CON TECNOLOGÍA RASPBERRY PI Reporte Técnico de Investigación presentado por: Fernando Israel Cervantes Ramírez. Matrícula: 98666 Requisito para la obtención del título de INGENIERO EN SISTEMAS COMPUTACIONALES Profesor Responsable: M.C. Fernando Estrada Saldaña Mayo de 2015 ii Declaraci6n de Originalidad Yo Fernando Israel Cervantes Ramirez declaro que el material contenido en esta publicaci6n fue generado con la revisi6n de los documentos que se mencionan en la secci6n de Referencias y que el Programa de C6mputo (Software) desarrollado es original y no ha sido copiado de ninguna otra fuente, ni ha sido usado para obtener otro tftulo o reconocimiento en otra Instituci6n de Educaci6n Superior. Nombre alumno IV Dedicatoria A Dios porque Él es quien da la sabiduría y de su boca viene el conocimiento y la inteligencia. A mis padres y hermana por brindarme su apoyo y ayuda durante mi carrera. A mis tíos y abuelos por enseñarme que el trabajo duro trae sus recompensas y que no es imposible alcanzar las metas soñadas, sino que solo es cuestión de perseverancia, trabajo, esfuerzo y tiempo. A mis amigos: Ana, Adriel, Miguel, Angélica, Deisy, Jonathan, Antonio, Daniel, Irving, Lupita, Christian y quienes me falte nombrar, pero que se han convertido en verdaderos compañeros de vida. v Agradecimientos Agradezco a Dios por haberme permitido llegar hasta este punto en la vida, sin Él, yo nada sería y es Él quien merece el primer lugar en esta lista. Gracias Señor porque tu mejor que nadie sabes cuánto me costó, cuanto espere, cuanto esfuerzo y trabajo invertí en todos estos años, gracias. -

System Tools Reference Manual for Filenet Image Services
IBM FileNet Image Services Version 4.2 System Tools Reference Manual SC19-3326-00 IBM FileNet Image Services Version 4.2 System Tools Reference Manual SC19-3326-00 Note Before using this information and the product it supports, read the information in “Notices” on page 1439. This edition applies to version 4.2 of IBM FileNet Image Services (product number 5724-R95) and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright IBM Corporation 1984, 2019. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents About this manual 17 Manual Organization 18 Document revision history 18 What to Read First 19 Related Documents 19 Accessing IBM FileNet Documentation 20 IBM FileNet Education 20 Feedback 20 Documentation feedback 20 Product consumability feedback 21 Introduction 22 Tools Overview 22 Subsection Descriptions 35 Description 35 Use 35 Syntax 35 Flags and Options 35 Commands 35 Examples or Sample Output 36 Checklist 36 Procedure 36 May 2011 FileNet Image Services System Tools Reference Manual, Version 4.2 5 Contents Related Topics 36 Running Image Services Tools Remotely 37 How an Image Services Server can hang 37 Best Practices 37 Why an intermediate server works 38 Cross Reference 39 Backup Preparation and Analysis 39 Batches 39 Cache 40 Configuration 41 Core Files 41 Databases 42 Data Dictionary 43 Document Committal 43 Document Deletion 43 Document Services 44 Document Retrieval 44 Enterprise Backup/Restore (EBR) -

Cutting the Cable Cord
3/11/2021 The views, opinions, and information expressed during this • March 11, 6:30-7:30 PM webinar are those of the presenter and are not the views or opinions of the Newton Public Library. The Newton Public Library • FREE! NO REGISTRATION REQUIRED makes no representation or warranty with respect to the webinar or any information or materials presented therein. Users of webinar materials should not rely upon or construe the Thinking of cutting the cord? What are your options? ChromeCast information or resource materials contained in this webinar as Why and why not do it, Apple TV, Roku alternatives and more sources of entertainment. Sling, Hulu, Netflix legal or other professional advice and should not act or fail to act To log in live from home go to: based on the information in these materials without seeking the services of a competent legal or other specifically specialized https://kslib.zoom.us/j/561178181 professional. Watch the recorded presentation anytime after the 15th or Recorded https://kslib.info/1180/Digital-Literacy---Tech-Talks Presenter: Nathan, IT Supervisor, at the Newton Public Library 1. Protect your computer • A computer should always have the most recent updates installed for spam filters, anti-virus and anti-spyware software and http://www.districtdispatch.org/wp-content/uploads/2012/03/triple_play_web.png a secure firewall. http://cdn.greenprophet.com/wp-content/uploads/2012/04/frying-pan-kolbotek-neoflam-560x475.jpg What is “Cutting the Cord” Cable TV Cord Cutting (verb): The act of canceling your cable or Cable is the immediate answer satellite subscription in favor of a more affordable and obvious choice with the most television viewing option.