Chapter 1 Introduction to the Internet
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CS101 Lecture 9
How do you copy/move/rename/remove files? How do you create a directory ? What is redirection and piping? Readings: See CCSO’s Unix pages and 9-2 cp option file1 file2 First Version cp file1 file2 file3 … dirname Second Version This is one version of the cp command. file2 is created and the contents of file1 are copied into file2. If file2 already exits, it This version copies the files file1, file2, file3,… into the directory will be replaced with a new one. dirname. where option is -i Protects you from overwriting an existing file by asking you for a yes or no before it copies a file with an existing name. -r Can be used to copy directories and all their contents into a new directory 9-3 9-4 cs101 jsmith cs101 jsmith pwd data data mp1 pwd mp1 {FILES: mp1_data.m, mp1.m } {FILES: mp1_data.m, mp1.m } Copy the file named mp1_data.m from the cs101/data Copy the file named mp1_data.m from the cs101/data directory into the pwd. directory into the mp1 directory. > cp ~cs101/data/mp1_data.m . > cp ~cs101/data/mp1_data.m mp1 The (.) dot means “here”, that is, your pwd. 9-5 The (.) dot means “here”, that is, your pwd. 9-6 Example: To create a new directory named “temp” and to copy mv option file1 file2 First Version the contents of an existing directory named mp1 into temp, This is one version of the mv command. file1 is renamed file2. where option is -i Protects you from overwriting an existing file by asking you > cp -r mp1 temp for a yes or no before it copies a file with an existing name. -

Windows Command Prompt Cheatsheet
Windows Command Prompt Cheatsheet - Command line interface (as opposed to a GUI - graphical user interface) - Used to execute programs - Commands are small programs that do something useful - There are many commands already included with Windows, but we will use a few. - A filepath is where you are in the filesystem • C: is the C drive • C:\user\Documents is the Documents folder • C:\user\Documents\hello.c is a file in the Documents folder Command What it Does Usage dir Displays a list of a folder’s files dir (shows current folder) and subfolders dir myfolder cd Displays the name of the current cd filepath chdir directory or changes the current chdir filepath folder. cd .. (goes one directory up) md Creates a folder (directory) md folder-name mkdir mkdir folder-name rm Deletes a folder (directory) rm folder-name rmdir rmdir folder-name rm /s folder-name rmdir /s folder-name Note: if the folder isn’t empty, you must add the /s. copy Copies a file from one location to copy filepath-from filepath-to another move Moves file from one folder to move folder1\file.txt folder2\ another ren Changes the name of a file ren file1 file2 rename del Deletes one or more files del filename exit Exits batch script or current exit command control echo Used to display a message or to echo message turn off/on messages in batch scripts type Displays contents of a text file type myfile.txt fc Compares two files and displays fc file1 file2 the difference between them cls Clears the screen cls help Provides more details about help (lists all commands) DOS/Command Prompt help command commands Source: https://technet.microsoft.com/en-us/library/cc754340.aspx. -
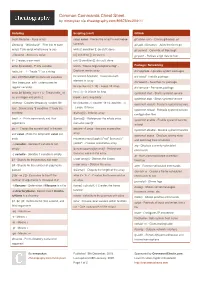
Common Commands Cheat Sheet by Mmorykan Via Cheatography.Com/89673/Cs/20411
Common Commands Cheat Sheet by mmorykan via cheatography.com/89673/cs/20411/ Scripting Scripting (cont) GitHub bash filename - Runs script sleep value - Forces the script to wait value git clone <url > - Clones gitkeeper url Shebang - "# !bi n/b ash " - First line of bash seconds git add <fil ena me> - Adds the file to git script. Tells script what binary to use while [[ condition ]]; do stuff; done git commit - Commits all files to git ./file name - Also runs script if [[ condition ]]; do stuff; fi git push - Pushes all git files to host # - Creates a comment until [[ condition ]]; do stuff; done echo ${varia ble} - Prints variable words=" h ouse dogs telephone dog" - Package / Networking hello_int = 1 - Treats "1 " as a string Declares words array dnf upgrade - Updates system packages Use UPPERC ASE for constant variables for word in ${words} - traverses each dnf install - Installs package element in array Use lowerc ase _wi th_ und ers cores for dnf search - Searches for package for counter in {1..10} - Loops 10 times regular variables dnf remove - Removes package for ((;;)) - Is infinite for loop echo $(( ${hello _int} + 1 )) - Treats hello_int systemctl start - Starts systemd service as an integer and prints 2 break - exits loop body systemctl stop - Stops systemd service mktemp - Creates temporary random file for ((count er=1; counter -le 10; counter ++)) systemctl restart - Restarts systemd service test - Denoted by "[[ condition ]]" tests the - Loops 10 times systemctl reload - Reloads systemd service condition -

Introduction to UNIX at MSI June 23, 2015 Presented by Nancy Rowe
Introduction to UNIX at MSI June 23, 2015 Presented by Nancy Rowe The Minnesota Supercomputing Institute for Advanced Computational Research www.msi.umn.edu/tutorial/ © 2015 Regents of the University of Minnesota. All rights reserved. Supercomputing Institute for Advanced Computational Research Overview • UNIX Overview • Logging into MSI © 2015 Regents of the University of Minnesota. All rights reserved. Supercomputing Institute for Advanced Computational Research Frequently Asked Questions msi.umn.edu > Resources> FAQ Website will be updated soon © 2015 Regents of the University of Minnesota. All rights reserved. Supercomputing Institute for Advanced Computational Research What’s the difference between Linux and UNIX? The terms can be used interchangeably © 2015 Regents of the University of Minnesota. All rights reserved. Supercomputing Institute for Advanced Computational Research UNIX • UNIX is the operating system of choice for engineering and scientific workstations • Originally developed in the late 1960s • Unix is flexible, secure and based on open standards • Programs are often designed “to do one simple thing right” • Unix provides ways for interconnecting these simple programs to work together and perform more complex tasks © 2015 Regents of the University of Minnesota. All rights reserved. Supercomputing Institute for Advanced Computational Research Getting Started • MSI account • Service Units required to access MSI HPC systems • Open a terminal while sitting at the machine • A shell provides an interface for the user to interact with the operating system • BASH is the default shell at MSI © 2015 Regents of the University of Minnesota. All rights reserved. Supercomputing Institute for Advanced Computational Research Bastion Host • login.msi.umn.edu • Connect to bastion host before connecting to HPC systems • Cannot run software on bastion host (login.msi.umn.edu) © 2015 Regents of the University of Minnesota. -

TEE Internal Core API Specification V1.1.2.50
GlobalPlatform Technology TEE Internal Core API Specification Version 1.1.2.50 (Target v1.2) Public Review June 2018 Document Reference: GPD_SPE_010 Copyright 2011-2018 GlobalPlatform, Inc. All Rights Reserved. Recipients of this document are invited to submit, with their comments, notification of any relevant patents or other intellectual property rights (collectively, “IPR”) of which they may be aware which might be necessarily infringed by the implementation of the specification or other work product set forth in this document, and to provide supporting documentation. The technology provided or described herein is subject to updates, revisions, and extensions by GlobalPlatform. This documentation is currently in draft form and is being reviewed and enhanced by the Committees and Working Groups of GlobalPlatform. Use of this information is governed by the GlobalPlatform license agreement and any use inconsistent with that agreement is strictly prohibited. TEE Internal Core API Specification – Public Review v1.1.2.50 (Target v1.2) THIS SPECIFICATION OR OTHER WORK PRODUCT IS BEING OFFERED WITHOUT ANY WARRANTY WHATSOEVER, AND IN PARTICULAR, ANY WARRANTY OF NON-INFRINGEMENT IS EXPRESSLY DISCLAIMED. ANY IMPLEMENTATION OF THIS SPECIFICATION OR OTHER WORK PRODUCT SHALL BE MADE ENTIRELY AT THE IMPLEMENTER’S OWN RISK, AND NEITHER THE COMPANY, NOR ANY OF ITS MEMBERS OR SUBMITTERS, SHALL HAVE ANY LIABILITY WHATSOEVER TO ANY IMPLEMENTER OR THIRD PARTY FOR ANY DAMAGES OF ANY NATURE WHATSOEVER DIRECTLY OR INDIRECTLY ARISING FROM THE IMPLEMENTATION OF THIS SPECIFICATION OR OTHER WORK PRODUCT. Copyright 2011-2018 GlobalPlatform, Inc. All Rights Reserved. The technology provided or described herein is subject to updates, revisions, and extensions by GlobalPlatform. -

Domain Tips and Tricks Lab
Installing a Domain Service for Windows: Domain Tips and Tricks Lab Novell Training Services www.novell.com OES10 ATT LIVE 2012 LAS VEGAS Novell, Inc. Copyright 2012-ATT LIVE-1-HARDCOPY PERMITTED. NO OTHER PRINTING, COPYING, OR DISTRIBUTION ALLOWED. Legal Notices Novell, Inc., makes no representations or warranties with respect to the contents or use of this documentation, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc., reserves the right to revise this publication and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. Further, Novell, Inc., makes no representations or warranties with respect to any software, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc., reserves the right to make changes to any and all parts of Novell software, at any time, without any obligation to notify any person or entity of such changes. Any products or technical information provided under this Agreement may be subject to U.S. export controls and the trade laws of other countries. You agree to comply with all export control regulations and to obtain any required licenses or classification to export, re-export or import deliverables. You agree not to export or re-export to entities on the current U.S. export exclusion lists or to any embargoed or terrorist countries as specified in the U.S. export laws. You agree to not use deliverables for prohibited nuclear, missile, or chemical biological weaponry end uses. -

Show Command Output Redirection
show Command Output Redirection The show Command Output Redirection feature provides the capability to redirect output from Cisco IOS command-line interface (CLI) show commands and more commands to a file. • Finding Feature Information, page 1 • Information About show Command Output Redirection, page 1 • How to Use the show Command Enhancement, page 2 • Additional References, page 2 • Feature Information for show Command Output Redirection, page 3 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature information, see Bug Search Tool and the release notes for your platform and software release. To find information about the features documented in this module, and to see a list of the releases in which each feature is supported, see the feature information table at the end of this module. Use Cisco Feature Navigator to find information about platform support and Cisco software image support. To access Cisco Feature Navigator, go to www.cisco.com/go/cfn. An account on Cisco.com is not required. Information About show Command Output Redirection This feature enhances the show commands in the Cisco IOS CLI to allow large amounts of data output to be written directly to a file for later reference. This file can be saved on local or remote storage devices such as Flash, a SAN Disk, or an external memory device. For each show command issued, a new file can be created, or the output can be appended to an existing file. Command output can optionally be displayed on-screen while being redirected to a file by using the tee keyword. -

Unix (And Linux)
AWK....................................................................................................................................4 BC .....................................................................................................................................11 CHGRP .............................................................................................................................16 CHMOD.............................................................................................................................19 CHOWN ............................................................................................................................26 CP .....................................................................................................................................29 CRON................................................................................................................................34 CSH...................................................................................................................................36 CUT...................................................................................................................................71 DATE ................................................................................................................................75 DF .....................................................................................................................................79 DIFF ..................................................................................................................................84 -

The Linux Command Line Presentation to Linux Users of Victoria
The Linux Command Line Presentation to Linux Users of Victoria Beginners Workshop August 18, 2012 http://levlafayette.com What Is The Command Line? 1.1 A text-based user interface that provides an environment to access the shell, which interfaces with the kernel, which is the lowest abstraction layer to system resources (e.g., processors, i/o). Examples would include CP/M, MS-DOS, various UNIX command line interfaces. 1.2 Linux is the kernel; GNU is a typical suite of commands, utilities, and applications. The Linux kernel may be accessed by many different shells e.g., the original UNIX shell (sh), the TENEX C shell (tcsh), Korn shell (ksh), and explored in this presentation, the Bourne-Again Shell (bash). 1.3 The command line interface can be contrasted with the graphic user interface (GUI). A GUI interface typically consists of window, icon, menu, pointing-device (WIMP) suite, which is popular among casual users. Examples include MS-Windows, or the X- Window system. 1.4 A critical difference worth noting is that in UNIX-derived systems (such as Linux and Mac OS), the GUI interface is an application launched from the command-line interface, whereas with operating systems like contemporary versions of MS-Windows, the GUI is core and the command prompt is a native MS-Windows application. Why Use The Command Line? 2.1 The command line uses significantly less resources to carry out the same task; it requires less processor power, less memory, less hard-disk etc. Thus, it is preferred on systems where performance is considered critical e.g., supercomputers and embedded systems. -

APPENDIX a Aegis and Unix Commands
APPENDIX A Aegis and Unix Commands FUNCTION AEGIS BSD4.2 SYSS ACCESS CONTROL AND SECURITY change file protection modes edacl chmod chmod change group edacl chgrp chgrp change owner edacl chown chown change password chpass passwd passwd print user + group ids pst, lusr groups id +names set file-creation mode mask edacl, umask umask umask show current permissions acl -all Is -I Is -I DIRECTORY CONTROL create a directory crd mkdir mkdir compare two directories cmt diff dircmp delete a directory (empty) dlt rmdir rmdir delete a directory (not empty) dlt rm -r rm -r list contents of a directory ld Is -I Is -I move up one directory wd \ cd .. cd .. or wd .. move up two directories wd \\ cd . ./ .. cd . ./ .. print working directory wd pwd pwd set to network root wd II cd II cd II set working directory wd cd cd set working directory home wd- cd cd show naming directory nd printenv echo $HOME $HOME FILE CONTROL change format of text file chpat newform compare two files emf cmp cmp concatenate a file catf cat cat copy a file cpf cp cp Using and Administering an Apollo Network 265 copy std input to std output tee tee tee + files create a (symbolic) link crl In -s In -s delete a file dlf rm rm maintain an archive a ref ar ar move a file mvf mv mv dump a file dmpf od od print checksum and block- salvol -a sum sum -count of file rename a file chn mv mv search a file for a pattern fpat grep grep search or reject lines cmsrf comm comm common to 2 sorted files translate characters tic tr tr SHELL SCRIPT TOOLS condition evaluation tools existf test test -

Installation Instruction
Rev 1/2020 Installation Instruction Please read the instructions completely before beginning the installation. Circ Collection Model Number: 3920CI Flush both supply lines before installation, then shut off both supply lines. Minimum hole size for the spout and handle trim is 1-1/4” and maximum of 1-1/2” SPOUT INSTALLATION 1 - Remove the tee connector, spout mounting hardware and tee connector washer from the bottom of the spout assembly. Apply a ring of silicon caulking around the center hole on the top of the sink. Do not use plumbers' putty which can damage the finish of the faucet. - From the top of the deck, insert the spout's threaded shank through the center hole of the sink. Make sure the spout flange washer is properly placed underneath of the flange and gently pressed against the sink top. Rubber washer 2 - Slip the spout mounting hardware back onto the spout. First the notched rubber washer, then the notched metal washer and lastly the brass lock nut. Hand tighten the lock nut. - Tighten the lock nut. Make sure the spout does not move side ways Adjust it if necessary. - Place the tee connector washer into the tee connector and thread the tee connector onto the end of the spout shank. Tighten to seal. - Align the spout and tighten the shank lock nut firmly. Notched rubber washer Notched metal washer Spout stabilizer Brass lock nut Tee connector washer Tee connector The measurements shown are for reference only. Products and specifications shown are subject to change without notice. www.santecfaucet.com | P: 310.542.0063 F: 310.542.5681 1/7 HANDLE TRIM INSTALLATION DO NOT DISASSEMBLE HANDLE ASSEMBLY - DROP-IN VALVES 1 - Both hot and cold side handle trims are pre-assmbled for faster installation. -

Laboratory 1: Getting Familiar with GLUE UNIX Programming Environment
Laboratory 1: Getting Familiar with GLUE UNIX Programming Environment Lecture notes: 1. Scope of the course Prerequisite for ENEE 150 (see the last page for more details), very basic skills in programming and UNIX. a. Principles of programming and software development. b. C will be used as the programming language to illustrate the concepts. c. Basic skills in UNIX operating systems. 2. How to program (or develop software package in the future) a. Document everything you do in each of the following steps. b. Understand the project/problem requirements c. Develop algorithm (the way or method to solve the problem) d. Plan for the implementation of your algorithm (data structure, etc.) e. Write the programming (C, C++, Java, Matlab, etc.) f. Compile the program (gcc or cc in GLUE UNIX for C codes. Compiler is the interpreter that translates the program written in the so-called high level programming languages like C by human, who call themselves programmers, and understandable by human to the low level language that the computer understands.) g. Execute, test, and debug your program on sample data. h. Go back to step d. (modify your code) if necessary (programming or syntax bugs). i. Go back to step c. or step b. if there are serious problems (algorithm or logic bugs). j. Confirm that all the project requirements are met. (output format, etc.) 3. What is UNIX? a. UNIX is an operating system, like windows, which is a complex set of computer codes that manages the activities and resources of the computer. It is very popular in universities and colleges.