Introduction to Software Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CS101 Lecture 9
How do you copy/move/rename/remove files? How do you create a directory ? What is redirection and piping? Readings: See CCSO’s Unix pages and 9-2 cp option file1 file2 First Version cp file1 file2 file3 … dirname Second Version This is one version of the cp command. file2 is created and the contents of file1 are copied into file2. If file2 already exits, it This version copies the files file1, file2, file3,… into the directory will be replaced with a new one. dirname. where option is -i Protects you from overwriting an existing file by asking you for a yes or no before it copies a file with an existing name. -r Can be used to copy directories and all their contents into a new directory 9-3 9-4 cs101 jsmith cs101 jsmith pwd data data mp1 pwd mp1 {FILES: mp1_data.m, mp1.m } {FILES: mp1_data.m, mp1.m } Copy the file named mp1_data.m from the cs101/data Copy the file named mp1_data.m from the cs101/data directory into the pwd. directory into the mp1 directory. > cp ~cs101/data/mp1_data.m . > cp ~cs101/data/mp1_data.m mp1 The (.) dot means “here”, that is, your pwd. 9-5 The (.) dot means “here”, that is, your pwd. 9-6 Example: To create a new directory named “temp” and to copy mv option file1 file2 First Version the contents of an existing directory named mp1 into temp, This is one version of the mv command. file1 is renamed file2. where option is -i Protects you from overwriting an existing file by asking you > cp -r mp1 temp for a yes or no before it copies a file with an existing name. -
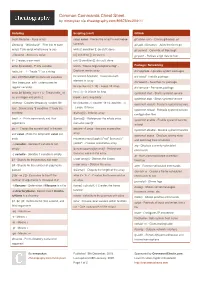
Common Commands Cheat Sheet by Mmorykan Via Cheatography.Com/89673/Cs/20411
Common Commands Cheat Sheet by mmorykan via cheatography.com/89673/cs/20411/ Scripting Scripting (cont) GitHub bash filename - Runs script sleep value - Forces the script to wait value git clone <url > - Clones gitkeeper url Shebang - "# !bi n/b ash " - First line of bash seconds git add <fil ena me> - Adds the file to git script. Tells script what binary to use while [[ condition ]]; do stuff; done git commit - Commits all files to git ./file name - Also runs script if [[ condition ]]; do stuff; fi git push - Pushes all git files to host # - Creates a comment until [[ condition ]]; do stuff; done echo ${varia ble} - Prints variable words=" h ouse dogs telephone dog" - Package / Networking hello_int = 1 - Treats "1 " as a string Declares words array dnf upgrade - Updates system packages Use UPPERC ASE for constant variables for word in ${words} - traverses each dnf install - Installs package element in array Use lowerc ase _wi th_ und ers cores for dnf search - Searches for package for counter in {1..10} - Loops 10 times regular variables dnf remove - Removes package for ((;;)) - Is infinite for loop echo $(( ${hello _int} + 1 )) - Treats hello_int systemctl start - Starts systemd service as an integer and prints 2 break - exits loop body systemctl stop - Stops systemd service mktemp - Creates temporary random file for ((count er=1; counter -le 10; counter ++)) systemctl restart - Restarts systemd service test - Denoted by "[[ condition ]]" tests the - Loops 10 times systemctl reload - Reloads systemd service condition -

CSC 405 Computer Security Linux Security
CSC 405 Computer Security Linux Security Alexandros Kapravelos [email protected] Unix / Linux • Started in 1969 at AT&T / Bell Labs • Split into a number of popular branches – BSD, System V (commercial, AT&T), Solaris, HP-UX, AIX • Inspired a number of Unix-like systems – Linux, Minix • Standardization attempts – POSIX, Single Unix Specification (SUS), Filesystem Hierarchy Standard (FHS), Linux Standard Base (LSB), ELF OS Security • Kernel vulnerability – usually leads to complete system compromise – attacks performed via system calls Kernel vulnerabilities Kernel vulnerabilities Kernel exploitation research is active Unleashing Use-Before-Initialization Vulnerabilities in the Linux Kernel Using Targeted Stack Spraying • reliably exploiting uninitialized uses on the kernel stack has been considered infeasible • code executed prior to triggering the vulnerability must leave an attacker-controlled pattern on the stack • a fully automated targeted stackspraying approach for the Linux kernel that reliably facilitates the exploitation of uninitialized uses • published in NDSS 2017 source: https://www.cc.gatech.edu/~klu38/publications/ubi-ndss17.pdf Unix • Code running in user mode is always linked to a certain identity – security checks and access control decisions are based on user identity • Unix is user-centric – no roles • User – identified by username (UID), group name (GID) – typically authenticated by password (stored encrypted) • User root – superuser, system administrator – special privileges (access resources, modify OS) – cannot -

Environment Variable and Set-UID Program Lab 1
SEED Labs – Environment Variable and Set-UID Program Lab 1 Environment Variable and Set-UID Program Lab Copyright © 2006 - 2016 Wenliang Du, All rights reserved. Free to use for non-commercial educational purposes. Commercial uses of the materials are prohibited. The SEED project was funded by multiple grants from the US National Science Foundation. 1 Overview The learning objective of this lab is for students to understand how environment variables affect program and system behaviors. Environment variables are a set of dynamic named values that can affect the way running processes will behave on a computer. They are used by most operating systems, since they were introduced to Unix in 1979. Although environment variables affect program behaviors, how they achieve that is not well understood by many programmers. As a result, if a program uses environment variables, but the programmer does not know that they are used, the program may have vulnerabilities. In this lab, students will understand how environment variables work, how they are propagated from parent process to child, and how they affect system/program behaviors. We are particularly interested in how environment variables affect the behavior of Set-UID programs, which are usually privileged programs. This lab covers the following topics: • Environment variables • Set-UID programs • Securely invoke external programs • Capability leaking • Dynamic loader/linker Readings and videos. Detailed coverage of the Set-UID mechanism, environment variables, and their related security problems can be found in the following: • Chapters 1 and 2 of the SEED Book, Computer & Internet Security: A Hands-on Approach, 2nd Edition, by Wenliang Du. -

Unix (And Linux)
AWK....................................................................................................................................4 BC .....................................................................................................................................11 CHGRP .............................................................................................................................16 CHMOD.............................................................................................................................19 CHOWN ............................................................................................................................26 CP .....................................................................................................................................29 CRON................................................................................................................................34 CSH...................................................................................................................................36 CUT...................................................................................................................................71 DATE ................................................................................................................................75 DF .....................................................................................................................................79 DIFF ..................................................................................................................................84 -

SETUID Programming Due: February 15, 2017
CSC 482/582 Assignment #3 (100 points) SETUID Programming Due: February 15, 2017 1 Introduction The learning objective of this assignment is for students to understand how environment variables affect program and system behaviors. Environment variables are a set of dynamic named values that can affect the way running processes will behave on a computer. They are used by most operating systems, including Unix and Windows. Although environment variables affect program behaviors, how they achieve that is not well understood by many programmers. Therefore, if a program uses environment variables, but the programmer do not know that they are used, the program may have vulnerabilities. In this assignment, students will learn how environment variables work, how they are propogated from parent process to child, and how they affect system/program bahivors. We are particularly interested in how environment variables affect the behavior of SETUID programs, which are usually privileged programs. SETUID is an important security mechanism in Unix operating systems. When a regular program is run, it runs with the privilege of the user executing that program. When a SETUID program is run, it runs with the privilege of the program file owner. For example, if the program’s owner is root, then when anyone runs this program, the program gains root’s privileges during its execution. SETUID allows us to perform essential tasks, such as changing passwords, but vulnerabilities in SETUID programs can allow an adversary to perform local privilege escalation. While the SETUID concept is limited to Unix, the problems of dangerous environment variables and local privilege escalation exists on all operating systems. -

Laboratory 1: Getting Familiar with GLUE UNIX Programming Environment
Laboratory 1: Getting Familiar with GLUE UNIX Programming Environment Lecture notes: 1. Scope of the course Prerequisite for ENEE 150 (see the last page for more details), very basic skills in programming and UNIX. a. Principles of programming and software development. b. C will be used as the programming language to illustrate the concepts. c. Basic skills in UNIX operating systems. 2. How to program (or develop software package in the future) a. Document everything you do in each of the following steps. b. Understand the project/problem requirements c. Develop algorithm (the way or method to solve the problem) d. Plan for the implementation of your algorithm (data structure, etc.) e. Write the programming (C, C++, Java, Matlab, etc.) f. Compile the program (gcc or cc in GLUE UNIX for C codes. Compiler is the interpreter that translates the program written in the so-called high level programming languages like C by human, who call themselves programmers, and understandable by human to the low level language that the computer understands.) g. Execute, test, and debug your program on sample data. h. Go back to step d. (modify your code) if necessary (programming or syntax bugs). i. Go back to step c. or step b. if there are serious problems (algorithm or logic bugs). j. Confirm that all the project requirements are met. (output format, etc.) 3. What is UNIX? a. UNIX is an operating system, like windows, which is a complex set of computer codes that manages the activities and resources of the computer. It is very popular in universities and colleges. -

ANSWERS ΤΟ EVEN-Numbered
8 Answers to Even-numbered Exercises 2.1. WhatExplain the following unexpected are result: two ways you can execute a shell script when you do not have execute permission for the file containing the script? Can you execute a shell script if you do not have read permission for the file containing the script? You can give the name of the file containing the script as an argument to the shell (for example, bash scriptfile or tcsh scriptfile, where scriptfile is the name of the file containing the script). Under bash you can give the following command: $ . scriptfile Under both bash and tcsh you can use this command: $ source scriptfile Because the shell must read the commands from the file containing a shell script before it can execute the commands, you must have read permission for the file to execute a shell script. 4.3. AssumeWhat is the purpose ble? you have made the following assignment: $ person=zach Give the output of each of the following commands. a. echo $person zach b. echo '$person' $person c. echo "$person" zach 1 2 6.5. Assumengs. the /home/zach/grants/biblios and /home/zach/biblios directories exist. Specify Zach’s working directory after he executes each sequence of commands. Explain what happens in each case. a. $ pwd /home/zach/grants $ CDPATH=$(pwd) $ cd $ cd biblios After executing the preceding commands, Zach’s working directory is /home/zach/grants/biblios. When CDPATH is set and the working directory is not specified in CDPATH, cd searches the working directory only after it searches the directories specified by CDPATH. -
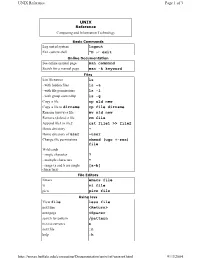
UNIX Logout ^D Or Exit Man Command Man -K Keyword Ls Ls -A Ls -L Ls -G Cp
UNIX Reference Page 1 of 3 UNIX Reference Computing and Information Technology Basic Commands Log out of system logout Exit current shell ^D or exit Online Documentation See online manual page man command Search for a manual page man -k keyword Files List filenames ls - with hidden files ls -a - with file permissions ls -l - with group ownership ls -g Copy a file cp old new Copy a file to dirname cp file dirname Rename (move) a file mv old new Remove (delete) a file rm file Append file1 to file2 cat file1 >> file2 Home directory ~ Home directory of user ~user Change file permissions chmod (ugo +-rwx) file Wild cards - single character ? - multiple characters * - range (a and b are single [a-b] characters) File Editors Emacs emacs file vi vi file pico pico file Using less View file less file next line <Return> next page <Space> search for pattern /pattern next occurrence n next file :n help :h http://wings.buffalo.edu/computing/Documentation/unix/ref/unixref.html 9/13/2004 UNIX Reference Page 2 of 3 quit :q Directories Make a directory mkdir dirname Change directories cd dirname Remove a directory rmdir dirname See thecurrent directory name pwd Current directory . Parent of the current directory .. Root of the file system / Printing Print file to default printer lpr file (Bell 101) Print file to a printer at another lpr -Pprintername site file View printer queue lpq -Pprinter Remove job number jn lprm jn View job turnaround time prstat Job and Process Control Run job j in the background j& List jobs jobs Connect to job number n %n List -

Least Privilege and Privilege Separation
CSE 127: Computer Security Least privilege and privilege separation Deian Stefan Slides adopted from John Mitchell, Dan Boneh, and Stefan Savage This week… • How to build secure systems ➤ Least privilege and privilege separation ➤ Sandboxing and isolation • Key is underlying principles not mechanisms ➤ We’re going to look at systems techniques ➤ Other ways to achieve similar goals: language-based Principles of secure design • Principle of least privilege • Privilege separation • Defense in depth ➤ Use more than one security mechanism ➤ Fail securely/closed • Keep it simple Principles of secure design • Principle of least privilege • Privilege separation • Defense in depth ➤ Use more than one security mechanism ➤ Fail securely/closed • Keep it simple Principle of Least Privilege Defn: A system should only have the minimal privileges needed for its intended purposes • What’s a privilege? ➤ Ability to access (e.g., read or write) a resource Principle of Least Privilege Defn: A system should only have the minimal privileges needed for its intended purposes • What’s a privilege? ➤ Ability to access (e.g., read or write) a resource Principle of Least Privilege Defn: A system should only have the minimal privileges needed for its intended purposes • What’s a privilege? ➤ Ability to access (e.g., read or write) a resource What’s the problem with this defn? • Talking about a huge, monolith system is not really useful • Why? Network Network User input User device File system File system Breaking a system into components • Compartmentalization and isolation ➤ Separate the system into isolated compartments ➤ Limit interaction between compartments • Why is this more meaningful? Network Network User input User device File system File system How dow we break things apart? Map compartment to user ids! • Recall: permissions in UNIX granted according to UID ➤ A process may access files, network sockets, …. -

Operating Systems 06R
Operating Systems 06r. Assignment 5 Discussion Paul Krzyzanowski Rutgers University Spring 2015 March 9, 2015 © 2014-2015 Paul Krzyzanowski 1 Assignment 5 • Write a simple shell – Read one line: command and arguments – Run the command with the given arguments – Wait for the command to exit – Print the exit code of the command • You need to support built-in commands – cd dirname Change the current working directory to dirname – exit value Exit the shell. Optionally specify a value for the exit code March 9, 2015 © 2014-2015 Paul Krzyzanowski 2 What you need to support • You need to support built-in commands – cd dirname Change the current working directory to dirname – exit value Exit the shell. Optionally specify a value for the exit code • You need to support pipes – Pipe: ability to redirect the output of one program to the input of another program March 9, 2015 © 2014-2015 Paul Krzyzanowski 3 You do not need to support • A command that spans multiple lines • Background processes • Environment variables • Multiple commands per line – E.g.: pwd; echo hello; ls /; who • Programming constructs – E.g., while, for, if, do • I/O redirection – E.g., ls -l >outfile • Any other constructs not specifically mentioned March 9, 2015 © 2014-2015 Paul Krzyzanowski 4 Understanding pipes • Guiding philosophy in the design of Unix commands and the Unix shell – A set of small, well-defined commands – Each command does one thing – The output of a command should ideally be in a format that is useful as the input to another command (avoid headers and other -

Linux Networking Cookbook.Pdf
Linux Networking Cookbook ™ Carla Schroder Beijing • Cambridge • Farnham • Köln • Paris • Sebastopol • Taipei • Tokyo Linux Networking Cookbook™ by Carla Schroder Copyright © 2008 O’Reilly Media, Inc. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (safari.oreilly.com). For more information, contact our corporate/institutional sales department: (800) 998-9938 or [email protected]. Editor: Mike Loukides Indexer: John Bickelhaupt Production Editor: Sumita Mukherji Cover Designer: Karen Montgomery Copyeditor: Derek Di Matteo Interior Designer: David Futato Proofreader: Sumita Mukherji Illustrator: Jessamyn Read Printing History: November 2007: First Edition. Nutshell Handbook, the Nutshell Handbook logo, and the O’Reilly logo are registered trademarks of O’Reilly Media, Inc. The Cookbook series designations, Linux Networking Cookbook, the image of a female blacksmith, and related trade dress are trademarks of O’Reilly Media, Inc. Java™ is a trademark of Sun Microsystems, Inc. .NET is a registered trademark of Microsoft Corporation. Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and O’Reilly Media, Inc. was aware of a trademark claim, the designations have been printed in caps or initial caps. While every precaution has been taken in the preparation of this book, the publisher and author assume no responsibility for errors or omissions, or for damages resulting from the use of the information contained herein.