Some Unix and Emacs Commands
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CS101 Lecture 9
How do you copy/move/rename/remove files? How do you create a directory ? What is redirection and piping? Readings: See CCSO’s Unix pages and 9-2 cp option file1 file2 First Version cp file1 file2 file3 … dirname Second Version This is one version of the cp command. file2 is created and the contents of file1 are copied into file2. If file2 already exits, it This version copies the files file1, file2, file3,… into the directory will be replaced with a new one. dirname. where option is -i Protects you from overwriting an existing file by asking you for a yes or no before it copies a file with an existing name. -r Can be used to copy directories and all their contents into a new directory 9-3 9-4 cs101 jsmith cs101 jsmith pwd data data mp1 pwd mp1 {FILES: mp1_data.m, mp1.m } {FILES: mp1_data.m, mp1.m } Copy the file named mp1_data.m from the cs101/data Copy the file named mp1_data.m from the cs101/data directory into the pwd. directory into the mp1 directory. > cp ~cs101/data/mp1_data.m . > cp ~cs101/data/mp1_data.m mp1 The (.) dot means “here”, that is, your pwd. 9-5 The (.) dot means “here”, that is, your pwd. 9-6 Example: To create a new directory named “temp” and to copy mv option file1 file2 First Version the contents of an existing directory named mp1 into temp, This is one version of the mv command. file1 is renamed file2. where option is -i Protects you from overwriting an existing file by asking you > cp -r mp1 temp for a yes or no before it copies a file with an existing name. -
Common Commands Cheat Sheet by Mmorykan Via Cheatography.Com/89673/Cs/20411
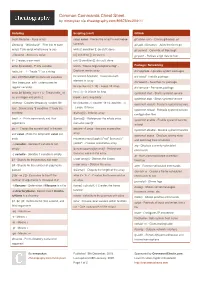
Common Commands Cheat Sheet by mmorykan via cheatography.com/89673/cs/20411/ Scripting Scripting (cont) GitHub bash filename - Runs script sleep value - Forces the script to wait value git clone <url > - Clones gitkeeper url Shebang - "# !bi n/b ash " - First line of bash seconds git add <fil ena me> - Adds the file to git script. Tells script what binary to use while [[ condition ]]; do stuff; done git commit - Commits all files to git ./file name - Also runs script if [[ condition ]]; do stuff; fi git push - Pushes all git files to host # - Creates a comment until [[ condition ]]; do stuff; done echo ${varia ble} - Prints variable words=" h ouse dogs telephone dog" - Package / Networking hello_int = 1 - Treats "1 " as a string Declares words array dnf upgrade - Updates system packages Use UPPERC ASE for constant variables for word in ${words} - traverses each dnf install - Installs package element in array Use lowerc ase _wi th_ und ers cores for dnf search - Searches for package for counter in {1..10} - Loops 10 times regular variables dnf remove - Removes package for ((;;)) - Is infinite for loop echo $(( ${hello _int} + 1 )) - Treats hello_int systemctl start - Starts systemd service as an integer and prints 2 break - exits loop body systemctl stop - Stops systemd service mktemp - Creates temporary random file for ((count er=1; counter -le 10; counter ++)) systemctl restart - Restarts systemd service test - Denoted by "[[ condition ]]" tests the - Loops 10 times systemctl reload - Reloads systemd service condition -

Unix (And Linux)
AWK....................................................................................................................................4 BC .....................................................................................................................................11 CHGRP .............................................................................................................................16 CHMOD.............................................................................................................................19 CHOWN ............................................................................................................................26 CP .....................................................................................................................................29 CRON................................................................................................................................34 CSH...................................................................................................................................36 CUT...................................................................................................................................71 DATE ................................................................................................................................75 DF .....................................................................................................................................79 DIFF ..................................................................................................................................84 -

Laboratory 1: Getting Familiar with GLUE UNIX Programming Environment
Laboratory 1: Getting Familiar with GLUE UNIX Programming Environment Lecture notes: 1. Scope of the course Prerequisite for ENEE 150 (see the last page for more details), very basic skills in programming and UNIX. a. Principles of programming and software development. b. C will be used as the programming language to illustrate the concepts. c. Basic skills in UNIX operating systems. 2. How to program (or develop software package in the future) a. Document everything you do in each of the following steps. b. Understand the project/problem requirements c. Develop algorithm (the way or method to solve the problem) d. Plan for the implementation of your algorithm (data structure, etc.) e. Write the programming (C, C++, Java, Matlab, etc.) f. Compile the program (gcc or cc in GLUE UNIX for C codes. Compiler is the interpreter that translates the program written in the so-called high level programming languages like C by human, who call themselves programmers, and understandable by human to the low level language that the computer understands.) g. Execute, test, and debug your program on sample data. h. Go back to step d. (modify your code) if necessary (programming or syntax bugs). i. Go back to step c. or step b. if there are serious problems (algorithm or logic bugs). j. Confirm that all the project requirements are met. (output format, etc.) 3. What is UNIX? a. UNIX is an operating system, like windows, which is a complex set of computer codes that manages the activities and resources of the computer. It is very popular in universities and colleges. -

ANSWERS ΤΟ EVEN-Numbered
8 Answers to Even-numbered Exercises 2.1. WhatExplain the following unexpected are result: two ways you can execute a shell script when you do not have execute permission for the file containing the script? Can you execute a shell script if you do not have read permission for the file containing the script? You can give the name of the file containing the script as an argument to the shell (for example, bash scriptfile or tcsh scriptfile, where scriptfile is the name of the file containing the script). Under bash you can give the following command: $ . scriptfile Under both bash and tcsh you can use this command: $ source scriptfile Because the shell must read the commands from the file containing a shell script before it can execute the commands, you must have read permission for the file to execute a shell script. 4.3. AssumeWhat is the purpose ble? you have made the following assignment: $ person=zach Give the output of each of the following commands. a. echo $person zach b. echo '$person' $person c. echo "$person" zach 1 2 6.5. Assumengs. the /home/zach/grants/biblios and /home/zach/biblios directories exist. Specify Zach’s working directory after he executes each sequence of commands. Explain what happens in each case. a. $ pwd /home/zach/grants $ CDPATH=$(pwd) $ cd $ cd biblios After executing the preceding commands, Zach’s working directory is /home/zach/grants/biblios. When CDPATH is set and the working directory is not specified in CDPATH, cd searches the working directory only after it searches the directories specified by CDPATH. -
UNIX Logout ^D Or Exit Man Command Man -K Keyword Ls Ls -A Ls -L Ls -G Cp
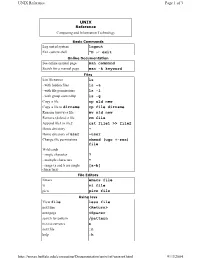
UNIX Reference Page 1 of 3 UNIX Reference Computing and Information Technology Basic Commands Log out of system logout Exit current shell ^D or exit Online Documentation See online manual page man command Search for a manual page man -k keyword Files List filenames ls - with hidden files ls -a - with file permissions ls -l - with group ownership ls -g Copy a file cp old new Copy a file to dirname cp file dirname Rename (move) a file mv old new Remove (delete) a file rm file Append file1 to file2 cat file1 >> file2 Home directory ~ Home directory of user ~user Change file permissions chmod (ugo +-rwx) file Wild cards - single character ? - multiple characters * - range (a and b are single [a-b] characters) File Editors Emacs emacs file vi vi file pico pico file Using less View file less file next line <Return> next page <Space> search for pattern /pattern next occurrence n next file :n help :h http://wings.buffalo.edu/computing/Documentation/unix/ref/unixref.html 9/13/2004 UNIX Reference Page 2 of 3 quit :q Directories Make a directory mkdir dirname Change directories cd dirname Remove a directory rmdir dirname See thecurrent directory name pwd Current directory . Parent of the current directory .. Root of the file system / Printing Print file to default printer lpr file (Bell 101) Print file to a printer at another lpr -Pprintername site file View printer queue lpq -Pprinter Remove job number jn lprm jn View job turnaround time prstat Job and Process Control Run job j in the background j& List jobs jobs Connect to job number n %n List -

Operating Systems 06R
Operating Systems 06r. Assignment 5 Discussion Paul Krzyzanowski Rutgers University Spring 2015 March 9, 2015 © 2014-2015 Paul Krzyzanowski 1 Assignment 5 • Write a simple shell – Read one line: command and arguments – Run the command with the given arguments – Wait for the command to exit – Print the exit code of the command • You need to support built-in commands – cd dirname Change the current working directory to dirname – exit value Exit the shell. Optionally specify a value for the exit code March 9, 2015 © 2014-2015 Paul Krzyzanowski 2 What you need to support • You need to support built-in commands – cd dirname Change the current working directory to dirname – exit value Exit the shell. Optionally specify a value for the exit code • You need to support pipes – Pipe: ability to redirect the output of one program to the input of another program March 9, 2015 © 2014-2015 Paul Krzyzanowski 3 You do not need to support • A command that spans multiple lines • Background processes • Environment variables • Multiple commands per line – E.g.: pwd; echo hello; ls /; who • Programming constructs – E.g., while, for, if, do • I/O redirection – E.g., ls -l >outfile • Any other constructs not specifically mentioned March 9, 2015 © 2014-2015 Paul Krzyzanowski 4 Understanding pipes • Guiding philosophy in the design of Unix commands and the Unix shell – A set of small, well-defined commands – Each command does one thing – The output of a command should ideally be in a format that is useful as the input to another command (avoid headers and other -

Configuring Your Login Session
SSCC Pub.# 7-9 Last revised: 5/18/99 Configuring Your Login Session When you log into UNIX, you are running a program called a shell. The shell is the program that provides you with the prompt and that submits to the computer commands that you type on the command line. This shell is highly configurable. It has already been partially configured for you, but it is possible to change the way that the shell runs. Many shells run under UNIX. The shell that SSCC users use by default is called the tcsh, pronounced "Tee-Cee-shell", or more simply, the C shell. The C shell can be configured using three files called .login, .cshrc, and .logout, which reside in your home directory. Also, many other programs can be configured using the C shell's configuration files. Below are sample configuration files for the C shell and explanations of the commands contained within these files. As you find commands that you would like to include in your configuration files, use an editor (such as EMACS or nuTPU) to add the lines to your own configuration files. Since the first character of configuration files is a dot ("."), the files are called "dot files". They are also called "hidden files" because you cannot see them when you type the ls command. They can only be listed when using the -a option with the ls command. Other commands may have their own setup files. These files almost always begin with a dot and often end with the letters "rc", which stands for "run commands". -

GNU Coreutils Cheat Sheet (V1.00) Created by Peteris Krumins ([email protected], -- Good Coders Code, Great Coders Reuse)
GNU Coreutils Cheat Sheet (v1.00) Created by Peteris Krumins ([email protected], www.catonmat.net -- good coders code, great coders reuse) Utility Description Utility Description arch Print machine hardware name nproc Print the number of processors base64 Base64 encode/decode strings or files od Dump files in octal and other formats basename Strip directory and suffix from file names paste Merge lines of files cat Concatenate files and print on the standard output pathchk Check whether file names are valid or portable chcon Change SELinux context of file pinky Lightweight finger chgrp Change group ownership of files pr Convert text files for printing chmod Change permission modes of files printenv Print all or part of environment chown Change user and group ownership of files printf Format and print data chroot Run command or shell with special root directory ptx Permuted index for GNU, with keywords in their context cksum Print CRC checksum and byte counts pwd Print current directory comm Compare two sorted files line by line readlink Display value of a symbolic link cp Copy files realpath Print the resolved file name csplit Split a file into context-determined pieces rm Delete files cut Remove parts of lines of files rmdir Remove directories date Print or set the system date and time runcon Run command with specified security context dd Convert a file while copying it seq Print sequence of numbers to standard output df Summarize free disk space setuidgid Run a command with the UID and GID of a specified user dir Briefly list directory -

Unix Quickref.Dvi
Summary of UNIX commands Table of Contents df [dirname] display free disk space. If dirname is omitted, 1. Directory and file commands 1994,1995,1996 Budi Rahardjo ([email protected]) display all available disks. The output maybe This is a summary of UNIX commands available 2. Print-related commands in blocks or in Kbytes. Use df -k in Solaris. on most UNIX systems. Depending on the config- uration, some of the commands may be unavailable 3. Miscellaneous commands du [dirname] on your site. These commands may be a commer- display disk usage. cial program, freeware or public domain program that 4. Process management must be installed separately, or probably just not in less filename your search path. Check your local documentation or 5. File archive and compression display filename one screenful. A pager similar manual pages for more details (e.g. man program- to (better than) more. 6. Text editors name). This reference card, obviously, cannot de- ls [dirname] scribe all UNIX commands in details, but instead I 7. Mail programs picked commands that are useful and interesting from list the content of directory dirname. Options: a user's point of view. 8. Usnet news -a display hidden files, -l display in long format 9. File transfer and remote access mkdir dirname Disclaimer make directory dirname The author makes no warranty of any kind, expressed 10. X window or implied, including the warranties of merchantabil- more filename 11. Graph, Plot, Image processing tools ity or fitness for a particular purpose, with regard to view file filename one screenfull at a time the use of commands contained in this reference card. -

C++ Basics Cs246, Fall 2020
ASSIGNMENT #2: C++ BASICS CS246, FALL 2020 Assignment #2: C++ basics Due Date 1: Wednesday, October 7, 2020, 5:00 pm Due Date 2: Wednesday, October 21, 2020, 5:00 pm Online Quiz: Wednesday, October 28, 2020, 5:00 pm Topics that must have been completed before starting Due Date 1: 1. Software Testing 2. produceOutputs and runSuite from A1 Topics that must have been completed before starting Due Date 2: 1. C++: Introduction to C++ 2. Preprocessing and Compilation Learning objectives: • C++ I/O (standard, file streams) and output formatting • argv and argc • C++ strings and stringstreams • separate compilation and Makefiles • Questions 1a, 2a, and 3a are due on Due Date 1; questions 1b, 2b, 3b, 4b, 5 and 6 are due on Due Date 2. You must submit the online quiz on Learn by the Quiz date. • On this and subsequent assignments, you will take responsibility for your own testing. This assignment is designed to get you into the habit of thinking about testing before you start writing your program. If you look at the deliverables and their due dates, you will notice that there is no C++ code due on Due Date 1. Instead, you will be asked to submit test suites for C++ programs that you will later submit by Due Date 2. Test suites will be in a format compatible with that of the latter questions of Assignment 1, so if you did a good job writing your runSuite script, that experience will serve you well here. • Design your test suites with care; they are your primary tool for verifying the correctness of your code. -

Introduction to Software Security
PONG Introduction to software security Goals of this lab: ❖ Get practical experience with manual and automatic code review ❖ Get practical experience with basic exploit development ❖ Get practical experience with protection against exploits ❖ Get practical experience with repairing vulnerable code Prerequisites: A basic understanding of security in general REVISION: 1.97 [2020-11-09] ©2007-2020 DAVID BYERS;ULF KARGÉN TABLE OF CONTENTS Part 1: Using the Linux command line ....................................................................................................................................... 1 The shell .............................................................................................................................................................................................. 1 Paths ..................................................................................................................................................................................................... 1 Commands ......................................................................................................................................................................................... 2 Part 2: The QEMU lab environment ............................................................................................................................................ 4 Setting up the local image ..........................................................................................................................................................