Codebook (PDF Format)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Intercambio De Información
VIERNES, 21 DE MARZO DE 1958 DIARIO LAS AMERICAS Pág.I 5 "Semana de Panamá'' en Jordán Marsh Nicaragua Regala Comentarios Prominentes Profesores Púnamenos a Miami Estatua Por G. H. P. fl i Mr Visitan Miami con Motivo de las de Rubén Darío El desafortunado reportaje de contento está llegando a la base Bernardo Viera Trejo —en el úl- y la corroe los cimientos de ese Magníficas Exposiciones, de Arte El Dr. René Schick, Ministro de timo número de la revista Bohe- gigante con pies de barro lla- Educación de Nicaragua ha anun- mia— tiene que haber llenado mado comunismo. El Prof. Alejandro Méndez Instituto de Fomento Económi- ciado que su país regalará a la de satisfacción a los "omunis- Pereira, catedrático de la Uni- co a la “Semana de Panamá” lo ciudad de Miami un monumento toides criollos. En sus notas nos versidad de Panama y Director constituyen artículos típicos, fo- de Rubén Darío, la figura literaria pinta a la China comunista como del Museo Nacionat, es el dele- tografías ilustrativas, colecciones más sobresaliente que ha tenido un país próspero y progresista Ratificado Fallo gado oficial del Gobierno y de de maderas panameñas, mapas Nicaragua y uno de los más gran- donde se respetan las religiones la Universidad de Panamá a la de la República y distintos tipos des poetas de habla española. y la justicia alcanza su más alto Para Integración celebración de la Semana de Pa- de Camisillas, traje característi- Dijo el Dr. Schick que se ha en- nivel. A Mao Tse-Tung y a Chou namá, que tiene lugar en Miami, co del interior El Musco Nacio- cargado ala famosa escultora ni- En-Lai los presenta como ange- patrocinada por los prestigiosos nal ha enviado una colección de caragüense, Edilh Gron, la ejecu- litos amarillos con halo y todo. -

Report on Fact-Finding Mission to Lebanon 2 - 18 May 1998
The Danish Immigration Service Ryesgade 53 DK-2100 Copenhagen Ø Phone: + 45 35 36 66 00 Website: www.udlst.dk E-mail: [email protected] Report on fact-finding mission to Lebanon 2 - 18 May 1998 List of contents Introduction 1. Political situation A. General political situation in Lebanon at present Continued Israeli presence Taif agreement and Syrian influence Main political issues and events B. Presence of Syrians C. Main Palestinian organisations in Lebanon and their significance D. Lebanese view of Palestinians at present and in future Official position Views of independent sources Palestinian comments Conditions for Palestinians in Syria and Jordan 2. Security conditions A. General security situation in Lebanon at present, including southern Lebanon Territory under the authorities' control Situation in southern Lebanon Security in the camps B. Palestinians' relationship with Lebanese C. Palestinians' relationship with Syrians D. Inter-Palestinian conflicts 3. Palestinians' legal status A. Residence status Legal basis Types of residence status B. Obtaining of identity papers and travel documents, including renewability etc. Travel documents and laissez-passers C. Naturalisation legislation D. Lebanese legal system E. Law enforcement Crime trends Report on fact-finding mission to Lebanon Syrian authority 4. Social and economic conditions A. General living conditions B. Palestinians' access to and entitlement to take up employment and self-employment Legal basis Actual access to employment Self-employment C. Palestinians' entitlement and access to education and training D. Palestinians' access to housing and right to own property E. Other civil rights and duties for Palestinians F. Freedom of movement for Palestinians 5. UNRWA A. UNRWA's role and activities Health Education Social and emergency aid B. -
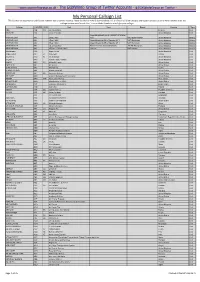
My Personal Callsign List This List Was Not Designed for Publication However Due to Several Requests I Have Decided to Make It Downloadable
- www.egxwinfogroup.co.uk - The EGXWinfo Group of Twitter Accounts - @EGXWinfoGroup on Twitter - My Personal Callsign List This list was not designed for publication however due to several requests I have decided to make it downloadable. It is a mixture of listed callsigns and logged callsigns so some have numbers after the callsign as they were heard. Use CTL+F in Adobe Reader to search for your callsign Callsign ICAO/PRI IATA Unit Type Based Country Type ABG AAB W9 Abelag Aviation Belgium Civil ARMYAIR AAC Army Air Corps United Kingdom Civil AgustaWestland Lynx AH.9A/AW159 Wildcat ARMYAIR 200# AAC 2Regt | AAC AH.1 AAC Middle Wallop United Kingdom Military ARMYAIR 300# AAC 3Regt | AAC AgustaWestland AH-64 Apache AH.1 RAF Wattisham United Kingdom Military ARMYAIR 400# AAC 4Regt | AAC AgustaWestland AH-64 Apache AH.1 RAF Wattisham United Kingdom Military ARMYAIR 500# AAC 5Regt AAC/RAF Britten-Norman Islander/Defender JHCFS Aldergrove United Kingdom Military ARMYAIR 600# AAC 657Sqn | JSFAW | AAC Various RAF Odiham United Kingdom Military Ambassador AAD Mann Air Ltd United Kingdom Civil AIGLE AZUR AAF ZI Aigle Azur France Civil ATLANTIC AAG KI Air Atlantique United Kingdom Civil ATLANTIC AAG Atlantic Flight Training United Kingdom Civil ALOHA AAH KH Aloha Air Cargo United States Civil BOREALIS AAI Air Aurora United States Civil ALFA SUDAN AAJ Alfa Airlines Sudan Civil ALASKA ISLAND AAK Alaska Island Air United States Civil AMERICAN AAL AA American Airlines United States Civil AM CORP AAM Aviation Management Corporation United States Civil -

Airline Schedules
Airline Schedules This finding aid was produced using ArchivesSpace on January 08, 2019. English (eng) Describing Archives: A Content Standard Special Collections and Archives Division, History of Aviation Archives. 3020 Waterview Pkwy SP2 Suite 11.206 Richardson, Texas 75080 [email protected]. URL: https://www.utdallas.edu/library/special-collections-and-archives/ Airline Schedules Table of Contents Summary Information .................................................................................................................................... 3 Scope and Content ......................................................................................................................................... 3 Series Description .......................................................................................................................................... 4 Administrative Information ............................................................................................................................ 4 Related Materials ........................................................................................................................................... 5 Controlled Access Headings .......................................................................................................................... 5 Collection Inventory ....................................................................................................................................... 6 - Page 2 - Airline Schedules Summary Information Repository: -

Ba'ath Propaganda During the Iran-Iraq War Jennie Matuschak [email protected]
Bucknell University Bucknell Digital Commons Honors Theses Student Theses Spring 2019 Nationalism and Multi-Dimensional Identities: Ba'ath Propaganda During the Iran-Iraq War Jennie Matuschak [email protected] Follow this and additional works at: https://digitalcommons.bucknell.edu/honors_theses Part of the International Relations Commons, and the Near and Middle Eastern Studies Commons Recommended Citation Matuschak, Jennie, "Nationalism and Multi-Dimensional Identities: Ba'ath Propaganda During the Iran-Iraq War" (2019). Honors Theses. 486. https://digitalcommons.bucknell.edu/honors_theses/486 This Honors Thesis is brought to you for free and open access by the Student Theses at Bucknell Digital Commons. It has been accepted for inclusion in Honors Theses by an authorized administrator of Bucknell Digital Commons. For more information, please contact [email protected]. iii Acknowledgments My first thanks is to my advisor, Mehmet Döşemeci. Without taking your class my freshman year, I probably would not have become a history major, which has changed my outlook on the world. Time will tell whether this is good or bad, but for now I am appreciative of your guidance. Also, thank you to my second advisor, Beeta Baghoolizadeh, who dealt with draft after draft and provided my thesis with the critiques it needed to stand strongly on its own. Thank you to my friends for your support and loyalty over the past four years, which have pushed me to become the best version of myself. Most importantly, I value the distractions when I needed a break from hanging out with Saddam. Special shout-out to Andrew Raisner for painstakingly reading and editing everything I’ve written, starting from my proposal all the way to the final piece. -

The Making of a Leftist Milieu: Anti-Colonialism, Anti-Fascism, and the Political Engagement of Intellectuals in Mandate Lebanon, 1920- 1948
THE MAKING OF A LEFTIST MILIEU: ANTI-COLONIALISM, ANTI-FASCISM, AND THE POLITICAL ENGAGEMENT OF INTELLECTUALS IN MANDATE LEBANON, 1920- 1948. A dissertation presented By Sana Tannoury Karam to The Department of History In partial fulfillment of the requirements for the degree of Doctor of Philosophy In the field of History Northeastern University Boston, Massachusetts December 2017 1 THE MAKING OF A LEFTIST MILIEU: ANTI-COLONIALISM, ANTI-FASCISM, AND THE POLITICAL ENGAGEMENT OF INTELLECTUALS IN MANDATE LEBANON, 1920- 1948. A dissertation presented By Sana Tannoury Karam ABSTRACT OF DISSERTATION Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in History in the College of Social Sciences and Humanities of Northeastern University December 2017 2 This dissertation is an intellectual and cultural history of an invisible generation of leftists that were active in Lebanon, and more generally in the Levant, between the years 1920 and 1948. It chronicles the foundation and development of this intellectual milieu within the political Left, and how intellectuals interpreted leftist principles and struggled to maintain a fluid, ideologically non-rigid space, in which they incorporated an array of ideas and affinities, and formulated their own distinct worldviews. More broadly, this study is concerned with how intellectuals in the post-World War One period engaged with the political sphere and negotiated their presence within new structures of power. It explains the social, political, as well as personal contexts that prompted intellectuals embrace certain ideas. Using periodicals, personal papers, memoirs, and collections of primary material produced by this milieu, this dissertation argues that leftist intellectuals pushed to politicize the role and figure of the ‘intellectual’. -

Acta De Consejo No. 08-13 2013
COOPERATIVA DE TRABAJADORES DE AVIANCA “COOPAVA” CONSEJO DE ADMINISTRACIÓN- REUNIÓN ORDINARIA ACTA N° 08/13 FECHA: SEPTIEMBRE 5 DE 2013 HORA: 12:30 P.M. LUGAR: HOTEL HABITEL – AV ELDORADO N° 100-97- BOGOTA D.C. Solicitudes de reingreso aprobadas: El Comité da su visto bueno a las 206 solicitudes de reingreso a continuación relacionadas: NOMBRE REGISTRO Y LOCALIZACIÓN 1 AHUMADA VALBUENA JUAN CAMILO 01-16015 AVIANCA 2 ALCAZAR CANTARIS SANTIAGO 01-1009123 AVIANCA 3 ALVAREZ GUTIERREZ MILTON ALVAREZ 01-1039805 AVIANCA 4 AMAYA MORA GINA ALEJANDRA 01-1027905 AVIANCA 5 ARANGO BURGOS BRONLY ALEJANDRO 01-43992 AVIANCA 6 ATEHORTUA SANDOVAL RUBEN 01-80090473 AVIANCA 7 BALLESTEROS BABATIVA LUZ DARY 01-75504 AVIANCA 8 BERNAL MUÑOZ HANNIA LUCIA 01-1018120 AVIANCA 9 BERNAL DIAZ MARISOL 01-52029686 AVIANCA 10 BERNAL SANTOS CAMILA 01-1050725 AVIANCA 11 BUSTOS GOMEZ ADELA 01-139893 AVIANCA 12 CARTAGENA LOZANO AMPARO 01-1044215 AVIANCA 13 CHAPARRO BECERRA NORMA LISSET 01-1040181 AVIANCA 14 CHARRIS GOMEZ ALFONSO 01-215014 AVIANCA 15 CRUZ ANGULO JAIME ALBERTO 01-244368 AVIANCA 16 DELGADO VELEZ MILADYS 01-1022585 AVIANCA 17 ESCOBAR REYES ADRIANA PAOLA 01-1043460 AVIANCA 18 ESTEVES RODRIGUEZ JUAN CARLOS 01-326728 AVIANCA 19 GALEANO CIFUENTES CAROLINA 01-360065 AVIANCA 20 GALLEGO MARTINEZ JAMILTON 01-1006721 AVIANCA 21 GARCES VEGA ALVARO JOSE 01-1028804 AVIANCA 22 GARZON ORTIZ ANA MARIA 01-385011 AVIANCA 23 GOMEZ GONZALEZ ROSA STELLA 01-397692 AVIANCA 24 GOMEZ QUIMBAY KATHERINE JOHANNA 01-1042303 AVIANCA 25 GOMEZ GARZON JOHANA JULIETE 01-398355 AVIANCA 26 GUALDRON -

June 17, 1949 Untitled Note Concerning a Secret Memo Distributed by the Central Committee of the Lebanese Communist Party
Digital Archive digitalarchive.wilsoncenter.org International History Declassified June 17, 1949 Untitled note concerning a secret memo distributed by the Central Committee of the Lebanese Communist Party Citation: “Untitled note concerning a secret memo distributed by the Central Committee of the Lebanese Communist Party,” June 17, 1949, History and Public Policy Program Digital Archive, Emir Farid Chehab Collection, GB165-0384, Box 1, File 157/1, Middle East Centre Archive, St Antony’s College, Oxford. https://digitalarchive.wilsoncenter.org/document/119854 Summary: On the eve of the 50th anniversary of Syrian and Lebanese Communist independence, a secret memo is distributed by the Lebanese Community Party defining the role of the Regional Secretary. Credits: This document was made possible with support from Youmna and Tony Asseily. Original Language: Arabic Contents: English Translation Scan of Original Document 1/157 Beirut, Jun 17, 1949 Number 85/ The communists are preparing to celebrate the fifth anniversary of the independence of the Syrian and Lebanese Communist Parties with the strengthening of their branches in the regional specific committees by finding strong elements as supervisory secretaries for these committees. I have come across the text of a secret memo distributed by the central committee of the Lebanese Communist Party entitled; (The role of the Regional Secretary) that included the following: “We remind you that article 19 of the Party bylaws [page 2] states that “ The Regional Committee consults the Central Committee regarding the candidacy of the Regional Secretary.” If the party conference votes on this bylaw; that means that this matter has become insignificant and the Regional Secretary is a fighter with great responsibility, on whom party action is great dependent. -

Vea Un Ejemplo
3 To search aircraft in the registration index, go to page 178 Operator Page Operator Page Operator Page Operator Page 10 Tanker Air Carrier 8 Air Georgian 20 Amapola Flyg 32 Belavia 45 21 Air 8 Air Ghana 20 Amaszonas 32 Bering Air 45 2Excel Aviation 8 Air Greenland 20 Amaszonas Uruguay 32 Berjaya Air 45 748 Air Services 8 Air Guilin 20 AMC 32 Berkut Air 45 9 Air 8 Air Hamburg 21 Amelia 33 Berry Aviation 45 Abu Dhabi Aviation 8 Air Hong Kong 21 American Airlines 33 Bestfly 45 ABX Air 8 Air Horizont 21 American Jet 35 BH Air - Balkan Holidays 46 ACE Belgium Freighters 8 Air Iceland Connect 21 Ameriflight 35 Bhutan Airlines 46 Acropolis Aviation 8 Air India 21 Amerijet International 35 Bid Air Cargo 46 ACT Airlines 8 Air India Express 21 AMS Airlines 35 Biman Bangladesh 46 ADI Aerodynamics 9 Air India Regional 22 ANA Wings 35 Binter Canarias 46 Aegean Airlines 9 Air Inuit 22 AnadoluJet 36 Blue Air 46 Aer Lingus 9 Air KBZ 22 Anda Air 36 Blue Bird Airways 46 AerCaribe 9 Air Kenya 22 Andes Lineas Aereas 36 Blue Bird Aviation 46 Aereo Calafia 9 Air Kiribati 22 Angkasa Pura Logistics 36 Blue Dart Aviation 46 Aero Caribbean 9 Air Leap 22 Animawings 36 Blue Islands 47 Aero Flite 9 Air Libya 22 Apex Air 36 Blue Panorama Airlines 47 Aero K 9 Air Macau 22 Arab Wings 36 Blue Ridge Aero Services 47 Aero Mongolia 10 Air Madagascar 22 ARAMCO 36 Bluebird Nordic 47 Aero Transporte 10 Air Malta 23 Ariana Afghan Airlines 36 Boliviana de Aviacion 47 AeroContractors 10 Air Mandalay 23 Arik Air 36 BRA Braathens Regional 47 Aeroflot 10 Air Marshall Islands 23 -

Nicaragua: a Society in Transition
Rochester Institute of Technology RIT Scholar Works Theses 6-1-1982 Nicaragua: a society in transition James Mason Stillings Follow this and additional works at: https://scholarworks.rit.edu/theses Recommended Citation Stillings, James Mason, "Nicaragua: a society in transition" (1982). Thesis. Rochester Institute of Technology. Accessed from This Thesis is brought to you for free and open access by RIT Scholar Works. It has been accepted for inclusion in Theses by an authorized administrator of RIT Scholar Works. For more information, please contact [email protected]. IIICARAGUA, A $OCIllTY III TRAIISrMolI llul>mltt«lln PartW ,.llm..... of tI,. ~IN ...... t... '110 Doct'M lIIASTER OP PINE ARTII lIIFA P~OTOORAPHY PROGRAIlt SCltOOL OP PHOTOGRAPIlIC ARTS AIID SCIBIICF1I IlOCHESTIR lNlI'lTMJT8 OP TOOKIIOLOOY ItOCIIE9TIIt, 11811 YOItK lUlIllgn Gunther Gartwlighl Gunt1>or Cor'"ric!", Cholrpo.-. An'''''' Prot..... -.of__""'"""....... """ S<:l_ Paul A. Miller Poul A.lIIl1lor ~,- ColI..ot Gonorl>l Sh.mo, Il1l' Charles C. WertleIig chiilil C. Il'orhiiii A_lot... f>n>f_ ~ of 1'fIot...."""le .....10 """..,1_ I, lom.. Ill"""" StiUInp, ......". v-n' POt...I."" to'ho R.~T. WaUa<o Momorlol ~ito"'1'0 ~o,., lhMIo, "Illo..._, .. _I, .. T_lJon,' 10 ~holo or It> POt'....., tollfOd\l<U"" ...UI ""I be for "",.,....otol _ or pt<>flt. Jamos Mason Stillings onn ~o,... Mooon StlllJ,. " In dedication . To Mother and Father for their constant love, support, belief in my abilities, and inspiration by their fine examples, and to Margy for her generous patience, -

Empresas De Trabajos Aéreos Especiales Certificadas
EMPRESAS DE TRABAJOS AÉREOS ESPECIALES CERTIFICADAS NO. CERT. RAZON SOCIAL VIGENTE CANCELADO CDO-AA- 01 FUMIVILLA LTDA. FUMIGACIONES AEREAS DE VILLANUEVA X CDO-AA- 02 SERVICIOS AEROAGRICOLAS DEL LLANO S.A.S SADELL S.A.S X CDO-AA- 03 FADELCE LTDA. FUMIGACIONES AEREAS DEL CESAR X CDO-AA- 04 AMA LTDA. AVIONES Y MAQUINARIAS AGRICOLAS X CDO-AA- 05 SFA LTDA. SERVICIO DE FUMIGACION AEREA DEL CASANARE X CDO-AA- 06 COMERCIALIZADORA ECO LTDA. X CDO-AA- 07 FUMICOL S.A. FUMIGACIONES AEREAS DE COLOMBIA, ANTES LTDA. X CDO-AA- 08 SERVICIO AÉREO ORIENTE (SAO) X CDO-AA- 09 AEROPENORT X CDO-AA- 10 AEROTEC LTDA. ASPERSIONES TECNICAS DEL CAMPO X CDO-AA- 11 FAGAN S. EN C." FUMIGACION AEREA LOS GAVANES X CDO-AA- 12 SERVICIOS AÉREOS AGRICOLAS DE CASANARE (SAAC) X CDO-AA- 13 AERO SANIDAD AGRICOLA S. EN C. "ASA LTDA." X CDO-AA- 14 AEROSERVICIOS MAJAGUAL "ASEM LTDA" X CDO-AA- 15 FARI LTDA. FUMIGACIONES AEREAS DEL ARIARI X CDO-AA- 16 FUMIGARAY S.A. SERVICIOS DE FUMIGACION AEREA GARAY ANTES, LTDA. X CDO-AA- 17 AVIOCESAR SAS AMBULANCIA AEREA X CDO-AA- 18 QUIMBAYA EXPLORACION Y RECURSS GEOMETRICOS X CDO-AA- 19 TAES X CDO-AA- 20 COMPAÑÍA COLOMBIANA DE AEROSERVICIOS X CDO-AA- 21 COMPAÑÍA AEROAGRICOLA DE GIRARDOT "AGIL" X CDO-AA- 22 COMPAÑÍA AEROEXPRESS (AEROFOTOGRAFIA) X CDO-AA- 23 AMBULANCIAS AÉREAS DE COLOMBIA LTDA X CDO-AA- 24 GLOBAL SERVICE AVIATION ESA X CDO-AA- 25 RIOSUR - AMBULANCIA X CDO-AA- 26 AVIONES PUBLICITARIOS DE COLOMBIA S.AS AERIAL SIGN X CDO-AA- 27 MEDICALFLY S.A.S X CDO-AA- 28 FUNDACION CARDIOVASCULAR X CDO-AA- 29 TECNIAEREAS DE COLOMBIA SAS X CDO-AA- 30 SOLAIR AMBULANCIA X CDO-AA- 31 COLCHARTER X CDO-AA- 32 SERVICIOS AEREOS ESPECIALES SAE - GLOBAL LIFE AMBULANCIAS X CDO-AA- 33 ISATECH CORPORATION AEROFOTOGRAFIA X CDO-AA- 34 GOODFLY CO SAS AMBULANCIA AEREA X CDO-AA- 35 SOCIEDAD AEROAGRICOLA DE AMBALEMA SAMBA X CDO-AA- 36 MG MEDICAL GROUP X CDO-AA- 37 LANS X CDO-AA- 38 COMPAÑÍA AEROAGRICOLA INTEGRAL SAS - CAAISA X CDO-AA- 39 CELTA LTDA. -

Analysis of Platforms in Lebanon's 2018 Parliamentary Election
ا rلeمtركnزe اCل لبeنsانneي aلbلeدرLا eساThت LCPS for Policy Studies r e p a 9 Analysis of Platforms 1 P 0 2 y a y M in Lebanon's 2018 c i l o Parliamentary Election P Nizar Hassan Founded in 1989, the Lebanese Center for Policy Studies is a Beirut-based independent, non-partisan think tank whose mission is to produce and advocate policies that improve good governance in fields such as oil and gas, economic development, public finance, and decentralization. Copyright© 2019 The Lebanese Center for Policy Studies Designed by Polypod Executed by Dolly Harouny Sadat Tower, Tenth Floor P.O.B 55-215, Leon Street, Ras Beirut, Lebanon T: + 961 1 79 93 01 F: + 961 1 79 93 02 [email protected] www.lcps-lebanon.org Analysis of Platforms in Lebanon's 2018 Parliamentary Election 1 1 Nizar Hassan The author would like to thank Sami Nizar Hassan is a former researcher at the Lebanese Center for Policy Studies. He Atallah, John McCabe, and Georgia Dagher for their contributions to this paper. holds an M.Sc. in Labour, Social Movements and Development from the School of Oriental and African Studies, University of London. At LCPS, his work focused on Lebanese political parties and movements and their policy platforms. His master’s research examined protest movements in Lebanon and he currently researches political behavior in the districts of Chouf and Aley. Nizar co-hosts ‘The Lebanese Politics Podcast’, and his previous work has included news reporting and non-profit project management. 2 LCPS Policy Paper Introduction Prior to the May 2018 Lebanese Parliamentary Election, a majority of 2 2 political parties and emerging political groups launched electoral Henceforth referred to as 'emerging platforms outlining their political and socioeconomic goals and means groups'.