Common Intellectual Property Abbreviations and Symbols
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Jupyter Reference Guide
– 1 – Nicholas Bowman, Sonja Johnson-Yu, Kylie Jue Handout #15 CS 106AP August 5, 2019 Jupyter Reference Guide This handout goes over the basics of Jupyter notebooks, including how to install Jupyter, launch a notebook, and run its cells. Jupyter notebooks are a common tool used across different disciplines for exploring and displaying data, and they also make great interactive explanatory tools. Installing Jupyter To install Jupyter, run the following command inside your Terminal (replace python3 with py if you’re using a Windows device): $ python3 -m pip install jupyter Launching a notebook A Jupyter notebook is a file that ends in the extension .ipynb, which stands for “interactive Python notebook.” To launch a Python notebook after you’ve installed Jupyter, you should first navigate to the directory where your notebook is located (you’ll be there by default if you’re using the PyCharm terminal inside a project). Then run the following command inside your Terminal (if this doesn’t work, see the “Troubleshooting” section below): $ jupyter notebook This should open a window in your browser (Chrome, Firefox, Safari, Edge, etc.) that looks like Figure 1. Jupyter shows the files inside the current directory and allows you to click on any Python notebook files within that folder. Figure 1: After running the jupyter notebook command, you should see a window that lists the Python notebooks inside the current directory from which you ran the command. The picture above shows the Lecture 25 directory. – 2 – To launch a particular notebook, click on its file name. This should open a new tab with the notebook. -

Circular 1 Copyright Basics
CIRCULAR 1 Copyright Basics Copyright is a form of protection Copyright is a form of protection provided by the laws of the provided by U.S. law to authors of United States to the authors of “original works of authorship” that are fixed in a tangible form of expression. An original “original works of authorship” from work of authorship is a work that is independently created by the time the works are created in a a human author and possesses at least some minimal degree of creativity. A work is “fixed” when it is captured (either fixed form. This circular provides an by or under the authority of an author) in a sufficiently overview of basic facts about copyright permanent medium such that the work can be perceived, and copyright registration with the reproduced, or communicated for more than a short time. Copyright protection in the United States exists automatically U.S. Copyright Office. It covers from the moment the original work of authorship is fixed.1 • Works eligible for protection • Rights of copyright owners What Works Are Protected? • Who can claim copyright • Duration of copyright Examples of copyrightable works include • Literary works • Musical works, including any accompanying words • Dramatic works, including any accompanying music • Pantomimes and choreographic works • Pictorial, graphic, and sculptural works • Motion pictures and other audiovisual works • Sound recordings, which are works that result from the fixation of a series of musical, spoken, or other sounds • Architectural works These categories should be viewed broadly for the purpose of registering your work. For example, computer programs and certain “compilations” can be registered as “literary works”; maps and technical drawings can be registered as “pictorial, graphic, and sculptural works.” w copyright.gov note: Before 1978, federal copyright was generally secured by publishing a work with an appro- priate copyright notice. -

How the Past Affects the Future: the Story of the Apostrophe1
HOW THE PAST AFFECTS THE FUTURE: THE STORY OF THE APOSTROPHE1 Christina Cavella and Robin A. Kernodle I. Introduction The apostrophe, a punctuation mark which “floats above the line, symbolizing something missing in the text” (Battistella, 1999, p. 109), has been called “an unstable feature of written English” (Gasque, 1997, p. 203), “the step-child of English orthography” (Barfoot, 1991, p. 121), and “an entirely insecure orthographic squiggle” (Barfoot, 1991, p. 133). Surely the apostrophe intends no harm; why then the controversy and apparent emotionalism surrounding it? One major motivation for investigating the apostrophe is simply because it is so often misused. A portion of the usage problem can perhaps be attributed to the chasm dividing spoken and written language, as the apostrophe was originally intended to indicate missing letters, which may or may not have actually been enunciated. To understand what has been called “the aberrant apostrophe,” (Crystal, 1995, p. 203) and the uncertainty surrounding its usage, an examination of its history is essential, for it is this “long and confused” (Crystal, 1995, p. 203) history that is partially responsible for the modern-day misuses of the apostrophe. This paper will trace the history of the apostrophe, examining the purpose(s) for which the apostrophe has been utilized in the past as well as presenting its current use. An overview of contemporary rules of usage is then included, along with specific examples of apostrophe misuse and a recommendation on how to teach apostrophe usage to non- native speakers of English. Finally, an attempt is made to predict the apostrophe’s future. -

Trademarks 10 Things You Should Know to Protect Your Product and Business Names
Trademarks 10 things you should know to protect your product and business names 1. What is a trademark? A trademark is a brand name for a product. It can be a word, phrase, logo, design, or virtually anything that is used to identify the source of the product and distinguish it from competitors’ products. More than one trademark may be used in connection with a product; for example, COCA-COLA® and DIET COKE® are both trademarks for beverages. A trademark represents the goodwill and reputation of a product and its source. Its owner has the right to prevent others from trading on that goodwill by using the same or a similar trademark on the same or similar products in a way that is likely to cause confusion as to the source, origin, or sponsorship of the products. A service mark is like a trademark, except it is used to identify and distinguish services rather than products. For example, the “golden arches” mark shown below is a service mark for restaurant services. The terms “trademark” and “mark” are often used interchangeably to refer to either a trademark or service mark. 2. How should a mark be used? Trademarks must be used properly to maintain their value. Marks should be used as adjectives, but not as nouns or verbs. 4 | knobbe.com For example, when referring to utilizing the FACEBOOK® website, do not say that you “Facebooked” or that you were “Facebooking.” To prevent loss of trademark or service mark rights, the generic name for the product should appear after the mark, and the mark should appear visually different from the surrounding text. -

Embedding a Copyright Into an Image One of the Main Concerns About Putting Images on the Web, Is the Theft of Those Images
Embedding A Copyright Into An Image One of the main concerns about putting images on the web, is the theft of those images. Putting your name in text on the image will not guarantee the safety of the image. The healing brush can easily remove text from an image. Photoshop offers a number of ways to embed your personal and copyright information in your image files. There is a bit of extra work involved in the copyright process and sometimes it can be visually intrusive. But, if the image is important to you, the time is worth it. There is also a more powerful option available via a plugin that is less visually intru- sive. This option is available though the Digimarc plugin which when chosen, takes you to the their web site. You can read more about it by going to http://www.digimarc. com. There is a yearly fee for using this option based on the number of images and options selected. Add Copyright Information to File Info 1. Open an image. 2. In the File menu, choose File Info... The File Info dialogue box appears. 3. Fill in all important information. Embedding TitleA Copyright goes here Into An Image Use a Font Copyright Symbol 1. Select the Type Tool. 2. In the Tools Option bar set options to: Helvetica Bold 500 pts - 3. Click the Type Palette icon if the Type Palette is not already open. 4. Use the option +g keys (mac), or Alt+g keys (windows) to type a copyright symbol 5. Move into position. -

Copyrights Quick Reference Series
Copyrights Quick Reference Series Designing a t-shirt? Showing a movie on campus? Creating a website? For these things and more it is important to understand the laws and rules surrounding copyrighted material. Check out the information below to understand how copyright affects your student org. Copyright Material In the United States Code, Title 17, Section 107 of the Copyright Law allows for the “fair use” of a copyrighted work for purposes such as criticism, comment, news reporting, teaching, scholarship, or research. The Fair Use Doctrine allows for limited use of copyrighted materials without obtaining permission from the copyright holder, but the limitations are significant. The factors to be considered in determining if the copying is fair use are: The purpose and character of the use (education is more likely to be fair use and use that causes the work to be used for a new purpose is more likely to be fair use) The nature of the copyrighted work (a fact-based work is more likely to be fair use than a creative fictional work) The amount and substantiality of the copied portion compared to the work as a whole (a small portion and/or not copying the “best” portion(s) of the work is more likely to be fair use) The effect of the use on the potential market (copying that does not cause someone to not buy the whole work is more likely to be fair use) Copyright and Trademark Symbols © is the copyright symbol and signifies a creator’s exclusive rights to publish, reproduce, or sell an original work. -

List of Approved Special Characters
List of Approved Special Characters The following list represents the Graduate Division's approved character list for display of dissertation titles in the Hooding Booklet. Please note these characters will not display when your dissertation is published on ProQuest's site. To insert a special character, simply hold the ALT key on your keyboard and enter in the corresponding code. This is only for entering in a special character for your title or your name. The abstract section has different requirements. See abstract for more details. Special Character Alt+ Description 0032 Space ! 0033 Exclamation mark '" 0034 Double quotes (or speech marks) # 0035 Number $ 0036 Dollar % 0037 Procenttecken & 0038 Ampersand '' 0039 Single quote ( 0040 Open parenthesis (or open bracket) ) 0041 Close parenthesis (or close bracket) * 0042 Asterisk + 0043 Plus , 0044 Comma ‐ 0045 Hyphen . 0046 Period, dot or full stop / 0047 Slash or divide 0 0048 Zero 1 0049 One 2 0050 Two 3 0051 Three 4 0052 Four 5 0053 Five 6 0054 Six 7 0055 Seven 8 0056 Eight 9 0057 Nine : 0058 Colon ; 0059 Semicolon < 0060 Less than (or open angled bracket) = 0061 Equals > 0062 Greater than (or close angled bracket) ? 0063 Question mark @ 0064 At symbol A 0065 Uppercase A B 0066 Uppercase B C 0067 Uppercase C D 0068 Uppercase D E 0069 Uppercase E List of Approved Special Characters F 0070 Uppercase F G 0071 Uppercase G H 0072 Uppercase H I 0073 Uppercase I J 0074 Uppercase J K 0075 Uppercase K L 0076 Uppercase L M 0077 Uppercase M N 0078 Uppercase N O 0079 Uppercase O P 0080 Uppercase -

Use of Copyrighted/Trademarked Materials in 4-H Fair Exhibits And
For Staff and Judges Use of COPYRIGHTED/TRADEMARKED Material In 4-H Fair Exhibits and Activities What does copyright mean?????? A copyright and/or a trademark are legal methods used by artists, photographers, writers, and others to protect their original and creative works. Protected items may range from professional photography and books to music, sport logo insignias, corporate and brand name logos to art designs. It is important to remember the idea itself cannot receive a copyright. The expression of an idea is what is copyrighted. For example, one cannot copyright "bears", but specific bears like Winnie-the-Pooh and Smoky Bear cannot be copied without permission. As an educational agency, 4-H has the responsibility to prepare materials that help program participants learn about proper use of copyright and trademark regulations. Copyright means complete or portions of materials cannot be reproduced without permission and proper crediting of the source. It is not possible to address all situations that may occur; however, the following information will provide some background for making decisions and determining appropriate actions. Proper crediting of source includes name of book, magazine, newspaper, etc., author/artist/ publisher (which ever is most logical), date of publication, page number. If 4-H’ers lack some of the documentation when exhibiting, judges should use the situation as a teachable moment, remembering this is meant to be a learning experience not a policing experience. It is the responsibility of individual 4-H’ers to be aware of copyright/trademark regulations when developing 4-H exhibits and communication activities for county and state fairs. -

Beginner's Guide to Asterisk
Getting Started With Open Source Telephony A Beginners Guide to Asterisk Steve Sokol Asterisk Marketing Lead, Digium Justin Hester Lead Asterisk Technical Instructor, Digium Agenda • Summary of Asterisk • Basics and Distributions • Resources • Asterisk is a toolkit • Distros are more complete • Training classes package with GUI • Digium and Asterisk • Getting started using Asterisk • AstriCon 2016 • Architecture - Linux + Asterisk • Difference between CLI and GUI • Versioning Getting Started with Asterisk Getting Started with Asterisk • Find it • Install it • Configure it What is Asterisk? An Open Source Communications Platform • Software, written in C, that you put on an ordinary operating system—transforming that system into a communications engine. Software – A communications platform A system through which communications flow, from one endpoint to another. What is Asterisk - Platform Open Source Communications Platform Software - Extensible Architecture A simple core with only a few responsibilities Module Management Reading Configuration CORE System Timing CORE Channel Management Software – Modular Architecture Modules app_dial.so • Use the native modules • Use Asterisk’s APIs to control and extend Asterisk – AMI, AGI, and ARI Preparing for Asterisk – Set up a host machine • Old physical hardware – Laptop, rackmount or tower system • Virtual machine – e.g. VirtualBox (on your Mac, Windows or Linux laptop!) www.virtualbox.org • Cloud server – e.g. www.digitalocean.com or aws.amazon.com Finding Asterisk – Choose your path ‘Source’ or ‘Plain Vanilla’ AsteriskNOW, a PBX ‘distro’. www.asterisk.org/downloads Choosing Asterisk - Source • Install a Linux operating system • Set up networking • Configure software repositories • Install Asterisk dependencies • Download and install Asterisk, DAHDI, LibPRI from provided scripts. And you will have an unconfigured, pristine, ready to configure “Asterisk Configuration Framework”. -

Appraisal Institute Trademark Usage Manual
Trademark Usage Manual for Appraisal Institute Copyright © 2020 Appraisal Institute. All rights reserved. Printed in the United States of America. No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, electronic, mechanical, photocopy, recording or otherwise, without the prior written consent of the publisher. TRADEMARK USAGE MANUAL FOR APPRAISAL INSTITUTE Table of Contents I. Introduction 1 II. Trademarks, Service Marks, Collective Service Marks and Collective Membership Marks 1 III. Trade Names are Different from Trademarks 2 IV. Proper Trademark Usage 3 A. Always Use Trademarks as Proper Adjectives ............................................................................... 3 B. Make the Trademark Stand Out .................................................................................................... 3 C. Only One Trademark Should Appear on the Same Label or Name Plate ....................................... 4 D. Use of Appraisal Institute Trademarks ........................................................................................... 4 1. Signature Requirements and Restrictions ................................................................................ 4 2. Membership Designation Requirements and Restrictions ........................................................ 5 3. Proper Use of Letter Designations ........................................................................................... 5 4. Emblem Requirements and Restrictions ................................................................................. -

Microsoft Word Top Ten Tips
Microsoft Word Top Ten Tips 1. Normal/defaults 2. Quick Access Toolbar 3. AutoCorrect 4. Section symbol 5. AutoText/Quick Part Gallery 6. Insert Text from File 7. Suppress page number 8. Converting documents 9. Reveal Formatting 10. Resources Administrative Office Created by Lois McLeod, AO-DTS-SDSO-TD of the U.S. Courts June 2016 Normal/defaults To set the default font: 1. Launch the Font dialog box. 2. Choose the desired Font and Size. 3. Click Set As Default. 4. Click All documents based on the Normal.dotm template? and click OK. 2 #2 Quick Access Toolbar The Quick Access Toolbar (QAT) begins with only three tools: Save, Undo, and Redo. Here are two ways to add tools: 1. Click the More button ( ) at the right end of the QAT and select any listed tool desired. Click More Commands at the bottom of the QAT drop-down list to access All Commands and/or to rearrange the order of the tools on the QAT. 2. Right-click any tool on any ribbon and select Add to Quick Access Toolbar. 3 #3 AutoCorrect AutoCorrect enables you to create “abbreviations” for often-used text and/or corrections to incorrectly typed text. 1. On the File tab, click Options. 2. Click the Proofing tab. 3. Click AutoCorrect Options. 4. Click the AutoCorrect tab. 5. In the Replace box, enter the abbreviation (or misspelled/mistyped word to be corrected automatically). 6. In the With box, enter the replacement text. 7. Click Add. 8. To close the dialog boxes, click OK twice. As the abbreviation or incorrect form of the word is typed (followed by pressing the Spacebar, Tab or Enter), it is automatically replaced with the expanded version or correct spelling. -
AST-2011-009 Product Asterisk Summary Remote Crash Vulnerability in SIP Channel Driver Natu
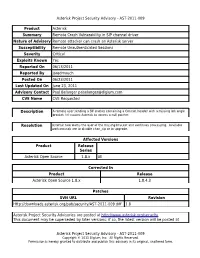
Asterisk Project Security Advisory - AST-2011-009 Product Asterisk Summary Remote Crash Vulnerability in SIP channel driver Nature of Advisory Remote attacker can crash an Asterisk server Susceptibility Remote Unauthenticated Sessions Severity Critical Exploits Known Yes Reported On 06/13/2011 Reported By jaredmauch Posted On 06/23/2011 Last Updated On June 23, 2011 Advisory Contact Paul Belanger [email protected] CVE Name CVE Requested Description A remote user sending a SIP packet containing a Contact header with a missing left angle bracket (<) causes Asterisk to access a null pointer. Resolution Asterisk now warns the user of the missing bracket and continues processing. Available workarounds are to disable chan_sip or to upgrade. Affected Versions Product Release Series Asterisk Open Source 1.8.x All Corrected In Product Release Asterisk Open Source 1.8.x 1.8.4.3 Patches SVN URL Revision Http://downloads.asterisk.org/pub/security/AST-2011-009.diff 1.8 Asterisk Project Security Advisories are posted at http://www.asterisk.org/security This document may be superseded by later versions; if so, the latest version will be posted at Asterisk Project Security Advisory - AST-2011-009 Copyright © 2011 Digium, Inc. All Rights Reserved. Permission is hereby granted to distribute and publish this advisory in its original, unaltered form. Asterisk Project Security Advisory - AST-2011-009 http://downloads.digium.com/pub/security/AST-2011-009.pdf and http://downloads.digium.com/pub/security/AST-2011-009.html Revision History Date Editor Revisions Made 06/20/2011 Kinsey Moore Initial Release Asterisk Project Security Advisory - AST-2011-009 Copyright © 2011 Digium, Inc.