The Asterisk Handbook Version 2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Jupyter Reference Guide
– 1 – Nicholas Bowman, Sonja Johnson-Yu, Kylie Jue Handout #15 CS 106AP August 5, 2019 Jupyter Reference Guide This handout goes over the basics of Jupyter notebooks, including how to install Jupyter, launch a notebook, and run its cells. Jupyter notebooks are a common tool used across different disciplines for exploring and displaying data, and they also make great interactive explanatory tools. Installing Jupyter To install Jupyter, run the following command inside your Terminal (replace python3 with py if you’re using a Windows device): $ python3 -m pip install jupyter Launching a notebook A Jupyter notebook is a file that ends in the extension .ipynb, which stands for “interactive Python notebook.” To launch a Python notebook after you’ve installed Jupyter, you should first navigate to the directory where your notebook is located (you’ll be there by default if you’re using the PyCharm terminal inside a project). Then run the following command inside your Terminal (if this doesn’t work, see the “Troubleshooting” section below): $ jupyter notebook This should open a window in your browser (Chrome, Firefox, Safari, Edge, etc.) that looks like Figure 1. Jupyter shows the files inside the current directory and allows you to click on any Python notebook files within that folder. Figure 1: After running the jupyter notebook command, you should see a window that lists the Python notebooks inside the current directory from which you ran the command. The picture above shows the Lecture 25 directory. – 2 – To launch a particular notebook, click on its file name. This should open a new tab with the notebook. -

How the Past Affects the Future: the Story of the Apostrophe1
HOW THE PAST AFFECTS THE FUTURE: THE STORY OF THE APOSTROPHE1 Christina Cavella and Robin A. Kernodle I. Introduction The apostrophe, a punctuation mark which “floats above the line, symbolizing something missing in the text” (Battistella, 1999, p. 109), has been called “an unstable feature of written English” (Gasque, 1997, p. 203), “the step-child of English orthography” (Barfoot, 1991, p. 121), and “an entirely insecure orthographic squiggle” (Barfoot, 1991, p. 133). Surely the apostrophe intends no harm; why then the controversy and apparent emotionalism surrounding it? One major motivation for investigating the apostrophe is simply because it is so often misused. A portion of the usage problem can perhaps be attributed to the chasm dividing spoken and written language, as the apostrophe was originally intended to indicate missing letters, which may or may not have actually been enunciated. To understand what has been called “the aberrant apostrophe,” (Crystal, 1995, p. 203) and the uncertainty surrounding its usage, an examination of its history is essential, for it is this “long and confused” (Crystal, 1995, p. 203) history that is partially responsible for the modern-day misuses of the apostrophe. This paper will trace the history of the apostrophe, examining the purpose(s) for which the apostrophe has been utilized in the past as well as presenting its current use. An overview of contemporary rules of usage is then included, along with specific examples of apostrophe misuse and a recommendation on how to teach apostrophe usage to non- native speakers of English. Finally, an attempt is made to predict the apostrophe’s future. -

Trademarks 10 Things You Should Know to Protect Your Product and Business Names
Trademarks 10 things you should know to protect your product and business names 1. What is a trademark? A trademark is a brand name for a product. It can be a word, phrase, logo, design, or virtually anything that is used to identify the source of the product and distinguish it from competitors’ products. More than one trademark may be used in connection with a product; for example, COCA-COLA® and DIET COKE® are both trademarks for beverages. A trademark represents the goodwill and reputation of a product and its source. Its owner has the right to prevent others from trading on that goodwill by using the same or a similar trademark on the same or similar products in a way that is likely to cause confusion as to the source, origin, or sponsorship of the products. A service mark is like a trademark, except it is used to identify and distinguish services rather than products. For example, the “golden arches” mark shown below is a service mark for restaurant services. The terms “trademark” and “mark” are often used interchangeably to refer to either a trademark or service mark. 2. How should a mark be used? Trademarks must be used properly to maintain their value. Marks should be used as adjectives, but not as nouns or verbs. 4 | knobbe.com For example, when referring to utilizing the FACEBOOK® website, do not say that you “Facebooked” or that you were “Facebooking.” To prevent loss of trademark or service mark rights, the generic name for the product should appear after the mark, and the mark should appear visually different from the surrounding text. -

List of Approved Special Characters
List of Approved Special Characters The following list represents the Graduate Division's approved character list for display of dissertation titles in the Hooding Booklet. Please note these characters will not display when your dissertation is published on ProQuest's site. To insert a special character, simply hold the ALT key on your keyboard and enter in the corresponding code. This is only for entering in a special character for your title or your name. The abstract section has different requirements. See abstract for more details. Special Character Alt+ Description 0032 Space ! 0033 Exclamation mark '" 0034 Double quotes (or speech marks) # 0035 Number $ 0036 Dollar % 0037 Procenttecken & 0038 Ampersand '' 0039 Single quote ( 0040 Open parenthesis (or open bracket) ) 0041 Close parenthesis (or close bracket) * 0042 Asterisk + 0043 Plus , 0044 Comma ‐ 0045 Hyphen . 0046 Period, dot or full stop / 0047 Slash or divide 0 0048 Zero 1 0049 One 2 0050 Two 3 0051 Three 4 0052 Four 5 0053 Five 6 0054 Six 7 0055 Seven 8 0056 Eight 9 0057 Nine : 0058 Colon ; 0059 Semicolon < 0060 Less than (or open angled bracket) = 0061 Equals > 0062 Greater than (or close angled bracket) ? 0063 Question mark @ 0064 At symbol A 0065 Uppercase A B 0066 Uppercase B C 0067 Uppercase C D 0068 Uppercase D E 0069 Uppercase E List of Approved Special Characters F 0070 Uppercase F G 0071 Uppercase G H 0072 Uppercase H I 0073 Uppercase I J 0074 Uppercase J K 0075 Uppercase K L 0076 Uppercase L M 0077 Uppercase M N 0078 Uppercase N O 0079 Uppercase O P 0080 Uppercase -

Beginner's Guide to Asterisk
Getting Started With Open Source Telephony A Beginners Guide to Asterisk Steve Sokol Asterisk Marketing Lead, Digium Justin Hester Lead Asterisk Technical Instructor, Digium Agenda • Summary of Asterisk • Basics and Distributions • Resources • Asterisk is a toolkit • Distros are more complete • Training classes package with GUI • Digium and Asterisk • Getting started using Asterisk • AstriCon 2016 • Architecture - Linux + Asterisk • Difference between CLI and GUI • Versioning Getting Started with Asterisk Getting Started with Asterisk • Find it • Install it • Configure it What is Asterisk? An Open Source Communications Platform • Software, written in C, that you put on an ordinary operating system—transforming that system into a communications engine. Software – A communications platform A system through which communications flow, from one endpoint to another. What is Asterisk - Platform Open Source Communications Platform Software - Extensible Architecture A simple core with only a few responsibilities Module Management Reading Configuration CORE System Timing CORE Channel Management Software – Modular Architecture Modules app_dial.so • Use the native modules • Use Asterisk’s APIs to control and extend Asterisk – AMI, AGI, and ARI Preparing for Asterisk – Set up a host machine • Old physical hardware – Laptop, rackmount or tower system • Virtual machine – e.g. VirtualBox (on your Mac, Windows or Linux laptop!) www.virtualbox.org • Cloud server – e.g. www.digitalocean.com or aws.amazon.com Finding Asterisk – Choose your path ‘Source’ or ‘Plain Vanilla’ AsteriskNOW, a PBX ‘distro’. www.asterisk.org/downloads Choosing Asterisk - Source • Install a Linux operating system • Set up networking • Configure software repositories • Install Asterisk dependencies • Download and install Asterisk, DAHDI, LibPRI from provided scripts. And you will have an unconfigured, pristine, ready to configure “Asterisk Configuration Framework”. -

Appraisal Institute Trademark Usage Manual
Trademark Usage Manual for Appraisal Institute Copyright © 2020 Appraisal Institute. All rights reserved. Printed in the United States of America. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopy, recording or otherwise, without the prior written consent of the publisher. TRADEMARK USAGE MANUAL FOR APPRAISAL INSTITUTE Table of Contents I. Introduction 1 II. Trademarks, Service Marks, Collective Service Marks and Collective Membership Marks 1 III. Trade Names are Different from Trademarks 2 IV. Proper Trademark Usage 3 A. Always Use Trademarks as Proper Adjectives ............................................................................... 3 B. Make the Trademark Stand Out .................................................................................................... 3 C. Only One Trademark Should Appear on the Same Label or Name Plate ....................................... 4 D. Use of Appraisal Institute Trademarks ........................................................................................... 4 1. Signature Requirements and Restrictions ................................................................................ 4 2. Membership Designation Requirements and Restrictions ........................................................ 5 3. Proper Use of Letter Designations ........................................................................................... 5 4. Emblem Requirements and Restrictions ................................................................................. -
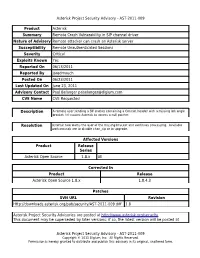
AST-2011-009 Product Asterisk Summary Remote Crash Vulnerability in SIP Channel Driver Natu
Asterisk Project Security Advisory - AST-2011-009 Product Asterisk Summary Remote Crash Vulnerability in SIP channel driver Nature of Advisory Remote attacker can crash an Asterisk server Susceptibility Remote Unauthenticated Sessions Severity Critical Exploits Known Yes Reported On 06/13/2011 Reported By jaredmauch Posted On 06/23/2011 Last Updated On June 23, 2011 Advisory Contact Paul Belanger [email protected] CVE Name CVE Requested Description A remote user sending a SIP packet containing a Contact header with a missing left angle bracket (<) causes Asterisk to access a null pointer. Resolution Asterisk now warns the user of the missing bracket and continues processing. Available workarounds are to disable chan_sip or to upgrade. Affected Versions Product Release Series Asterisk Open Source 1.8.x All Corrected In Product Release Asterisk Open Source 1.8.x 1.8.4.3 Patches SVN URL Revision Http://downloads.asterisk.org/pub/security/AST-2011-009.diff 1.8 Asterisk Project Security Advisories are posted at http://www.asterisk.org/security This document may be superseded by later versions; if so, the latest version will be posted at Asterisk Project Security Advisory - AST-2011-009 Copyright © 2011 Digium, Inc. All Rights Reserved. Permission is hereby granted to distribute and publish this advisory in its original, unaltered form. Asterisk Project Security Advisory - AST-2011-009 http://downloads.digium.com/pub/security/AST-2011-009.pdf and http://downloads.digium.com/pub/security/AST-2011-009.html Revision History Date Editor Revisions Made 06/20/2011 Kinsey Moore Initial Release Asterisk Project Security Advisory - AST-2011-009 Copyright © 2011 Digium, Inc. -

Common Intellectual Property Abbreviations and Symbols
www.oliveandolive.com 500 Memorial Street • Post Office Box 2049 • Durham, NC 27702-2049 I Phone (919)683-5514 • Fax (919)683-3781 COMMON INTELLECTUAL PROPERTY ABBREVIATIONS AND INTELLECTUAL PROPERTY SYMBOLS: The Meaning of Abbreviations and Symbols for Patents, Trademarks, Copyrights, Mask Works, and Designs Abbreviation or Meaning Symbol Patent or Pat. Indicates an invention protected by an issued United States patent. A proper patent notice contains one of these listed terms, followed by the patent number. Sometimes the letters “U.S.” are added before one of the terms, and sometimes the abbreviation “No.” or “Number” are used after one of the terms, but they are not required. The notice should appear either on the protected article or, if that is not possible, on a label affixed to it or to its packaging. For more information about patents, refer to our Learning Center article on Patents. Patent Pending or An application has been filed seeking to protect some aspect of the Pat. Pending marked invention. This designation does not mean a patent has issued. It may never issue. Reg. U.S. Pat. & Indicates a mark which has been registered with the United States TM Office or Patent & Trademark Office. The owner of such a mark has greater protection than do owners of unregistered marks. For more ® information about trademarks, refer to our Learning Center article on Trademarks, and our short article on appropriate trademark use. SM SM or Stands for “service mark” and means that someone is claiming the adjacent word or symbol as their trademark to identify the services, such as restaurant services, which they are offering. -

VOICE OVER IP with ASTERISK 11 Postgresql-Based CDR and Saw Multiple Entries of the Same Toll-Free Number
ASTERISK IS A SOFTWARE-BASED PBX that runs under Linux, *BSDs, and Mac OS X. HEISON CHAK It can also be used as a VoIP gateway and can provide a bridge to the PSTN (Public Switched Telephone Network, a.k.a. Plain Old Telephone Service). IAX (Inter-Asterisk voice over IP eXchange), pronounced “eeks,” is a protocol with Asterisk used by Asterisk as an alternative to SIP, H.323, etc., when connecting to other VoIP Heison Chak is a system and network administrator devices that support IAX. at SOMA Networks. He focuses on network manage- ment and performance analysis of data and voice networks. Heison has been an active member of the Asterisk community since 2003 and will be deliver- This article describes some of the interesting things I ing a tutorial on VoIP Principles and Practice at the have done using Asterisk and VoIP, told as the story of USENIX ’05 Annual Technical Conference. a business trip from my home in Toronto. [email protected] It was 12:15 in the morning and I had just gotten home from work. Realizing that I had not yet packed for my trip to San Francisco, I was a little worried about missing my early morning flight. I knew that snooze alarms no longer worked for me; I would often keep hitting the snooze button when the alarm went off, or I would just be so used to the sound that I wouldn’t even hear it at all. Either way, I could wind up being late. The AGI (Asterisk Gateway Interface) script I had installed on my Asterisk box that serves wake-up calls solved both my problems with snooze alarms. -

Sangoma Trademark Policy the Trademarks ASTERISK
Sangoma Trademark Policy The trademarks ASTERISK, ASTERISKNOW, ASTRICON, DAHDI, DIVA, DIGIUM, FREEPBX, DAHDI, SANGOMA, SWITCHVOX, WANPIPE, and other Sangoma trademarks signal quality, dependability, and the cutting edge, especially to those familiar with IP telephony. Sangoma Technologies Corp. and its subsidiaries (collectively, “Sangoma”) as the owner of these trademarks and others, takes the value of these marks seriously. This Trademark Policy (the “Policy”) explains the basic circumstances in which Sangoma may consent to the use by others of the trademarks owned by Sangoma. It also sets out the limitations and conditions that we expect every person to abide by when using any of the marks of Sangoma. All use of any of the trademarks in any way in connection with VoIP and VoIP-related goods or services (whether in a domain name, URL, path, advertising, tag line, website, on products or packaging, or otherwise) must comply with this policy. We encourage communication to prevent misunderstanding. If you have any questions or comments, please contact [email protected] . General Sangoma takes its trademark rights seriously. You may be aware that certain software of Sangoma, such as Asterisk and FreePBX, is distributed under the GPL as “open source” software. While this means we have consented to certain distribution of this software under our copyright rights, the GPL does not negate our ability to control our trademark rights. The issues addressed by copyright and trademark are separate. Although you may distribute and modify certain of our software under the GPL, this Policy outlines Sangoma’s restrictions on use of our trademarks in connection with those modifications and distributions. -

Asterisk Vs Switchvox Explained
Asterisk® versus Switchvox® Sangoma is the developer and primary sponsor of Commercial Switchvox the Asterisk project. As a free open-source platform, Unified Communications Asterisk transforms a standard computer into a powerful Solution or Asterisk communications and collaboration server. open-source platform— Switchvox, another product from Sangoma, is a turn-key How do you decide Unified Communications solution (or IP PBX), built upon which is right for you? Asterisk, that includes powerful telephony features at a fraction of the price of competitive products on the market. Switchvox is available as a traditional on-premise appliance or hosted as Switchvox Cloud. Asterisk is the platform that enables developers Low-level engines like Asterisk and to initiate, maintain, Apache are extremely powerful precisely and manipulate calls because they have no fixed function or between phones and specific purpose set by their creators. other telephony devices. The functions to which they are ultimately applied are determined not by the creators (the developers of the Asterisk and Apache development teams) but by Asterisk is built by and for communication systems application developers. developers. The open source project began in 1999 when Mark Spencer released the original Asterisk source Application developers take engine- code and began accepting submissions from a growing level components like Asterisk and community of users. The resulting product is an engine that Apache and build on top of them. These handles all of the low-level details of initiating, maintaining, developers craft purpose-built solutions and manipulating real-time media streams (calls) between that implement a specific set of functions. endpoints (phones). -

List of Symbols
Appendix A List of Symbols For convenience, many symbols frequently used in the text are listed below alphabetically. Some of the symbols may play a dual role, in which case the meaning should be obvious from the context. A number in parentheses refers to an Eq. number (or the text or footnote near that Eq. number) in which the symbol is defined or appears for the first time; in a few cases a page number, Table number, Sect. number, footnote (fn.) number, or Fig. number is given instead. Quantum number is abbreviated as q. n. Quantum numbers (atomic): Symbol Description Eq. No. j D l ˙ s Inner q. n. of an electron (3.13) J D L C S Inner (total angular momentum) q. n. of a state (5.51b) l P Azimuthal (orbital) q. n. of an electron (3.1) and (3.2) L D l Azimuthal (orbital) q. n. of a state (5.51c) ml Magnetic orbital q. n. of an electron (3.1) ms Magnetic spin q. n. of an electron (3.1) M Total magnetic q. n. (5.51d) n Principal q. n. of an electron (3.1) s P Spin q. n. of an electron (3.13) S D s Spin q. n. of a state (5.51e) Relativistic azimuthal q. n. of an electron (3.15a) and (3.15b) Relativistic magnetic q. n. of an electron (3.18a) and (3.18b) W.F. Huebner and W.D. Barfield, Opacity, Astrophysics and Space Science Library 402, 457 DOI 10.1007/978-1-4614-8797-5, © Springer Science+Business Media New York 2014 458 Appendix A: List of Symbols Quantum numbers (molecular)1: Symbol Description Eq.