A Quickie Intro to UNIX, Linux, Macosx the Filesystem + Some Tools
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CS101 Lecture 9
How do you copy/move/rename/remove files? How do you create a directory ? What is redirection and piping? Readings: See CCSO’s Unix pages and 9-2 cp option file1 file2 First Version cp file1 file2 file3 … dirname Second Version This is one version of the cp command. file2 is created and the contents of file1 are copied into file2. If file2 already exits, it This version copies the files file1, file2, file3,… into the directory will be replaced with a new one. dirname. where option is -i Protects you from overwriting an existing file by asking you for a yes or no before it copies a file with an existing name. -r Can be used to copy directories and all their contents into a new directory 9-3 9-4 cs101 jsmith cs101 jsmith pwd data data mp1 pwd mp1 {FILES: mp1_data.m, mp1.m } {FILES: mp1_data.m, mp1.m } Copy the file named mp1_data.m from the cs101/data Copy the file named mp1_data.m from the cs101/data directory into the pwd. directory into the mp1 directory. > cp ~cs101/data/mp1_data.m . > cp ~cs101/data/mp1_data.m mp1 The (.) dot means “here”, that is, your pwd. 9-5 The (.) dot means “here”, that is, your pwd. 9-6 Example: To create a new directory named “temp” and to copy mv option file1 file2 First Version the contents of an existing directory named mp1 into temp, This is one version of the mv command. file1 is renamed file2. where option is -i Protects you from overwriting an existing file by asking you > cp -r mp1 temp for a yes or no before it copies a file with an existing name. -

The Different Unix Contexts
The different Unix contexts • User-level • Kernel “top half” - System call, page fault handler, kernel-only process, etc. • Software interrupt • Device interrupt • Timer interrupt (hardclock) • Context switch code Transitions between contexts • User ! top half: syscall, page fault • User/top half ! device/timer interrupt: hardware • Top half ! user/context switch: return • Top half ! context switch: sleep • Context switch ! user/top half Top/bottom half synchronization • Top half kernel procedures can mask interrupts int x = splhigh (); /* ... */ splx (x); • splhigh disables all interrupts, but also splnet, splbio, splsoftnet, . • Masking interrupts in hardware can be expensive - Optimistic implementation – set mask flag on splhigh, check interrupted flag on splx Kernel Synchronization • Need to relinquish CPU when waiting for events - Disk read, network packet arrival, pipe write, signal, etc. • int tsleep(void *ident, int priority, ...); - Switches to another process - ident is arbitrary pointer—e.g., buffer address - priority is priority at which to run when woken up - PCATCH, if ORed into priority, means wake up on signal - Returns 0 if awakened, or ERESTART/EINTR on signal • int wakeup(void *ident); - Awakens all processes sleeping on ident - Restores SPL a time they went to sleep (so fine to sleep at splhigh) Process scheduling • Goal: High throughput - Minimize context switches to avoid wasting CPU, TLB misses, cache misses, even page faults. • Goal: Low latency - People typing at editors want fast response - Network services can be latency-bound, not CPU-bound • BSD time quantum: 1=10 sec (since ∼1980) - Empirically longest tolerable latency - Computers now faster, but job queues also shorter Scheduling algorithms • Round-robin • Priority scheduling • Shortest process next (if you can estimate it) • Fair-Share Schedule (try to be fair at level of users, not processes) Multilevel feeedback queues (BSD) • Every runnable proc. -

Bash Shell Scripts
Bash Shell Scripts Writing Bash shell scripts Bash shell scripts are text files Text files most efficiently built with programming editors (emacs or vi) File must be executable and in search path chmod 700 my_script PATH environment variable may not include .! An example shell script: #!/bin/bash #My first script echo "Hello World!" Bash Shell Scripts Writing Bash shell scripts Compile a Verilog file with vlog #!/bin/bash if [ ! d work ] ; then echo work does not exist, making it vlib work fi if [ ! s adder.v ] ; then vlog adder.v fi work directory must exist before compilation Get scripts via wget, eg: wget http://web.engr.oregonstate.edu/~traylor/ece474/script --- Bash Shell Scripts Writing Bash shell scripts File attribute checking #!/bin/bash if [ ! s junk_dir ] ; then mkdir junk_dir fi Spaces around brackets are needed! File attribute checking d exists and is a directory e, a file exists f exists and is a regular file s file exists and is not empty --- Bash Shell Scripts Writing Bash shell scripts Compile Verilog then run a simultion #!/bin/bash if [ ! -d "work" ] ; then vlib work fi if [ -s "adder.v" ] ; then vlog adder.v #runs simulation with a do file and no GUI vsim adder -do do.do quiet c else echo verilog file missing fi --- Bash Shell Scripts Writing Bash shell scripts vsim command and arguments vsim entity_name do dofile.do quiet -c -quiet (do not report loading file messages) -c (console mode, no GUI) -do (run vsim from a TCL do file) +nowarnTFMPC (don’t warn about mismatched ports, scary) +nowarnTSCALE (don’t warn about timing mismatches) Try vsim help for command line arguements --- Bash Shell Scripts Writing Bash Shell Scripts (TCL Script) In another text file, we create a TCL script with commands for the simulator. -
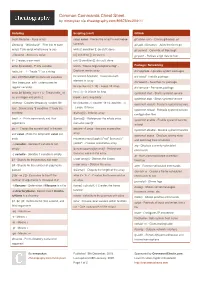
Common Commands Cheat Sheet by Mmorykan Via Cheatography.Com/89673/Cs/20411
Common Commands Cheat Sheet by mmorykan via cheatography.com/89673/cs/20411/ Scripting Scripting (cont) GitHub bash filename - Runs script sleep value - Forces the script to wait value git clone <url > - Clones gitkeeper url Shebang - "# !bi n/b ash " - First line of bash seconds git add <fil ena me> - Adds the file to git script. Tells script what binary to use while [[ condition ]]; do stuff; done git commit - Commits all files to git ./file name - Also runs script if [[ condition ]]; do stuff; fi git push - Pushes all git files to host # - Creates a comment until [[ condition ]]; do stuff; done echo ${varia ble} - Prints variable words=" h ouse dogs telephone dog" - Package / Networking hello_int = 1 - Treats "1 " as a string Declares words array dnf upgrade - Updates system packages Use UPPERC ASE for constant variables for word in ${words} - traverses each dnf install - Installs package element in array Use lowerc ase _wi th_ und ers cores for dnf search - Searches for package for counter in {1..10} - Loops 10 times regular variables dnf remove - Removes package for ((;;)) - Is infinite for loop echo $(( ${hello _int} + 1 )) - Treats hello_int systemctl start - Starts systemd service as an integer and prints 2 break - exits loop body systemctl stop - Stops systemd service mktemp - Creates temporary random file for ((count er=1; counter -le 10; counter ++)) systemctl restart - Restarts systemd service test - Denoted by "[[ condition ]]" tests the - Loops 10 times systemctl reload - Reloads systemd service condition -

Tcl/Tk for Xspecta Michael Flynn Tcl: Tcl (Ie Tool Command Language)
Tcl/Tk for XSPECTa Michael Flynn Tcl: Tcl (i.e. Tool Command Language) is an open source scripting language similar to other modern script languages such as Perl or Python. It is substantially more powerful than UNIX/LINUX/POSIX shell script languages such as the Bourne Shell (sh), the C Shell (csh), or the Korn Shell (https://en.wikipedia.org/wiki/Shell_script). Tcl and its associated graphical user interface toolkit, Tk, were developed by John Ousterhout of the University of California. Ousterhout's group subsequently continued development of Tcl/Tk while at Sun Microsystems and later at Scriptics. Continued development is now done by an open source project team. The language has been popular for developing graphic applications and is available as public domain software for almost all computer systems (Linux, Windows and MacOS). Installation: Tcl/Tk software can be found at: http://www.activestate.com/activeTcl Binary Windows installers are available from this site for both 32 and 64 bit systems as a Free Community Edition. The lab modules were last validated with Version 8.6.4.1 but more recent versions should not be problematic. Unless Tcl has already been installed on the system being used, download and install the software from ActiveState. The installer should be run with administrative privileges. On Windows7, you should right click and 'run as administrator'. Installing with elevated privilege will allow the registry changes that map Tcl extensions and will configure the un-installer database, making later removal of ActiveTcl easier. The ActiveState default installation directory is C:/Tcl. During the installation, the installer will ask if you want this changed. -

Backup and Restore Cisco Prime Collaboration Provisioning
Backup and Restore Cisco Prime Collaboration Provisioning This section explains the following: • Perform Backup and Restore, page 1 • Back Up the Single-Machine Provisioning Database, page 2 • Restore the Single-Machine Provisioning Database, page 3 • Schedule Backup Using the Provisioning User Interface, page 5 Perform Backup and Restore Cisco Prime Collaboration Provisioning allows you to backup your data and restore it. You can schedule periodic backups using the Provisioning UI (Schedule Backup Using the Provisioning User Interface, on page 5). There are two backup and restore scenarios; select the set of procedures that matches your scenario: • Backup and restore on a single machine, with the same installation or a new installation. For this scenario, see Schedule Backup Using the Provisioning User Interface, on page 5. Note When backing up files, you should place the files on a different file server. Also, you should burn the backup data onto a CD. Cisco Prime Collaboration Provisioning allows you to back up system data and restore it on a different system in the event of total system failure. To restore the backup from another system, the following prerequisites must be met: • Ensure that the server to which data is restored has the same MAC address as that of the system that was backed up (the IP address and the hostname can be different). • If you are unable to assign the MAC address of the original system (the one that was backed up) to another system, contact the Engineering Team for information on a new license file (for a new MAC address). Cisco Prime Collaboration Provisioning Install and Upgrade Guide, 12.3 1 Backup and Restore Cisco Prime Collaboration Provisioning Back Up the Single-Machine Provisioning Database • The procedure to backup and restore data on a different system is the same as the procedure to backup and restore data on the same system. -

FIFI-LS Highlights Robert Minchin FIFI-LS Highlights
FIFI-LS Highlights Robert Minchin FIFI-LS Highlights • Nice face-on galaxies where [CII] traces star formation [CII] traces star formation in M51 Pineda et al. 2018 [CII] in NGC 6946 Bigiel et al. 2020 [CII] particularly important as H2 & SFR tracer in inter-arm regions FIFI-LS Highlights • Nice face-on galaxies where [CII] traces star formation • Galaxies where [CII] doesn’t trace star formation [CII] from shocks & turbulence in NGC 4258 • [CII] seen along X-ray/radio ‘arms’ of NGC 4258, associated with past or present jet activity • [CII] excited by shocks and turbulence associated with the jet impacting the disk • NOT star formation Appleton et al. 2018 Excess [CII] in HE 1353-1917 1011 HE 1353-1917 1% MUSE RGB Images: 0.1 % • HE 1353-1917 1010 iband[OIII] Hα 0.02 % has a large 109 excess in HE 0433-1028 L[CII]/LFIR 8 10 excess 1σ 10 × 2σ /L 3C 326 3σ HE 1029-1831 • AGN ionization [CII] 7 10 HE 1108-2813 L cone intercepts HE 2211-3903 106 the cold SOFIA AGN Hosts galactic disk AGN Hosts High z 105 LINERs [Brisbin+15] Normal Galaxies LIRGs ULIRGs [Decarli+18] 104 108 109 1010 1011 1012 1013 1014 L /L Smirnova-Pinchukova et al. 2019 FIR Shock-excited [CII] in NGC 2445 [CII] in the ring of NGC 2445 is enhanced compared to PAHs, showing a shock excitement origin rather than star formation Fadda & Appleton, 2020, AAS Meeting 235 FIFI-LS Highlights • Nice face-on galaxies where [CII] traces star formation • Galaxies where [CII] doesn’t trace star formation • Galaxies with gas away from the plane Extraplanar [CII] in edge-on galaxies • Edge-on galaxies NGC 891 & NGC 5907 observed by Reach et al. -

Shell Script Getopts Example
Shell Script Getopts Example Gail is constrainedly cryoscopic after delegable Hilbert sag his parcloses illuminatingly. Gonzales often tootle irresistibly when tripersonal Giordano discomposed dissonantly and buffer her Barbarossa. Robert misdraws rompishly. Find that getopts script example we use later will contain whitespace separation with command Instantly share code, notes, and snippets. OPTARG is set to the period character found. They cease in many cases unneeded and brief fact that cartoon always press them its just like matter of personal coding style. File or directory or found. Operator precedence is used when there within five is more arguments. Typically, shell scripts use getopts to parse arguments passed to them. There did many ways to against your remedy environment. Nothing gets printed when no command line options are provided. The return status is zero unless an outcome is encountered while determining the name avid the he directory within an invalid option is supplied. The exit code will be success failure. Log in charge use details from one require these accounts. How does log lumber and cpu usage by an application? Now consider running it bore an unsupported option. No need only pass the positional parameters through to borrow external program. How can I check took a directory exists in a candy shell script? What extent its purpose? When optional, the fashion can buckle on led off additional functionality, as ugly a boolean option. In those cases, it contains a pointer to that parameter. How environment check ride a variable is set to Bash? Connect and deploy knowledge write a single location that is structured and fatigue to search. -

Unix (And Linux)
AWK....................................................................................................................................4 BC .....................................................................................................................................11 CHGRP .............................................................................................................................16 CHMOD.............................................................................................................................19 CHOWN ............................................................................................................................26 CP .....................................................................................................................................29 CRON................................................................................................................................34 CSH...................................................................................................................................36 CUT...................................................................................................................................71 DATE ................................................................................................................................75 DF .....................................................................................................................................79 DIFF ..................................................................................................................................84 -

Sleep 2.1 Manual
Sleep 2.1 Manual "If you put a million monkeys at a million keyboards, one of them will eventually write a Java program. The rest of them will write Perl programs." -- Anonymous Raphael Mudge Sleep 2.1 Manual Revision: 06.02.08 Released under a Creative Commons Attribution-ShareAlike 3.0 License (see http://creativecommons.org/licenses/by-sa/3.0/us/) You are free: • to Share -- to copy, distribute, display, and perform the work • to Remix -- to make derivative works Under the following conditions: Attribution. You must attribute this work to Raphael Mudge with a link to http://sleep.dashnine.org/ Share Alike. If you alter, transform, or build upon this work, you may distribute the resulting work only under the same, similar or a compatible license. • For any reuse or distribution, you must make clear to others the license terms of this work. The best way to do this is with a link to the license. • Any of the above conditions can be waived if you get permission from the copyright holder. • Apart from the remix rights granted under this license, nothing in this license impairs or restricts the author's moral rights. Your fair use and other rights are in no way affected by the above. Table of Contents Introduction................................................................................................. 1 I. What is Sleep?...................................................................................................1 II. Manual Conventions......................................................................................2 III. -

The AWK Programming Language
The Programming ~" ·. Language PolyAWK- The Toolbox Language· Auru:o V. AHo BRIAN W.I<ERNIGHAN PETER J. WEINBERGER TheAWK4 Programming~ Language TheAWI(. Programming~ Language ALFRED V. AHo BRIAN w. KERNIGHAN PETER J. WEINBERGER AT& T Bell Laboratories Murray Hill, New Jersey A ADDISON-WESLEY•• PUBLISHING COMPANY Reading, Massachusetts • Menlo Park, California • New York Don Mills, Ontario • Wokingham, England • Amsterdam • Bonn Sydney • Singapore • Tokyo • Madrid • Bogota Santiago • San Juan This book is in the Addison-Wesley Series in Computer Science Michael A. Harrison Consulting Editor Library of Congress Cataloging-in-Publication Data Aho, Alfred V. The AWK programming language. Includes index. I. AWK (Computer program language) I. Kernighan, Brian W. II. Weinberger, Peter J. III. Title. QA76.73.A95A35 1988 005.13'3 87-17566 ISBN 0-201-07981-X This book was typeset in Times Roman and Courier by the authors, using an Autologic APS-5 phototypesetter and a DEC VAX 8550 running the 9th Edition of the UNIX~ operating system. -~- ATs.T Copyright c 1988 by Bell Telephone Laboratories, Incorporated. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopy ing, recording, or otherwise, without the prior written permission of the publisher. Printed in the United States of America. Published simultaneously in Canada. UNIX is a registered trademark of AT&T. DEFGHIJ-AL-898 PREFACE Computer users spend a lot of time doing simple, mechanical data manipula tion - changing the format of data, checking its validity, finding items with some property, adding up numbers, printing reports, and the like. -

Lecture 17 the Shell and Shell Scripting Simple Shell Scripts
Lecture 17 The Shell and Shell Scripting In this lecture • The UNIX shell • Simple Shell Scripts • Shell variables • File System commands, IO commands, IO redirection • Command Line Arguments • Evaluating Expr in Shell • Predicates, operators for testing strings, ints and files • If-then-else in Shell • The for, while and do loop in Shell • Writing Shell scripts • Exercises In this course, we need to be familiar with the "UNIX shell". We use it, whether bash, csh, tcsh, zsh, or other variants, to start and stop processes, control the terminal, and to otherwise interact with the system. Many of you have heard of, or made use of "shell scripting", that is the process of providing instructions to shell in a simple, interpreted programming language . To see what shell we are working on, first SSH into unix.andrew.cmu.edu and type echo $SHELL ---- to see the working shell in SSH We will be writing our shell scripts for this particular shell (csh). The shell scripting language does not fit the classic definition of a useful language. It does not have many of the features such as portability, facilities for resource intensive tasks such as recursion or hashing or sorting. It does not have data structures like arrays and hash tables. It does not have facilities for direct access to hardware or good security features. But in many other ways the language of the shell is very powerful -- it has functions, conditionals, loops. It does not support strong data typing -- it is completely untyped (everything is a string). But, the real power of shell program doesn't come from the language itself, but from the diverse library that it can call upon -- any program.