Asterisk™: the Definitive Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Jupyter Reference Guide
– 1 – Nicholas Bowman, Sonja Johnson-Yu, Kylie Jue Handout #15 CS 106AP August 5, 2019 Jupyter Reference Guide This handout goes over the basics of Jupyter notebooks, including how to install Jupyter, launch a notebook, and run its cells. Jupyter notebooks are a common tool used across different disciplines for exploring and displaying data, and they also make great interactive explanatory tools. Installing Jupyter To install Jupyter, run the following command inside your Terminal (replace python3 with py if you’re using a Windows device): $ python3 -m pip install jupyter Launching a notebook A Jupyter notebook is a file that ends in the extension .ipynb, which stands for “interactive Python notebook.” To launch a Python notebook after you’ve installed Jupyter, you should first navigate to the directory where your notebook is located (you’ll be there by default if you’re using the PyCharm terminal inside a project). Then run the following command inside your Terminal (if this doesn’t work, see the “Troubleshooting” section below): $ jupyter notebook This should open a window in your browser (Chrome, Firefox, Safari, Edge, etc.) that looks like Figure 1. Jupyter shows the files inside the current directory and allows you to click on any Python notebook files within that folder. Figure 1: After running the jupyter notebook command, you should see a window that lists the Python notebooks inside the current directory from which you ran the command. The picture above shows the Lecture 25 directory. – 2 – To launch a particular notebook, click on its file name. This should open a new tab with the notebook. -

Skype for Asterisk™ Administrator Manual
Skype for Asterisk™ Administrator Manual 601-00017 Rev. B2 Digium, Inc. 445 Jan Davis Drive NW Huntsville, AL 35806 United States Main Number: 1.256.428.6000 Tech Support: 1.256.428.6161 U.S. Toll Free: 1.877.344.4861 Sales: 1.256.428.6262 www.asterisk.org www.digium.com www.asterisknow.org © Digium®, Inc. 2010 All rights reserved. No part of this publication may be copied, distributed, transmitted, transcribed, stored in a retrieval system, or translated into any human or computer language without the prior written permission of Digium, Inc. Digium, Inc. has made every effort to ensure that the instructions contained in this document are adequate and error free. The manufacturer will, if necessary, explain issues that may not be covered by this documentation. The manufacturer’s liability for any errors in the documents is limited to the correction of errors and the aforementioned advisory services. This document has been prepared for use by professional and properly trained personnel, and the customer assumes full responsibility when using it. Adobe and Acrobat are registered trademarks, and Acrobat Reader is a trademark of Adobe Systems Incorporated. Asterisk, Digium, Switchvox, and AsteriskNOW are registered trademarks and Asterisk Business Edition, AsteriskGUI, and Asterisk Appliance are trademarks of Digium, Inc. Any other trademarks mentioned in the document are the property of their respective owners. Digium, Inc. Page 2 TABLE OF CONTENTS Chapter 1: Overview.................................................................................................................6 -

The Origins of the Underline As Visual Representation of the Hyperlink on the Web: a Case Study in Skeuomorphism
The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Romano, John J. 2016. The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism. Master's thesis, Harvard Extension School. Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:33797379 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Other Posted Material, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#LAA The Origins of the Underline as Visual Representation of the Hyperlink on the Web: A Case Study in Skeuomorphism John J Romano A Thesis in the Field of Visual Arts for the Degree of Master of Liberal Arts in Extension Studies Harvard University November 2016 Abstract This thesis investigates the process by which the underline came to be used as the default signifier of hyperlinks on the World Wide Web. Created in 1990 by Tim Berners- Lee, the web quickly became the most used hypertext system in the world, and most browsers default to indicating hyperlinks with an underline. To answer the question of why the underline was chosen over competing demarcation techniques, the thesis applies the methods of history of technology and sociology of technology. Before the invention of the web, the underline–also known as the vinculum–was used in many contexts in writing systems; collecting entities together to form a whole and ascribing additional meaning to the content. -

A Framework for Real-Time Communications
Anton is a leading experts on Real Time Anton Venema Communications solutions, and the 1 Chief Technology Officer visionary lead architect behind IceLink, WebSync and LiveSwitch. iRTC Internet-Based Real Time Communications Introduction What’s the first thought that comes into your mind when you think about real-time communications? Is it a phone call you had a few minutes ago? A text message sent to your mobile? Maybe something more modern, like a tweet or video broadcast? All of these fall under the umbrella of what we like to call Internet-based real time communications, or iRTC for short. Real-time communications have been a part of our lives for a long time. From public telephone networks to radios all the way back to the telegraph, humanity has a history of seeking out new and better ways to use technology to improve communication. In the past decade, technology has arguably advanced more than the past century before it. Smartphones have stormed the market, mobile processors are advancing in line with Moore’s law, LTE rollouts are delivering unprecedented Internet speeds across the world, and WiFi hotspots are becoming ubiquitous. iRTC Includes Many Applications The availability of high-speed Internet services just about everywhere is causing a fundamental shift in the way people want to communicate and consume media. Cable networks are finding it more difficult to distinguish between their Internet and TV services, especially when companies like Netflix and HBO are able to publish their content directly to consumers over the Internet. Even live broadcasts, TV’s last stronghold, are being slowly replaced as platforms like YouTube allow content to be broadcast live to millions of users simultaneously over the Internet. -

Edit Bibliographic Records
OCLC Connexion Browser Guides Edit Bibliographic Records Last updated: May 2014 6565 Kilgour Place, Dublin, OH 43017-3395 www.oclc.org Revision History Date Section title Description of changes May 2014 All Updated information on how to open the diacritic window. The shortcut key is no longer available. May 2006 1. Edit record: basics Minor updates. 5. Insert diacritics Revised to update list of bar syntax character codes to reflect and special changes in character names and to add newly supported characters characters. November 2006 1. Edit record: basics Minor updates. 2. Editing Added information on guided editing for fields 541 and 583, techniques, template commonly used when cataloging archival materials. view December 2006 1. Edit record: basics Updated to add information about display of WorldCat records that contain non-Latin scripts.. May 2007 4. Validate record Revised to document change in default validation level from None to Structure. February 2012 2 Editing techniques, Series added entry fields 800, 810, 811, 830 can now be used to template view insert data from a “cited” record for a related series item. Removed “and DDC” from Control All commands. DDC numbers are no longer controlled in Connexion. April 2012 2. Editing New section on how to use the prototype OCLC Classify service. techniques, template view September 2012 All Removed all references to Pathfinder. February 2013 All Removed all references to Heritage Printed Book. April 2013 All Removed all references to Chinese Name Authority © 2014 OCLC Online Computer Library Center, Inc. 6565 Kilgour Place Dublin, OH 43017-3395 USA The following OCLC product, service and business names are trademarks or service marks of OCLC, Inc.: CatExpress, Connexion, DDC, Dewey, Dewey Decimal Classification, OCLC, WorldCat, WorldCat Resource Sharing and “The world’s libraries. -
Learning Aid-Common Commas
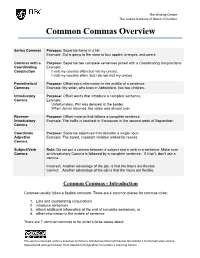
The Writing Centre The Justice Institute of British Columbia Common Commas Overview Series Commas Purpose: Separate items in a list Example: Sid is going to the store to buy apples, oranges, and pears. Commas with a Purpose: Separate two complete sentences joined with a Coordinating Conjunctions Coordinating Example: Conjunction I visit my cousins often but not my uncles. I visit my cousins often, but I do not visit my uncles. Parenthetical Purpose: Offset extra information in the middle of a sentence Commas Example: My sister, who lives in Abbotsford, has two children. Introductory Purpose: Offset words that introduce a complete sentence. Comma Example: Unfortunately, Phil was delayed at the border. When Jamar returned, the video was almost over. Reverse- Purpose: Offset material that follows a complete sentence. Introductory Example: The traffic is heaviest in Vancouver in the second week of September. Comma Coordinate Purpose: Separate adjectives that describe a single noun. Adjective Example: The bored, impatient children waited for recess. Comma Subject/Verb Rule: Do not put a comma between a subject and a verb in a sentence. Make sure Comma an Introductory Comma is followed by a complete sentence. If it isn’t, don’t use a comma. Incorrect: Another advantage of the job, is that the hours are flexible. Correct: Another advantage of the job is that the hours are flexible. Common Commas - Introduction Commas usually follow a flexible structure. There are 4 common places for commas to be: 1. Lists and coordinating conjunctions 2. introduce sentences 3. attach additional information at the end of complete sentences, or 4. -

FOSDEM 2017 Schedule
FOSDEM 2017 - Saturday 2017-02-04 (1/9) Janson K.1.105 (La H.2215 (Ferrer) H.1301 (Cornil) H.1302 (Depage) H.1308 (Rolin) H.1309 (Van Rijn) H.2111 H.2213 H.2214 H.3227 H.3228 Fontaine)… 09:30 Welcome to FOSDEM 2017 09:45 10:00 Kubernetes on the road to GIFEE 10:15 10:30 Welcome to the Legal Python Winding Itself MySQL & Friends Opening Intro to Graph … Around Datacubes Devroom databases Free/open source Portability of containers software and drones Optimizing MySQL across diverse HPC 10:45 without SQL or touching resources with my.cnf Singularity Welcome! 11:00 Software Heritage The Veripeditus AR Let's talk about The State of OpenJDK MSS - Software for The birth of HPC Cuba Game Framework hardware: The POWER Make your Corporate planning research Applying profilers to of open. CLA easy to use, aircraft missions MySQL Using graph databases please! 11:15 in popular open source CMSs 11:30 Jockeying the Jigsaw The power of duck Instrumenting plugins Optimized and Mixed License FOSS typing and linear for Performance reproducible HPC Projects algrebra Schema Software deployment 11:45 Incremental Graph Queries with 12:00 CloudABI LoRaWAN for exploring Open J9 - The Next Free It's time for datetime Reproducible HPC openCypher the Internet of Things Java VM sysbench 1.0: teaching Software Installation on an old dog new tricks Cray Systems with EasyBuild 12:15 Making License 12:30 Compliance Easy: Step Diagnosing Issues in Webpush notifications Putting Your Jobs Under Twitter Streaming by Open Source Step. Java Apps using for Kinto Introducing gh-ost the Microscope using Graph with Gephi Thermostat and OGRT Byteman. -

Openfire Service Level Agreement
Service Level Agreement Technical Services — Communications Service University Technology Services 1. Overview This Service Level Agreement (SLA) is between University Technology Services (UTS) and either departments or groups choosing to utilize the internal Oakland University instant messaging (OUIM) service. The OUIM service is currently referenced by talk.oakland.edu and runs XMPP/Jabber software called Openfire. Under this SLA, UTS agrees to provide specific information technology (IT) services. This SLA also covers performance and reliability targets and objectives. Section 7 requires the signature and contact information of the group coordinator as an agreement to the SLA. OUIM is an online service that is available on campus and off campus. The requirements to utilize the service are a NetID, an XMPP client, and an Internet connection. XMPP clients are available online. The UTS Helpdesk supports the XMPP clients Spark, Pidgin, and Adium. Instructions are available on the UTS Web site at http://www.oakland.edu/?id=13849&sid=70. 2. Purpose The purpose of this SLA is to establish a cooperative partnership between UTS staff members with the community of customers who may opt into its use by clarifying roles, setting expectations, and providing service objectives and limitations. 3. Terms of Agreement This service is provided on an ongoing basis. From time to time, it may be reviewed and modified by UTS. Modifications to this agreement will be done at the sole discretion of UTS and the Technical Support and Services team (TSS). 4. Service Hours Regularly scheduled maintenance will be scheduled during low-use hours as much as possible; such work will be done either before 8:00 A.M. -

Sangoma T116 16-Span T1/E1/J1 Tapping Board
Sangoma T116 16-Span T1/E1/J1 Tapping Board Dedicated tapping solution for up to 8 two-way connections or 16 one-way connections. The T116 Tapping Card is part of Sangoma’s family of Advanced Flexible Telecommunications hardware product line — it uses the same high-performance PCI Express interface that is providing superior performance in critical systems all over the world. The T116 supports the passive tapping of up to 240 voice calls using up to 16 T1, E1 or J1 spans. With Sangoma cards, you can take advantage of hardware and software improvements, as soon as they become available. The T116, like all cards in Sangoma’s AFT family, is eld upgradable with unbreakable rmware. Choose the T116 to collect call control information, telecom protocol information and voice/media. T116 Card Features Sixteen receive-only spans with Supports Robbed Bit Channel optimum PCI-Express interface Associated Signaling (CAS) and ISDN enables tapping of sixteen one-way PRI or eight two-way conversation T1/E1 and fractional T1/E1, multiple Support for Asterisk®, Yate®, and channel HDLC per line for mixed 5 Year warranty on parts and labor FreeSWITCH® PBX/IVR Projects, as data/TDM voice applications well as other open source and Supports the passive tapping of up proprietary PBX, Switch, IVR, or VoIP WANPIPE® routing stack is to 240 voice calls using up to 16 gateway applications completely independent of TDM T1, E1 or J1 spans voice application for total system Optimized per channel DMA streams reliability and hardware-level HDLC handling Field -

Voip Tutorial
VoIP and FreeBSD The daemon meets the phone May 15th, 2008 University of Ottawa, , Ottawa, Canada Massimiliano Stucchi [email protected] May 16th, 2007, Agenda • Introduction • Terms • Introduction to Asterisk key concepts • Let's connect to a provider • What's a dialplan ? • How cool is an IVR... • (if time permits) AGI overview 2 Who am I ? • First of all, good morning • I’m Max, nice to meet you all • I worked on VoIP and FreeBSD for the last 3,5 years implementing technologies for businesses large and small • I’m now working at BrianTel Srl, delivering voice services over geographical Wi-Fi Networks (more on this @ other talk) Why am I doing this ? • VoIP is business, but you have to know how to deal with it (and have right equipment) • It's not rocket science, but it's a totally different environment for computer professionals • I have some deal of experience • I don't feel the need to keep others from doing what I do 1000's miles away • It's fun ! Let’s start • A few questions to let me understand the level of knowledge of the class • If you have any question further on, raise your hand at any time any time TERMS Terms 1/5 • Direct Inward Dial • It's a real PSTN number which lets the call into your VoIP system. • Normally works on a PRI DID • It's normally intended as a phone number • Can be bought from many different providers and forwarded to your asterisk box via any provider Terms 2/5 • Voice Circuit (may carry data as well) • Can carry either 24 (T1) or 30 (E1) b- channels (audio) and 1 d-channel (for data communication across peers). -

BSA Brand Guidelines Real-World Examples 97 Introduction
Boy Scouts of America Brand Guidelines BSALast Brand revised Guidelines July 2019 Table of Contents Corporate Brand Scouting Sub-Brands Digital Guidelines Scouting Architecture 6 Scouts BSA 32 Guiding Principles 44 WEBSITES 69 Prepared. For Life.® 7 Position and Identity 33 Web Policies 45 Information Architecture 70 Vision and Mission 8 Cub Scouting 34 TYPOGRAPHY 46 Responsive Design 71 Brand Position, Personality, and Communication Elements 9 Position and Identity 35 Typefaces for Digital Projects 47 Forms 72 Corporate Trademark 10 Venturing 36 Hierarchy 48 Required Elements 73 Corporate Signature 11 Position and Identity 37 Best Practices 49 Real-World Examples 74 The Activity Graphic 12 Sea Scouting 38 Typography Pitfalls 50 MOBILE 75 Prepared. For Life.® Trademark 13 Position and Identity 39 DIGITAL COLOR PALETTES 51 Interface Design 76 Preparados para el futuro.® 14 Primary Boy Scouts of America Colors 52 Using Icons in Apps 77 BSA Extensions Trademark and Logo Protection 15 Secondary Boy Scouts of America Colors 53 Mobile Best Practices 78 BSA Extensions Brand Positioning BSA Corporate Fonts 17 41 Cub Scouting 54 Resources 79 Council, Group, Department, and Team Designation PHOTOGRAPHY 18 42 Scouts BSA 55 Real-World Example: BSA Camp Registration App 80 Photography 19 Venturing 56 EMAIL 81 Living Imagery 20 Sea Scouting 57 HTML Email 82 Doing Imagery 21 Choosing the Correct Color Palette 58 Email Signatures 83 Best Practices 22 IMAGERY 59 Email Best Practices 84 Image Pitfalls 23 Texture 60 ONLINE ADVERTISING 85 Resources 24 Icons -

How the Past Affects the Future: the Story of the Apostrophe1
HOW THE PAST AFFECTS THE FUTURE: THE STORY OF THE APOSTROPHE1 Christina Cavella and Robin A. Kernodle I. Introduction The apostrophe, a punctuation mark which “floats above the line, symbolizing something missing in the text” (Battistella, 1999, p. 109), has been called “an unstable feature of written English” (Gasque, 1997, p. 203), “the step-child of English orthography” (Barfoot, 1991, p. 121), and “an entirely insecure orthographic squiggle” (Barfoot, 1991, p. 133). Surely the apostrophe intends no harm; why then the controversy and apparent emotionalism surrounding it? One major motivation for investigating the apostrophe is simply because it is so often misused. A portion of the usage problem can perhaps be attributed to the chasm dividing spoken and written language, as the apostrophe was originally intended to indicate missing letters, which may or may not have actually been enunciated. To understand what has been called “the aberrant apostrophe,” (Crystal, 1995, p. 203) and the uncertainty surrounding its usage, an examination of its history is essential, for it is this “long and confused” (Crystal, 1995, p. 203) history that is partially responsible for the modern-day misuses of the apostrophe. This paper will trace the history of the apostrophe, examining the purpose(s) for which the apostrophe has been utilized in the past as well as presenting its current use. An overview of contemporary rules of usage is then included, along with specific examples of apostrophe misuse and a recommendation on how to teach apostrophe usage to non- native speakers of English. Finally, an attempt is made to predict the apostrophe’s future.