Email Threats 2017
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Technical and Legal Approaches to Unsolicited Electronic Mail, 35 USFL Rev
UIC School of Law UIC Law Open Access Repository UIC Law Open Access Faculty Scholarship 1-1-2001 Technical and Legal Approaches to Unsolicited Electronic Mail, 35 U.S.F. L. Rev. 325 (2001) David E. Sorkin John Marshall Law School, [email protected] Follow this and additional works at: https://repository.law.uic.edu/facpubs Part of the Computer Law Commons, Internet Law Commons, Marketing Law Commons, and the Privacy Law Commons Recommended Citation David E. Sorkin, Technical and Legal Approaches to Unsolicited Electronic Mail, 35 U.S.F. L. Rev. 325 (2001). https://repository.law.uic.edu/facpubs/160 This Article is brought to you for free and open access by UIC Law Open Access Repository. It has been accepted for inclusion in UIC Law Open Access Faculty Scholarship by an authorized administrator of UIC Law Open Access Repository. For more information, please contact [email protected]. Technical and Legal Approaches to Unsolicited Electronic Mailt By DAVID E. SORKIN* "Spamming" is truly the scourge of the Information Age. This problem has become so widespread that it has begun to burden our information infrastructure. Entire new networks have had to be constructed to deal with it, when resources would be far better spent on educational or commercial needs. United States Senator Conrad Burns (R-MT)1 UNSOLICITED ELECTRONIC MAIL, also called "spain," 2 causes or contributes to a wide variety of problems for network administrators, t Copyright © 2000 David E. Sorkin. * Assistant Professor of Law, Center for Information Technology and Privacy Law, The John Marshall Law School; Visiting Scholar (1999-2000), Center for Education and Research in Information Assurance and Security (CERIAS), Purdue University. -

Securing Your Email in 13 Steps: the Email Security Checklist Handbook Securing Your Email in 13 Steps
HANDBOOK Securing Your Email in 13 Steps: The Email Security Checklist handbook Securing Your Email in 13 Steps overview You’ve hardened your servers, locked down your website and are ready to take on the internet. But all your hard work was in vain, because someone fell for a phishing email and wired money to a scammer, while another user inadvertently downloaded and installed malware from an email link that opened a backdoor into the network. Email is as important as the website when it comes to security. As a channel for social engineering, malware delivery and resource exploitation, a combination of best practices and user education should be enacted to reduce the risk of an email-related compromise. By following this 13 step checklist, you can make your email configuration resilient to the most common attacks and make sure it stays that way. 2 @UpGuard | UpGuard.com handbook Securing Your Email in 13 Steps 1. Enable SPF How do you know if an email is really from who it says it’s from? There are a couple of ways to answer this question, and Sender Policy Framework (SPF) is one. SPF works by publishing a DNS record of which servers are allowed to send email from a specific domain. 1. An SPF enabled email server receives an email from [email protected] 2. The email server looks up example.com and reads the SPF TXT record in DNS. 3. If the originating server of the email matches one of the allowed servers in the SPF record, the message is accepted. -

Locating Spambots on the Internet
BOTMAGNIFIER: Locating Spambots on the Internet Gianluca Stringhinix, Thorsten Holzz, Brett Stone-Grossx, Christopher Kruegelx, and Giovanni Vignax xUniversity of California, Santa Barbara z Ruhr-University Bochum fgianluca,bstone,chris,[email protected] [email protected] Abstract the world-wide email traffic [20], and a lucrative busi- Unsolicited bulk email (spam) is used by cyber- ness has emerged around them [12]. The content of spam criminals to lure users into scams and to spread mal- emails lures users into scams, promises to sell cheap ware infections. Most of these unwanted messages are goods and pharmaceutical products, and spreads mali- sent by spam botnets, which are networks of compro- cious software by distributing links to websites that per- mised machines under the control of a single (malicious) form drive-by download attacks [24]. entity. Often, these botnets are rented out to particular Recent studies indicate that, nowadays, about 85% of groups to carry out spam campaigns, in which similar the overall spam traffic on the Internet is sent with the mail messages are sent to a large group of Internet users help of spamming botnets [20,36]. Botnets are networks in a short amount of time. Tracking the bot-infected hosts of compromised machines under the direction of a sin- that participate in spam campaigns, and attributing these gle entity, the so-called botmaster. While different bot- hosts to spam botnets that are active on the Internet, are nets serve different, nefarious goals, one important pur- challenging but important tasks. In particular, this infor- pose of botnets is the distribution of spam emails. -

Large-Scale Malware Experiments
LARGE-SCALE MALWARE EXPERIMENTS ... CALVET ET AL. LARGE-SCALE MALWARE • Unlike with in-the-wild experiments [1], there are fewer ethical or legal issues to deal with than when performing EXPERIMENTS: WHY, HOW, AND arbitrary attacks against infected computers. SO WHAT? • Having an in vitro environment provides us with a way to Joan Calvet, Jose M. Fernandez conduct computer security research in a scientifi c way: we École Polytechnique de Montréal, Montréal, Canada can reproduce experiments and test the effect of various independent variables. Email {joan.calvet, jose.fernandez}@polymtl.ca We decided to use the Waledac botnet as a fi rst experiment for the following reasons: Pierre-Marc Bureau ESET, Montréal, Canada • Thanks to prior reverse engineering [2], we had in-depth knowledge of this threat family. Email [email protected] • This malware does not replicate, thus limiting the risk of running an experiment that might get out of control. Jean-Yves Marion LORIA, Nancy, France • There exists a set of vulnerabilities in Waledac’s peer-to- peer protocol that were worth investigating. We wanted to Email [email protected] evaluate the impact of a mitigation scheme against the botnet. ABSTRACT 1.1 The Waledac case study One of the most popular research areas in the anti-malware The architecture of the Waledac botnet is split into four layers. industry (second only to detection) is to document malware The fi rst layer contains infected hosts with private IP addresses characteristics and understand their operations. Most initiatives that are referred to as spammers. They are essentially the are based on reverse engineering of malicious binaries so as to ‘worker’ bots and constitute approximately 80% of the botnet. -

Imail V12 Web Client Help
Ipswitch, Inc. Web: www.imailserver.com 753 Broad Street Phone: 706-312-3535 Suite 200 Fax: 706-868-8655 Augusta, GA 30901-5518 Copyrights ©2011 Ipswitch, Inc. All rights reserved. IMail Server – Web Client Help This manual, as well as the software described in it, is furnished under license and may be used or copied only in accordance with the terms of such license. Except as permitted by such license, no part of this publication may be reproduced, photocopied, stored on a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, recording, or otherwise, without the expressed prior written consent of Ipswitch, Inc. The content of this manual is furnished for informational use only, is subject to change without notice, and should not be construed as a commitment by Ipswitch, Inc. While every effort has been made to assure the accuracy of the information contained herein, Ipswitch, Inc. assumes no responsibility for errors or omissions. Ipswitch, Inc. also assumes no liability for damages resulting from the use of the information contained in this document. Ipswitch Collaboration Suite (ICS), the Ipswitch Collaboration Suite (ICS) logo, IMail, the IMail logo, WhatsUp, the WhatsUp logo, WS_FTP, the WS_FTP logos, Ipswitch Instant Messaging (IM), the Ipswitch Instant Messaging (IM) logo, Ipswitch, and the Ipswitch logo are trademarks of Ipswitch, Inc. Other products and their brands or company names are or may be trademarks or registered trademarks, and are the property of their respective companies. Update History December 2011 v12 April 2011 v11.5 October 2010 v11.03 May 2010 v11.02 Contents CHAPTER 1 Introduction to IMail Web Client About Ipswitch Web Messaging Help .................................................................................................................. -

Introduction to Email
Introduction to Email gcflearnfree.org/print/email101/introduction-to-email Introduction Do you ever feel like the only person who doesn't use email? You don't have to feel left out. If you're just getting started, you'll see that with a little bit of practice, email is easy to understand and use. In this lesson, you will learn what email is, how it compares to traditional mail, and how email addresses are written. We'll also discuss various types of email providers and the features and tools they include with an email account. Getting to know email Email (electronic mail) is a way to send and receive messages across the Internet. It's similar to traditional mail, but it also has some key differences. To get a better idea of what email is all about, take a look at the infographic below and consider how you might benefit from its use. Email advantages Productivity tools: Email is usually packaged with a calendar, address book, instant messaging, and more for convenience and productivity. Access to web services: If you want to sign up for an account like Facebook or order products from services like Amazon, you will need an email address so you can be safely identified and contacted. Easy mail management: Email service providers have tools that allow you to file, label, prioritize, find, group, and filter your emails for easy management. You can even easily control spam, or junk email. Privacy: Your email is delivered to your own personal and private account with a password required to access and view emails. -

Spambots: Creative Deception
PATTERNS 2020 : The Twelfth International Conference on Pervasive Patterns and Applications Spambots: Creative Deception Hayam Alamro Costas S. Iliopoulos Department of Informatics Department of Informatics King’s College London, UK King’s College London, UK Department of Information Systems email: costas.iliopoulos Princess Nourah bint Abdulrahman University @kcl.ac.uk Riyadh, KSA email: [email protected] Abstract—In this paper, we present our spambot overview on the intent of building mailing lists to send unsolicited or phishing creativity of the spammers, and the most important techniques emails. Furthermore, spammers can create fake accounts to that the spammer might use to deceive current spambot detection target specific websites or domain specific users and start send- tools to bypass detection. These techniques include performing a ing predefined designed actions which are known as scripts. series of malicious actions with variable time delays, repeating the Moreover, spammers can work on spreading malwares to steal same series of malicious actions multiple times, and interleaving other accounts or scan the web to obtain customers contact legitimate and malicious actions. In response, we define our problems to detect the aforementioned techniques in addition information to carry out credential stuffing attacks, which is to disguised and "don’t cares" actions. Our proposed algorithms mainly used to login to another unrelated service. In addition, to solve those problems are based on advanced data structures spambots can be designed to participate in deceiving users on that are able to detect malicious actions efficiently in linear time, online social networks through the spread of fake news, for and in an innovative way. -

A Visual Analytics Toolkit for Social Spambot Labeling
© 2019 IEEE. This is the author’s version of the article that has been published in IEEE Transactions on Visualization and Computer Graphics. The final version of this record is available at: 10.1109/TVCG.2019.2934266 VASSL: A Visual Analytics Toolkit for Social Spambot Labeling Mosab Khayat, Morteza Karimzadeh, Jieqiong Zhao, David S. Ebert, Fellow, IEEE G A H B C E I D F Fig. 1. The default layout of the front-end of VASSL: A) the timeline view, B) the dimensionality reduction view, C) the user/tweet detail views, D) & E) the topics view (clustering / words), F) the feature explorer view, G) the general control panel, H) the labeling panel, and I) the control panels for all the views (the opened control panel in the figure is for topics clustering view). Abstract—Social media platforms are filled with social spambots. Detecting these malicious accounts is essential, yet challenging, as they continually evolve to evade detection techniques. In this article, we present VASSL, a visual analytics system that assists in the process of detecting and labeling spambots. Our tool enhances the performance and scalability of manual labeling by providing multiple connected views and utilizing dimensionality reduction, sentiment analysis and topic modeling, enabling insights for the identification of spambots. The system allows users to select and analyze groups of accounts in an interactive manner, which enables the detection of spambots that may not be identified when examined individually. We present a user study to objectively evaluate the performance of VASSL users, as well as capturing subjective opinions about the usefulness and the ease of use of the tool. -

Detection of Spambot Groups Through DNA-Inspired Behavioral Modeling
IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING 1 Social Fingerprinting: detection of spambot groups through DNA-inspired behavioral modeling Stefano Cresci, Roberto Di Pietro, Marinella Petrocchi, Angelo Spognardi, and Maurizio Tesconi Abstract—Spambot detection in online social networks is a long-lasting challenge involving the study and design of detection techniques capable of efficiently identifying ever-evolving spammers. Recently, a new wave of social spambots has emerged, with advanced human-like characteristics that allow them to go undetected even by current state-of-the-art algorithms. In this paper, we show that efficient spambots detection can be achieved via an in-depth analysis of their collective behaviors exploiting the digital DNA technique for modeling the behaviors of social network users. Inspired by its biological counterpart, in the digital DNA representation the behavioral lifetime of a digital account is encoded in a sequence of characters. Then, we define a similarity measure for such digital DNA sequences. We build upon digital DNA and the similarity between groups of users to characterize both genuine accounts and spambots. Leveraging such characterization, we design the Social Fingerprinting technique, which is able to discriminate among spambots and genuine accounts in both a supervised and an unsupervised fashion. We finally evaluate the effectiveness of Social Fingerprinting and we compare it with three state-of-the-art detection algorithms. Among the peculiarities of our approach is the possibility to apply off-the-shelf DNA analysis techniques to study online users behaviors and to efficiently rely on a limited number of lightweight account characteristics. Index Terms—Spambot detection, social bots, online social networks, Twitter, behavioral modeling, digital DNA. -

An Introduction to Malware
Downloaded from orbit.dtu.dk on: Sep 24, 2021 An Introduction to Malware Sharp, Robin Publication date: 2017 Document Version Publisher's PDF, also known as Version of record Link back to DTU Orbit Citation (APA): Sharp, R. (2017). An Introduction to Malware. General rights Copyright and moral rights for the publications made accessible in the public portal are retained by the authors and/or other copyright owners and it is a condition of accessing publications that users recognise and abide by the legal requirements associated with these rights. Users may download and print one copy of any publication from the public portal for the purpose of private study or research. You may not further distribute the material or use it for any profit-making activity or commercial gain You may freely distribute the URL identifying the publication in the public portal If you believe that this document breaches copyright please contact us providing details, and we will remove access to the work immediately and investigate your claim. An Introduction to Malware Robin Sharp DTU Compute Spring 2017 Abstract These notes, written for use in DTU course 02233 on Network Security, give a short introduction to the topic of malware. The most important types of malware are described, together with their basic principles of operation and dissemination, and defenses against malware are discussed. Contents 1 Some Definitions............................2 2 Classification of Malware........................2 3 Vira..................................3 4 Worms................................ -

Modeling and Evaluating the Resilience of Peer-To-Peer Botnets
P2PWNED: Modeling and Evaluating the Resilience of Peer-to-Peer Botnets Christian Rossow∗‡, Dennis Andriesse‡, Tillmann Werner¶, Brett Stone-Gross†, Daniel Plohmann§, Christian J. Dietrich∗, Herbert Bos‡ ∗ Institute for Internet Security, Gelsenkirchen, Germany {rossow,dietrich}@internet-sicherheit.de ‡ VU University Amsterdam, The Netherlands {d.a.andriesse,h.j.bos}@vu.nl § Fraunhofer FKIE, Bonn, Germany, [email protected] † Dell SecureWorks, [email protected] ¶ CrowdStrike, Inc. Abstract—Centralized botnets are easy targets for takedown disrupted using the traditional approach of attacking critical efforts by computer security researchers and law enforcement. centralized infrastructure. Thus, botnet controllers have sought new ways to harden the Even though active P2P botnets such as the Zeus P2P infrastructures of their botnets. In order to meet this objective, some botnet operators have (re)designed their botnets to use variant, Sality, ZeroAccess and Kelihos have survived in the Peer-to-Peer (P2P) infrastructures. Many P2P botnets are far wild for as long as five years, relatively little is known about more resilient to takedown attempts than centralized botnets, the sizes of these botnets. It is difficult to estimate a P2P because they have no single points of failure. However, P2P botnets are subject to unique classes of attacks, such as node botnet’s size, for a number of reasons. P2P botnets often enumeration and poisoning. In this paper, we introduce a use custom protocols, so that researchers must first reverse formal graph model to capture the intrinsic properties and engineer the protocol and encryption before they can track fundamental vulnerabilities of P2P botnets. We apply our the botnet’s population. -
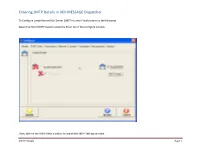
Entering SMTP Details in REV MESSAGE Dispatcher
Entering SMTP Details in REV MESSAGE Dispatcher. To Configure using Internet Mail Server (SMTP) to send Emails please do the following. Select the Email (SMTP) option under the Email tab in the Configure window. Then, click on the SMTP Details button to launch the SMTP Settings window. SMTP details Page 1 Entering SMTP Details in REV MESSAGE Dispatcher. In the User Information enter the Sender Name and the Sender E-mail Address. This is what will appear in the ‘From:’ field when the email is received. For example, we use Message Dispatcher for the Name and [email protected] as the E-mail Address SMTP details Page 2 Entering SMTP Details in REV MESSAGE Dispatcher. Example of what it looks like when the email is viewed. SMTP details Page 3 Entering SMTP Details in REV MESSAGE Dispatcher. The next step is to enter the Outgoing Mail Server SMTP (Simple Mail Transport Protocol) address. You can also use an IP address instead, i.e. 118.208.34.220 SMTP details Page 4 Entering SMTP Details in REV MESSAGE Dispatcher. The final step is to enter your outgoing email account and password information that provided to you by your ISP or Network Administrator. SMTP details Page 5 Entering SMTP Details in REV MESSAGE Dispatcher. There’re also Options for Email Attachment Encoding (MIME and UUEncode) and Email Message Format (HTML Mail Format). To send out long URL link in the email (like we have with the Web Interface link) we recommend you to select the HTML Mail Format option. Now, we just need to click on the Accept button to save these settings SMTP details Page 6 .