Nosenko: Five Paths to Judgment RICHARDS J
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

John Mccone and the Assassination of President John F. Kennedy
C061B5413 Approved for Release: 2014/09/29 C06185413 •' •' , S&GRIH'!JNOFORN Death of a President (U) DCI John McCone and the Assassination of President John F. Kennedy David Robarge (U) In recognition ofthe .50th anniversary ofthe assassination ofPresident John F. Kennedy on 22 November 1963, Studies in Intelligence reprints the below, which originally appeared as a chajJter in ChiefHistorian Da\tld Robarge:S bookJohn McCone as Director ofCentral Intelligence, 1961-1?65, published by the Center for the Study ofIntelligence in 200.5. (U) Misconceptions abound regarding CIA~ connection to the assas· sination and its role in subsequent investigations, contributing to the foct that, according to a recent polltalrm by the History Chan· (U) Walter Elder dashed nel, 71 percent ofthe American public still believes that Kennedy's in and cried'' out, 'The del:lth reniltedfrom a conspiracy. president's been shot/' ·(U) Robarge tells a very different story about Cl.A!! immediDte response to the assassination, ils interaction wilh the FBI and War ren Commission, the surprise appearance ofKGB defector Htri Nosenko with troubling information about Lee Harvey Oswald, and DC/ McCone's involvement with later inquiries about Kennedy's '' murder. Nothing in tlie numerous books and articles about the ass~sination that have appeared since the publication ofMcCone has materially changed any ofRobarge~ conclusions. (S) Jolut McCone and Lyman K.irk7 leaving, over hu1th, wanted to talk patrick, the Agency's Executive about the PFIAB meeting with his Director-Comptroller, met with Presi· senior deputies. They were eating in dent's Foreign Intelligence Advisory the French Room, a smaJI space next Boanl (PFIAB) through the morning .to the director•s office, when of22 November 1963. -

British Domestic Security Policy and Communist Subversion: 1945-1964
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Apollo British Domestic Security Policy and Communist Subversion: 1945-1964 William Styles Corpus Christi College, University of Cambridge September 2016 This dissertation is submitted for the degree of Doctor of Philosophy William Styles British Domestic Security Policy and Communist Subversion: 1945-1964 This thesis is concerned with an analysis of British governmental attitudes and responses to communism in the United Kingdom during the early years of the Cold War, from the election of the Attlee government in July 1945 up until the election of the Wilson government in October 1964. Until recently the topic has been difficult to assess accurately, due to the scarcity of available original source material. However, as a result of multiple declassifications of both Cabinet Office and Security Service files over the past five years it is now possible to analyse the subject in greater depth and detail than had been previously feasible. The work is predominantly concerned with four key areas: firstly, why domestic communism continued to be viewed as a significant threat by successive governments – even despite both the ideology’s relatively limited popular support amongst the general public and Whitehall’s realisation that the Communist Party of Great Britain presented little by way of a direct challenge to British political stability. Secondly, how Whitehall’s understanding of the nature and severity of the threat posed by British communism developed between the late 1940s and early ‘60s, from a problem considered mainly of importance only to civil service security practices to one which directly impacted upon the conduct of educational policy and labour relations. -

Historical Dictionary of Russian and Soviet Intelligence
Russia • Military / Security Historical Dictionaries of Intelligence and Counterintelligence, No. 5 PRINGLE At its peak, the KGB (Komitet Gosudarstvennoy Bezopasnosti) was the largest HISTORICAL secret police and espionage organization in the world. It became so influential DICTIONARY OF in Soviet politics that several of its directors moved on to become premiers of the Soviet Union. In fact, Russian president Vladimir V. Putin is a former head of the KGB. The GRU (Glavnoe Razvedvitelnoe Upravleniye) is the principal intelligence unit of the Russian armed forces, having been established in 1920 by Leon Trotsky during the Russian civil war. It was the first subordinate to the KGB, and although the KGB broke up with the dissolution of the Soviet Union in 1991, the GRU remains intact, cohesive, highly efficient, and with far greater resources than its civilian counterparts. & The KGB and GRU are just two of the many Russian and Soviet intelli- gence agencies covered in Historical Dictionary of Russian and Soviet Intelligence. Through a list of acronyms and abbreviations, a chronology, an introductory HISTORICAL DICTIONARY OF essay, a bibliography, and hundreds of cross-referenced dictionary entries, a clear picture of this subject is presented. Entries also cover Russian and Soviet leaders, leading intelligence and security officers, the Lenin and Stalin purges, the gulag, and noted espionage cases. INTELLIGENCE Robert W. Pringle is a former foreign service officer and intelligence analyst RUSSIAN with a lifelong interest in Russian security. He has served as a diplomat and intelligence professional in Africa, the former Soviet Union, and Eastern Europe. For orders and information please contact the publisher && SOVIET Scarecrow Press, Inc. -

S Spies: the Evolution of Spy Units Through Obama Administration
The Pentagon’s Spies: The Evolution of Spy Units through Obama Administration By Jeffrey T. Richelson Region: USA Global Research, July 07, 2015 Theme: Intelligence The National Security Archive 6 July 2015 Washington, D.C. – On April 20, 2012, Secretary of Defense Leon Panetta formally established a new Department of Defense spy organization — the Defense Clandestine Service (DCS). That memo marked yet another in the multiple starts, stops, and reversals in the human intelligence activities of the Department of Defense and the military services. The defense community’s rocky history of involvement with HUMINT includes both war- related and non-war missions, overt and covert programs, conflicts with Congress over the lack of transparency, and inevitable bureaucratic tensions among the uniformed services. Today, the National Security Archive updates its 2001 Electronic BriefingThe Book, Pentagon’s Spies, adding thirty-five new documents that bring the history of military HUMINT activities up to the year 2015. In addition to the Panetta memo (Document 50), this update contains records concerning: The House Permanent Select Committee’s discovery of the existence of the U.S. Army Intelligence Support Activity (Document 8, Document 10) The role of Admiral Bobby Inman in the disestablishment of Task Force 157 (Document 40) Operations of two Air Force human intelligence organizations – the 1127 Field Activities Group and the Air Force Special Activities CenterDocument ( 3a, Document 14a) Defense HUMINT Service activities in operations other than war (Document 30) The work of the Iraq Survey Group (Document 37) Expansion of Army and Air Force HUMINT operations since 2002Document ( 39, Document 41, Document 46, Document 54) The Pentagon’s Spies By Jeffrey T. -

Covert Networks a Comparative Study Of
COVERT NETWORKS A COMPARATIVE STUDY OF INTELLIGENCE TECHNIQUES USED BY FOREIGN INTELLIGENCE AGENCIES TO WEAPONIZE SOCIAL MEDIA by Sarah Ogar A thesis submitted to Johns Hopkins University in conformity with the requirements for the degree of Master of Arts Baltimore, Maryland December 2019 2019 Sarah Ogar All Rights Reserved Abstract From the Bolshevik Revolution to the Brexit Vote, the covert world of intelligence has attempted to influence global events with varying degrees of success. In 2016, one of the most brazen manifestations of Russian intelligence operations was directed against millions of Americans when they voted to elect a new president. Although this was not the first time that Russia attempted to influence an American presidential election, it was undoubtedly the largest attempt in terms of its scope and the most publicized to date. Although much discussion has followed the 2016 election, there have not been much concerted historical analysis which situates the events of 2016 within the global timeline of foreign intelligence collection. This paper argues that the onset of social media has altered intelligence collection in terms of its form, but not in terms of its essence. Using the case study method, this paper illustrates how three different nations apply classical intelligence techniques to the modern environment of social media. This paper examines how China has utilized classical agent recruitment techniques through sites like LinkedIn, how Iran has used classical honey trap techniques through a combination of social media sites, and how Russia has employed the classical tactics of kompromat, forgery, agents of influence and front groups in its modern covert influence campaigns. -
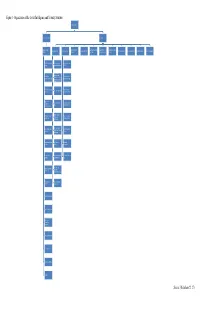
Organization of the Soviet Intelligence and Security Structure Source
Figure 1- Organization of the Soviet Intelligence and Security Structure General Chairman First Deputy Chairman Chief, GRU Deputy Chairman Space Intelligence Operational/ Technical Administrative/ Directorate for Foreign First Deputy Chief Chief of Information Personnel Directorate Political Department Financial Department Eighth Department Archives Department (KGB) Directorate Directorate Technical Directorate Relations First Chief Directorate First Directorate: Seventh Directorate: (Foreign) Europe and Morocco NATO Second Directorate: North and South Second Chief Eighth Directorate: America, Australia, Directorate (Internal) Individual Countries New Zealand, United Kingdom Fifth Chief Directorate Ninth Directorate: Third Directorate: Asia (Dissidents) Military Technology Eighth Chief Fourth Directorate: Tenth Directorate: Directorate Africa Military Economics (Communications) Fifth Directorate: Chief Border Troops Eleventh Directorate: Operational Directorates Doctrine, Weapons Intelligence Sixth Directorate: Third (Armed Forces) Twelfth Directorate: Radio, Radio-Technical Directorate Unknown Intelligence Seventh (Surveillance) First Direction: Institute of Directorate Moscow Information Ninth (Guards) Second Direction: East Information Command Directorate and West Berlin Post Third: National Technical Operations Liberation Directorate Movements, Terrorism Administration Fourth: Operations Directorate from Cuba Personnel Directorate Special Investigations Collation of Operational Experience State Communications Physical Security Registry and Archives Finance Source: (Richelson 22, 27) Figure 2- Organization of the United States Intelligence Community President National Security Advisor National Security DNI State DOD DOJ DHS DOE Treasury Commerce Council Nuclear CIO INR USDI FBI Intelligence Foreign $$ Flow Attachés Weapons Plans DIA NSA NGA NRO Military Services NSB Coast Guard Collection MSIC NGIC (Army) MRSIC (Air Analysis AFMic Force) NCTC J-2's ONI (Navy) CIA Main DIA INSCOM (Army) NCDC MIA (Marine) MIT Source: (Martin-McCormick) . -

Hacks, Leaks and Disruptions | Russian Cyber Strategies
CHAILLOT PAPER Nº 148 — October 2018 Hacks, leaks and disruptions Russian cyber strategies EDITED BY Nicu Popescu and Stanislav Secrieru WITH CONTRIBUTIONS FROM Siim Alatalu, Irina Borogan, Elena Chernenko, Sven Herpig, Oscar Jonsson, Xymena Kurowska, Jarno Limnell, Patryk Pawlak, Piret Pernik, Thomas Reinhold, Anatoly Reshetnikov, Andrei Soldatov and Jean-Baptiste Jeangène Vilmer Chaillot Papers HACKS, LEAKS AND DISRUPTIONS RUSSIAN CYBER STRATEGIES Edited by Nicu Popescu and Stanislav Secrieru CHAILLOT PAPERS October 2018 148 Disclaimer The views expressed in this Chaillot Paper are solely those of the authors and do not necessarily reflect the views of the Institute or of the European Union. European Union Institute for Security Studies Paris Director: Gustav Lindstrom © EU Institute for Security Studies, 2018. Reproduction is authorised, provided prior permission is sought from the Institute and the source is acknowledged, save where otherwise stated. Contents Executive summary 5 Introduction: Russia’s cyber prowess – where, how and what for? 9 Nicu Popescu and Stanislav Secrieru Russia’s cyber posture Russia’s approach to cyber: the best defence is a good offence 15 1 Andrei Soldatov and Irina Borogan Russia’s trolling complex at home and abroad 25 2 Xymena Kurowska and Anatoly Reshetnikov Spotting the bear: credible attribution and Russian 3 operations in cyberspace 33 Sven Herpig and Thomas Reinhold Russia’s cyber diplomacy 43 4 Elena Chernenko Case studies of Russian cyberattacks The early days of cyberattacks: 5 the cases of Estonia, -

The European Union Approach to Disinformation and Misinformation the Case of the 2019 European Parliament Elections
University of Strasbourg European Master’s Degree in Human Rights and Democratisation A.Y. 2018/2019 The European Union approach to disinformation and misinformation The case of the 2019 European Parliament elections Author: Shari Hinds Supervisor: Dr Florence Benoit- Rohmer Abstract In the last years, the phenomenon of so called “fake news” on social media has become more and more discussed, in particular after the 2016 US elections. The thesis examines how the European Union is approaching “fake news” on social media, taking the 2019 European Parliament elections as a case study. This research favours the words “disinformation” and “misinformation”, over “fake news”. It, firstly, explores the different way of spreading disinformation and misinformation and how this can affect our human rights. This thesis will, secondly, focus on the different approaches, remedies and solutions to false information, outlining their limits, in order to recommend to the European Union, the best policies to tackle the phenomenon. The research will, thirdly, focuses on how the European Institutions are currently approaching this issue on social media and the steps that have been taken to protect European citizens from disinformation and misinformation; at this purpose the relevant European policy documents will be analysed. This analysis is necessary to understand the ground of the EU elections. The thesis will conclude with the case study of 2019 European Parliament elections. It will find if there have been cases of disinformation on social media and if the actions taken by the European Union have been enough to protect the second largest elections in the world. Key words: fake news, disinformation, misinformation, co-regulation, Russian disinformation campaigns, European Union, 2019 European Parliament elections. -

Was the CIA Involved in the Assassination of President Kennedy Or the Cover up Conspiracy?
Was the CIA Involved in the Assassination of President Kennedy or the Cover Up Conspiracy? Introduction: For more than ten years there has been much speculation about whether the Central Intelligence Agency played a role in the assassination of President John F. Kennedy. With the Watergate revelations, the testimony of such well known CIA types as Richard Helms, E. Howard Hunt, and James McCord, and with many questions about the CIA's role in the Watergate episode still unanswered, it seems pertinent to once again raise the questions in the title. Was the CIA involved in some way in the conspiracy to assassinate John Kennedy, and was the agency involved in the second conspiracy to cover up the first? Various assassination researchers and writers have, through the ten years, shown substantial evidence that CIA front organizations and former CIA agents were involved in the first conspiracy and that the CIA itself was deeply involved in the cover up conspiracy. (1)(2)(3)(4) Recent revelations and.new evidence has appeared that make the questions worth further exploration. 2 E. Howard Hunt and Mexico City: The most recent revelations concern that compulsive spy, Everette Howard Hunt. Tad Szulc (5) has informed us that Hunt was CIA acting station chief in Mexico City during August and September, 1963. Because of a hole in the known whereabouts of Hunt, as documented by Szulc, we can draw the conclusion that he was still acting station chief in October and November 1963. To the uninitiated this may seem disconnected from the JFK assassina- tion. However, to the researchers who have had access to the statements made by CIA agents Harry Dean, Richard Case Nagell and to FBI reports about CIA agents Ronald Augustinovich and Mary Hope, Hunt's position in Mexico City is very significant. -

Disinformation Campaigns
August 2016 w . c e p a o r g Winning the Information War Techniques and Counter-strategies to Russian Propaganda in Central and Eastern Europe A Report by CEPA’s Information Warfare Project in Partnership with the Legatum Institute Edward Lucas and Peter Pomeranzev I WINNING THE INFORMATION WAR Acknowledgments This report, “Winning the Information War: Techniques and Counter-Strategies in Russian Propaganda,” is produced under the auspices of the Center for European Policy Analysis’ (CEPA) Information Warfare Initiative. Co-authored by CEPA Senior Vice President Edward Lucas and Legatum Institute Senior Fellow Peter Pomerantsev, it is part of an ongoing effort at CEPA to monitor, collate, analyze, rebut and expose Russian propaganda in the countries of Central and Eastern Europe (CEE). Previous publications in this series provided an analytical foundation for evaluating the methods and aims of Russian propaganda. This report extends that research, examining how Russian propaganda is being employed across the CEE region, the perils it presents and actionable counter-strategies for addressing it. In preparing this report, the authors conducted an extended assessment of the existing record of Russian, English and Baltic language literature on the subject of information warfare. They solicited written inputs from, and conducted interviews with, members of the scholarly, academic and expert community who are investigating specific dimensions of Russia’s “new” propaganda. Additionally, the authors solicited written and conceptual inputs through -

Active Measures: Moscow Blends Media/Technology in Information
Warren | 2 Active Measures: Moscow Blends Center for Anticipatory Media/Technology in Information Intelligence Student Warfare to Influence Elections Research Reports Eric Warren December 2019 Executive Summary In its report on Russian active measures campaigns to interfere with the 2016 United States election, the US Senate Select Committee on Intelligence found that the Russian government conducted a comprehensive disinformation campaign against US election infrastructure that started in at least 2014 and carried through to 2017.1 Ensuing reports conclude that Russian active measures, or political warfare designed to influence foreign affairs without reaching the threshold of a hot war, continue to permeate American political discourse.2 Russia’s intent is to influence the outcome of upcoming elections by leveraging, enhancing, and fabricating differences in American society. This poses a serious national security threat.3 While Russian influence in the 2016 US presidential campaign gained wide attention, Russia has a long history of disinformation campaigns targeting US elections, beginning in at least 1919. Over the next century, Russia honed its disinformation tactics, culminating in the manipulation of voters through the use of new media as a way to use America’s “civilization, identity, and will by generating complexity, confusion, and political and social schisms.”4 Russia’s contemporary disinformation efforts to affect internal political debate reaches beyond US borders and strikes within US allies’ and other nations’ boundaries. -

Quiet Heroes Cover.Qxd
UNITED STATES CRYPTOLOGIC HISTORY Series IV World War II Volume 7 The Quiet Heroes of the Southwest Pacific Theater: An Oral History of the Men and Women of CBB and FRUMEL Sharon A. Maneki CENTER FOR CRYPTOLOGIC HISTORY NATIONAL SECURITY AGENCY Reprinted 2007 This monograph is a product of the National Security Agency history program. Its contents and conclusions are those of the author, based on original research, and do not necessarily represent the official views of the National Security Agency. Please address divergent opinion or additional detail to the Center for Cryptologic History (EC). Page ii Table of Contents Foreword . v Preface . vii Acknowledgments . xii An Introduction to the Central Bureau Story . .1 Chapter 1: The Challenge of Reaching Australia . .3 Escaping from the Philippines: A View from the Navy . .3 Escaping from the Philippines: A View from the Army . .5 Traveling from Stateside . .7 Chapter 2: Challenges at Central Bureau Field Sections . .11 Mastering Japanese Intercept . .12 The Paradox of Life at a Field Site . .13 On the Move in New Guinea . .16 An American Perspective on Traffic Analysis . .18 Chapter 3: Cryptanalysts at Work in Central Bureau . .23 The Key to Success Was Teamwork . .25 The Joy of Discovery . .30 Putting Our Cryptanalytic Skills to the Test at Central Bureau 1942-1945 .34 Developing the Clues to Solve the Cryptanalytic Puzzle . .37 Chapter 4: Central Bureau: A Complete Signals Intelligence Agency . .39 The Trials and Tribulations of an IBM Operator . .39 Supporting Central Bureau’s Information Needs . .41 A Central Bureau J-Boy . .42 A Bizarre Experiment .